Remove Win32:BogEnt (Virus Removal Instructions) - 2021 updated
Win32:BogEnt Removal Guide
Description of Win32:BogEnt
Win32:BogEnt – a heuristics detection name used by AVG and Avast security engines
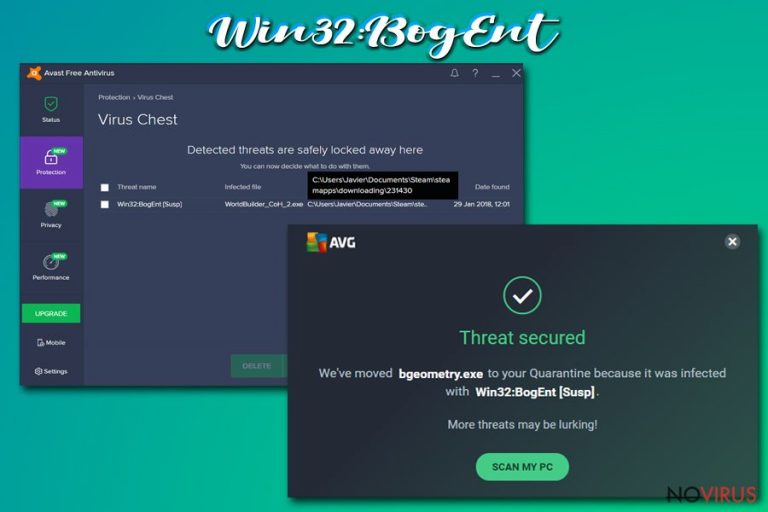
Win32:BogEnt is a computer infection detection name that might suggest that your Windows device is infected with malware. Avast and AVG anti-malware tools use this term to describe files that act suspiciously compared to similar ones. Although, keep in mind that not all malware detections are real, meaning that this might be a false-positive.
Users have reported that Win32:BogEnt detection was causing problems with their gaming, as game files from Steam were automatically quarantined or removed. If AVG or Avast is your preferred security tool, you should ignore the virus detection as it might be true. To be sure about it, you should get an alternate anti-malware software and scan your device for malware threats.
| name | Win32:BogEnt |
|---|---|
| Type | Malware |
| Affected Operating systems | Windows 7, Windows 8/8.1, Windows 10 |
| False-positive? | Anti-malware tools aren't always right about their detections. They analyze files and track their behavior to determine whether they're malicious or not. If you didn't open any suspicious emails, downloaded any new software, and the virus notification pop-up when playing Steam games, then there's a good chance that the detection was false-positive |
| Distribution | Malware can be hidden in spam emails, torrent platforms, deceptive ads, fake Flash Player updates, shady websites, and tons of other places. Your best weapon against it is a trustworthy anti-malware tool |
| Malware removal | To find out whether it was a false-positive or Win32:BogEnt virus is indeed malicious, we recommend scanning your device with a different security tool |
| System health check | In case your device was infected with malware, you have to take care of its overall health by restoring Registry values and fixing any other system inconsistencies. The best tool for this task is the powerful FortectIntego system repair software |
Anti-malware software can impede your browsing, gaming, working, or leisure time on the computer by showing threat notifications, but please be assured that it's just doing its job. When Win32:BogEnt is detected, you should download a secondary tool to scan it and make sure it's not malicious.
If another AV engine deems the file harmless, only then can you add it to your exceptions list and keep on doing whatever you were doing. It was reported that Win32:BogEnt virus detection name is associated with games from the Steam platform, including:
- Path of Exile,
- Company of Heroes 2,
- Chuzzle Deluxe,
- H1Z1 King of the Kill, etc.
Thus if you didn't install any new questionable software, didn't open any spam emails, or visited a suspicious website, Win32:BogEnt detection might be a false-positive. Steam gaming platform is a legitimate company that ensures that no malware is delivered to their users.
