Remove CrescentCore (Detailed Removal Instructions) - Virus Removal Instructions
CrescentCore Removal Guide
Description of CrescentCore
CrescentCore is a type of malware that typically spreads via fake Flash Player updates and installs PUP on Macs
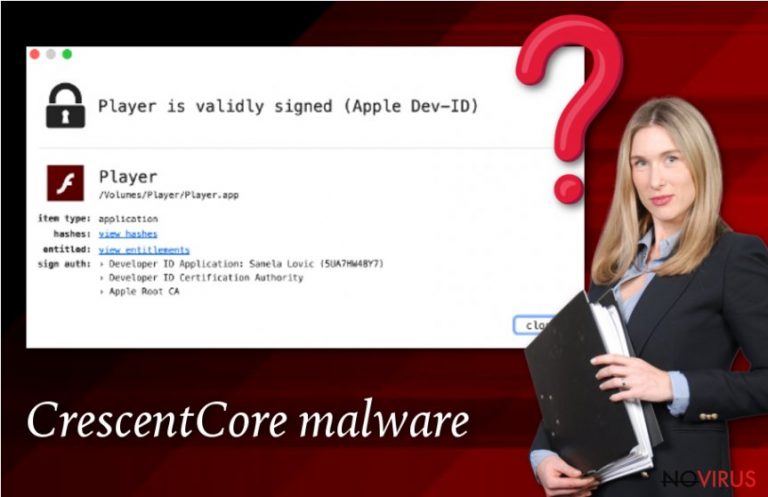
CrescentCore is a Trojan horse that was discovered by Intego security researchers in late June 2019, soon after they analysed similar malware samples. Also known as OSX/CrescentCore, the malware is designed for macOS systems, and its primary goal is to monetise on illegal installations of potentially unwanted applications, such as Advanced Mac Cleaner. CrescentCore virus is mostly spread via fake Flash Player installers that can be encountered across the web, although experts noted that it possesses by far more sophisticated capabilities than a regular Mac malware spread via this method.
| Name | CrescentCore |
| Alternative names | OSX/CrescentCore |
| Type | Mac virus, trojan |
| OS | macOS |
| Distribution | Fake Flash player updates, software cracks, pirated software installers, sites that offer to access licenced content for free |
| Dangers | As soon as CrescentCore is installed on a Mac, it renders it vulnerable to all types of threats, as it may install other malicious software that would not only infiltrate PUPs, but also other malware which can send spam, secretly mine cryptocurrency, steal login credentials and banking information, and expose the computer to vulnerabilities |
| Termination | Malware is known to install various components into systems which might prevent its manual removal. Therefore, you should employ reputable anti-malware software such as SpyHunter 5Combo Cleaner and perform a full system scan to get rid of it automatically |
| Mac optimization | In case your macOS is slow even after removing malware, you could use a space recovery app FortectIntego and get rid of duplicates, large files, and other data that might slow down your computer |
Fake Flash player installers are known to be one of the leading Mac malware attack vectors and bring in many different infections to the host machines – from adware that shows intrusive advertisements on the installed web browsers to malicious Trojans like OSX/Shlayer or OSX/CrescentCore.
To remove CrescentCore from a device and stop the intrusion of other malicious software, users need to install a powerful anti-malware software and thoroughly scan their machines. Note that the malware will not even infect systems that protected by a third-party anti-virus, so it is important to have the software running at all times to avoid CrescentCore virus and other malware infections in the future.
Infection and operation routine of CrescentCore Trojan
CrescentCore malware avoids analysis by checking whether it entered a virtual machine (VM) – it is often users by security researchers to analyse malware samples to avoid infecting actual computers they are working on. After the malware confirms that the machine belongs to a regular user, it also checks whether one of many popular third-party anti-viruses is installed on the system. If both checks do not pass, the CrescentCore virus simply exists without causing any damage.
In case of the opposite, CrescentCore will proceed with the infection process and will implant LaunchAgent components into a Mac, which improves its persistence. In other words, this is what can make manual CrescentCore removal so complicated, and many might fail even after trying to get rid of the fake Flash present on the system.
