How to remove trojans
Trojan horse, or Trojan, is a dangerous program that can get inside computer system without user’s knowledge and start illegal and harmful activities there. Trojan horses are commonly disguised as safe programs or files and used as tools to carry out particular activities on the target systems. In most cases, trojans are utilised by cyber criminals who seek to steal personal and valuable information, control the target computer remotely, corrupt files stored on the computer and prevent the user from using particular programs or block access to certain websites. Trojans cannot self-replicate since they do not function like typical computer viruses or worms. They are designed to stay hidden and avoid detection, and they can remain in the system and stay active for weeks, months or even years until the victim either realises that computer is compromised or runs a system scan with an anti-malware program to detect it.
How do trojans operate?
Trojans can function however their authors command them to do. It depends on how Trojan is programmed and for what purpose it is created. Below you can see a list of functions that a successful Trojan horse can do:
- Steal bank account details, passwords, and various important private information.
Work as a keylogger – spy on everything you type with your keyword, take screenshots and send them to a remote server or e-mail. - Set up a backdoor and allow the cyber criminal access and control the computer remotely.
- Encrypt, corrupt, delete, overwrite files, programs, and essential system files. Trojans can also wipe out all personal data, for example, by formatting the hard disk.
- Download, install and launch other viruses. Unfortunately, trojans do this quite frequently. In most cases, trojans install ransomware viruses, which encrypt personal data and demand a ransom.
- Set up a secret FTP server that can be used for various purposes.
- Initiate Denial of Service (DoS) attacks and similar network attacks. Trojans can attack remote hosts and also work as spam tools – they can send thousands of e-mail messages to certain computers with an intention to clutter them.
- Slow down the computer. Typically, Trojans run in the background and remain silent, so typically there are no visible signs of their presence, except slow computer’s performance.
- Block anti-virus programs to avoid detection, also block access to certain websites (typically – to security related websites).
- Show pop-up ads and change settings of Internet browsers.
- Slow down the speed of Internet by using it for its own needs.
- Cause problems with system’s stability.
Three examples of most known Trojan horses
- Trojan.ZeroAccess. It is a malicious Trojan horse that belongs to malware category. Some malware researchers identify it as max++. This Trojan horse functions as a keylogger and its main function is to track user’s keystrokes and steal sensitive information for illegal purposes. Can be installed from untrustworthy Internet sites, arrive as an email attachment, or come in a bundle with pirated software.
- Trojan.CryptoLocker. It is one of the most infamous crypto-ransomware type virus, which encrypts all files on the system and demands a ransom. Unfortunately, this trojan is strong enough to keep its decryption secret away from malware researchers, so none of the victims can recover their files for free. This Trojan horse is usually sent to victims via email in the form of a safe-looking email attachment.
- JS.Nemucod trojan. It is a typical Trojan horse that is used to download malware to the compromised computer. According to our research, JS.Nemucod virus is used for Locky, TeslaCrypt, and Crypted distribution. This Trojan also spreads via email and can look entirely safe at first sight. Once installed on the target system, it remains silent, and then all of a sudden connects to its server and downloads malware to the computer. JS.Nemucod can only be detected with the help of a powerful anti-malware program.
How do Trojan horses step into computer systems?
- If you remember the legend about the Trojan horse, you probably know that the fake horse imitation was used to get Greeks into the Troy city and let them win the war. Speaking of computer trojans, these are used to enter the PC system deceptively and initiate malicious activities there. When Trojan horse enters the system, the victim cannot notice any suspicious signs because unlike regular programs, Trojans do not need to launch installation wizards or ask for user’s permission to be installed. Now, we are going to discuss how Trojan horses manage to enter victims’ computers without being noticed.
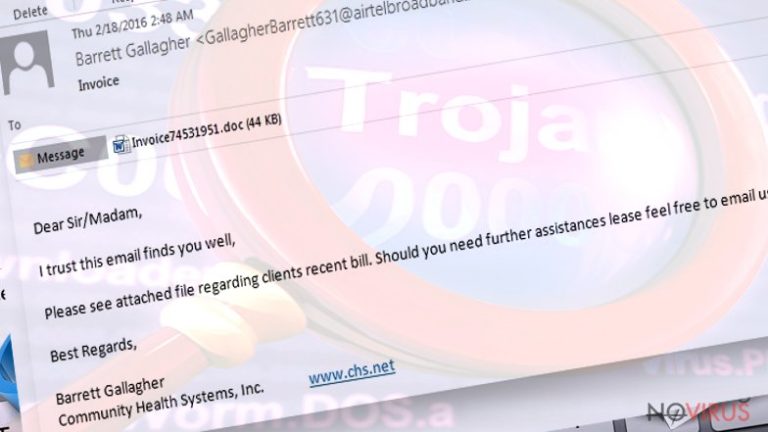
- Just like we have mentioned before, trojans spread via email, because their authors tend to create phony emails and attach viruses to them. Usually, deceptive emails ask the victim to open the email attachment and read “relevant” information written there, however, users should not rush to do that. Misleading email attachments typically hide malware payload, which, once dropped, infect the system and wreak havoc in it.
- Trojan horse can get into your PC together with bundled software. For example, you can refuse to install optional applications when installing a particular free program, but do you know how to do that? If not, we highly recommend you to pay attention to the installation setup and make sure there are no additional programs added to your download. You can find that out by opening Advanced or Custom settings and then manually deselecting suspicious or unwanted elements manually.
- Malicious Trojans can be installed due to browser’s vulnerabilities, so make sure you update them often. Criminals take every possible chance to infect users’ computer, and they use tools such as exploit kits to scan user’s computer for security vulnerabilities and exploit them. Exploit kits are made to run on web servers and check vulnerabilities in users’ PCs that communicate with it.
- Trojans can also be downloaded to the system by other malware variants, for example, worms, ransomware, viruses, even non-malicious programs. To avoid infiltration of such malicious programs, security experts recommend installing reliable anti-malware software.
How to remove a Trojan horse from a compromised computer?
Trojans should be uninstalled only with automatic malware removal tools because these are programmed by IT experts who have already examined Trojan horses and know what exactly to look for on the compromised computer. Trying to find trojan’s components manually can be hard, and also dangerous, because unsuccessful Trojan horse removal can do more harm than good. To uninstall Trojan horses, we strongly recommend using these tools: FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes. Please be careful and do not install computer programs without thinking first. If you suspect that your computer has been infected with a trojan horse, scan your computer with a free FortectIntego’s scan. For more information about Trojans, browse the database of Trojan parasites that is provided below.
Latest Trojan horses added to the database
Terminate Wacatac Trojan
Delete Trojan:Win32/CryptInject!ml
Terminate Csrss.exe virus
Additional information added on 2016-10-18