Uninstall XHAMSTER virus (Free Removal Guide) - Quick Decryption Solution
XHAMSTER virus Removal Guide
Description of XHAMSTER ransomware
XHAMSTER ransomware is the infection encoding personal files to get money from victims directly
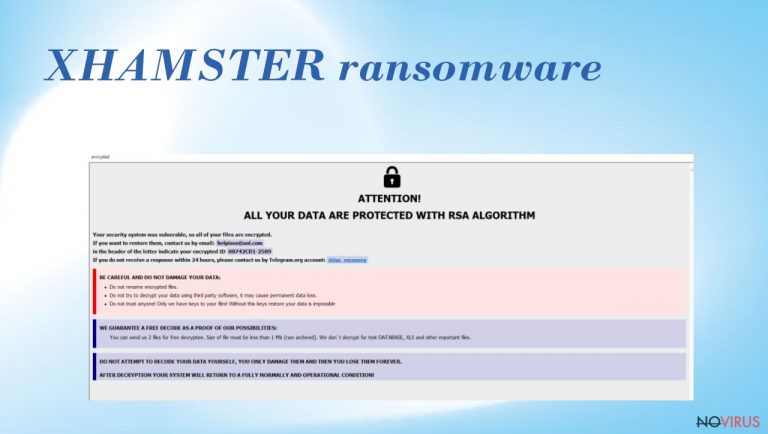
XHAMSTER ransomware is a dangerous cryptocurrency extortion-based threat. This is the particular virus that makes various changes on the computer once the system gets infected. Also, it locks various most common files with the help of encryption algorithms and makes them inaccessible. As a result, victims often try to pay the demanded ransom, but this is not recommended. It is better to take other actions than rely on untrustworthy cybercriminals.
This particular virus is the new variant of a well-known Phobos ransomware family. These creators encourage victims to pay the ransom amount and receive the alleged decryption tool in return. Such tactics are common and used by many other ransomware-type threats. However, it is important to note that cybercriminals can trick you and not help you unlock files or they can send additional threats instead of the promised tool.
Additional information about the file-locker
XHAMSTER ransomware makes data useless and unopenable when the infection finds its way to the vulnerable computer. This threat is dangerous and cannot be left unattended on the machine as it can cause additional problems or lock new files too. In addition to encrypting files, such viruses can severely damage your computer and its essential functions. If you do not want to experience a lot of problems, it is better to remove this virus.
XHAMSTER ransomware removal should be done with a reliable anti-malware tool. Only then can you think about file recovery. Unfortunately, there is no official decryption tool, but below you will find other solutions that can help in this situation. Also, it is important to repair the damaged system.
The threat renames files once they get locked, and the original code is altered. It marks files with a .XHAMSTER extension and then displays a message which offers to decrypt the data if payment in Bitcoin is made. If you do not know what the locked file looks like, here is a simple example: a file named 2.jpg becomes an unopenable piece renamed to 2.jpg.id[C279F237-2797].[ICQ@xhamster2020].XHAMSTER. Also, every victim gets a personal ID and contact information that is left in the info.hta and info.txt files. These ransom messages also describe facts about the payment and file recovery options.
| Name | XHAMSTER ransomware |
|---|---|
| Type | Cryptovirus, file-locker |
| Family | Phobos ransomware |
| File marker | .XHAMSTER |
| Ransom messages | info.hta, info.txt |
| Contact | @xhamster2020 on ICQ |
| Distribution | Files added to email attachments, distributed via pirated packages, other torrent files |
| Elimination | The best option is to base the elimination process on virus detection rate and choose a proper anti-malware tool for the termination of this virus and associated files |
| Repair | FortectIntego can ensure that the machine is working as it is supposed to and can fix virus damage left behind |
The ransom message that criminals deliver after successful encoding of data:
All your files have been encrypted!
All your files have been encrypted due to a security problem with your PC.
If you want to restore them, install ICQ software on your PC here hxxps://icq.com/windows/
or on mobile phone from Appstore/Google Play Market search for “ICQ”
Write to our ICQ @xhamster2020 hxxps://icq.im/xhamster2020
Write this ID in the title of your message –
You have to pay for decryption in Bitcoins. The price depends on how fast you write to us.
Free decryption as guarantee
Before paying you can send us up to 5 files for free decryption. The total size of files must be less than 3Mb (non archived), and files should not contain valuable information. (databases,backups, large excel sheets, etc.)
Attention!
Do not rename encrypted files.
Do not try to decrypt your data using third party software, it may cause permanent data loss.
Decryption of your files with the help of third parties may cause increased price (they add their fee to our) or you can become a victim of a scam.
Be assured we are the only people who can recover your files and there is no free tool.
Remove the virus completely as soon as possible
Such infection can cause more damage than file encryption. It alters system files and settings directly to ensure that the needed processes get to run with every reboot and all the functions are controlled by the ransomware. This is crucial since all the alterations lead to failed functions, disabled programs, and features of the OS. It is possible that ransomware releases additional malware payloads and triggers security tools or different applications to get shut down. You need to remove the infection, and the way to do so is to run the AV tool for the proper XHAMSTER ransomware removal.
Antivirus applications can detect the files related to ransomware and additional threats like malware, trojans, and worms. If you scan your system with SpyHunter 5Combo Cleaner or Malwarebytes, it can reveal all potential infections. This is a crucial step because any threats left behind can affect the machine further and even trigger another round of file encryption. It is even possible to lose the data permanently.
XHAMSTER file virus developers instruct victims to pay the demanded amount and contact them via ICQ for the payment details. But we do not recommend paying the ransom or trying to contact cybercriminals because they can take the ransom money but still not send the promised decryption tool.
