Remove Captcha-bros.com pop-up (fake) - Free Removal Instructions
Captcha-bros.com pop-up Removal Guide
Description of Captcha-bros.com ads
Captcha-bros.com is a site that tricks you into clicking on push notifications

Captcha-bros.com is the page that aims to get users' visits on the site or different domains which will then spam your device's screen to the point where it becomes difficult for users to see what they're doing. The potentially unwanted program catches unsuspecting victims in their web of deceit by luring them with pop-up ads, promotional content. Developers of PUPs while trying not to get caught, uses shady practices like deceptive material and misleading or scammy messages online.
Push notification sites and their developers have had a lot of trouble with fake accounts and security breaches, which is why they are on constant change. Creators make these pop-up sites every day, so when one gets caught and identified as dangerous, the new one gets created.
| Name | Captcha-bros.com |
|---|---|
| Type | Adware, PUP |
| Issues | Push notifications appear out of nowhere and trigger redirects to additional sites filled with malicious material |
| Danger level | Low, but ad-tracking issues can lead to more serious problems with the machine and privacy |
| Distribution | Sites, where software is promoted, can lead to direct installations of PUPs and other threats |
| Elimination | Anti-malware tools are needed for the proper threat removal process because pieces get hidden in various folders and files all over the machine |
| Repair | Infections can trigger unwanted changes, so tools like FortectIntego get created to repair files and functions damaged by the virus |
There are many security companies that work hard at finding these intruders in order to protect users from spammy ads as well as keep their own data secure. If you click “Allow” on this pop-up window you will get redirected to many other shady sites and push notifications keep coming to the screen when the particular browser is closed.
The annoying pop-up that triggers further intrusive content:
Press Allow to confirm that you are not a robot
It is advised to remove any threats as soon as they start to bother you. Make sure that there are no intruders on the machine by running the anti-malware tool immediately when you notice unwanted behavior. Apps like SpyHunter 5Combo Cleaner or Malwarebytes can help you achieve the best results while removing the PUP quickly.
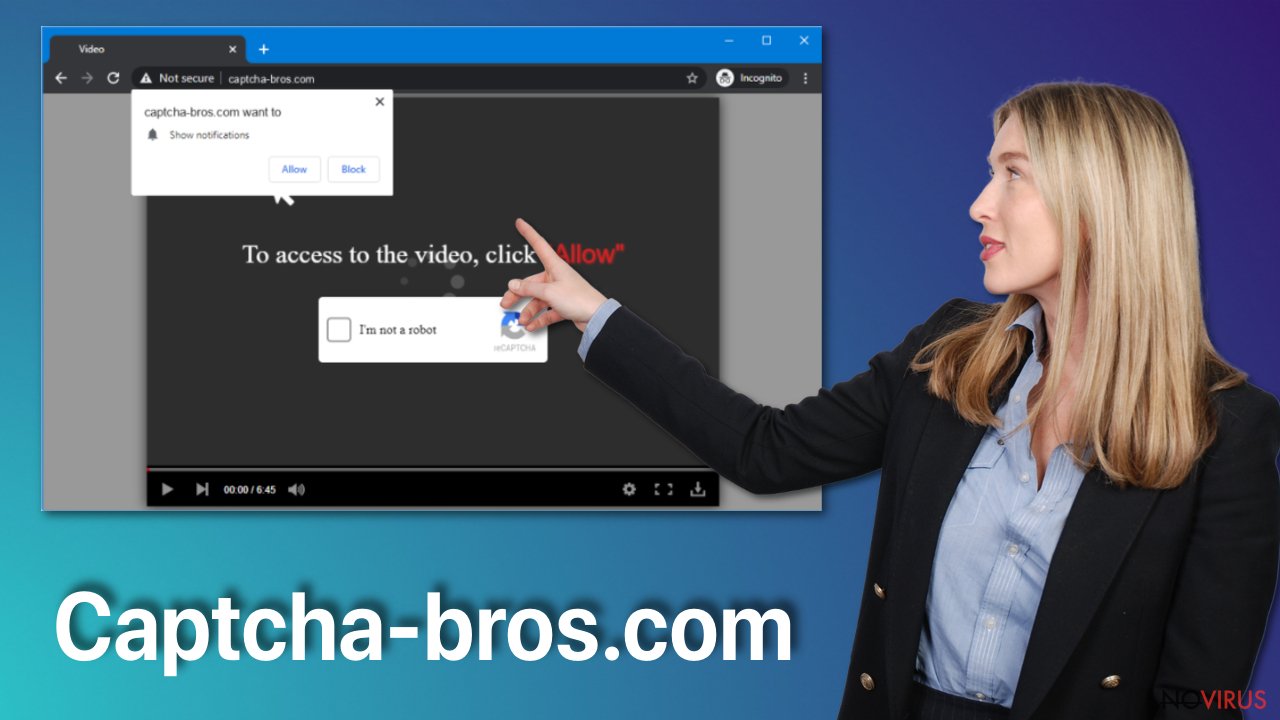
Captcha-bros.com website claims that human visitors have got a popup box when visiting the sites asking them the needed permission to allow notifications from the domain creators notifying about new posts, alerts. Enabling this additional content is not advisable. However, any interaction with the pop-up form can result in an agreement to get more pop-ups.
