How to get rid of ransomware virus
Ransomware is a malicious computer software, which is used by cyber criminals to infect victim’s computer and block access to it or to encrypt data stored on it. Ransomware viruses ask to pay a ransom to unblock the computer or to restore the encrypted data.
Different viruses use different techniques to scare the victim and convince him or her to pay the ransom. Some of them provide no information at all, just an e-mail address to contact ransomware authors and ask for instructions on how to fix the computer, other viruses attempt to pose as programs created by legal authorities and meant to hunt down people who supposedly break laws.
The main aim of these computer viruses is to scare the victim by taking his/hers computer or data hostage, and some viruses even threaten the victim to publish private data online. First examples of ransomware were spotted a long time ago in Russia. During the 2015 and 2016, the number of ransomware variants and attacks has incredibly proliferated, making this computer virus one of the most fearsome cyber threats of all time.
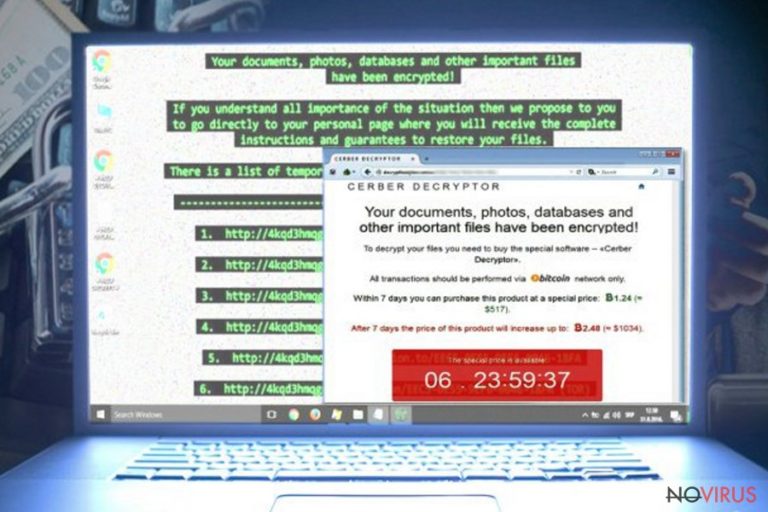
Examples of most widespread ransomware viruses
Locky ransomware. It is one of the most dangerous crypto-ransomware viruses. However, despite earning the name of the undefeatable crypto-ransomware virus, its authors have released several similar variants of it, including Bart ransomware and Zepto virus. This virus is distributed via deceptive email letters that contain .doc or .zip attachments. Typically, these files are named as invoices. If the victim fails to recognise a trickery and opens the JS file included in the .zip archive or allows Macros for malicious .doc file, the virus launches, and starts encrypting all victim’s files.
This virus is capable of encrypting data even on unmapped network shares. After encrypting all data, Locky creates and saves _Locky_recover_instructions.txt on the system, containing instructions on how to pay the payment and get Locky decryption software.
Your browser has been blocked virus. This ransomware variant does not encrypt victim’s files but prevents the user from accessing Internet browsers and triggers threatening messages, stating that the user has been caught watching or distributing prohibited content such as adult content, copyrighted software, and the like.
Typically, such menacing messages are designed to look like official messages from FBI, local police authorities, EUROPOL, or other well-known law-enforcement organisations. These messages urge the victim to pay a fine (ransom) to avoid going to jail. Instead of paying the ransom, the victim should remove this malware from the system.
FBI virus. This ransomware gets inside victim’s PC with the help of Trojan.LockScreen, and displays a lock screen, preventing the victim from accessing the PC. The virus shows scary-looking messages stating that the victim has broken several laws, for example, watched or distributed prohibited content, and might be sent to prison soon. These fake warnings ask the victim to pay a fine immediately to avoid jail sentence. Such hideous malware can be uninstalled using anti-malware software.