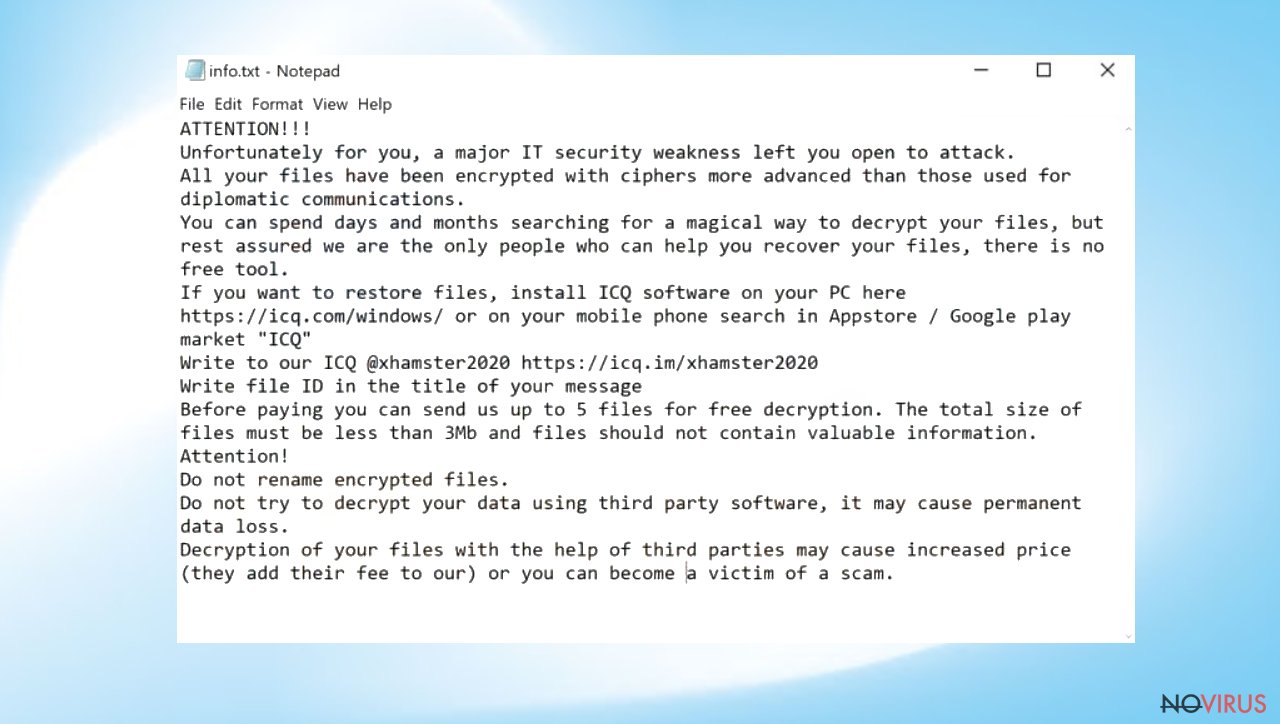
Even if you need these encrypted files, it is still not worth relying on virus developers. There are other ways to recover locked data and the simplest solution is using backups. If your computer has been affected by XHAMSTER ransomware, remove it as soon as possible and only then try other options for data recovery.
Remember to repair the virus damage
When ransomware and other viruses infect the machine, various processes get affected. Windows registry entries, other directories, and databases of system files can get damaged or corrupted. Affected files can lead to additional system issues. Malware damage to such files triggers problems with performance and stability, and security issues. Windows operating system recovery is needed then.
You should rely on proper tools that are designed to repair such files, and recover smooth performance. FortectIntego is developed with the purpose to fix damaged files, repairing processes, and removing other pieces of malware that get leftover. The program has a few engines and databases where needed Windows files can be found and repaired. This application also wan fix errors related to registry, damaged DLLs, and other system files. You can find links where you can download this PC repair tool, then:
- Download the application by clicking on the link above
- Click on the ReimageRepair.exe

- Choose Yes when the User Account Control (UAC) shows up.
- Press Install and wait for the installation process.
- The analysis of your machine with begin after the installation.
- Check the results listed in the Summary.
- You can choose each of the issues and fix them manually.
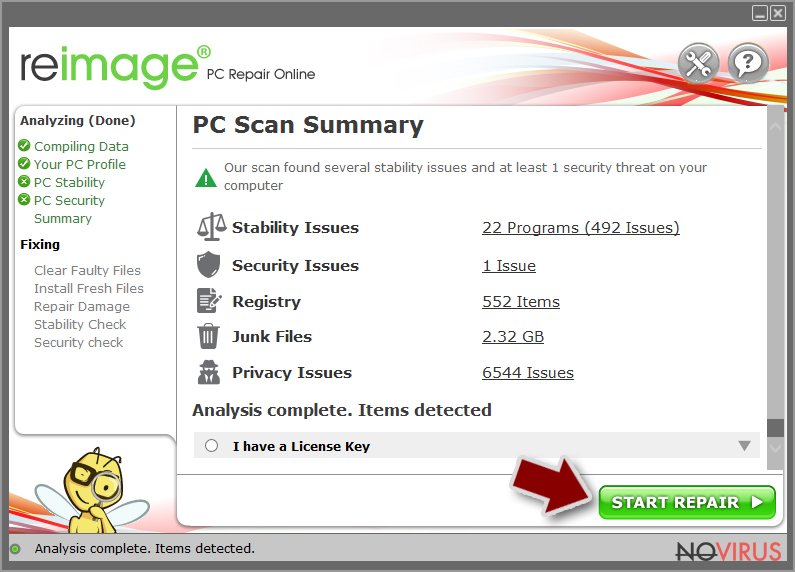
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.
Using this software can save a lot of time for you and improve the performance of the machine. Various issues can get fixed and system errors solved by running a thorough system scan and repair. You can avoid manual file repair that when done incorrectly can trigger more serious damage. Automatic system repair means that you do not need to reinstall the OS or different files.
