How to get rid of mac malware
Mac virus brings the real threat for your operating system
Computer virus is a piece of malicious code that is designed to perform some illegal activities on computers that it gets added to. Viruses can control or damage computer systems, use them as tools to attack other computers, use its resources, take victim’s files hostage and demand a ransom, and perform various other activities as well.
To put it shortly, the author of the virus decides what is the purpose of the virus. The virus can function entirely without the computer owner's knowledge. Computer viruses are extremely dangerous, especially because the majority of them hides deeply in the computer system and tends to hide their presence.
It is believed that Mac devices are immune to malware, and there are no cyber threats that can affect this operating system. Unfortunately, this is only a misconception and Mac virus is a real threat, not a myth.[1] Although, cyber threats are more targeting Windows devices, there are many reports about this particular type of malware that affects MacOS.[2] Recent years show that many malicious actors target devices that run the on MacOS specifically and those numbers increase.
The primary technique used to deliver such malware involves third-party application downloads and installation setups. Various plugins, extensions, and software like Adobe Reader, Java or Flash are needed for programs to launch properly. People get them from the internet and, in most cases, are not paying enough attention while installing or choosing the source. Getting questionable programs or plugins can put Mac's security into danger or even lead to cyber infections when you click on deceptive ads or download maliciously infected email attachments named “order information” or “invoice.”

There still are people who believe that Mac devices are safe and antivirus programs are useless on such machines, Mac viruses are real and there are various infections capable if spreading on MacOS even without users' permission or knowledge. Many social engineering attacks, scams or phishing campaigns target such systems especially.[3]
| Is Mac virus dangerous? | Yes. It becomes even more dangerous with every new campaign. It is a myth that MacOS is immune to malware |
|---|---|
| Distribution methods |
|
| Types |
|
| Popular examples | Mac Tonic; Mac Auto Fixer; Advanced Mac Cleaner; MacShiny; MacKeeper |
| Symptoms | Interrupted time online, system crashes and slowdowns; locked or even encrypted files, intrusive commercial content |
| Countries to get infected the most | USA, Germany, France, India, Russia, Chine, etc. |
Mac viruses are divided into different categories depending on their functionality
Mac viruses can come in all shapes and sizes and this not a new category of malware because it affects users' devices since 2006. There are many threats that affect all operating systems equally, in most cases, those are not that harmful or damaging as other specifically designed to infect MacOS.
Non-malicious software, which can pose a threat to the computer system if the user starts using their services carelessly:
- Browser hijackers;
- Adware (ad-supported programs);
- Rogue anti-spyware.
Dangerous computer viruses that can corrupt computer system install other malicious programs and initiate other illegal activities.
- Ransomware;
- Trojans;
- AOL parasites;
- Worms.
Viruses used to spy on the user; the rest of malicious/spyware related computer parasites.
- Sniffers;
- Network Management Tools;
- Remote Administration Tools;
- System Tools.
This list does not include other computer viruses that belong to several categories at once. Sometimes, computer parasites have several features that help to deceive anti-virus programs and avoid detection. It is no secret that cybercriminals do everything to keep their malicious tools on victims’ computers and continue to spy on the user, steal information, damage or control the computer entirely.
The first category of the lest dangerous threats like adware or hijackers includes potentially unwanted programs that are annoying and intrusive but not that damaging as other Mac viruses. However, such PUPs can enter the system without your permission or knowledge and alter browser settings by:
- changing the search engine, homepage, new tab preferences;
- altering startup programs;
- keeping from needed sites.
 Mac operating system is also prone to cyber infections, there is no need to believe that your Mac is immune to malware.
Mac operating system is also prone to cyber infections, there is no need to believe that your Mac is immune to malware.
Browser hijackers or adware are not that harmful, and people often ignore programs that focus on misleading promotional content or commercial material delivery. However, the time online is significantly diminished this way because when the user tries to search for anything on the affected web browser, he or she gets redirected to questionable pages. Unfortunately, those sites promote rogue tools or install applications automatically without users consent from one click on the pop-up or page visit.
Such installations and content related to advertisers can lead to malware infiltration like ransomware that is known for encrypting files and making them useless this way. Mac malware creators develop such threats that affect only MacOS devices and enter the system via insecure email messages. Various virus-related content gets attached to such emails as documents, files or executables.
