Uninstall COM surrogate virus (Jul 2017 updated) - Uninstall Guide
COM surrogate virus Removal Guide
Description of COM surrogate virus
How dangerous is COM Surrogate virus?
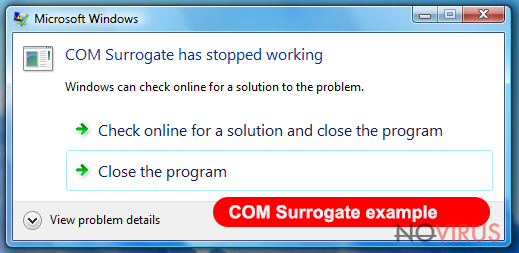
COM Surrogate virus might be the reason why your computer is slower than it used to be. Please, do NOT ignore such signs of malware because you can run into serious problems. Technically, this malicious program is a Trojan horse which can also be found as Dllhost.exe *32 COM Surrogate virus.
When inside the system, it tries to hide from its victim for as long as possible. However, the main aim of COM Surrogate trojan horse is to steal personal information about the victim and transfer it to its owners. The biggest danger is the full access to victim’s computer which could be achieved with the help of this trojan. There’s no doubt that you have to remove COM Surrogate from your computer and make sure you don't waste your time with that.
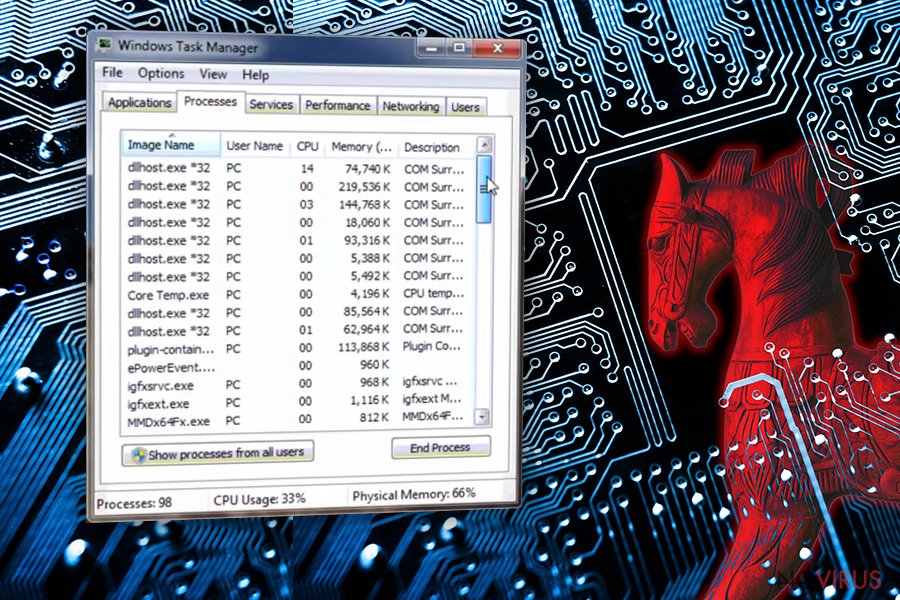
As we have already mentioned, sluggish computer’s performance should be the main sign for you showing that you are infected. Besides, you can also notice Windows notification titled as 'COM Surrogate has stopped working' and suspicious processes running in your Task Manager.
Talking about this virus, it's important to say that COM Surrogate is a real Windows file that is located in c:\windows\system32 or c:\winnt\system32 (the location might differ depending on Windows version). So, this file is not dangerous itself. In fact, it is a useful and helpful component that manages important processes, maintains the stability of computer’s performance, and protects it from crashing. However, this fact did not slip thru the eyes of hackers who decided to create COM Surrogate virus for their own needs.
Once the virus gets into the computer, it runs in the background of the system for as long as possible. It can install additional malware or steal your personal information. The most important thing is that you can't know the fact that you are infected because this malware hides under the name of legitimate process. For this reason, we highly recommend using professional malware removal tools to get rid of this virus. In this case, we recommend performing COM Surrogate removal on your computer with the help of FortectIntego.
How does it spread?
There is more than one way how COM Surrogate hijack might happen. The virus might spread via malicious websites. However, it is possible to get infected when visiting legitimate websites as well. In this case, they need to be hacked. Another method used for distribution of COM Surrogate trojan is infected emails.
Infected emails might contain malicious links or attachments that can be wrapped into nice words trying to convince users into downloading them to their systems. Finally, the virus might pretend to be another program and convince its victims that they are installing a necessary application on their computers.
As you can see, COM Surrogate virus has various ways used to trick users and sneak into target computer systems. Cyber security specialists have already warned people to stay away from suspicious websites and emails. Moreover, you should protect your computer by installing professional and reliable security program.
COM Surrogate removal from the system
Once you realise that the virus ended up on your computer, you should not hesitate and delete it as soon as possible. Reliable malware removal tools, such as FortectIntego or SpyHunter 5Combo Cleaner, can help you to remove COM Surrogate virus automatically. If you already have one of these programs, you should update it first and then run a full system scan. Automatic COM Surrogate removal ensures that virus, with all its components, is completely deleted from your PC.
How to prevent from getting trojans
A proper web browser and VPN tool can guarantee better safety
As online spying becomes an increasing problem, people are becoming more interested in how to protect their privacy. One way to increase your online security is to choose the most secure and private web browser. But if you want complete anonymity and security when surfing the web, you need Private Internet Access VPN service. This tool successfully reroutes traffic across different servers, so your IP address and location remain protected. It is also important that this tool is based on a strict no-log policy, so no data is collected and cannot be leaked or made available to first or third parties. If you want to feel safe on the internet, a combination of a secure web browser and a Private Internet Access VPN will help you.
Reduce the threat of viruses by backing up your data
Due to their own careless behavior, computer users can suffer various losses caused by cyber infections. Viruses can affect the functionality of the software or directly corrupt data on your system by encrypting it. These problems can disrupt the system and cause you to lose personal data permanently. There is no such threat if you have the latest backups, as you can easily recover lost data and get back to work.
It is recommended to update the backups in parallel each time the system is modified. This way, you will be able to access the latest saved data after an unexpected virus attack or system failure. By having the latest copies of important documents and projects, you will avoid serious inconveniences. File backups are especially useful if malware attacks your system unexpectedly. We recommend using the Data Recovery Pro program to restore the system.