The ransomware can enter the system unnoticed
XHAMSTER ransomware spreads the same way as any other version of the Phobos file virus. The malicious infection finds its way to the computer when the infectious file is opened and launched on the targeted machine. Users download such files using torrent platforms, inadvertently opening spam e-mails, downloading pirated game versions, etc. This is why you need to be very careful and always think about what websites you visit or what files you download.
Infected files can run the payload on the system quickly and cause the drop of dangerous malware like the XHAMSTER file virus. Often users do not even realize that they have downloaded the virus. They only notice it when all their personal files are encrypted and a ransom message is left on their computer.

If you want to avoid ransomware and other infections in the future, you should always have a reliable anti-malware program on the machine. Also, it is very important to download applications only from trusted sources. Suspicious emails, advertisements, links, etc. should be ignored.
Getting rid of XHAMSTER virus. Follow these steps
Software for file restoring
Data backups are important, but users tend to skip such an important step. Also, ransomware comes without notice, so many files affected by the threat can be the ones that haven't been backed up yet. paying the demanded ransom is not the solution, so trusting criminals is not the option for file recovery.
File recovery is a difficult thing, but it is possible to retrieve those files that get affected or encrypted, in some cases. It is highly related to the fact that there are many methods to lock files. The encryption algorithm used can determine if decryption is possible. Since there are thousands of ransomware strains, it is impossible to tell if any software will work for you.
We suggest trying the program regardless of which ransomware attacked your computer. Make sure to pay attention to some details before you begin:
- Note that encrypted data on your computer might get permanently damaged by security or data recovery software, you should first make backups of it to save crucial data.
- Make sure to recover your files using this method after you perform a thorough system scan with anti-malware software.
Install file recovery software
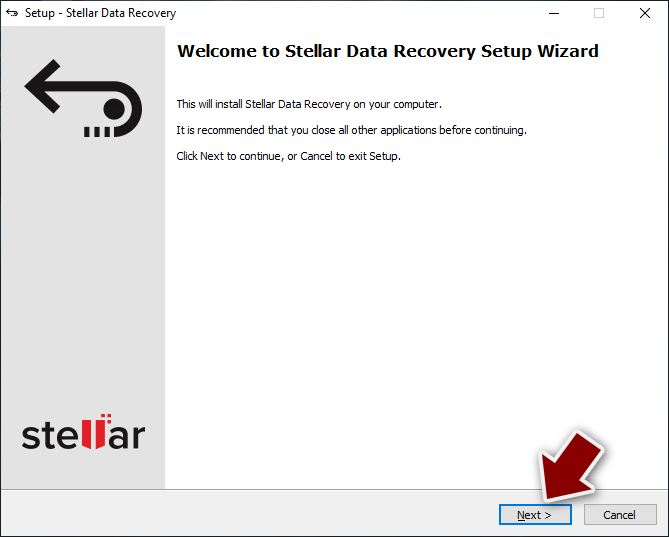
- Download Data Recovery Pro.
- Double-click the file to launch it.
- Follow instructions to install the software.
- Press Finish and use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.
- Press Next.
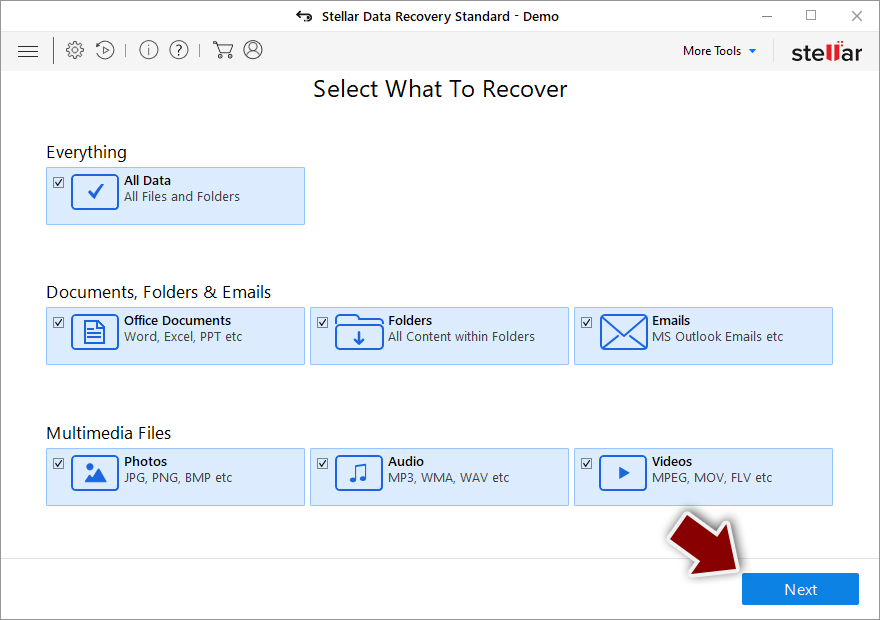
- Enable Deep scan and pick which Disks you want to be scanned.
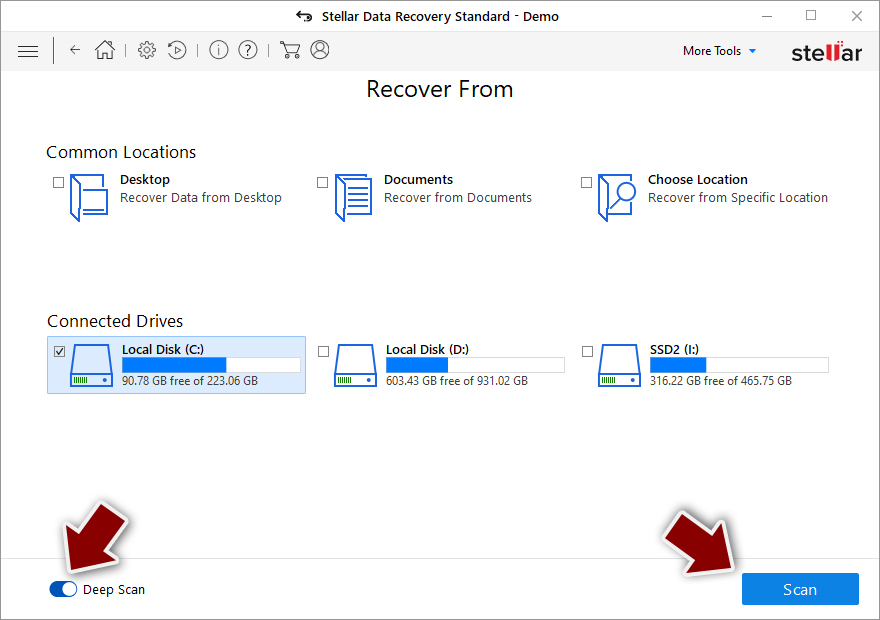
- Press Scan and wait till it is complete.
