Remove Wacatac Trojan (virus) - 2022 updated
Wacatac Trojan Removal Guide
Description of Wacatac Trojan
Wacatac is a malicious program that displays a warning about security issues or can be completely incorrect
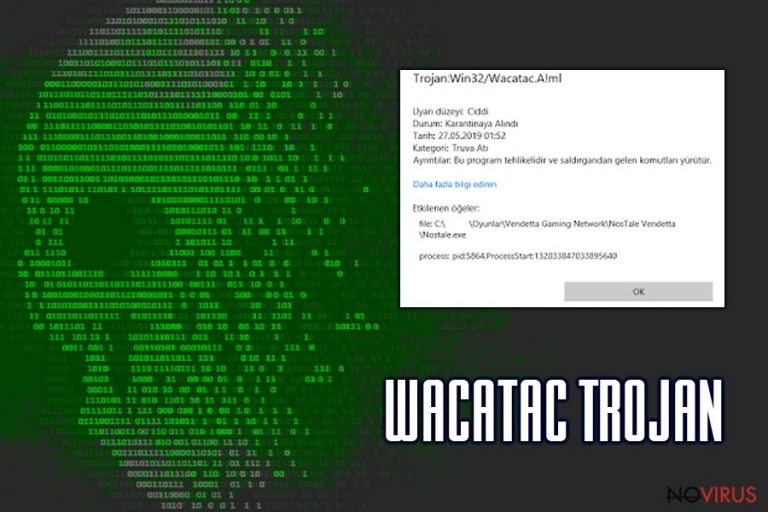
The Wacatac Trojan is a threat that can severely affect your computer system. A Trojan reduces the security of your device and can cause even more severe infections. As soon as this malware enters the system, it makes various changes and starts its malware activity immediately.
This malware's detection name is Trojan:Win32/Wacatac. Trojans usually enter devices through spam emails, f. e., attachments labelled “DHL Shipment Notification 3300777400-Delivery for 10 July 2019_pdf.gz” and similar. Nevertheless, victims can also infect their computers by downloading pirated software or visiting malicious websites with unsafe downloads. The Trojan spreads quickly through deceptive links and websites.
This particular malware is designed with a variety of features in mind and can cause significant problems and damage. The Wacatac Trojan may collect detailed information, such as passwords, usernames, bank details and other information, or data that may be used for subsequent fraud. It seems that in 2022 the trojan is spreading like a new wave as security professionals have discovered many campaigns and examples. It still shows chain infection features and spreads additional malware, such as ransomware, to infiltrate computers.
You may not even notice the symptoms of the infection, but the Wacatac detection names appear on the screen when the computer detects suspicious activity on the system. In this case, it is best to respond as quickly as possible and run a reliable antivirus program to clear all infections and completely stop the intruder, which can do a lot of damage to your device.
Detailed information about Wacatac Trojan
This type of malware can be extremely dangerous – it can collect personal information (login information, bank details, etc.) or help spread other malware (ransomware, RAT, and other dangerous infections). The worst part is that these processes run silently, and malware runs mostly in the background, so users often don’t notice something dangerous at first. In addition, infected devices can be included in a botnet and help carry out DDoS attacks against specific targets.
You should thoroughly inspect your device as soon as you receive an alert. Of course, it can also happen that the alert about a detected suspicious file is a false positive, so you won't need to remove any infection. However, read this article completely to learn about the possible symptoms and make sure you clean your device of any threats by running a reliable antivirus.
| Name | Wacatac |
| Type | Trojan, spyware |
| Related files | DHL Shipment Notification 3300777400-Delivery for 10 July 2019_pdf.gz, Unimpartial.exe |
| Related process | biddulphia9 |
| Infection means | Spam email attachments, although other methods can be used by hackers as well |
| Distribution | Typically reading using spam emails with malicious attachments or fake software and video game cracks |
| Risk factors | Infection of other malware, loss of money, identity theft |
| Symptoms | Rarely any. In some cases, users can experience high resource usage, program crashes, unknown processes running in the background |
| Termination | Employ reputable anti-malware software to see if there are any real threats on the computer |
| Repair | If the trojan runs for a while it can affect performance, functions, and other serious system files, so run FortectIntego to find and fix the virus damage |
If Trojan:Win32/Wacatac has been able to insert other cyber-parasites, you are likely to encounter frequent program crashes, slow device performance, BSoDs, higher numbers of internet ads, files, and programs that you don't remember downloading, etc.
Unfortunately, infecting devices with any malware, including this trojan, can have serious consequences. You could even lose money, infect your computer with other infections, experience identity theft, or face fraud. Silent, largely invisible parts of infections are often used as carriers of additional malware.
Therefore, you should make sure that your computer is virus-free, which you can do with a reliable security program with real-time protection features. In addition, you can use such tools to completely remove viruses. We recommend choosing trusted vendors such as Malwarebytes or SpyHunter 5Combo Cleaner.