If Win32:BogEnt virus would turn out to be a real threat, then it's very hard to determine how it would act and what its purpose might be. Practically any cyber threat could be hidden or camouflaged behind that heuristics name, including Trojans, ransomware, keyloggers, etc.
Therefore, you should download a free but trustworthy security tool such as SpyHunter 5Combo Cleaner or Malwarebytes and scan your device. If any of these tools don't locate any infections – great! However, you have to remove Win32:BogEnt immediately if they flag it as malicious.
Devices that had malware infections tend to exhibit various abnormal behavior, such as crashing, freezing, severe lag, etc. That happens due to altered system Registry and other core settings and files. Thus after Win32:BogEnt removal, we highly recommend fixing any system-related issues automatically with the all-in-one FortectIntego system repair tool.
Enhancing your cybersecurity and taking precautionary measures could help avoid malware infections
Cybercriminals are always creating new computer infections and ways to distribute them. Although tech giants like Google, Microsoft, Apple, and others try their best to make the internet a safer place, it's really hard to keep up with the criminals.
That's why people should take matters into their own hands and take care of their safety themselves. Our cybersecurity team has compiled a list of suggestions that wouldn't guarantee that an infection won't get through but will sure make it a tough task for any malware or PUPs:
- Acquire professional anti-malware software. Update it regularly and make a habit of scanning your device at least once a week.
- Maintain system files and settings at bay by running system diagnostics with compatible tools. Unattended, corrupted, or in any other way modified files could cause BSoDs, freezing, and other system issues.
- Keep backups of all essential files. In case of ransomware or other cyberattacks, you can easily restore data without the criminals' intervention.
- Install the latest updates to your Operating System and other software as soon as they are available. Outdated software is constantly exploited by hackers.
Remove Win32:BogEnt virus if another AV tool flags it as malicious
You shouldn't rush with Win32:BogEnt removal as you might eliminate a file that's needed for your games played at Steam. You have to make sure that the file is malicious before removing it. The best way to do that is by scanning it with an alternative anti-malware tool.
We recommend downloading free AV tools such as SpyHunter 5Combo Cleaner or Malwarebytes to perform a double-check. Remove Win32:BogEnt immediately if either of these security tools flags it as malicious. If they don't, add the file to AVG or Avast exceptions list so it wouldn't be questioned again.
Afterward, you should scan your Windows device for any system irregularities which may cause crashing, freezing, or any other strange behavior. According to many user reviews, the powerful FortectIntego system repair tool is the best software to take care of various system issues.
Getting rid of Win32:BogEnt. Follow these steps
In-depth guide for the Win32:BogEnt elimination
Important! →
The elimination guide can appear too difficult if you are not tech-savvy. It requires some knowledge of computer processes since it includes system changes that need to be performed correctly. You need to take steps carefully and follow the guide avoiding any issues created due to improper setting changes. Automatic methods might suit you better if you find the guide too difficult.
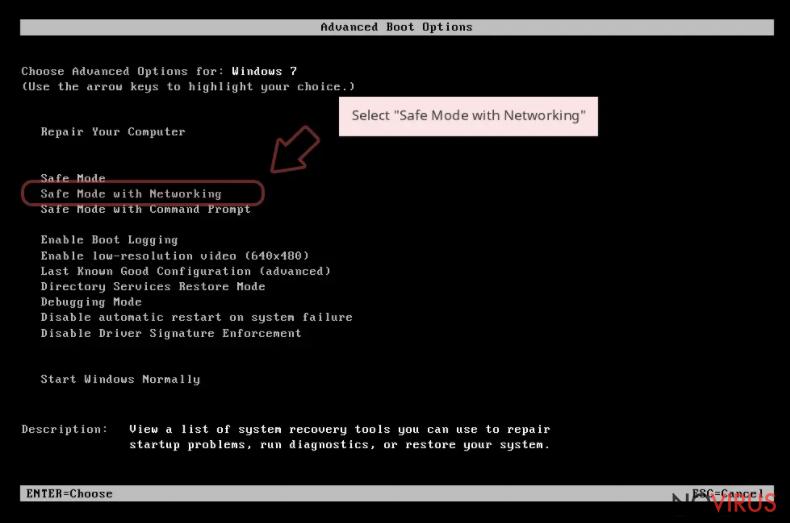
Step 1. Launch Safe Mode with Networking
Safe Mode environment offers better results of manual virus removal
Windows 7 / Vista / XP
- Go to Start.
