How to remove a mail bomber
Have you ever heard about computer programs that work like illegal email servers used by hackers, but at the same time can be installed on the unsuspecting users’ computers? They are called mail bombers and can only operate on computers that are connected to the web. Their initial and ultimate aim is to spam you with heavyweight emails offering price comparisons, sales, and other commercial deals which not only occupy quite a substantial amount of space in our inbox but may also expose you to some potentially dangerous online content. To be precise, links and advertisements presented in these emails often lead to shady domains that may not necessarily be malicious themselves, but can certainly promote malware-infected applications which can severely damage the devices they are installed on.
Not to be completely unilateral, we should also mention that there is legitimate mail bombing software that does not pursue any illegal benefit. They are used by large companies, organizations, travel agencies, social media sites, etc., to supply their clients with the latest news, offers or other information that might be potentially relevant to them. Essentially, both the legitimate and the malicious mail bombers share the same functionalities and can, in some cases, be equally annoying with their emails. Nevertheless, you should not forget that malicious bombers are primarily spreading malware, false advertising, and suspicious commercial offers, while the legal ones may provide some actually useful information.
The main strategies of mail bomber distribution:
Perhaps the most important step in mail bomber prevention is learning as much as possible about the distribution of these programs. So, before we head to discuss how these viruses act on the infected devices, we would like to discuss the basic strategies that the malware developers apply in their distribution. First of all, we should point out that mail bombers are not actual viruses since they do not spread around like most malware do. Instead, they need to be installed on the computer directly or carried inside by other potentially unwanted program, Trojan or virus.
Viruses like mail bombers always need permission to install, whether it is granted by the computer owner or other individual responsible for the computer or computer network administration. Unfortunately, the hackers may take control over the device by brute-forcing their way in and install these programs on it against the user’s will.
Trojans, backdoors and RAT systems which are also used to deliver mail bombers work the same way, only with less human interaction. These viruses may make their way into the user’s computer via fake software update downloads, pirated games or along with some shady software which the users download on their computers themselves. Then these programs open a gateway for the hackers to install mail bombers or any other programs they can think of.
Mail bombers are currently most active on Windows, though we can expect to see them invade other operating systems anytime soon.
How do mail bombers behave on the infected computers?
Although mail bombers are usually waved aside as applications that cause more annoyance than danger, in reality, they are far from being harmless. If such programs get in the hands of some evil-minded individuals, they may be modified to do malicious things that extend much further than spam delivery. The most malicious of mail bombers can:
- Spread spam with false advertising, fraudulent commercial offers, infected links, etc.
- Flood mail provider’s servers and victim’s computers with emails carrying large attachments
- Slow down the network connection speed or cut it entirely.
- Diminish the overall computer performance, making random applications run into errors or unexpectedly shut down the system.
- Hide on the computer and concealing the installed malicious files under completely inconspicuous-looking file names.
As we have already mentioned, these unpleasant features may be implemented on any device that connects to the internet, so this means that the virus may infect work or personal computers alike. Flooding the inboxes with irrelevant junk and even obstructing the receiving and sending of emails may cause daily inconveniences and privacy infringements. On top of it all, if the virus infects the computer network and runs on it undetected, it may cause unexpected network failures and undermine the whole business.
The infected computer may not only be bombarded with spam but also spread it itself after being connected to the malicious botnet of computers run by hackers. Usually, the users are unaware of such activity so that they may be accused of illegal actions online or even end up in prison. The links they unknowingly send around are infested with crapware, deceptive ads, and Trojans, so all of the dangerous Internet junk such as ransomware, malware and potentially unwanted programs have easier access to the computer.
The most active mail bombers today:
Mail bombers are annoying, though, luckily, not widely-spread threats. Due to their considerably low popularity, they also lack in diversity, so most of these programs function almost identically. Here are a few examples of the most active mail bombers today:
- Kaboom! and Avalanche are among the top mail bombers that spam the users with endless junk mail and online marketing-based messages. Both of these programs are currently taking the leading positions in the mail bomber ranks.
- Aenima – is another effective and fast mail bomber that aims to clog up the targeted computers, local networks or mail services with spam. The messages this program spreads around vary in their content and subject titles, but their malicious nature is what binds them together. Like most mail bombers, Aenima does not travel on its own, so the users have to download it on their computers themselves. Once the virus is there – its sends out junk to other computer users.
What should you do if you find a mail bomber on your computer?
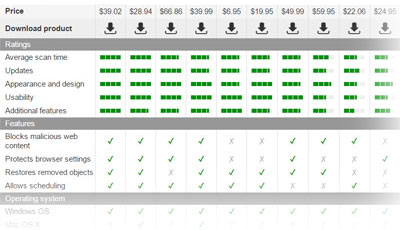
Malicious mail bombers should be eliminated from the computers as soon as they are detected. If they are left to roam the computer unattended, they may inflict serious problems, significantly diminishing your computer’s performance and stability. To inspect your computer from such viruses, you should employ reputable programs such as FortectIntego or SpyHunter 5Combo Cleaner which have already helped to fix thousands of computers. Scan your device with one of these professional tools and mail bomber will be as good as gone.
Latest mail bombers in the database
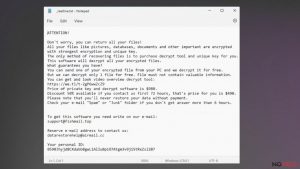
Steps for removing Bozq ransomware
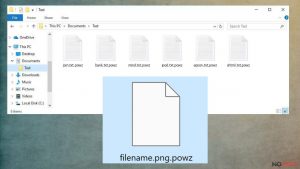
Uninstalling Powz ransomware
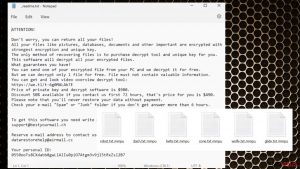
Mmpu ransomware removal tutorial
Additional information added on 2016-11-28