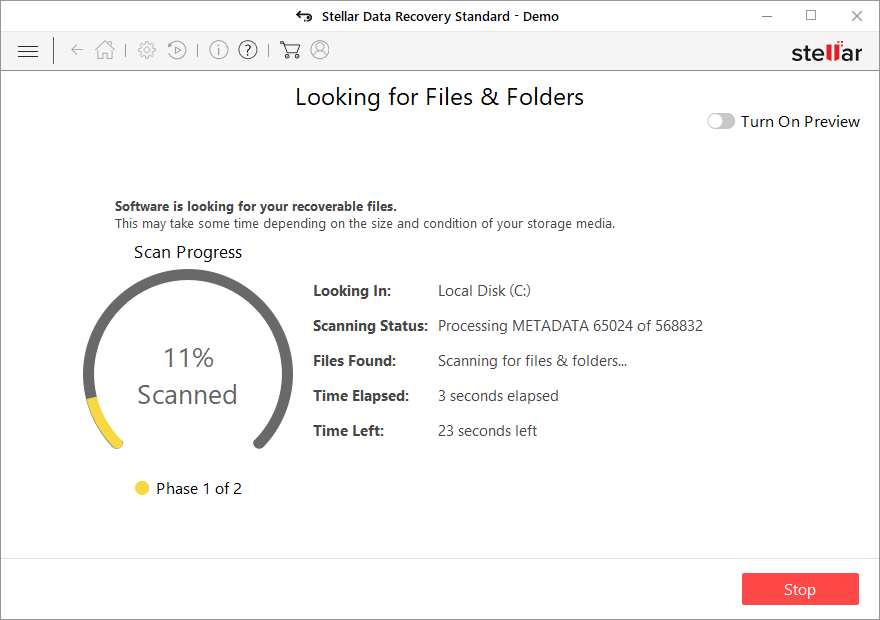
- You can choose folders/files to recover – don't forget you also have the option to search by the file name!
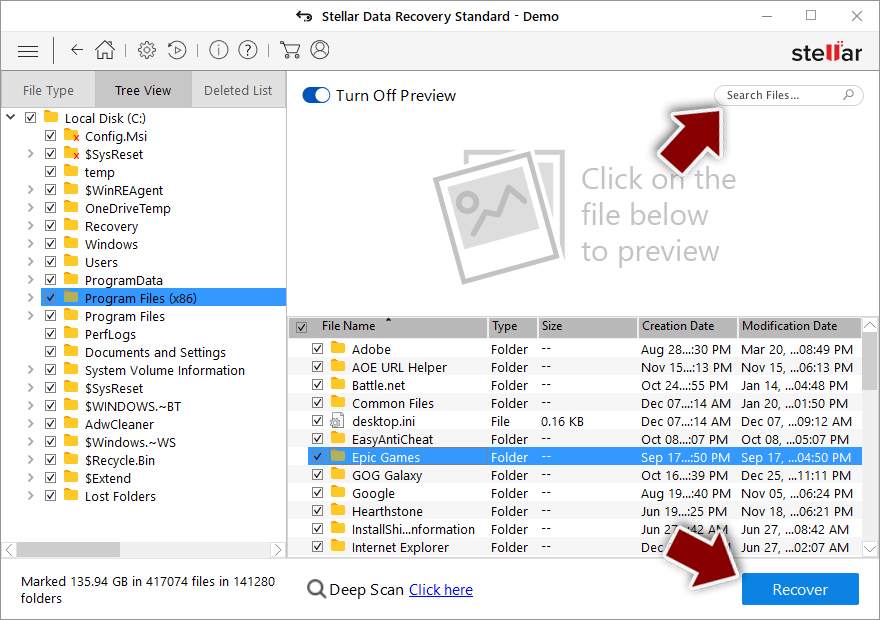
- Press Recover to retrieve your files.
In-depth guide for the XHAMSTER elimination
Important! →
The elimination guide can appear too difficult if you are not tech-savvy. It requires some knowledge of computer processes since it includes system changes that need to be performed correctly. You need to take steps carefully and follow the guide avoiding any issues created due to improper setting changes. Automatic methods might suit you better if you find the guide too difficult.
Step 1. Launch Safe Mode with Networking
Safe Mode environment offers better results of manual virus removal
Windows 7 / Vista / XP
- Go to Start.
- Choose Shutdown, then Restart, and OK.
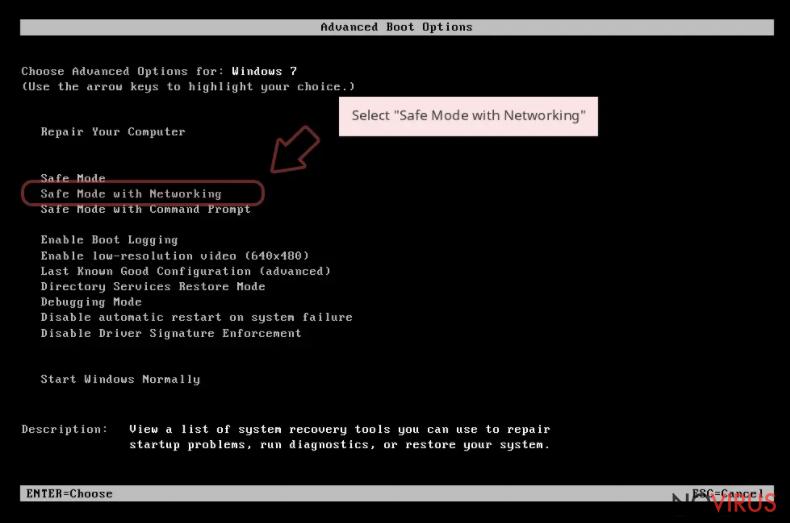
- When your computer boots, start pressing the F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) a few times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.
