How to get rid of system tools
When discussing system tools, we should draw a fine line between the legitimate programs and the malicious ones. It goes without saying that users download the legitimate system tools to help them with various day-to-day tasks, be it enhancement of the computer’s performance, improvement of the Internet browsing capabilities or the repair of particular system errors. Such tools are distributed by the established and reliable companies which invest a considerable amount of effort, money and time in making these programs as functional and simple to use as possible.
As you can probably suspect, the situation with rogue system assistants is quite the opposite. These tools are designed for purposes that do not even come close to being at least remotely beneficial to the user. In fact, rogue system tools might sometimes be as aggressive as legitimate cyber infections, viruses or malware. That is why the experts deem such programs as potentially unwanted and strongly suggest staying away from them, and if they are already taken hold of the system — removing them immediately. Otherwise, the malicious system tools may trigger numerous unpleasant problems which may vary depending on the fierceness of the program. Some of the malware may influence your system’s performance, making your computer unusually sluggish, others can initiate fake system scans and generate misleading notifications about the system’s condition. Finally, they may also affect your browsing quality, by randomly redirecting you to unfamiliar domains and dropping annoying pop-up ads on every single Internet site you visit.
In this article, we will take a closer look at the latter category of the system tools and try to define what specific types of rogue programs there are as well as how to recognize and remove these undesirable guests from an infected device. We will also discuss the most common strategies used for distributing these fraudulent tools around and provide several examples of the questionable software that should be avoided.

Three basic categories of rogue system tools
Though malware is highly unpredictable — its forms and working principles constantly vary — the experts distinguish three main types of rogue system tools: corrupt PC optimizers, scareware, and fake search engines. Let us discuss these categories one-by-one.
- PC optimizers have never been popular among the computer specialists, but regular users, who are less competent in computing, are always looking for tools that can help speed up the PC, clean it from junk files or automatically perform other functions that the user is unable to accomplish manually. Corrupt PC optimizers also offer all these useful functionalities, sadly, they often fail to execute them. Instead, they scan the PC and report minor or completely non-existent problems, pushing the user to purchase a premium version of the program to fix them. By purchasing such tools, you are simply wasting money, because they are not built to improve your computer in the first place.
- Scareware works similarly to PC optimizers. It may also lie to you about your computer’s “critical” state and try to persuade you that the only way to repair it is by purchasing some questionable software or trusting your device to a remote technician. Neither of these methods help solve the issues because the main issue is the program itself. Once you remove it from your PC, all the warning notifications simply disappear.
- Most of us are probably used to think of search engines as providers of a reliable source of information. Unfortunately, it is not always so. Some search providers may be affiliated with suspicious third-parties and try to promote their products and services through the search results. Such search engines are considered deceptive and dangerous because they may easily lead users to shady websites and give way to additional malware infiltration.
How are the malicious system tools distributed?
Probably the most dangerous aspect of the rogue system tools is that they barely differ from the legitimate applications. Identically to the reputable tools, malicious programs own official websites on which they are promoted in high-sounding slogans which make their legitimacy almost unquestionable. Thus, it is not surprising that users who come across such sites decide to download these applications self-willingly. Nevertheless, it is not the only channel through which these programs can reach computers. Shareware and freeware bundles is another major, if not the most important distribution technique that the potentially unwanted system tools use to get into your system. Malware creators take advantage of the “Advanced” and “Custom” installation settings (which the users usually bypass) by placing their malicious creations as optional installs there. Thus, opting for the quick installation mode is unrecommended. Finally, you should look out for the infected pop-up ads as well. These deceptive online advertisements may also carry unwanted applications around and install them on your computer disguised as software updates, other legitimate software or files.
The most active malicious system tools today:
Disk Optimizer Pro is one of the system management programs that promises to fix computer errors, delete old registry entries and speed up your PC. Unfortunately, this application and even its full licensed version will barely have any positive effects on your PC. If you are ever offered to download this tool, you can confidently decline. And in case you find this application on your computer — remove it without hesitation.
PC Mechanic 2015 is another application that is ought to shield your computer from malware and exterminate undesirable components. Sadly, this tool may leave you largely disappointed. The program is really useless and instead of helping you to clean up the PC, tries to scare you into thinking your computer is at risk and attempts to sell you the licensed version of the program.
YAC is probably the most popular application of the three. Just like PC Mechanic, it is a security tool, which promises a reliable system protection. Nevertheless, this tool should be dealt with particularly cautiously. It is no secret that once this program is installed, it changes browser settings and starts displaying ads and redirects you to its official website urging to purchase its full version. Though it receives quite a lot of critique from the security experts, at the end of the day, it is up to you to decide whether you want to spend your money on this program or not.
Peculiarities concerning the elimination of rogue system tools
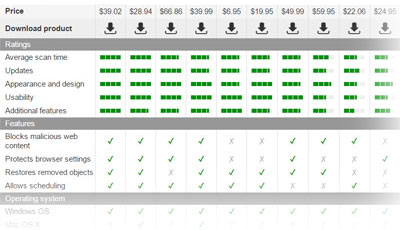
If you have an unusable system tool that you no longer use and which only takes up space on the hard disk, you can simply remove it using the uninstaller that comes with the application. Sadly, it is not that simple with corrupt system tools. These parasites are designed to conceal their existence and even use techniques to prevent antivirus utilities from detecting and removing them from the PC. Thus, such programs may require a combination of several techniques to make sure the removal is successful. Namely, the manual and the automatic one. Each program is different, so every time they need to be approached from a slightly different angle. For your convenience, you can find manual removal suggestions on our site, just below individual malware description. For the automatic removal approach, you will need a reputable antivirus, anti-spyware or anti-malware tool. 2-spyware experts always test the tools promoted on this site, so you can fully trust them and use them for the elimination of the malicious system tools and other undesirable programs.
Latest system tools in the database
Delete Discord virus
Elimination of Web companion
SAntivirus removal guide removal
Additional information added on 2016-10-21