- Choose Shutdown, then Restart, and OK.
- When your computer boots, start pressing the F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) a few times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.
Windows 10 / Windows 8
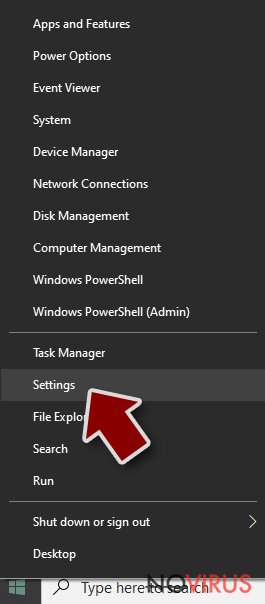
- Right-click the Start button and choose Settings.
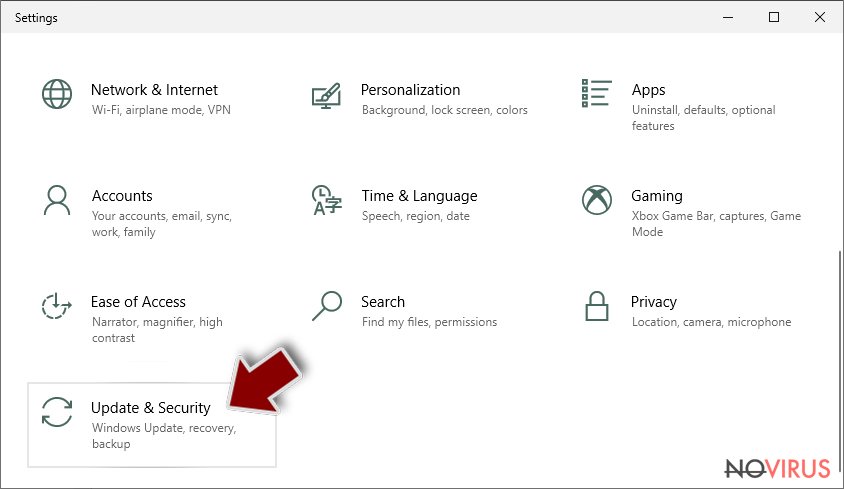
- Scroll down to find Update & Security.
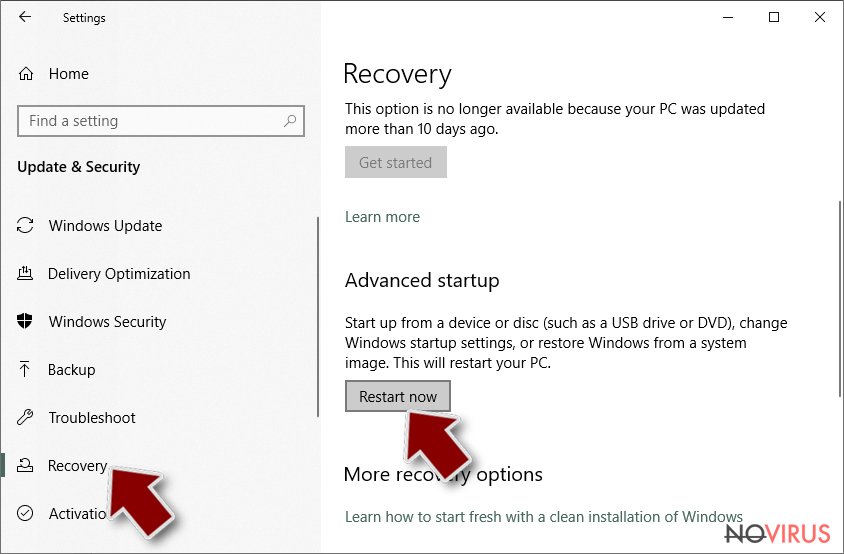
- On the left, pick Recovery.
