How to get rid of spyware
Some computer users are unfamiliar with the term “spyware,” which covers numerous computer infections. However, not all computer infections belong to malware category, and so they cannot be called as viruses. Typically, spyware-type programs are unpleasant and useless tools that carry out annoying activities on the compromised computer. While the majority of spyware programs are legitimate (for example, potentially unwanted programs like adware or browser hijackers), the other part can be dangerous and initiate illegal activities, so such programs should be feared and stay away from the computer system. An example of a malicious spyware-type program is a Trojan horse, although it is typically added to malware category.
What is more, spyware is capable of infiltrating the computer silently, without displaying any notifications, warnings or installation setups. Such programs can also silently collect information about the user for months until they are detected and removed. In most cases, information such programs gather is used for market research and selection of targeted advertisements. Non-malicious spyware programs cannot collect personally identifiable information, because such activity is considered illegal. However, they can collect non-personally identifiable information that describes user’s browsing habits, and not every computer user wants such programs on the computer. In this article, we are going to describe the spyware category in detail and provide you with the most relevant information about it, including instructions on how to prevent spyware infiltration or how to remove such potentially unwanted programs from the system.
How do spyware-type programs act and what can they do once they get installed?
- Collect private information. Spyware-type programs can collect both personally and personally non-identifiable data by tracking user’s activity online. For example, such programs can track clicks, bookmarks, information about downloaded files, search and browsing history, also IP address and related information completely without user’s knowledge. More aggressive spyware programs can gather personal information such as user’s name, surname, login information, and the like.
- Make arbitrary changes on the computer. Spyware programs that enter the computer with or without user’s knowledge can change some system settings to be able to carry out some activities later on. For example, they can change browser settings and change homepage address or install some suspicious components that serve pop-up ads for the user.
- Cause browser redirections. When infected with a spyware-type program, the user can experience unwanted and unexpected redirects to vague third-party websites whenever he or she attempts to use the infected web browser. These redirects are meant to increase traffic to certain web pages and can reroute the user to dangerous Internet sites.
- Showcase web ads. Spyware-type programs can generate and load annoying web advertisements for the user during his/hers browsing sessions. These ads can be based on information collected about the user. These ads typically are very annoying and usually they also cause web redirections to suspicious third-party websites.
- Set up a backdoor and allow attackers to hack the computer easily.
- Slow down computer’s functionality and diminish the overall performance.
How spyware threats manage to infiltrate computers?
Spyware threats spread with the help of several different techniques, which are listed below.
- Bogus web advertisements. Developers of spyware often pretend that their software is reliable, useful, and should be installed by every computer user. In reality, these authors advertise useless programs that can hardly improve user’s daily life.
- Bundled software. Be careful when installing free software because it can drag some unwanted files and programs to your computer. Typically, free programs suggest installing some “trustworthy” programs that can entertain you, provide useful information or so. Sadly, we cannot say that these programs are actually useful.
- Security holes in user’s computer system. Spyware can be very easily installed on computers of user’s that do not have an anti-malware software. For example, such programs can be installed quickly after clicking on a deceptive web advertisement, visiting a corrupted website, opening a bogus email attachment or installing bundled software without adjusting the installation settings first.
- Other viruses. Spyware mostly travels in software bundles, so be careful when you install something on your computer system. Make sure you choose Custom or Advanced settings and deselect unwanted components before clicking that “Install” button.
Three examples of spyware-type programs
QKSee ads. This application is a well-known spyware example because it uses various techniques to stay on the computer system. This spyware variant is stubborn and computer users find it hard to remove QKSee. While on the computer system, QKSee adware collects pieces of information about the user in order to determine what interests him/her, and later on displays related third-party offers in the form of pop-up ads or banners. The official website of this ad-supported spyware variant states that it is a “new image engine.” In reality, this program is only a suspicious tool meant to advertise third-party content.
Delta-homes.com browser hijacker. Delta-homes.com is a suspicious Internet site that suggests using a new search engine. It also provides shortcuts to various popular Internet sites and also some leading to questionable third-party websites. This search tool should not be trusted because it can cause web redirects to questionable third-party websites. This spyware-type application is usually installed without user’s knowledge, and it attempts to avoid detection by hiding its files on the system. It also collects information about user’s computer, browsing habits, and other information that helps to understand user’s needs. Later on, it selects targeted advertisements and showcases them for the user via pop-up ads or integrates them into search results.
Offers4u adware. This adware-type program can be installed along with other free programs and start collecting personally non-identifiable data right away. It silently makes minor adjustments in the target system and uses various tracking technologies to find out what the user is interested in. It can collect user’s search queries, clicks, review the list of recently visited websites, find out the geolocation of user’s computer and transfer such information to a remote server. Later on, this program compiles a list of third-party ads to display and starts bothering the PC user by showing them daily.
How to remove spyware programs?
Although spyware programs are not as hazardous as those that belong to malware category, it is highly recommended to keep the PC free of them. Although they cannot wreak havoc on the computer system, they can gather information about user’s activities online and also interests and use such data for some shady purposes or share it with third-parties. To remove spyware, we recommend using a reliable anti-spyware software, and the NoVirus.uk team recommends using these programs: FortectIntego, SpyHunter 5Combo Cleaner. If these programs cannot remove certain spyware variant, please contact the developers of these programs or us and report the issue. You can also browse our website for free spyware removal tutorials that we continuously publish. If you cannot find a certain removal tutorial, please get in touch with our support team.
Latest spyware threats added to the database
Steps for removing Bozq ransomware
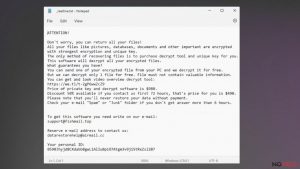
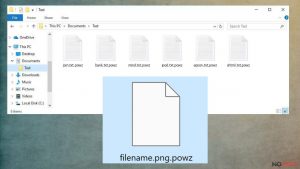
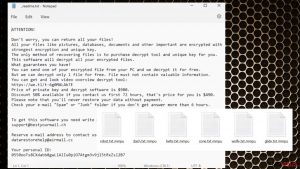
Uninstalling Powz ransomware
Mmpu ransomware removal tutorial
Additional information added on 2016-10-26