Windows 10 / Windows 8
- Right-click the Start button and choose Settings.
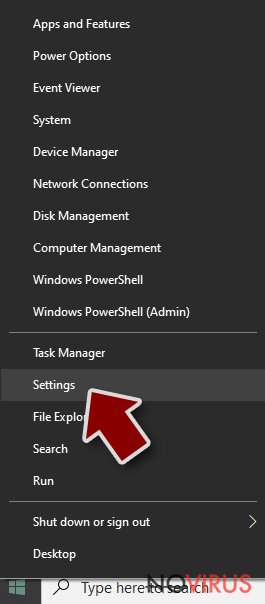
- Scroll down to find Update & Security.
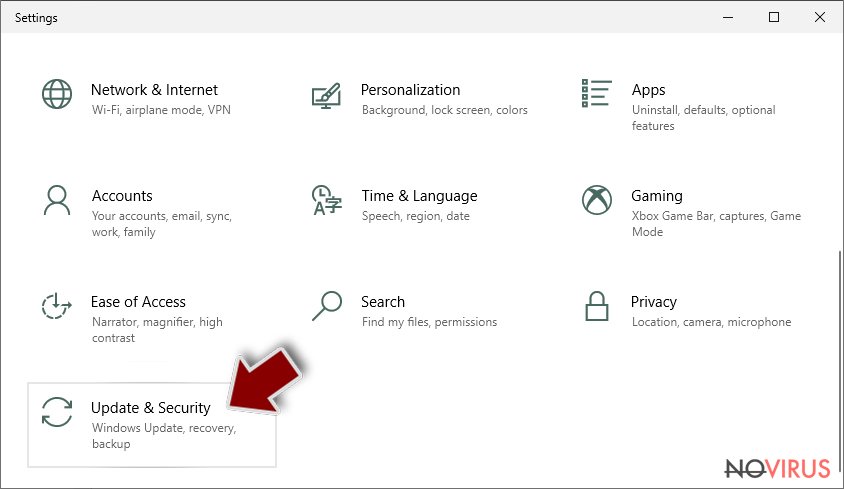
- On the left, pick Recovery.
- Scroll to find Advanced Startup section.
- Click Restart now.
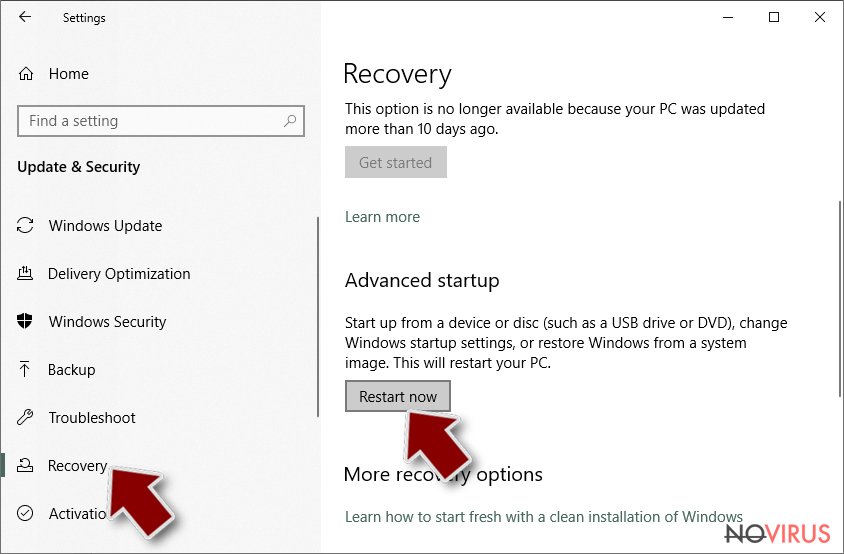
- Choose Troubleshoot.
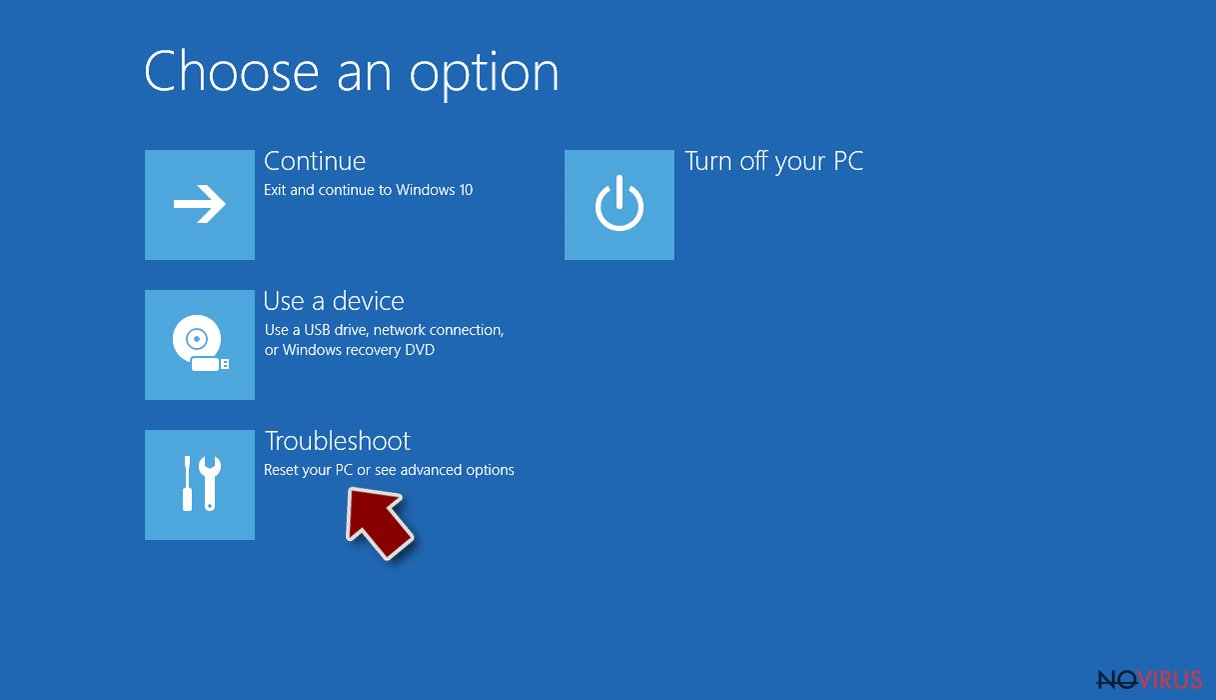
- Go to Advanced options.