- Scroll to find Advanced Startup section.
- Click Restart now.
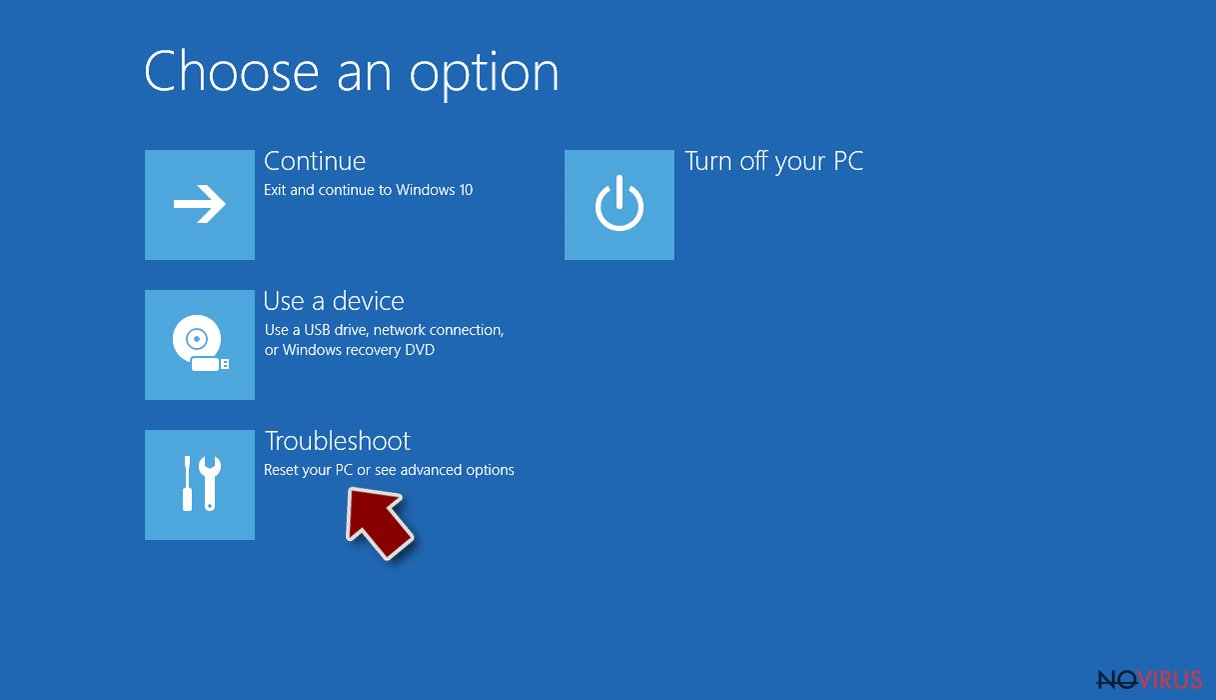
- Choose Troubleshoot.
- Go to Advanced options.