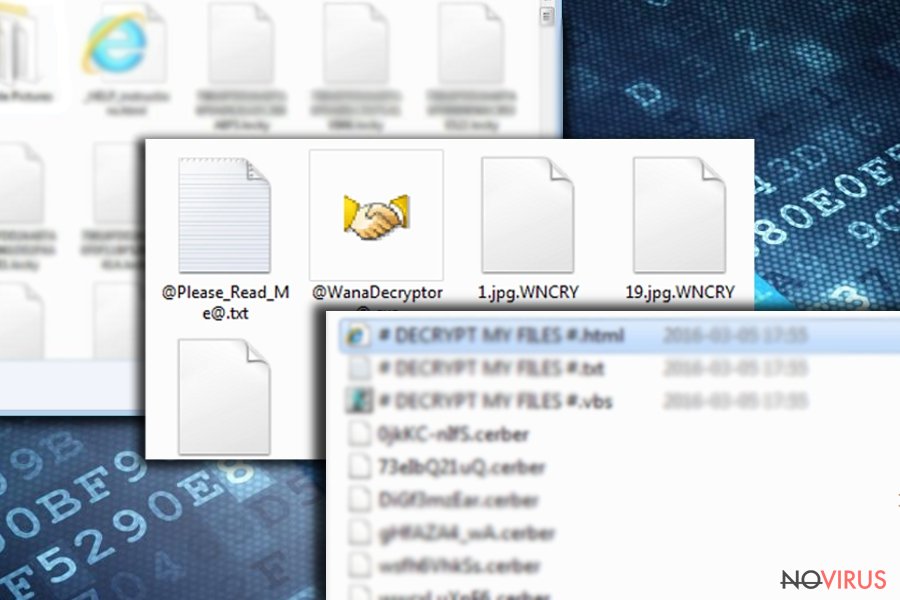
Modus operandi of ransomware
Different ransomware viruses use various techniques to blackmail the victim and force him or her to pay a ransom. Such infections can severely affect the computer system in order to convince the victim to pay up. After that, they ask the victim to pay the ransom either to a provided Bitcoin address or by buying Ukash, PaySafeCard, or MoneyPak payment methods. Below, we have listed most common activities of ransomware viruses to help you understand how such malware examples operate:
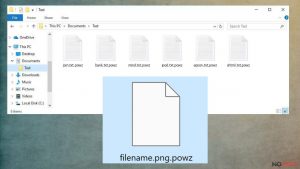
- The majority of ransomware viruses are programmed to find specific files on victim’s computer and encrypt them. Typically, they search for important documents, videos, databases, photos, music files, and other file types and encrypt them using a certain encryption system.
- Ransomware viruses can steal Bitcoins and valuable information from user’s computer and send them to their Command & Control servers.
- Ransomware can delete victim’s files. Typically, such viruses display a countdown clock showing how much time has left to pay the ransom, and remove a certain amount of victim’s files at fixed time intervals.
- Such viruses can terminate computer protection software and slow the entire system down, making it practically impossible to use it.
How are ransomware viruses distributed?
There are several methods used to distribute ransomware, and it seems that over the years they haven’t changed significantly. The most popular techniques cyber criminals use to spread this type of malware are these:
Malware-laden ads. Cybercriminals tend to target ad networks and infect them so they can distribute malicious software via them. Malicious ads can link the user to websites that contain particular exploit kit, capable of exploiting victim’s system vulnerabilities and infecting the computer with ransomware.
Malicious emails: This is probably the most popular method used to spread malware. Crooks craft safe-looking emails and append malicious attachments to them. Typically, such emails contain a convincing message inviting the victim to view some documents or read someone’s resume. When the victim opens such attachment, ransomware gets executed and immediately infects the system.
Trojan horses: Ransomware can be automatically downloaded to the system if it has been earlier compromised by a Trojan horse. Such threats tend to remain silent for a while and download more malicious files later on.

Should you pay the ransom and how to remove ransomware from the compromised computer?
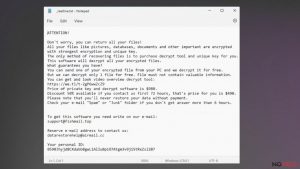
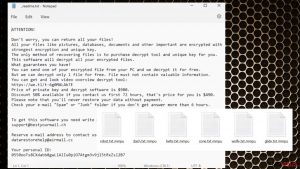
First of all, we would like to encourage all victims of ransomware NOT to pay the ransom. Paying the ransom will only fuel efforts of cyber criminals to continue malicious activities, create new ransomware projects, and affect more innocent people.
Besides, some ransomware authors are amateur programmers who fail to create working decryption tools, therefore, paying the ransom might not help you to recover the encrypted data using the decrypter they advertise. Files can always be retrieved from a backup, of course, in case the victim has one. Before plugging the device with data copies into the compromised computer, the user has to be sure that the ransomware is completely removed.
To remove ransomware virus, we suggest using automatic malware tool. We strongly recommend you not to try to uninstall ransomware virus manually, because it can be a hard thing to do even for an experienced IT expert. Besides, ransomware viruses do not provide uninstall feature, and that means that the victim needs to track down and remove each of virus components individually. Sometimes, ransomware viruses can try to block security programs, so in such case, the computer needs to be run in a Safe Mode first.
Latest ransomware viruses added to the database
Steps for removing Bozq ransomware
Uninstalling Powz ransomware
Mmpu ransomware removal tutorial
Additional information added on 2016-09-12