Once the necessary steps are completed on the infected macOS, users might not even notice the presence of malware, as it operates in the background. However, some symptoms might include:
- Computer slowdowns and lag, crashing apps;
- Unknown browser extension installed on Safari without permission;
- Malware apps like Advanced Mac Cleaner or Mac Mechanic present on the device;
- Web browser settings modified – new tab address, a customised search engine, and a new homepage applied without permission;
- Browser redirects lead to suspicious sites that are filled with advertisements;
- Ads appear on all visited websites.

Mac malware is not a myth, and CrescentCore is another virus that proves it
Security researchers from Intego noted that propagated rumour about Macs being somehow safer than Windows PCs is just a myth, as their security software managed to catch a variety of infections on machines running security software, including backdoors, cryptominers, and other Trojans:
Within the past month alone, there have been several new Mac malware campaigns aside from Intego’s discoveries of OSX/CrescentCore and OSX/Linker, including OSX/NewTab (which Intego was the first to detect), OSX/Netwire and OSX/Mokes (backdoors that spread via a Firefox zero-day vulnerability), OSX/LoudMiner aka OSX/BirdMiner (cryptocurrency miners that try to evade detection by running inside a virtualized operating system).
Security researchers from Kaspersky recently released a report about Mac malware that operates on machines running its security software, and it turned out that Shlayer Trojan was present on 10% of Macs. Due to its prevalence, CrescentCore might be another malware that could infect millions of users worldwide.
The infected macOS can cause various harm to its users, as threats like CrescentCore render machines vulnerable to other cyberattacks, and it is not a secret that malicious actors can often send the updates to already installed malware via Command and Control servers. The updated malware may be able to steal sensitive user data by logging keyboard inputs, direct users to spoofed banking sites, use the computer for sending spam, etc.
You can avoid malicious software on your Mac by employing basic security practices
Now that we established that Mac malware is not a myth, a natural question arises: how to defend yourself from computer parasites? The answer to the question is primitive but not as simple – you should be aware of how malware is distributed, so you can apply measures to defend yourself.
CrescentCore is typically spread via fake Flash Player prompts, that might include the actual installation of the software. Therefore, users may not even realise that they installed malware on their systems until it is detected by a security application or until they notice that something is very wrong with their machines.
It is important to note that Flash Player is an outdated piece of software that is full of security flaws, many of which are patched regularly by its developer Adobe. The truth is, many sites pulled of this plugin usage altogether, as most regular users do not require the functionality of Flash (unless they choose to play old Flash games on some dodgy sites, which is not recommended activity in the first place). In case you insist on having this flawed software, you should always install its updates via the official website. Note that you would never receive a notification about an outdated Flash – especially on Google Chrome, as it uses a built-in functionality to replace it.
Another critical point here is that most of these malicious links and download prompts are delivered to users via websites that host dubious content, including software cracks, pirated software, comics, games, or offers licenced TV show/movie streams allegedly for free. Please stay away from such sites as malware is often hidden on them.
Being careful is not enough, however, and you should also apply additional protection measures, such as anti-malware software, as well as ad-blocking extensions that would prevent malicious scripts from being executed in the first place.
Ways to remove CrescentCore malware
Without a doubt, the only secure way to remove CrescentCore virus is by employing reputable anti-malware software. However, keep in mind that the infection is relatively stealthy, and might avoid the detection by security software. Nevertheless, even with its various features, CrescentCore can be detected with the help of powerful security tools as they can find malicious files on Mac automatically. Keep in mind that advanced security solutions with real-time scanning feature would block malware altogether.
CrescentCore removal should also compile of web browser reset procedure, as it may introduce a malicious extension to Safari, and also alter web browser settings. Additionally, various potentially unwanted applications downloaded by the virus might also implant their own components into web browsers. To perform a browser reset, follow the instructions provided below.