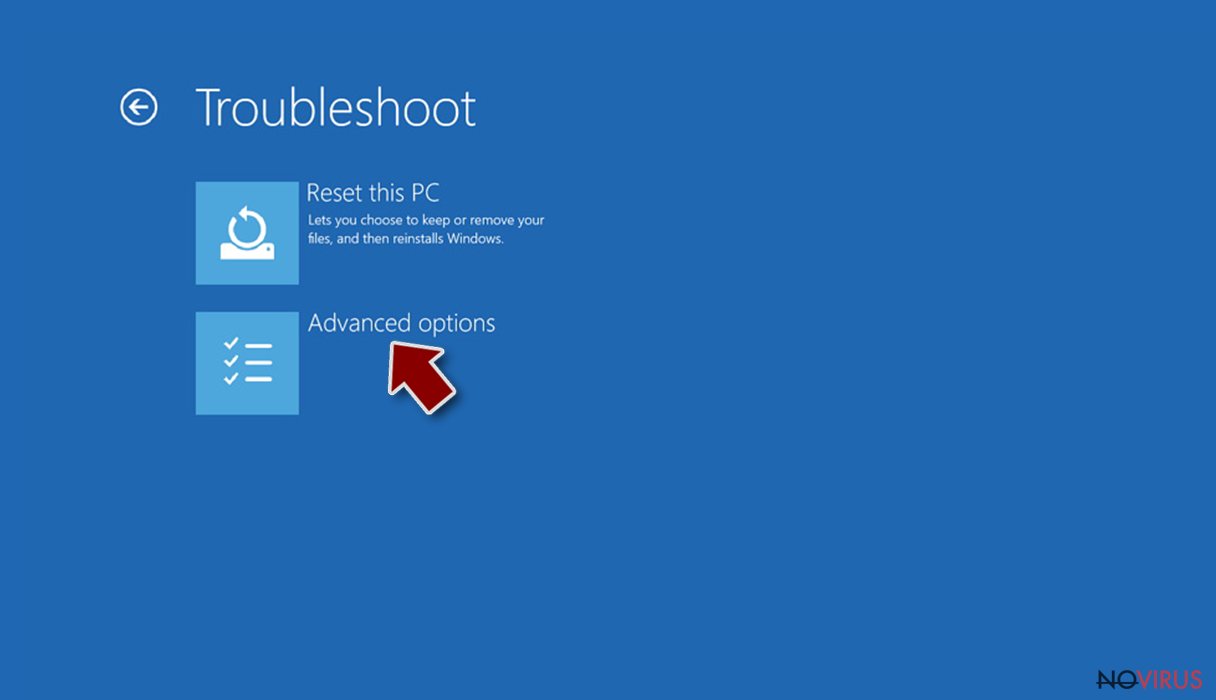
- Select Startup Settings.
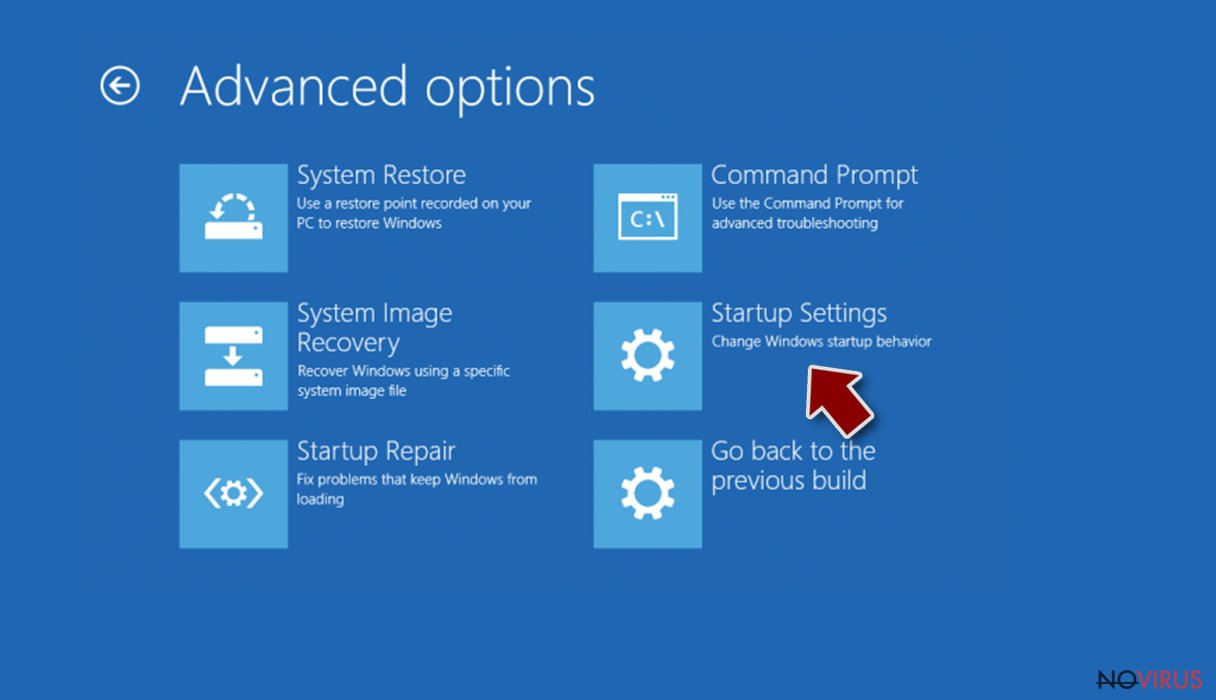
- Press Restart.