These intrusive and annoying advertisements delivered by a push notification browser feature are even more irritating when they reappear after the browser is closed. In order to eliminate this issue, one must go into their settings in order to remove it from websites that cause these symptoms. For a detailed explanation of how to do so, please scroll down for an explicit guide.
Eliminate extensions and applications from Google Chrome (desktop):
- Go to Menu on Google Chrome and choose Settings.
- Scroll down to Advanced.
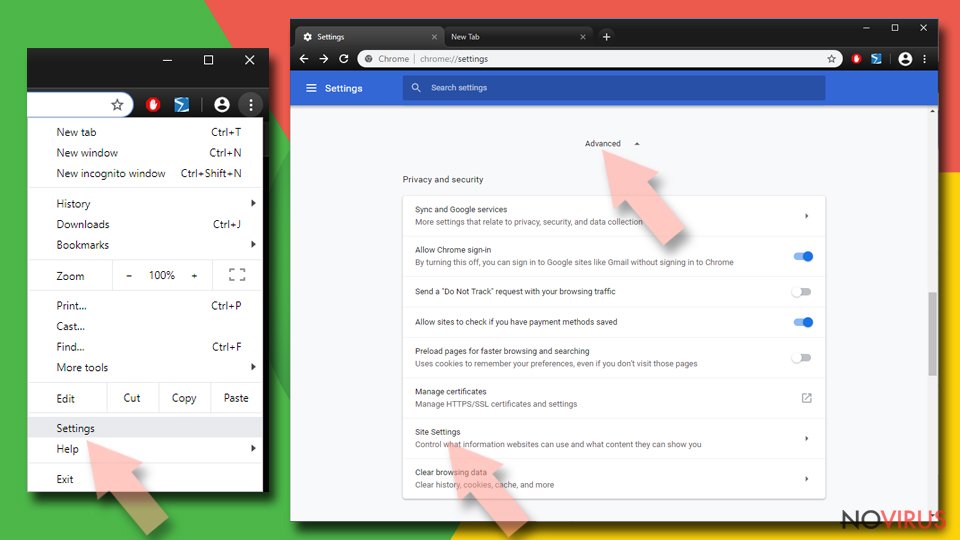
- Locate the Privacy and Security section.
- Choose Site Settings and go to Notifications.
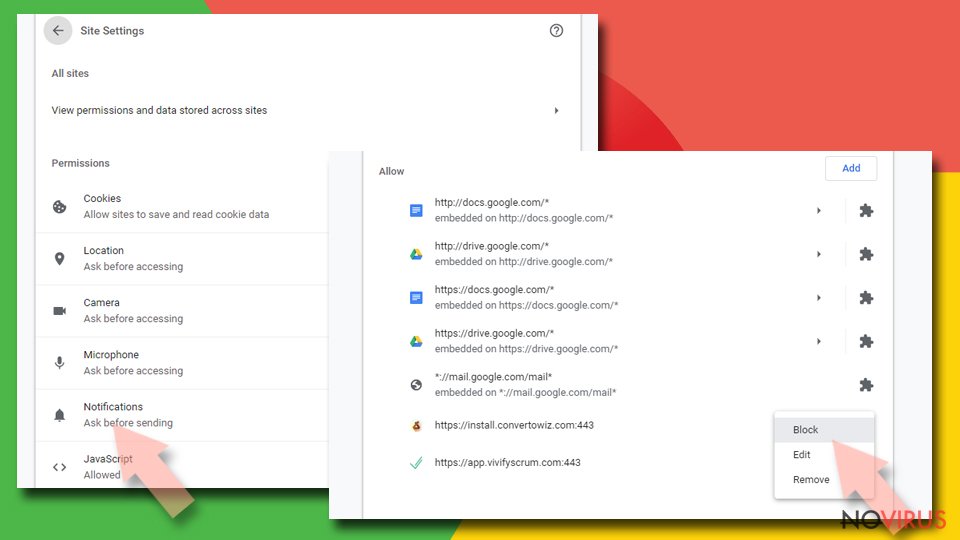
- Unwanted URLs can be found in Allow section if it annoys you.