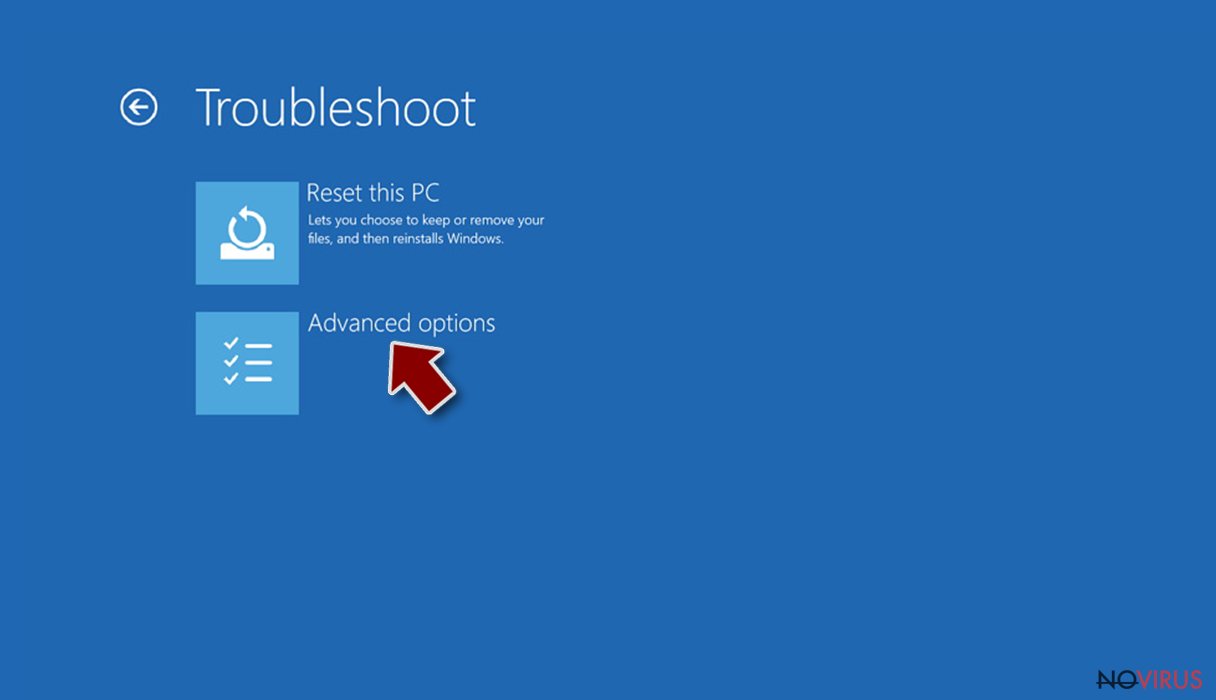
- Select Startup Settings.
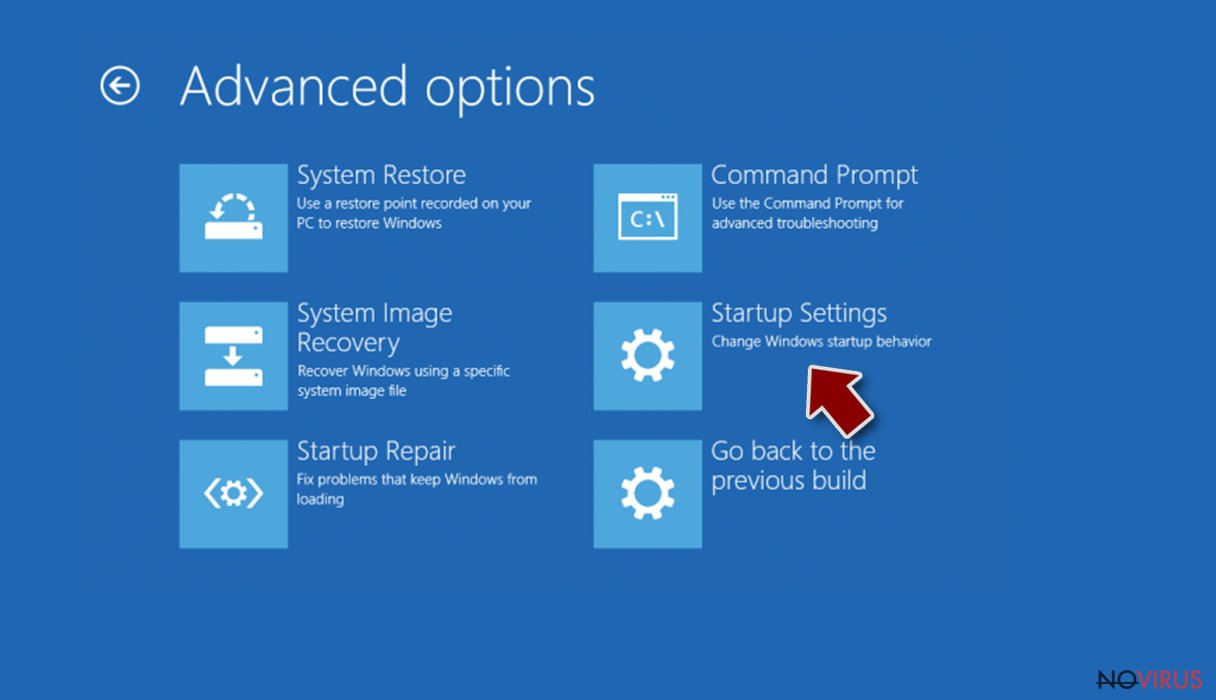
- Press Restart.