Getting rid of CrescentCore. Follow these steps
Delete CrescentCore from Mozilla Firefox (FF)
Remove suspicious Firefox extensions:
- Open Mozilla Firefox browser and click on the three horizontal lines at the top-right to open the menu.
- Select Add-ons in the context menu.
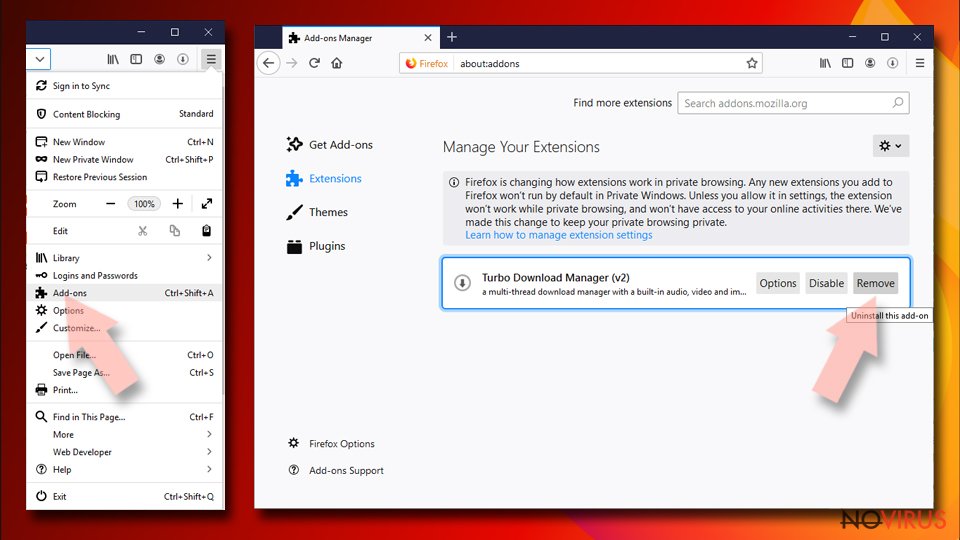
- Choose plugins that are creating issues and select Remove.
Reset the homepage on the browser:
- Click three horizontal lines at the top right corner.
- This time select Options.
- Under Home section, enter your preferred site for the homepage that will open every time you launch Mozilla Firefox.
Clear cookies and site data:
- Click Menu and pick Options.
- Find the Privacy & Security section.
- Scroll down to choose Cookies and Site Data.
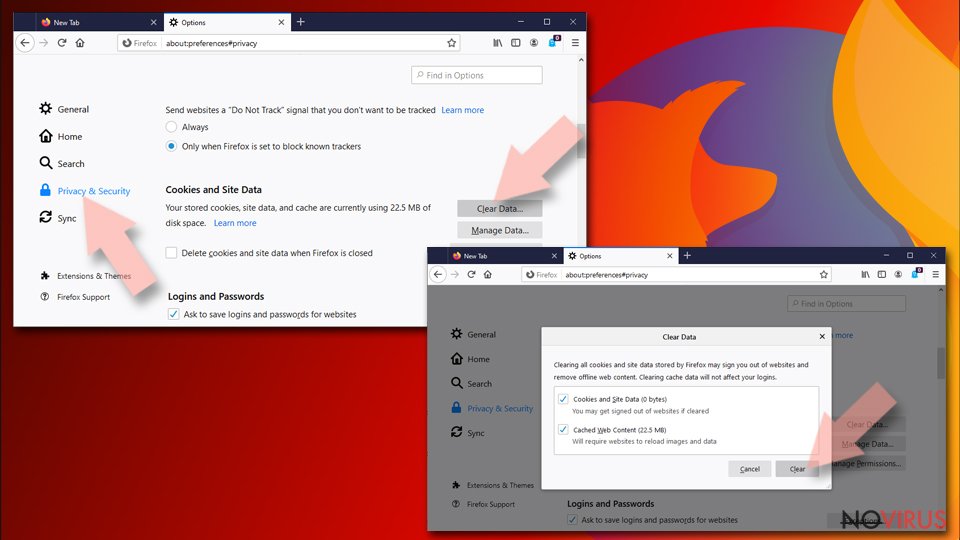
- Click on Clear Data… option.