- Click the three vertical dots next to the site and pick Block to remove unwanted notifications from Google Chrome.
Stop notifications from Google Chrome on Android:
- Open Google Chrome browser and tap on three vertical dots.
- Select Notifications.
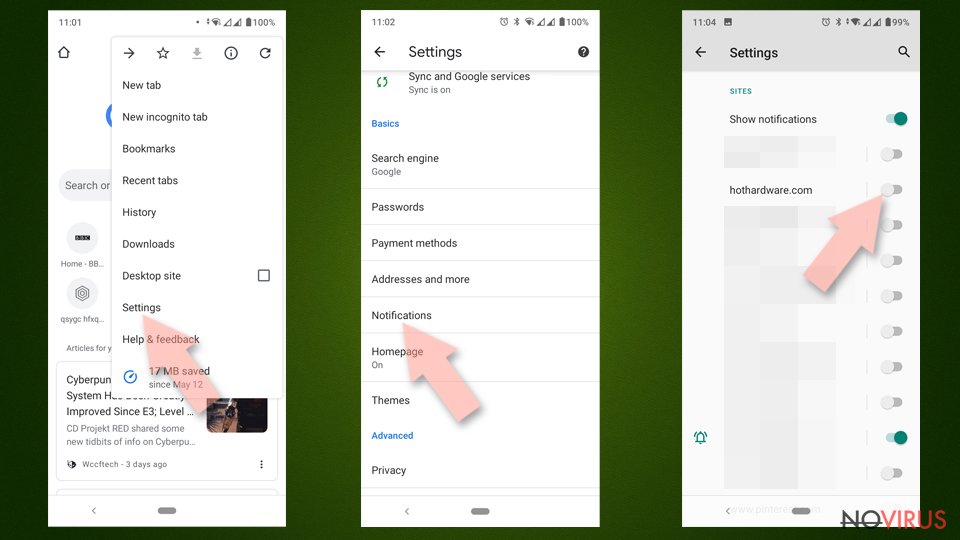
- Find Sites section.
- Locate the suspicious sites and toggle the button to the left to Off.
Remove suspicious notifications from Mozilla Firefox:
- Open Mozilla Firefox open the Menu > Options.
- Click on Privacy & Security section.
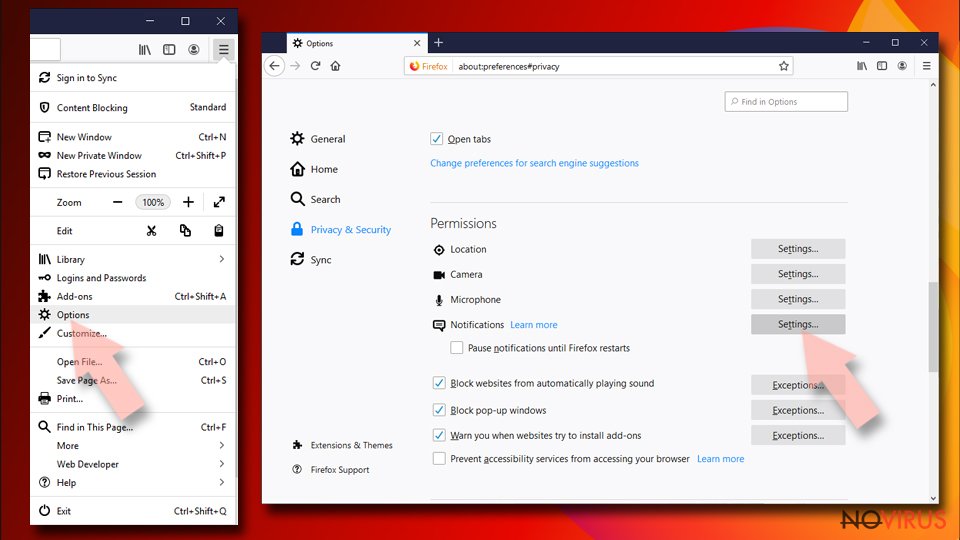
- In the Permissions section, you should see Notifications.