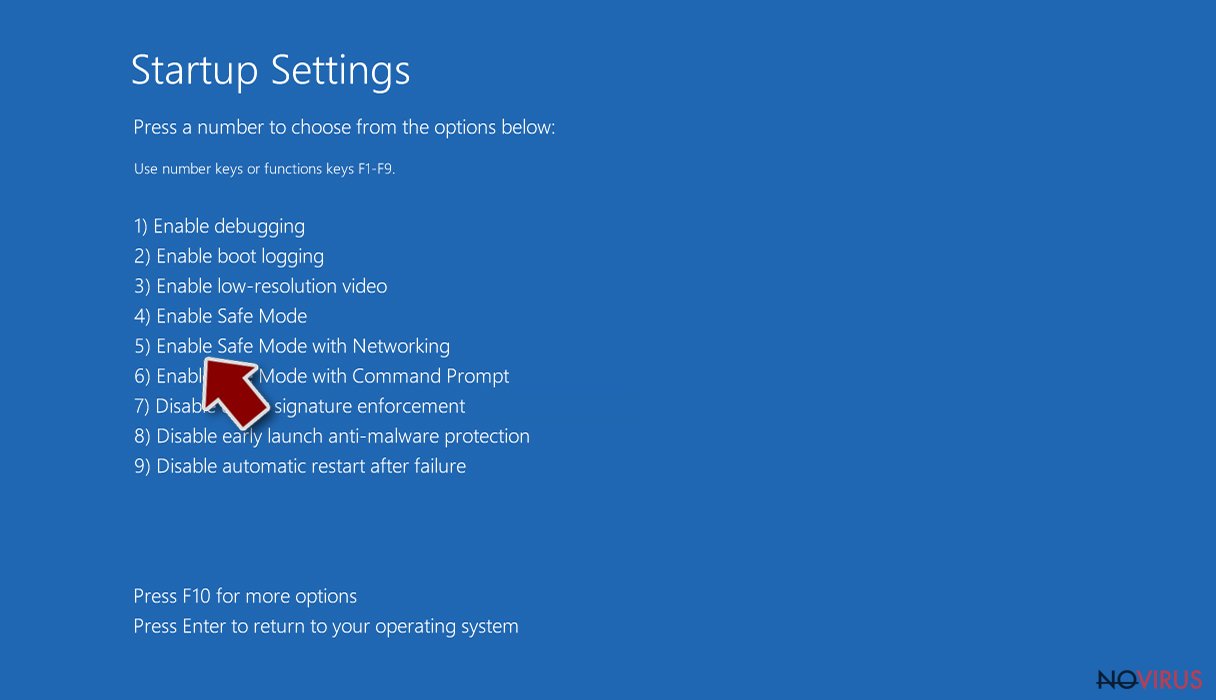
- Choose 5) Enable Safe Mode with Networking.
Step 2. End questionable processes
You can rely on Windows Task Manager that finds all the random processes in the background. When the intruder is triggering any processes, you can shut them down:
- Press Ctrl + Shift + Esc keys to open Windows Task Manager.
- Click on More details.