Trojan.Script.Wacatac.B.ml detection
Detection of this trojan can also be a false-positive result, as users have reported that Microsoft Defender sometimes marks legitimate installers such as Thaiphoon Burner and Soulash video games. If this is the case for you, you should include an exception for the legitimate file. And if a threat has actually been detected, then you should remove Wacatac Trojan from your device as soon as possible.
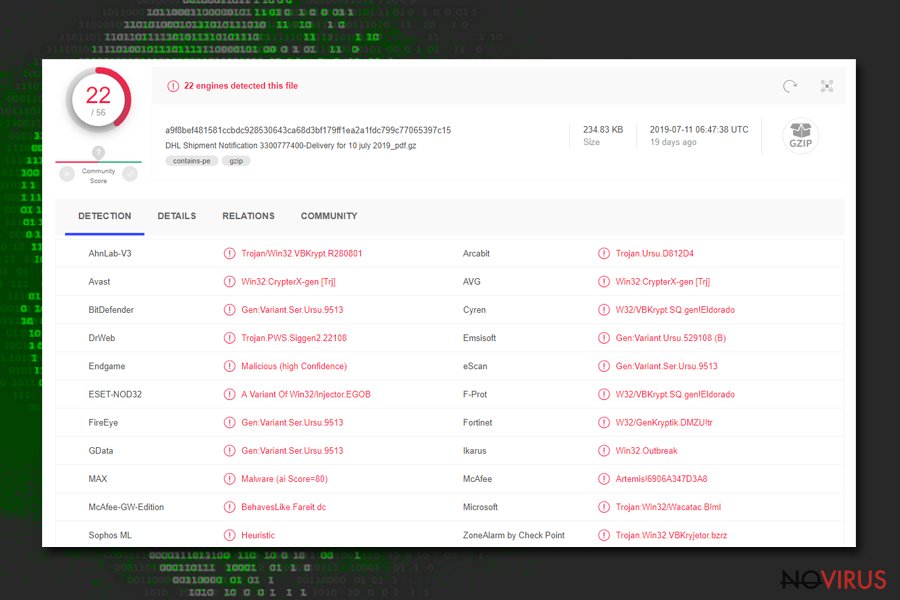
So how do you know if a virus has been detected and you have actually encountered a trojan? The best way to check if an alert for a detected threat is really wrong is to upload it to sources such as Virus Total. If the infection is real, you will be able to see its detection names from other vendors, such as:
- Win32:CrypterX-gen [Trj],
- A Variant Of Win32/Injector.EGOB,
- Artemis!6906A347D3A8,
- Gen:Variant.Ursu.529108 (B),
- Gen:Variant.Ser.Ursu.9513,
- Trojan.Win32.VBKryjetor.bzrz, etc.
Unfortunately, this is the only way to find out if you are infected with the Wacatac Trojan. In most cases, the actual infection is programmed so that it can hide its malignant activity in the background, which means you won’t notice any obvious symptoms of the infection.
The most common ways to distribute malware are malicious e-mail attachments
Malware developers are smart individuals who have chosen to use their skills for bad purposes. As a result, they typically use a variety of sophisticated methods to get the infections they develop to reach thousands of users. For example, they use fraudulent websites, exploit illegally downloaded programs, and the like.
However, perhaps the most common way to distribute malware is through spam. email attachments. Masked files attached to fraudulent emails can transmit the nastiest viruses such as ransomware or trojans. In most cases, consumers don’t even realize they’re trying to cheat because the message comes from a supposedly well-known company like DHL, Amazon, or Bank of America. Here's what one of the fake emails looks like. example mail:
Track DHL Express Shipment
Dear Customer,
Your email address was found on package with unclear delivery address as per DHL policy, we will not fail to return the package if it remain unclaimed within the next 48 hours.
Kindly review the receipt and make necessary steps if the package belongs to you to avoid loss of property.
Please Click and Download attached receipt to review the package details.Best Regards,
DHL TEAM
Copyright 2019
Obviously, email. the letter is not sent from a genuine DHL shipping company. Nevertheless, it’s hard to imagine how many people are actually waiting for a shipment from this carrier and may think the letter is genuine and then download the attached malicious attachment.
So never open a suspicious email. email attachments. If you are unsure whether a file is legitimate, you should always scan it with tools such as Virus Total before opening it.
Review any detected viruses and false positives before removing Wacatac
Before removing a trojan from your device, you must make sure that the warning you received is not false. As mentioned earlier, you should scan the file using another security program or use tools such as Virus Total. Once you are sure it is actually malicious, you should remove it immediately.
Although the Wacatac Trojan can be removed manually, it is not recommended for ordinary users who are not very knowledgeable about computer matters. A Trojan horse is a serious infection that changes the Windows operating system and affects key parts of it. Therefore, you should use a reliable antivirus program instead to stop the virus for you and restore normal system functions.