- Click Settings button next to it.
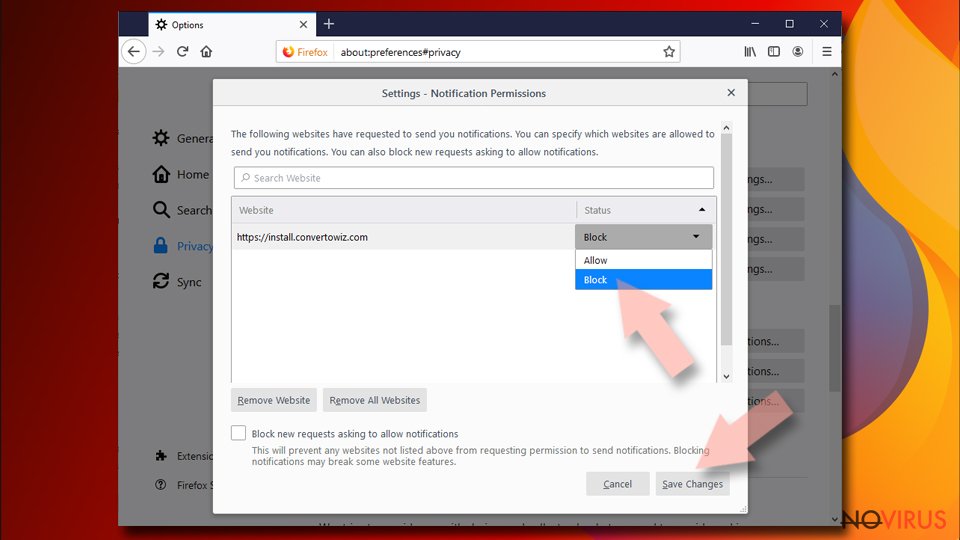
- Then on the Notification Permissions window, click on the drop-down menu by the suspicious address.
- Select Block and then click on Save Changes.
Reset notification settings on Safari:
- Click on Safari and then Preferences…
- Go to Websites tab.
- Under General, choose Notifications.
- Select the entry in question.
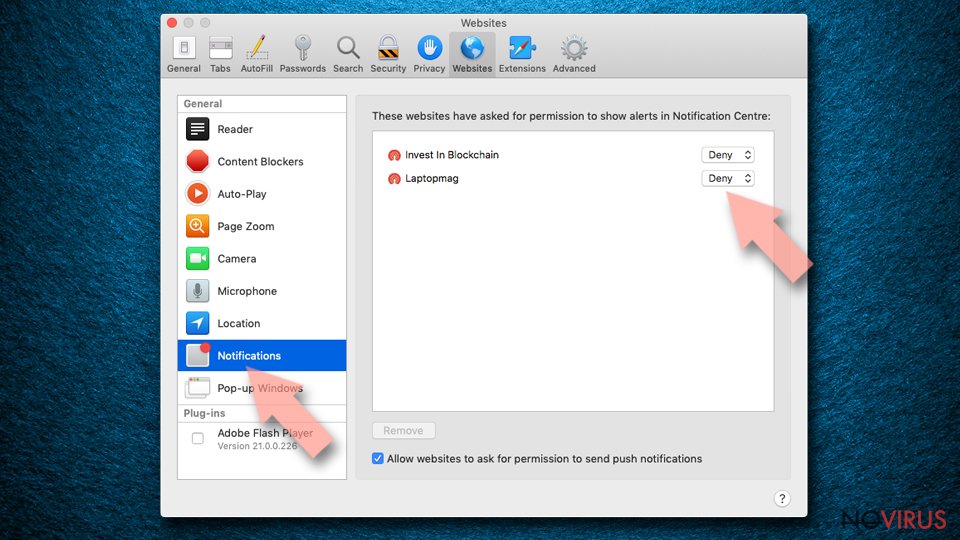
- Then choose Deny in the menu.
