How to eliminate browser hijackers
Browser hijackers are suspicious programs that tend to operate silently. Although they do not belong to malware category, computer users find them annoying because they change browser settings without asking for user’s permission. In most cases, browser hijackers add a plug-in or an extension that alters homepage, new tab page, and default search engine preferences by replacing the previous value with a new URL. Just to let you know, browser hijackers are named after the URL that they set to appear in user’s web browser. In most cases, the websites that hijackers seek to promote are simply vague search engines that deliver customised search results, which are filled with paid third-party results. The problem with these search results is that they can be untrustworthy since the majority of browser-hijacker developers claim that they do not endorse content that third-party advertisers share on these websites.
Another problem that third-party links cause is web redirections. By using unknown and suspicious search engines, you risk clicking on a wrong spot or link, which is enough to get you redirected to a dangerous website. Web redirections can throw you on websites you might never want to visit, and part of them can pose a threat to your computer system. Besides, browser hijackers are known for their ability to collect personally non-identifiable data, such as your search queries, browsing history, IP address, geolocation of the PC, clicks on ads, and related information that reveals your browsing habits. Information browser hijackers collect is typically used for marketing purposes and in some cases is shared with third-party partners. However, not all computer users would be pleased to start receiving ads based on their recent search queries, especially if they are using a computer that is used by several individuals.
What exactly do browser hijackers do?
Browser hijackers can be used to perform various activities on user’s computer, and below you can find a list of them.
- Browser hijackers modify browser or even system settings in order to make computer user visit a predetermined website over and over again. In most cases, they promote a search engine that delivers customised search results the entire time. Besides, hijackers can add new bookmarks or new entries to the list of favourite websites without warning the user first.
- Collect personally non-identifiable information, which discloses user’s interests and browsing habits. For example, browser hijackers can track your search queries, visited websites, ads clicked, and similar information. Later on, it might use such information to display targeted advertisements to the user.
- Redirect the user to affiliate websites that might be untrustworthy. Since browser hijackers are meant to promote particular websites and drive web traffic to them, they can reroute the user to insecure Internet sites, too. In most cases, browser hijackers do not filter third-party websites they promote, so by keeping such potentially unwanted program on the system, the user risks visiting a dangerous website.
- Hide their presence. Browser hijackers are programs that typically do not provide uninstallers. Some of them alter browser shortcuts or add registry keys so removing suspicious programs and deleting vague browser add-ons do not necessarily help to solve the redirection problem.
- Slow the computer down, make the web browser lag, or even crash. Browser hijackers are not designed to improve browser’s or computer’s performance – they can only diminish it.
Typical methods of distribution
Browser hijackers are not malicious viruses and methods used to distribute them are not that aggressive. In most cases, browser hijackers are installed with user’s intervention, although without his or her knowledge. Below, we provide information about typical browser hijacker distribution techniques.
Ad-supported programs can display misleading pop-up messages asking you to install “recommended software” to improve your browser’s functionality and enhance the browsing experience. Do not agree to install such vague programs, especially if you have never heard their names in your life. What is worse, some adware programs might simply add these additional applications without your knowledge. In such case, programs that operate without your knowledge should be uninstalled as soon as possible.
Questionable official web pages. Some browser hijackers do have their official websites, which present the browser hijacker type application as the most reliable, useful, and unequalled tool that the user just needs to have in his/hers life. In reality, such tools hardly have any use and are meant to implement pay-per-click advertising plan.
Bogus software updates. If you like to browse the Internet a lot, most likely you will come across websites that display misleading advertisements. Untrustworthy ads often are official-looking, and urge the user to install a needed software update, fill the computer with missing system files, or other essential files. Such ads are untrustworthy and can trick you into installing a browser hijacker or even more dangerous program.
Finally, the most popular way to spread browser hijackers, as well as other potentially unwanted programs is to bundle them with other programs. Software bundles are individual programs that look completely normal; however, their installation wizards typically hide information about extra applications added to them. Such software packages can be decomposed via Advanced or Custom setup settings.
The most prevalent browser hijackers
Trovigo.com redirect. It is a strain of the infamous Trovi redirect virus, which changes browser settings and pushes the user to use the search engine that Trovigo.com site provides. Search results provided by this search engine might look normal, but clicking them can be dangerous. Trovigo seems to be focused on pay-per-click revenue generation, so its primary aim is to reroute you to predetermined third-party websites. It is highly recommended not to use Trovigo.com as the main search engine, and in case it appears in your browser without your knowledge, you should start looking for Trovigo.com removal guidelines.
Search.safefinder.info redirect. This program has been developed by Linkury and is associated with numerous other browser hijackers. Just like other typical browser hijackers, it replaces user’s homepage and expects the user to use the search engine it provides. Sadly, search results generated by this questionable search engine might open highly questionable websites for the user instead of those the user actually wants to visit. Search.safefinder.info removal is a quite challenging task, so we recommend computer users to use automatic spyware removal tool to remove Search.safefinder.info hijacker.
Startgo123.com redirect. Startgo123.com browser hijacker is one of those potentially unwanted programs that enter the computer system without user’s knowledge and make small, but important amendments there. Startgo123.com hijack affects all popular web browsers and makes them cause redirections to suspicious third-party pages whenever the user uses the Startgo123 search engine.
How to fix a computer that has been affected by a browser hijacker?
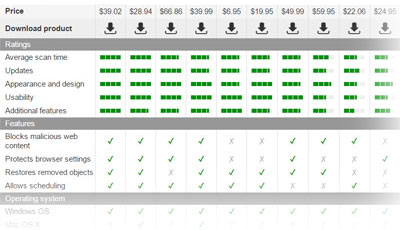
Browsers hijackers are quite simple programs, and it is not hard to remove them. Novirus.uk database contains hundreds of articles about various browser hijackers, and each of them contains informative removal instructions that every computer user can use for free. However, some browser hijackers are more complex, and they change registry key values, alter shortcuts and make other adjustments that are hard to notice. In such situation, the anti-spyware software comes in handy. You can use any anti-spyware software you like, but in case you do not have one, we recommend choosing either FortectIntego or SpyHunter 5Combo Cleaner.
Latest browser hijackers added to the database
Description of Trovi.com
Terminate weknow.ac virus
Elimination of Yahoo Redirect virus
Additional information added on 2016-10-19