When the malicious script gets triggered, ransomware can get on the system and start encryption processes.[4] For this file locking purpose, ransomware employs army-grade algorithms and marks encoded files with specific extensions. However, ransomware functions and particular features come with each virus. The most dangerous feature if such category is money extortion because ransomware demands cryptocurrency for the alleged data recovery.
The particular type of Mac virus – cryptocurrency miner
Cryptomining malware also involving the popular cryptocurrency, but in this case, there is no extortion purpose or direct contact between victims and criminals. This virus uses computers' resources and launches the process of mining currency. Illegal activity if mining Bitcoin, Litecoin, Monero, or Ethereum happens without users consent and knowledge. Threat infects the system and runs without causing any symptoms besides increased CPU usage or general slowness of the computer.
Cryptominers generally have two types of programs: crypto malware that runs on the machine and miners that mines cryptocurrency directly with the website. Once the user visits such a website, the power of their device gets used to mine the needed currency. The activity stops once the page is exited, and there is no direct malware involved. Users can employ particular internet security tools that can avoid visiting such pages or alert them once the malicious site is launched.
The malware designed to run on the computer launches the script directly on the device and then the process of mining the cryptocurrency can get launched. To stop such activity user needs to eliminate Mac virus itself, and the process requires an anti-malware tool that can find all associated programs or files.
 Malicious actors even design particular threats that only target mac devices with various processes like mining cryptocurrency.
Malicious actors even design particular threats that only target mac devices with various processes like mining cryptocurrency.
Unfortunately, there are much more than a few categories of Mac malware. Viruses developers can combine a few functions and launch a hybrid virus that shows misleading alerts, encrypts files and distributes other malware or runs processes on the machine. Mac virus that performs such unique features is even more challenging to remove than other threats mentioned before because such malware involves automatic reinstalls and other techniques used to ensure the persistence.
Various malware also has functions that allow them to disable antivirus functions or hide from detection tools. Monitoring antivirus software activity allows the malware to fake results of a system check. Antivirus may try to check for malicious files, but the virus launches an original and safe file instead and prevents the real detection from indicating the threat as dangerous.
Apple takes precautionary measures to protect from Mac viruses
Since Mac OS gets continuous updates and Apple ads security measures to the system to make devices more immune to Mac viruses. Gatekeeper is the main wall that defends Mac devices against viruses. Applications get declined if Apple doesn't approve them. This built-in scanner stops installations of the software and users need to have permissions to install third-party software on the machine.
Also, Mac devices have the Application Firewall technology that allows users to trust applications and decline others. Input and output connections get blocked when the necessary pre-set policy requirements of the Firewall are not fulfilled. File Quarantine or XProtect also defends the system from spyware and viruses as built-in antivirus software. Traditional anti-malware program scans the computer to find the malicious programs, XProtect is scanning downloads to check files against its database and make sure there is nothing malicious about it before the file gets launched.
Additionally, all applications that run on the Mac devices are sandboxed that means they are executed while preventing malicious scripts from distributing.[5] Users need to enter passwords and logins each time any application gets installed so rogue installation of software becomes more difficult.
 There is a need to have a reliable anti-malware program that can keep your Mac safe.
There is a need to have a reliable anti-malware program that can keep your Mac safe.
Mac malware developers use various methods to overcome the protection of Apple devices
Computer viruses are meant to be installed with or without user’s permission and knowledge, although in most cases the computer user unknowingly does something that allows the virus to enter the computer system. Viruses can be installed while sharing files with other computer users, browsing untrustworthy websites, downloading free files or programs to the system, opening the wrong emails and installing free applications with Default or Standard settings. To avoid malware attacks, follow these simple rules:
- Do not trust unknown people that send you emails, especially if these contain some attachments. Untrustworthy emails frequently contain some kind of malware. So please, stay away from Spam, Junk, Trash folders, but do not underestimate emails that reach your Inbox. Just because an email letter went to an inbox, it does not mean that it is safe to interact with it. If you do not know the sender, ignore such messages.
- Do not accept offers to install free software updates or “very useful programs” that you have never heard about. If you receive a pop-up saying that you must update Java, otherwise you will not be able to access certain content, do not rush to click “agree.” Java updates must be downloaded from safe sources only.