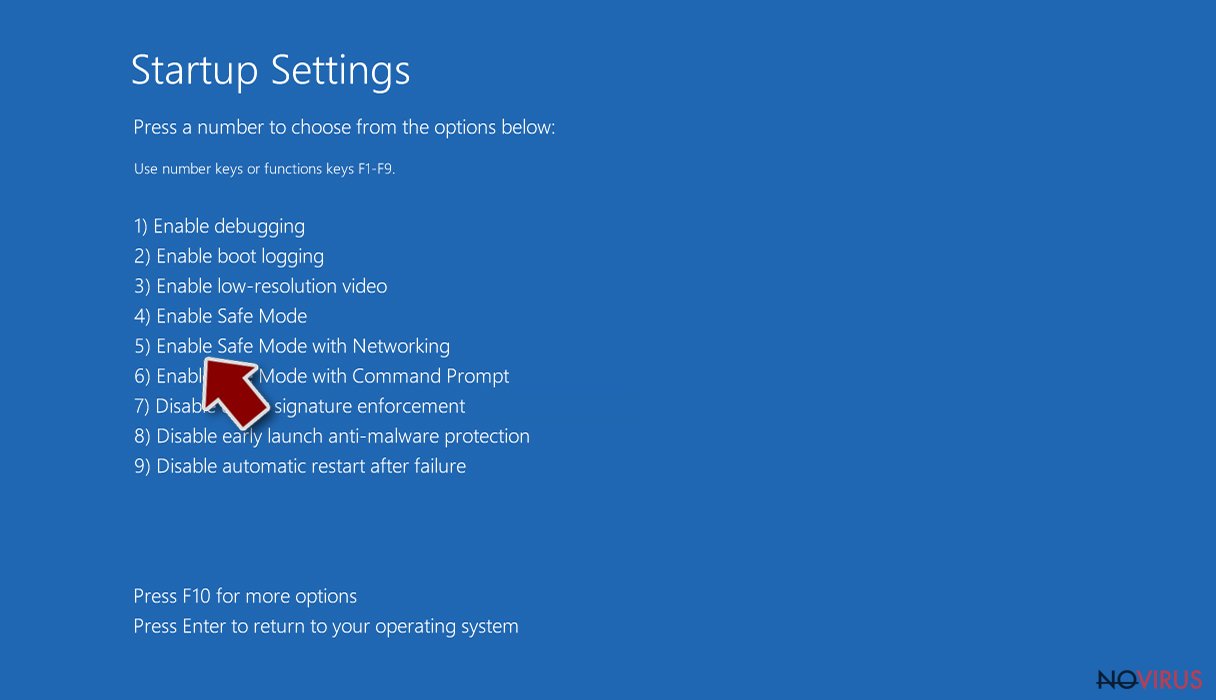
- Choose 5) Enable Safe Mode with Networking.
Step 2. End questionable processes
You can rely on Windows Task Manager that finds all the random processes in the background. When the intruder is triggering any processes, you can shut them down:
- Press Ctrl + Shift + Esc keys to open Windows Task Manager.
- Click on More details.
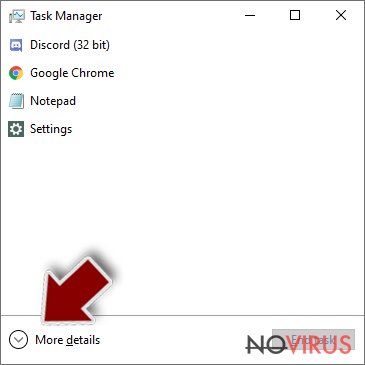
- Scroll down to Background processes.
- Look for anything suspicious.
- Right-click and select Open file location.
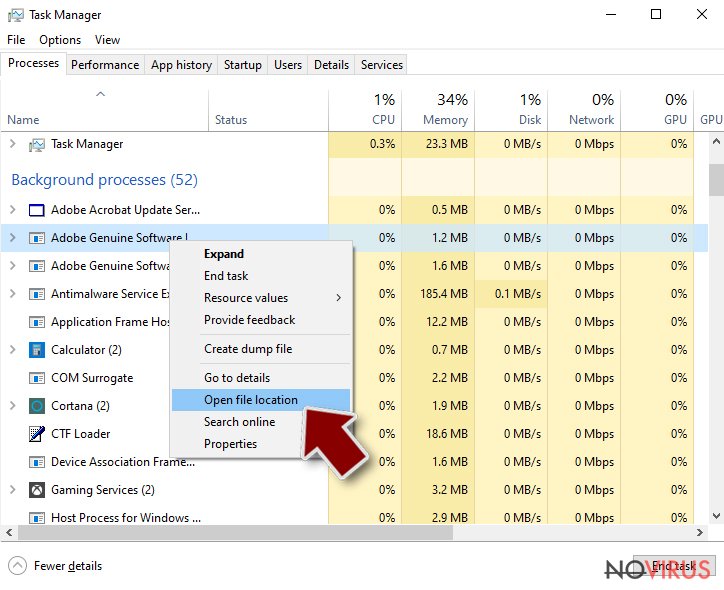
- Go back to the Process tab, right-click and pick End Task.