- Click Cookies and Site Data, Cached Web Content and press Clear.
Reset Mozilla Firefox:
If none of the steps above helped you, reset Mozilla Firefox as follows:
- Open Mozilla Firefox and go to the menu.
- Click Help and then choose Troubleshooting Information.
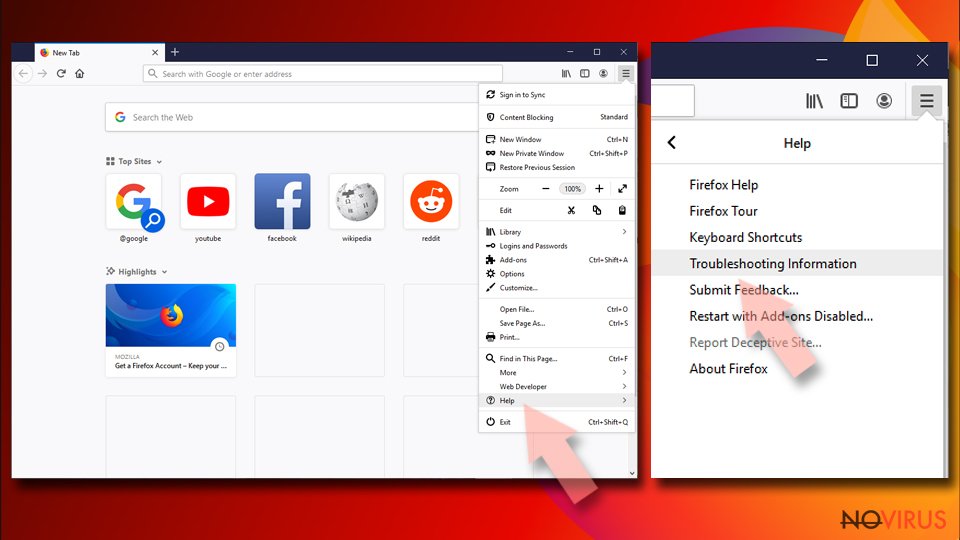
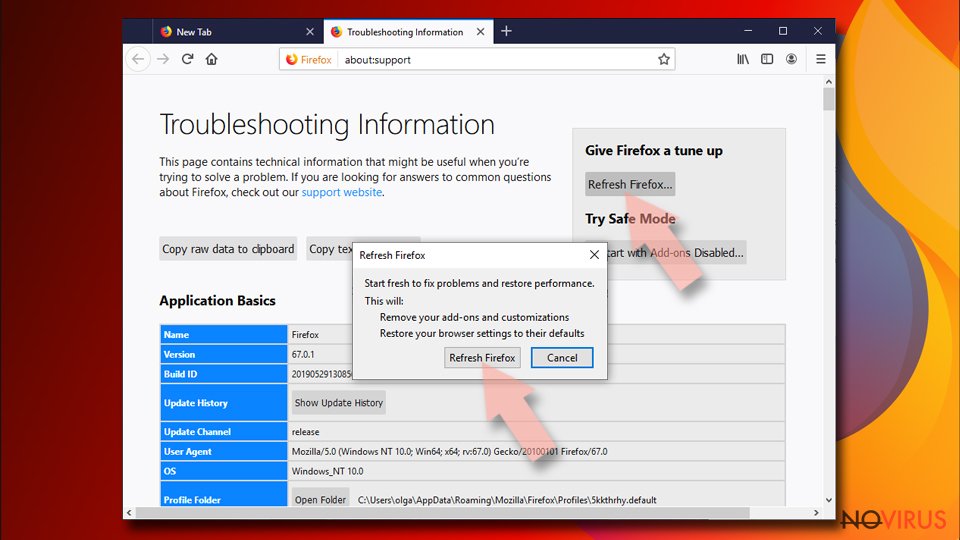
- Locate Give Firefox a tune-up section, click on Refresh Firefox…
- Confirm the action by pressing on Refresh Firefox on the pop-up.