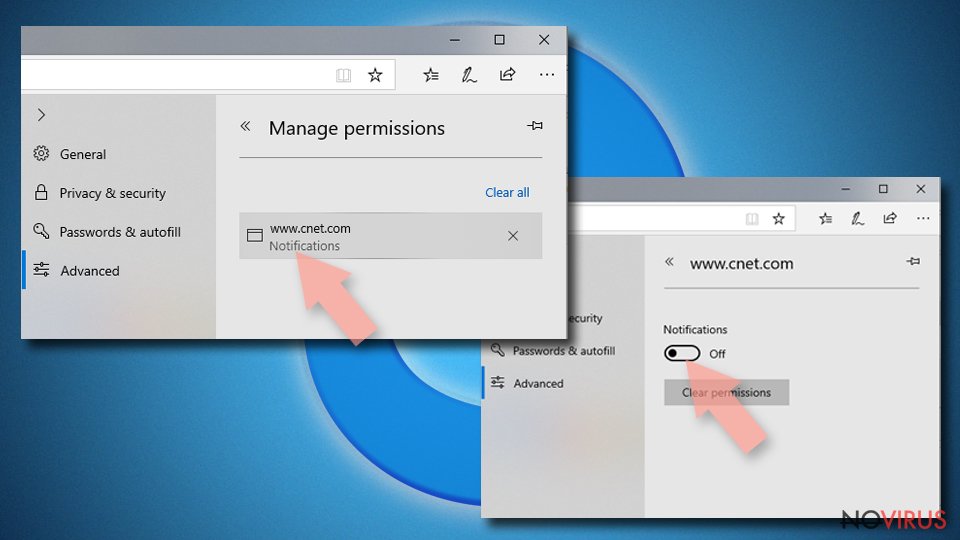
Remove unwanted notifications from MS Edge:
- Open Microsoft Edge and go to Settings.
- Select Settings and locate to Advanced.
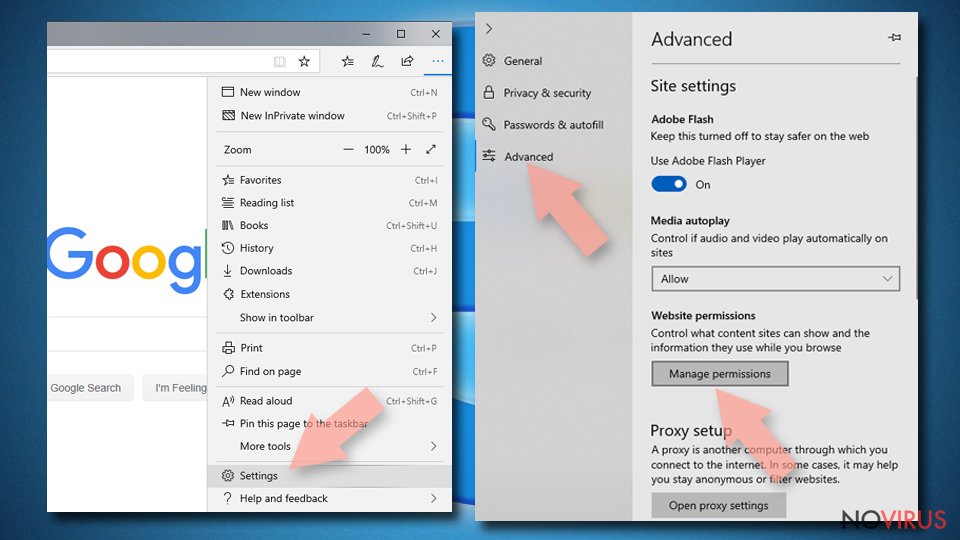
- Under Website permissions, find Manage permissions and select the unwanted site.
- Toggle the switch to turn notifications off on Microsoft Edge.
Eliminate unwanted notifications from MS Edge (Chromium):
- Open Microsoft Edge, and go to Settings.