- Delete the contents of the malicious folder.
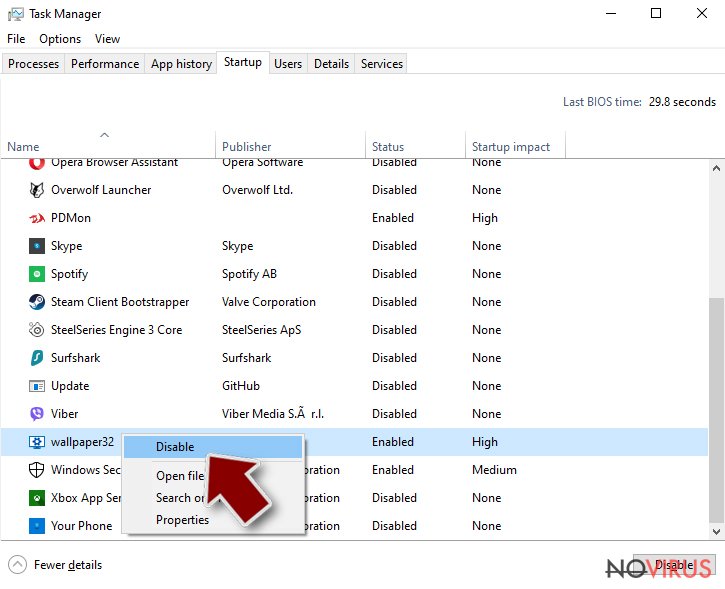
Step 3. Check the program in Startup
- Press Ctrl + Shift + Esc on your keyboard again.
- Go to the Startup tab.
- Right-click on the suspicious app and pick Disable.
Step 4. Find and eliminate virus files
Data related to the infection can be hidden in various places. Follow the steps and you can find them:
- Type in Disk Cleanup in Windows search and press Enter.
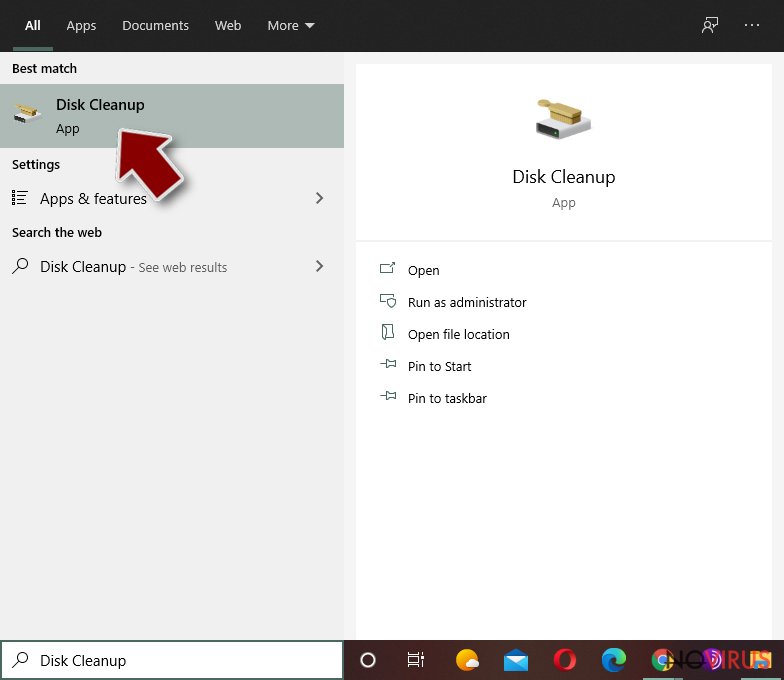
- Select the drive (C: is your main drive by default and is likely to be the one that has malicious files in) you want to clean.
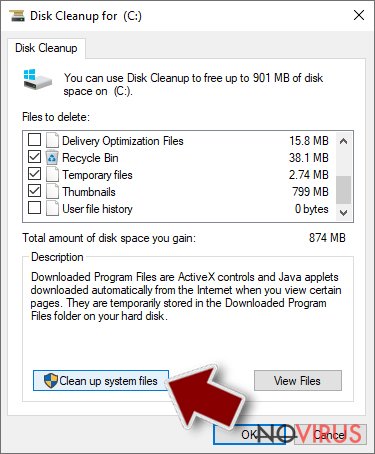
- Scroll through the Files to delete and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.
- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
It is strongly recommended to take precautions and secure your computer from malware attacks. To protect your PC from XHAMSTER and other dangerous viruses, you should install and keep a powerful malware removal tool, for instance, FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes.
How to prevent from getting ransomware
A proper web browser and VPN tool can guarantee better safety
As online spying becomes an increasing problem, people are becoming more interested in how to protect their privacy. One way to increase your online security is to choose the most secure and private web browser. But if you want complete anonymity and security when surfing the web, you need Private Internet Access VPN service. This tool successfully reroutes traffic across different servers, so your IP address and location remain protected. It is also important that this tool is based on a strict no-log policy, so no data is collected and cannot be leaked or made available to first or third parties. If you want to feel safe on the internet, a combination of a secure web browser and a Private Internet Access VPN will help you.
Reduce the threat of viruses by backing up your data
Due to their own careless behavior, computer users can suffer various losses caused by cyber infections. Viruses can affect the functionality of the software or directly corrupt data on your system by encrypting it. These problems can disrupt the system and cause you to lose personal data permanently. There is no such threat if you have the latest backups, as you can easily recover lost data and get back to work.
It is recommended to update the backups in parallel each time the system is modified. This way, you will be able to access the latest saved data after an unexpected virus attack or system failure. By having the latest copies of important documents and projects, you will avoid serious inconveniences. File backups are especially useful if malware attacks your system unexpectedly. We recommend using the Data Recovery Pro program to restore the system.