Chrome browser reset
If you don't reset Google Chrome to default, the activity of CrescentCore virus may continue::
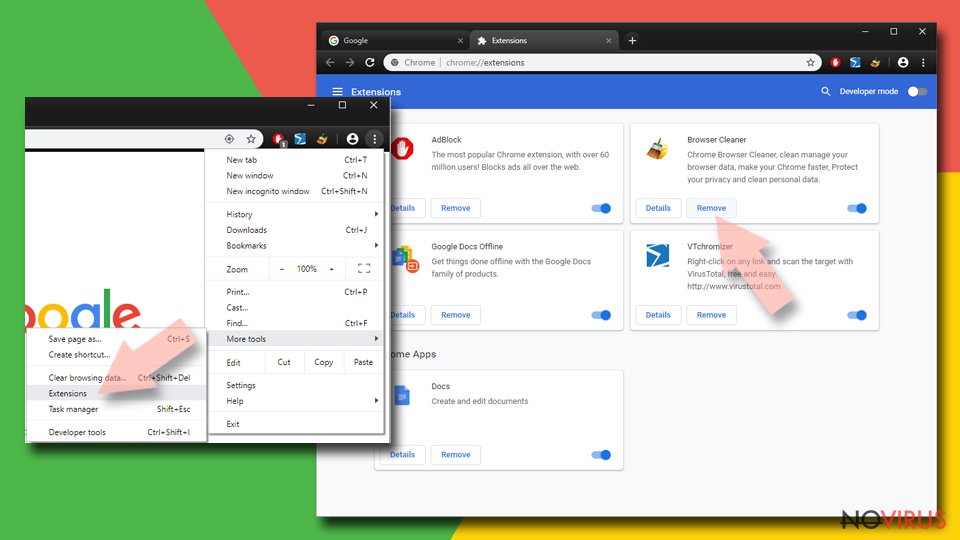
Find and remove suspicious extensions from Google Chrome:
- In Google Chrome, open the Menu by clicking three vertical dots at the top-right corner.
- Select More tools > Extensions.
- Once the window opens, you will see all the installed extensions.
- Find any suspicious add-ons related to any PUP.
- Uninstall them by clicking Remove.
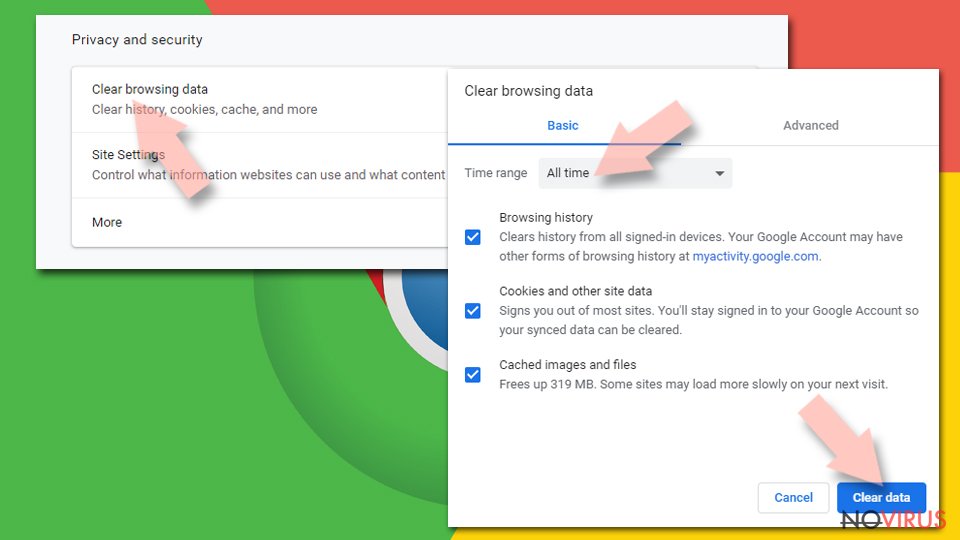
Clear cache and web data from Chrome:
- Click the Menu and select Settings.