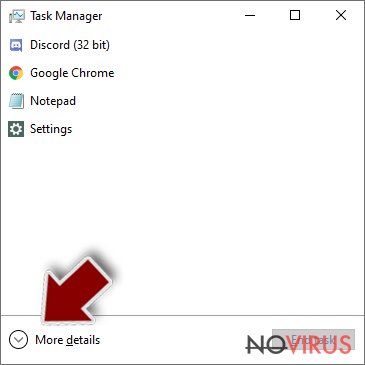
- Scroll down to Background processes.
- Look for anything suspicious.
- Right-click and select Open file location.
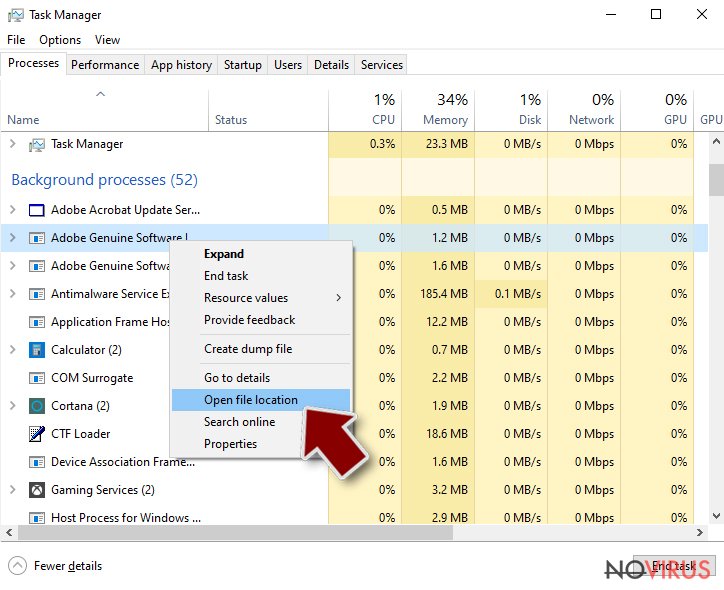
- Go back to the Process tab, right-click and pick End Task.
- Delete the contents of the malicious folder.
Step 3. Check the program in Startup
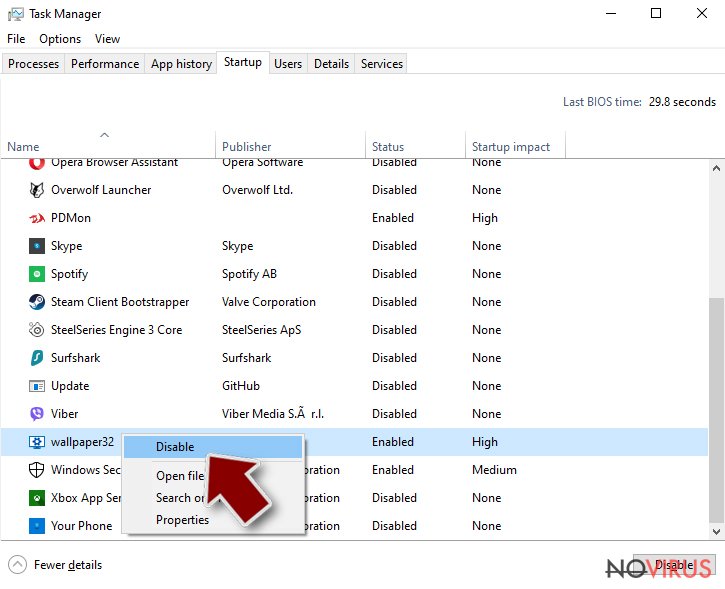
- Press Ctrl + Shift + Esc on your keyboard again.
- Go to the Startup tab.
- Right-click on the suspicious app and pick Disable.
Step 4. Find and eliminate virus files
Data related to the infection can be hidden in various places. Follow the steps and you can find them:
- Type in Disk Cleanup in Windows search and press Enter.