- Find Site permissions.
- Locate Notifications on the right.
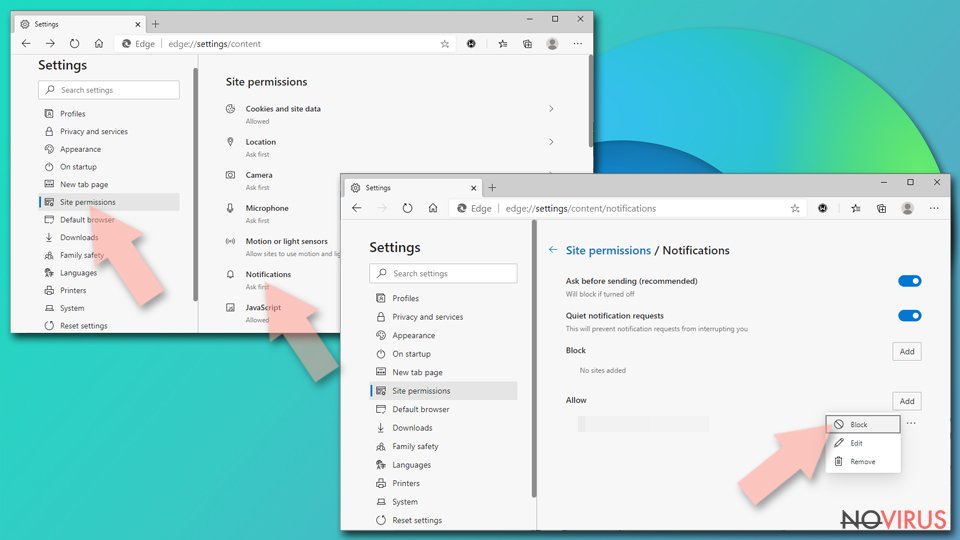
- Under Allow, find the unwanted entry.
- Click on More actions and choose Block.
Remove unwanted notifications from Internet Explorer:
- Open Internet Explorer browser.
- Find the Gear icon at the top-right on the window.
- Select Internet options in Settings and go to Privacy tab.
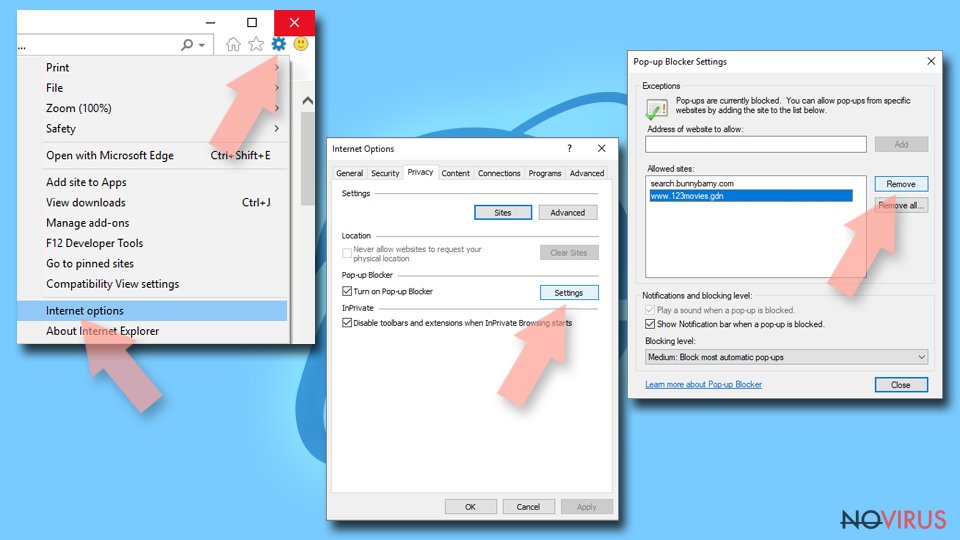
- Under the Pop-up Blocker section, click on Settings.
- Find the relevant URL under the Allowed sites and pick Remove.
Software bundling is a method often used by PUP developers
Software bundles are packages of programs that typically allow the purchaser to install multiple products without paying for individual licenses or downloading each program individually. The most common types are freeware versions of commercial software, which often come with malicious code embedded in them and end up infecting your computer when installed on it.