- Find Privacy and security section.
- Choose Clear browsing data.
- Select Browsing history.
- Cookies and other site data, also Cached images and files.
- Click Clear data.
Alter settings of the homepage:
- Go to the menu and choose Settings.
- Find odd entries in the On startup section.
- Click on Open a specific or set of pages.
- Then click on three dots and look for the Remove option.
Reset Google Chrome fully:
You might need to reset Google Chrome and properly eliminate all the unwanted components:
- Go to Chrome Settings.
- Once there, scroll down to expand Advanced section.
- Scroll down to choose Reset and clean up.
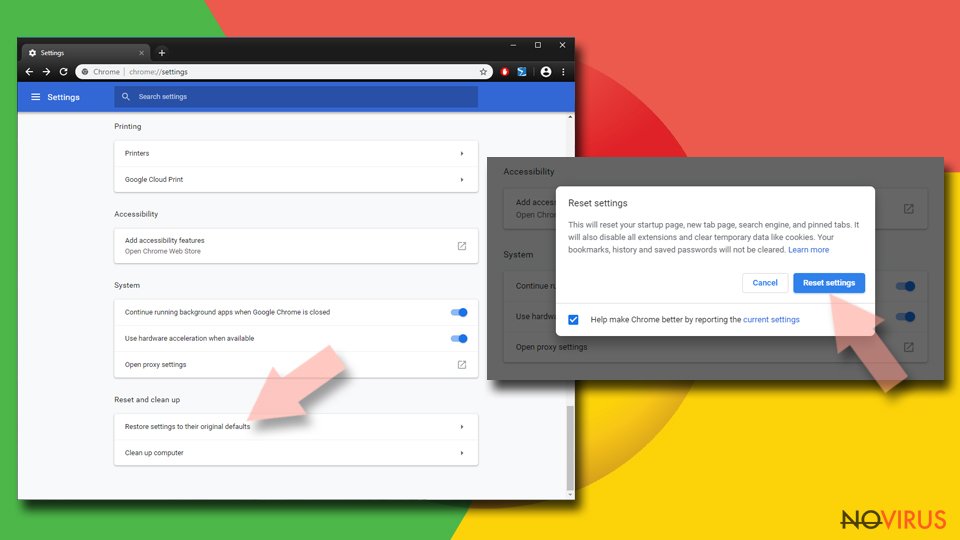
- Click Restore settings to their original defaults.
- Click Reset settings again.
Delete CrescentCore from Safari
CrescentCore malware might install a Safari extension without permission – reset your browser to eliminate it:
Get rid of questionable extensions from Safari:
- Click Safari.
- Then go to Preferences…
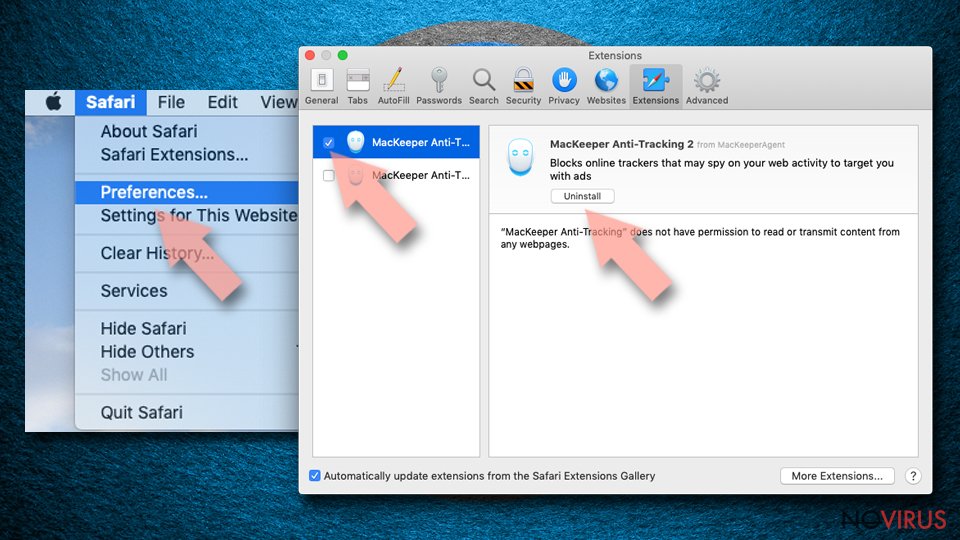
- Choose Extensions on the menu.