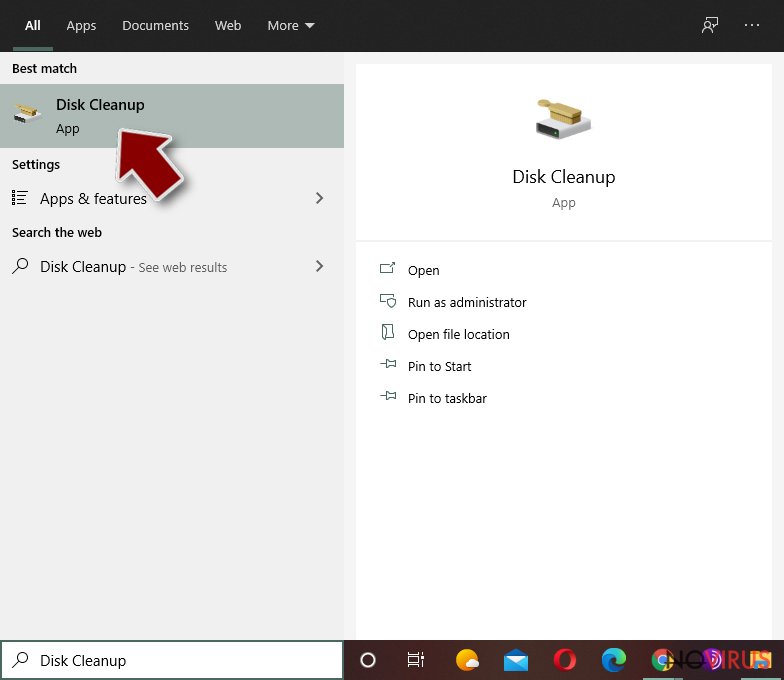
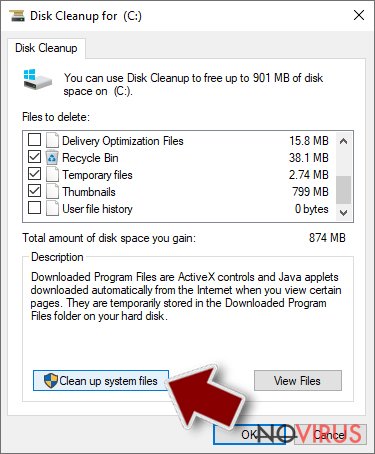
- Select the drive (C: is your main drive by default and is likely to be the one that has malicious files in) you want to clean.
- Scroll through the Files to delete and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.
- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
It is strongly recommended to take precautions and secure your computer from malware attacks. To protect your PC from Win32:BogEnt and other dangerous viruses, you should install and keep a powerful malware removal tool, for instance, FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes.
How to prevent from getting malware
A proper web browser and VPN tool can guarantee better safety
As online spying becomes an increasing problem, people are becoming more interested in how to protect their privacy. One way to increase your online security is to choose the most secure and private web browser. But if you want complete anonymity and security when surfing the web, you need Private Internet Access VPN service. This tool successfully reroutes traffic across different servers, so your IP address and location remain protected. It is also important that this tool is based on a strict no-log policy, so no data is collected and cannot be leaked or made available to first or third parties. If you want to feel safe on the internet, a combination of a secure web browser and a Private Internet Access VPN will help you.
Reduce the threat of viruses by backing up your data
Due to their own careless behavior, computer users can suffer various losses caused by cyber infections. Viruses can affect the functionality of the software or directly corrupt data on your system by encrypting it. These problems can disrupt the system and cause you to lose personal data permanently. There is no such threat if you have the latest backups, as you can easily recover lost data and get back to work.
It is recommended to update the backups in parallel each time the system is modified. This way, you will be able to access the latest saved data after an unexpected virus attack or system failure. By having the latest copies of important documents and projects, you will avoid serious inconveniences. File backups are especially useful if malware attacks your system unexpectedly. We recommend using the Data Recovery Pro program to restore the system.