Pre-bundled software creates an easy target because these third-party distributors like torrent site developers and runners, offer downloads from their websites – usually untrustworthy ones at that! As soon as users find what they want on one of those sites, they download it right away without taking precautions like installing the new program step by step first. That's how hackers take advantage of users' skipping habits.
When it comes to downloading a program, people often overlook the other programs included in the package that are not necessary. This causes chaos for users as they may end up with unwanted software on their computer and cause system malfunctions. Furthermore, you should be careful when installing anything onto your device because of this risk factor.
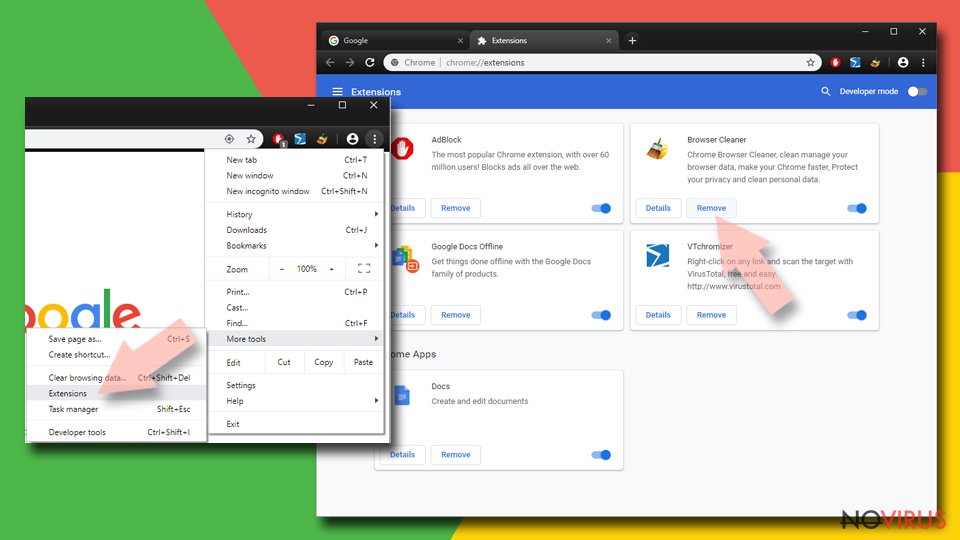
Find and remove suspicious extensions from Google Chrome:
- In Google Chrome, open the Menu by clicking three vertical dots at the top-right corner.
- Select More tools > Extensions.
- Once the window opens, you will see all the installed extensions.
- Find any suspicious add-ons related to any PUP.
- Uninstall them by clicking Remove.
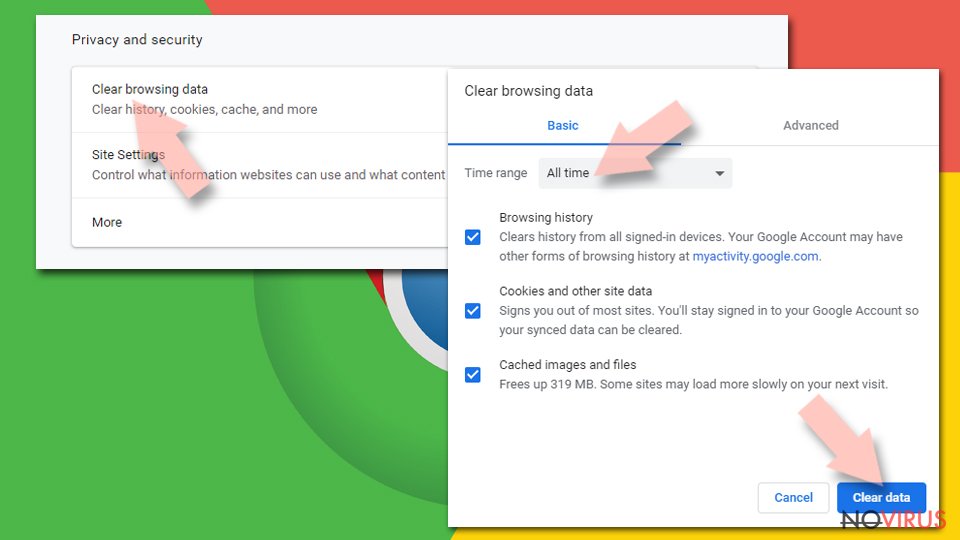
Clear cache and web data from Chrome:
- Click the Menu and select Settings.