Keep in mind that a virus can interfere with or prevent a security program from working properly. If this happens, you should turn on safe mode first. Below you will find instructions to help you do this. And remember that you should remove the infection immediately and remove it as soon as possible to avoid further damage to your computer.
Getting rid of Wacatac Trojan. Follow these steps
Make sure to use anti-malware tool to terminate Wacatac Trojan virus
When you fall victim to a file-encrypting virus like this, it is best to rely on anti-malware programs and terminate the virus. Even though some of the cryptovirus-type threats are self-destructive and can destroy pieces of the infection after file encoding procedures, malware leaves scripts and active modules that can steal data and damage the machine further.
You should rely on Malwarebytes or SpyHunter 5Combo Cleaner since such applications can find and terminate various files related to the file-locker. Even those additional modules and other threats can be detected and removed from the system. Security programs can be used easily by various users that have no knowledge of computers and security.
Recovering affected system files
When ransomware and other viruses infect the machine, various processes get affected. Windows registry entries, other directories, databases of system files can get damaged or corrupted. Affected files can lead to additional system issues. Malware damage to such files triggers problems with performance and stability, security issues. Windows operating system recovery is needed then.
You should rely on proper tools that are designed to repair such files, recover smooth performance. FortectIntego is developed with the purpose to fix damaged files, repair processes, and remove other pieces of malware that get leftover. The program has a few engines and databases where needed Windows files can be found and repaired. This application also wan fix errors related to registry, damaged DLLs, and other system files. You can find links where you can download this PC repair tool, then:
- Click on the ReimageRepair.exe file.

- Choose Yes when the User Account Control (UAC) shows up.
- Press Install and wait for the installation process.
- The analysis of your machine with begin after the installation.
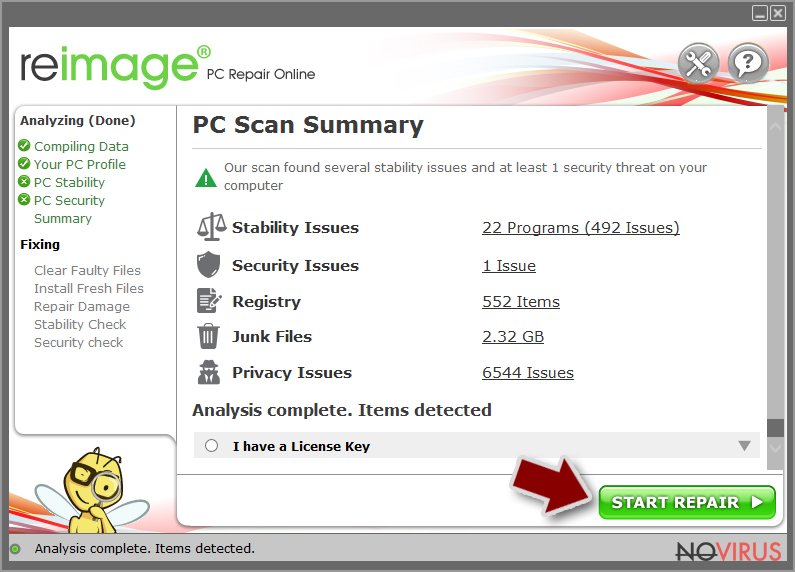
- Check the results listed in the Summary.
- You can choose each of the issues and fix them manually.
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.
Using FortectIntego can save a lot of time for you and improve the performance of the machine. Various issues can get fixed and system errors solved by running a thorough system scan and repair. You can avoid manual file repair that when done incorrectly can trigger more serious damage. Automatic system repair means that you do not need to reinstall the OS or different files.
How to prevent from getting trojans
Securely connect to your website wherever you are
Sometimes you may need to log in to a content management system or server more often, especially if you are actively working on a blog, website, or different project that needs constant maintenance or that requires frequent content updates or other changes. Avoiding this problem can be easy if you choose a dedicated/fixed IP address. It's a static IP address that only belongs to a specific device and does not change when you are in different locations.
VPN service providers such as Private Internet Access can help you with these settings. This tool can help you control your online reputation and successfully manage your projects wherever you are. It is important to prevent different IP addresses from connecting to your website. With a dedicated/fixed IP address, VPN service, and secure access to a content management system, your project will remain secure.
Recover files damaged by a dangerous malware attack
Despite the fact that there are various circumstances that can cause data to be lost on a system, including accidental deletion, the most common reason people lose photos, documents, videos, and other important data is the infection of malware.
Some malicious programs can delete files and prevent the software from running smoothly. However, there is a greater threat from the dangerous viruses that can encrypt documents, system files, and images. Ransomware-type viruses focus on encrypting data and restricting users’ access to files, so you can permanently lose personal data when you download such a virus to your computer.
The ability to unlock encrypted files is very limited, but some programs have a data recovery feature. In some cases, the Data Recovery Pro program can help recover at least some of the data that has been locked by a virus or other cyber infection.