- Select the unwanted extension and then pick Uninstall.
Clear cookies from Safari:
- Click Safari.
- Choose Clear History…

- From the drop-down menu under Clear, find and pick all history.
- Confirm with Clear History.
Reset Safari fully:
- Click Safari and then Preferences…
- Choose the Advanced tab.
- Tick the Show Develop menu in the menu bar.
- From the menu bar, click Develop.
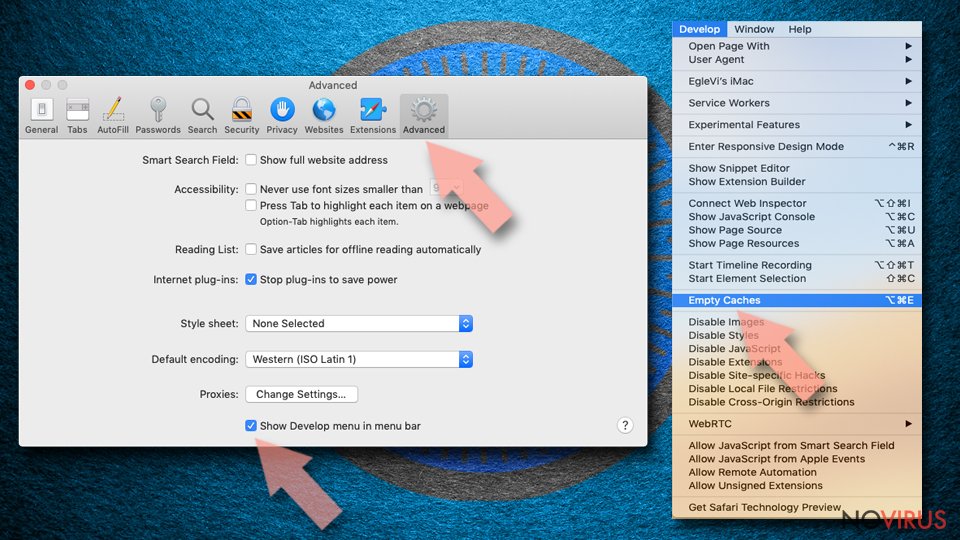
- Then select Empty Caches.
How to prevent from getting mac malware
Securely connect to your website wherever you are
Sometimes you may need to log in to a content management system or server more often, especially if you are actively working on a blog, website, or different project that needs constant maintenance or that requires frequent content updates or other changes. Avoiding this problem can be easy if you choose a dedicated/fixed IP address. It's a static IP address that only belongs to a specific device and does not change when you are in different locations.
VPN service providers such as Private Internet Access can help you with these settings. This tool can help you control your online reputation and successfully manage your projects wherever you are. It is important to prevent different IP addresses from connecting to your website. With a dedicated/fixed IP address, VPN service, and secure access to a content management system, your project will remain secure.
Recover files damaged by a dangerous malware attack
Despite the fact that there are various circumstances that can cause data to be lost on a system, including accidental deletion, the most common reason people lose photos, documents, videos, and other important data is the infection of malware.
Some malicious programs can delete files and prevent the software from running smoothly. However, there is a greater threat from the dangerous viruses that can encrypt documents, system files, and images. Ransomware-type viruses focus on encrypting data and restricting users’ access to files, so you can permanently lose personal data when you download such a virus to your computer.
The ability to unlock encrypted files is very limited, but some programs have a data recovery feature. In some cases, the Data Recovery Pro program can help recover at least some of the data that has been locked by a virus or other cyber infection.