- Find Privacy and security section.
- Choose Clear browsing data.
- Select Browsing history.
- Cookies and other site data, also Cached images and files.
- Click Clear data.
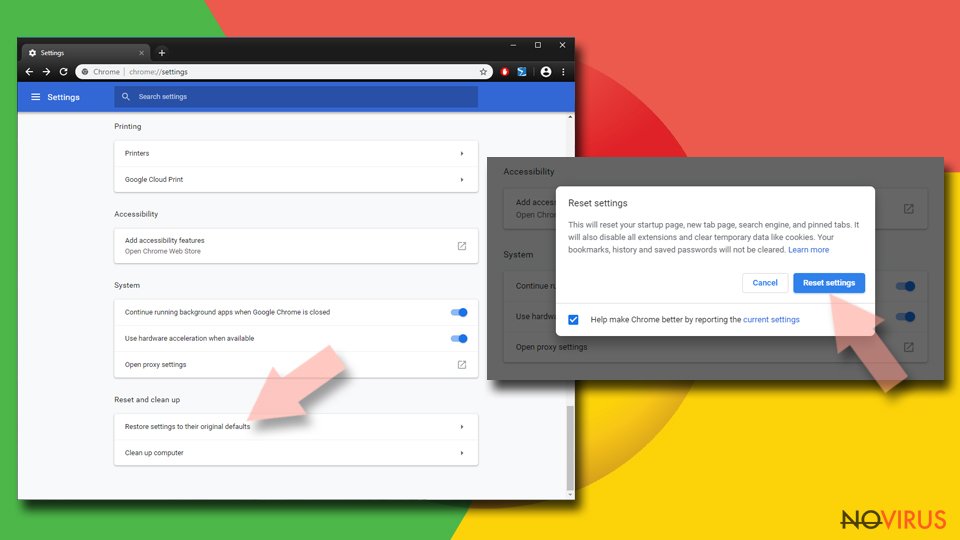
Reset Google Chrome fully:
You might need to reset Google Chrome and properly eliminate all the unwanted components:
- Go to Chrome Settings.
- Once there, scroll down to expand Advanced section.
- Scroll down to choose Reset and clean up.
- Click Restore settings to their original defaults.
- Click Reset settings again.
If you thought your computer was just a tool to browse the internet and do school work, think again. There are programs trying to get in through every crack they can find! This is because there are people out there that want access to all of our personal information; it's called spying.
Captcha-bros.com is not malicious, but creators can be related to malicious program distributors. PUPs might seem innocent at first glance, but these little pests will invade any room given half a chance often leaving no trace behind other than some data theft. You could be completely oblivious while this happens so don't underestimate them. Remove the intruder with SpyHunter 5Combo Cleaner or Malwarebytes as soon as possible and ensure that the machine is free of any cyber threats by double-checking.
How to prevent from getting adware
A proper web browser and VPN tool can guarantee better safety
As online spying becomes an increasing problem, people are becoming more interested in how to protect their privacy. One way to increase your online security is to choose the most secure and private web browser. But if you want complete anonymity and security when surfing the web, you need Private Internet Access VPN service. This tool successfully reroutes traffic across different servers, so your IP address and location remain protected. It is also important that this tool is based on a strict no-log policy, so no data is collected and cannot be leaked or made available to first or third parties. If you want to feel safe on the internet, a combination of a secure web browser and a Private Internet Access VPN will help you.
Recover files damaged by a dangerous malware attack
Despite the fact that there are various circumstances that can cause data to be lost on a system, including accidental deletion, the most common reason people lose photos, documents, videos, and other important data is the infection of malware.
Some malicious programs can delete files and prevent the software from running smoothly. However, there is a greater threat from the dangerous viruses that can encrypt documents, system files, and images. Ransomware-type viruses focus on encrypting data and restricting users’ access to files, so you can permanently lose personal data when you download such a virus to your computer.
The ability to unlock encrypted files is very limited, but some programs have a data recovery feature. In some cases, the Data Recovery Pro program can help recover at least some of the data that has been locked by a virus or other cyber infection.
