How to remove rogue antispyware program
Rogue anti-spyware is the term to define malware elimination utility which pretends to be a legitimate one. In some cases, it even contains malicious elements or facilitates viruses entering your device. Counterfeited security notifications and system errors are primary signs that your computer has become a haven for such unwanted tool. Alternatively, such applications frightens their users into purchasing the full version to eliminate fake malware and solve registry problems. In short, such tool is not as practical as it claims to be. Therefore, we recommend uninstalling rogue anti-spyware right away.
Developers of corrupted or fake anti-spyware utilities might be praised for their effort to disguise fake anti-spyware utilities in a veil of credibility. They do so by alerting users counterfeited messages about the damaged operating system. Frequently, the design of such tools creates an image of professionalism. In order to enlarge their number of customers, they offer additional features such as PC optimization, disk cleaning services, etc. Nonetheless, such characteristics should not be taken as real advantages. As a matter of fact, fake anti-spyware tools do not have their own malware database which makes them completely futile applications. They report about fake viruses, and once you obtain the full version, they seemingly eliminate those malicious elements. Users, who are not well-acquainted with the peculiarities of IT field, unfortunately, happen to be an easy target for felons.
Furthermore, the elimination of such programs should not be delayed. While these applications inhabit your operating system, they are likely to facilitate other unnecessary and fraudulent elements entering the device. Additionally, due to their covert operation, the number of system vulnerabilities might increase. In that case, your device becomes more vulnerable to severe threats. Note that rogue anti-spyware application may have a negative impact on the system as well. By interfering with daily processes and reducing CPU capacity, the device underperforms. As amusing as may it sound, you can remove such programs with real security applications.
The distribution peculiarities of rogue anti-spyware
While some samples of this category can be directly downloaded from their official web pages, frequently they settle on the operating system without users‘ direct permission. Here are some prevalent ways how such programs may appear on your device:
• Malvertising. Obviously, a newly created PC optimization has to advance into frequently visited web pages in order to boost its chances of getting downloaded. Racketeers use an alternative way to promote their products – pop-up advertisements. Likewise, you might notice such advertisements in questionable websites. Such pay-per-click commercial offers get highly annoying as flickering pop-ups constantly remind you to scan the device.
• Corrupted email attachments. Another form of malvertising comes in the form of attached file attachments. Most likely, you might accidentally download a rogue anti-spyware tool if you carelessly review your spam emails. If you are too curious and open every attachment of received spam, the chances to accidentally install rogue anti-spyware applications highly rocket. Keep in mind that such ominous and destructive threats as ransomware also prefer spreading via spam messages.
• Alternative malware. In fewer cases, such PC optimization tools might appear on your computer as a result of malware infection. In this regard, trojans, and computer worms mediate and accelerate the process of installing questionable applications on the system. One of the most bothersome features of such infections is its ability to disguise own processes. Likewise, finding the cause of suspicious behavior might not be an easy task. Such disguise expands the probabilities to operate on the device longer and, thus, wreak more havoc.
How do such programs operate?
As we have already discussed, these programs create fake notifications to manipulate users according to racketeers’ liking. Alternatively, in rarer cases, rogue anti-spyware programs might install adware or malicious elements and then remove them as soon as you purchase the full version. Besides this activity, the application affects other system processes.
• Shutting down legitimate security software and web pages. After you install a questionable anti-spyware utility, you might notice messages asking you to turn off your anti-virus utility because the former application cannot function efficiently. Alternatively, more aggressive variations might shut down the legitimate security applications by themselves. As a result, you are exposed to Internet threats.
• Displaying aggravating messages. Get prepared for numerous pesky and continuously emerging messages alerting you of the state of the device. Continuous notifications of hundreds of unsolved system errors and potentially damaging files residing on the computer might make even the most patient user lose his or her temper. Older or more credulous users, who worry about the privacy and security of the device, might rush to buy the promoted version even without questioning the credibility of such messages.
• Redirecting to the official website or alternative domains. Such phenomenon might cause irksome effects as well. Since the very programs are not trustful so are the web pages you might get redirected to. Rarely, they become havens for troublesome elements and viruses.
Prevalent types of rogue anti-spyware programs
System tools. These applications dominate the market of questionable security applications. In fact, hundreds of them can be found in thousands of users’ computers. They are convinced that such utilities monitor the performance of the device by solving registry issues by boosting the general performance of the device. Such tools gained popularity in 2010. Within a while, as people grew more aware of the true essence of such programs, they lost their appeal.
Security defenders. Interestingly, some of these utilities pose elimination difficulties. Some security defenders do not possess an uninstall function. These utilities became popular quite soon at the same time as system tools. Make a rush to remove such program as it may expose your technical information of the device to the developers of security defenders. As a consequence, the collection of technical details happens to be a valuable piece of data for developing more fraudulent tools.
Removing rogue anti-spyware – mission possible?
The very process is not difficult if you shift to using legitimate and proven anti-spyware programs, for example, FortectIntego or Malwarebytes. In order to detect all components of a rogue anti-spyware application, enter Safe Mode with Networking. Launch a security application to remove unwanted and corrupted tools. If you encounter difficulties downloading and opening it, USB and other portable data storage devices might be of help. Place the executable in the device and then transfer to the affected computer. If the downloaded corrupted program terminated your previous anti-virus app, changing its name of executable might help empower it again.
Latest rogues added to the database
Steps for removing Bozq ransomware
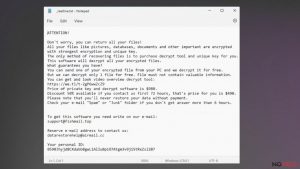
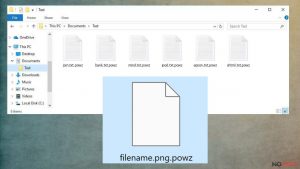
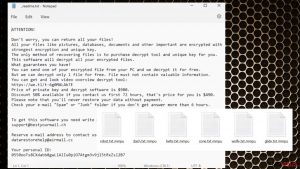
Uninstalling Powz ransomware
Mmpu ransomware removal tutorial
Additional information added on 2017-02-09