- Viruses can be installed manually, too. Make sure you always leave your PC in a safe place where no one can access it. Scammers can infect your computer just by plugging in a device that contains a malicious virus.
- Pirated programs, software cracks, and other suspicious downloads are frequently filled up with unnecessary components that can damage the computer system. Understand that free licensed software is something illegal and cybercriminals tend to take advantage of people who want to get full software versions for free. Do not break the laws or cybercriminals might damage your computer!
- Malware can also be installed by other viruses, most frequently – by Trojans. A Trojan horse can remain silent for weeks and then all of the sudden downloads a malicious program to the system.
- Viruses can be installed with the help of exploit kits, too. Exploit kits are hard to understand, but to put it simply, these tools are used to infect computers by exploiting vulnerabilities of Internet browsers, applications such as Java or Adobe Flash, and other software.
 MacOS can get infected by various programs belonging to Mac virus category. These activities even lead to privacy issues or identity theft.
MacOS can get infected by various programs belonging to Mac virus category. These activities even lead to privacy issues or identity theft.
Main purposes of Mac virus
Just like we have mentioned before, Mac viruses can perform many different functions. There are many more activities that malicious programs can initiate – the imaginary of cybercriminals cannot be measured in any way. Please understand that there are many more activities that malicious programs can start.
- Once installed, the Mac virus can add a malicious script to MBR and damage the computer system before the computer loads.
- It can also change hardware configuration, delete CMOS memory and damage BIOS. The computer that gets these settings adjusted in a bad way fails to function correctly, and specific data kept on the machine can be lost forever.
- Delete, corrupt, overwrite personal files. Despite the danger of data loss, you might also lose access to the computer. If the virus affects the wrong data, the computer might fail to boot.
- Download and install other malware examples, such as worms, trojans, backdoors, ransomware, and the like. Some viruses are designed to stay silently on compromised computers and show no signs of existence, but after some time, they download malware from a remote server and cause damage to the computer system.
- Use the compromised PC as a tool to distribute malicious programs further. Such viruses can use the computer’s resources and Internet connection and use numerous techniques to spread malware.
- Encrypt files and demand a ransom;
- Disguise malicious executive files and other components related to the virus as safe records and avoid detection;
- Slow down the operating system and cause other functionality and stability-related problems.
Steal personal information and use it for malevolent motives; - Create and save loads of useless files to clutter the computer’s memory;
- Corrupt reputable programs and make them corrupt every file as soon as it gets opened via the compromised application.
Tips for Mac virus elimination
Once Mac malware comes on the system, it can be found and removed from the machine. If the application is not harmful, but merely annoying and frustrating, you can end the unpleasant behaviour by uninstalling the software manually. However, dealing with cyber threats, it is important to clean the machine thoroughly so components of the malicious software can be deleted.
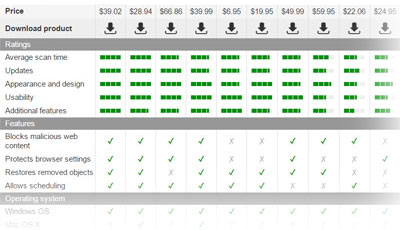
For that reason, you need to employ an anti-malware program and scan the system entirely. Unfortunately, antivirus tools also can fail to remove Mac virus because malicious actors keep changing their products. When the appliance you employ fails, you can provide us with the problem or question in the Ask us section of the page. We continue to provide you with the best solutions for virus removal.
- ^ Karen Haslam. Can macs get viruses & do Macs need antivirus software?. Macworld. News, tips, and reviews from Apple experts.
- ^ 5 types of malware currently affecting macOS. Tripwire. News, trends, insights.
- ^ Nicole Reineke. It’s Happened – Ransomware Now Affects Mac Computers. Unitrends. Blog.
- ^ Encryption. Wikipedia. The free encyclopedia.
- ^ Justin Pot. What is sandboxd, and Why Is It Running on my Mac?. Howtogeek. We explain technology.
Latest macOS malware in the database
Elimination of "Managed by your organization" virus
Terminate Searchmarquis.com
Calendar virus removal
Additional information added on 2019-05-17