How to remove cracks
Cracks operate as illegal applications which help access a perpetrator the full access to the preferred program. In other words, they substitute the original elements of the application in order to launch it fully. The main effects of these tools include generated registration codes and registry values. Additionally, they are able to make important modifications to the targeted applications. In short, the files have been originated from gaming as hackers found alternative ways how to access the full versions of the wanted games. Such activity is simply regarded as the violation of copyright rights. Some countries issue strict penalties for such piracy activities.
One of the key flaws of cracked applications is that they might possess severe malware. If you choose the cracked version of the preferred program instead of the original one, in fact, you might suffer from severe outcomes. Installing the infected game or software might result in the heavily infected computer. Eventually, your confidential information such as login data and the credit card information might be disclosed to cyber criminals. What is more, if cyber law enforcement institutions expose the illegal activities, including Bitcoin mining and DDoS attacks, the offender might simply lose access to the Internet, or his computer might be confiscated.
How is ‘cracking’ performed?
There are mainly three types of cracks. They include keygens, patches, and loaders. Their aim is the same though they vary in their operation modes:
- Keygen (alternative name – Key Generator). This tool simply creates the serial and activation keys in order for the perpetrator to activate the full version of the program. Note that keygens might be both legal and corrupted. The latter are often noticed in the torrent sharing domains. However, if a person downloads it in the hope of acquiring access to a program, he might be infected with a trojan or another severe cyber threat. Lastly, there is high chance that the generated codes simply do not work.
- Patch is designed for renewing the targeted application and downloading its updates without paying any charge. These programs make necessary changes in the program source code to launch the full version of the application. Needless to say that illegally updated applications might have tremendous effects on the system: from a PC decline to a completely malfunctioning operating system.
- Loader meddles with the startup mode of the application. Initially, it should provide the access to the wanted full version of the program by escaping the stage of activation. Along with keygens, loaders have become popular among hackers.
Advantages vs. Disadvantages of cracks
The idea of receiving two items for the price of one or acquiring the product for free is still a prevalent desire of a modern customer. Likewise, the business of generating cracks is booming on the Internet despite various incentives to shut down the domains distributing pirated software. Diverse cyber policies are initiated to discourage users from indulging in this activity. However, if violating author rights is not the proper argument for you not to use pirated software, then you should consider whether the corrupted computer and stolen data is worth the price of the sole cracked game. It is necessary to emphasize the main issues while using the cracked games:
- Infringement of copyright rights. Every country regulates the laws related to the piracy on the Internet. Thus, while some countries survey the act according to law strictly, others might consider this matter in more lose terms. However, according to the country of your residence, the penalties for piracy activities might be harsh.
- Lost personal data. Corrupted applications might be infected with trojans which can steal your personal data, including credit card information, login information to email accounts. Needless to say for what purposes cyber criminals might exploit such information.
- Malware assaults. Once the corrupted software settles on the system, more system vulnerabilities might be created. Likewise, the device becomes exposed to aggressive and complex malware which daily attacks it.
- Redirects to potentially infected domains. Cracked applications might not only be “enhanced” with data-stealing viruses, but with browser hijackers and elements controlling your browsing traffic. As a result, you might find yourself in an infected website.
- Deteriorated computer performance. Another highly negative aspect of cracks is that they negatively affect the computer processing capabilities. Likewise, the longer the corrupted software resides on the system, the slower the computer might become. Trojans, various PUPs take up enormous computer processing resources. Cracked software should not outweigh the poorly performing computer.
- Cracks might prevent automatic updates. In some cases, the corrupted applications might block the automatic update of the downloaded applications. Therefore, users of such tools are inclined to visit the illegal web pages to keep the corrupted software up-to-date. However, often visitation only increases the chances of attracting more viruses into the system.
Concluding remarks about cracks
Despite the risks of using the cracked application, there is a high number of users, who still indulge in such activity. Obtaining the applications for free is still a common desire. As long as there are going to be consumers, swindlers will continue their activities as well. Nonetheless, you should keep in mind that the illegally obtained applications might cause enormous system issues and threaten your personal data. It is highly disputed issue whether you should exchange the access to your private information for a sole corrupted application. If you still managed to download the crack and you suspect that it is infected with viruses, follow these steps:
- Remove the software from the computer
- Run system scans with an anti-spyware tool
Manually eliminating the software might not work as the cracks might have dispersed the malignant elements in the entire registry. Therefore, it would be better to entrust the elimination to a security application, such as FortectIntego or Malwarebytes, which would exterminate the cyber threats completely.
Latest crack viruses added to the database
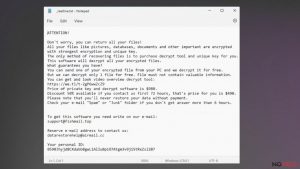
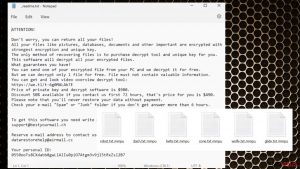
Steps for removing Bozq ransomware
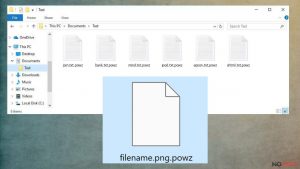
Uninstalling Powz ransomware
Mmpu ransomware removal tutorial
Additional information added on 2016-11-29