Remove VirTool:Win32/DefenderTamperingRestore (Virus Removal Instructions) - Jul 2021 updated
VirTool:Win32/DefenderTamperingRestore Removal Guide
Description of VirTool:Win32/DefenderTamperingRestore
VirTool:Win32/DefenderTamperingRestore – a computer infection that might disable installed security tools
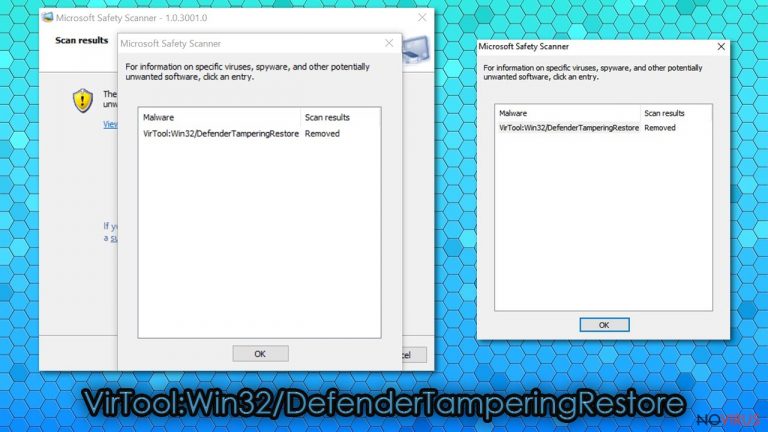
VirTool:Win32/DefenderTamperingRestore is a hazardous Windows OS malware that tampers with security tools, weakening the cybersecurity levels of the infected device and making it more prone to various infections. This virus might have different secondary goals; it all depends on what it's programmed to do.
After tampering with the Windows Defender or other anti-malware software, it might download additional malware (Remote Access Trojans, ransomware, etc.), resulting in identity theft, financial losses, and similar nightmares. If your AV engine flags this infection, you have to take action immediately.
In some cases, VirTool:Win32/DefenderTamperingRestore detection might be a false positive. Either way, it's crucial to take this warning seriously and investigate it scrupulously. This article contains the cyberthreat's summary, removal, and recovery methods.
| name | VirTool:Win32/DefenderTamperingRestore |
|---|---|
| Type | Malware |
| Symptoms of infection | BSoDs, errors, severe lag, and other abnormal device behavior; pop-ups informing of the infection appear out of the blue |
| Purpose | Weaken the defenses of Windows Defender |
| Dangers | Privacy issues, additional malware infections, financial losses |
| distribution | Fake Flash Player updates, spam emails |
| Associated scam | Trojan_Spyware Alert – Error Code #0x268d3 (!x3) |
| Elimination | Removal should be performed with reputable security tools in Safe Mode with Networking (guide included below the article in the instructions section) |
| System health check | This infection might modify system files and settings, which may result in various system failures. System diagnostics with a tool like the time-proven FortectIntego will automatically fix all system irregularities and delete tracking cookies in the process |
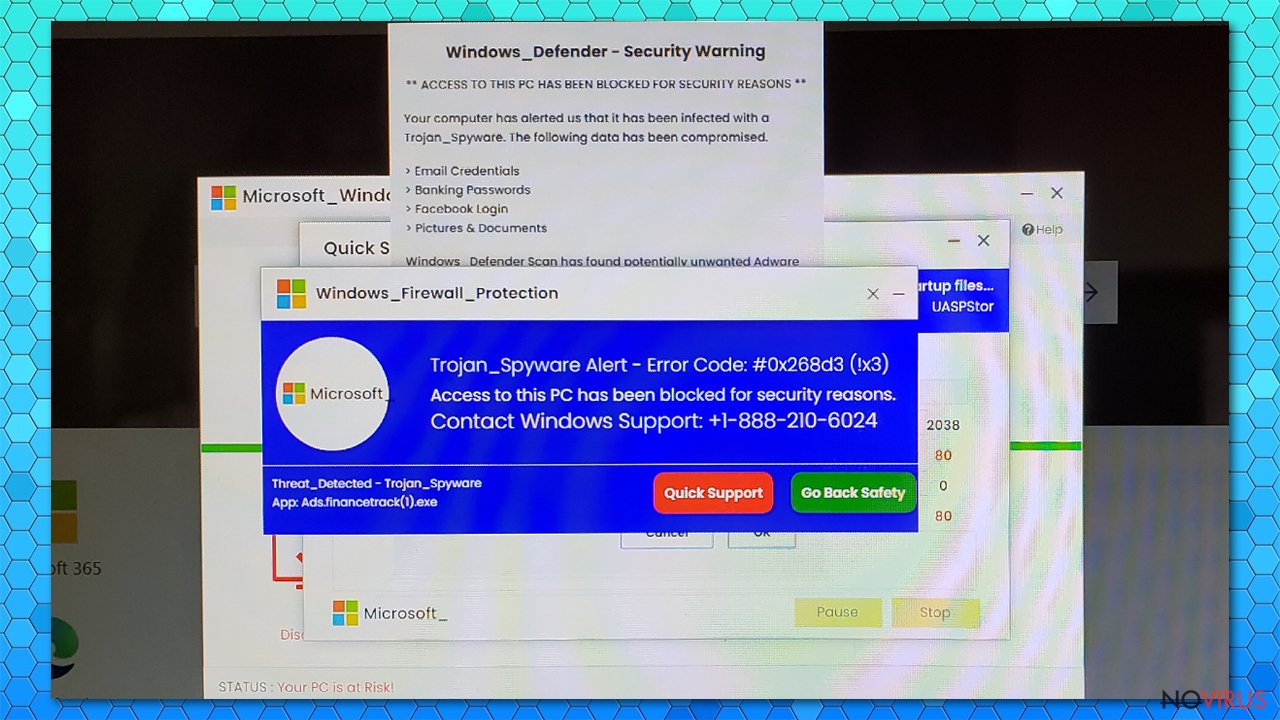
In some cases, when Windows computers got infected with VirTool:Win32/DefenderTamperingRestore, their screens were locked, and pop-ups stating that “Trojan_Spyware Alert – Error Code #0x268d3 (!x3)” was detected. It's a Microsoft Support Scam, urging you to call a toll-free number immediately to resolve the issue:
Windows_Firewall_Protection
Trojan_Spyware Alert – Error Code #0x268d3 (!x3)
Access to this PC has been blocked for security reasons.
Contact Windows Support: +1-888-210-6024
Please do not do that. You might be tricked into revealing your personal details and purchasing rogue system tools that are worthless by calling the provided number. Cybercriminals might also ask to grant them remote access to the infected PC to “resolve” the issues.
If you allow them remote access, they could upload additional malware onto your device, steal your files, or do whatever else they please. Unlock the screen by pressing Alt + Ctrl + Del and opening the Task Manager. Identify the running process and end its task. If that doesn't help, reboot your device in Safe Mode with Networking and perform a full system scan with one of our recommended security tools.
Download the time-proven Malwarebytes security software and, after updating it – scan the entire system. It should detect and remove VirTool:Win32/DefenderTamperingRestore virus. If the scan comes up empty, perform it once more, but in Safe Mode with Networking. If you need assistance with that, feel free to use our guides posted below the article.
Another great addition to have is the SpyHunter 5Combo Cleaner anti-malware tool. Like the aforementioned software, it will block you from installing potentially unwanted programs, prevent you from opening infected email attachments, and safeguard your computer from other ways that various cyber infections are traveling.
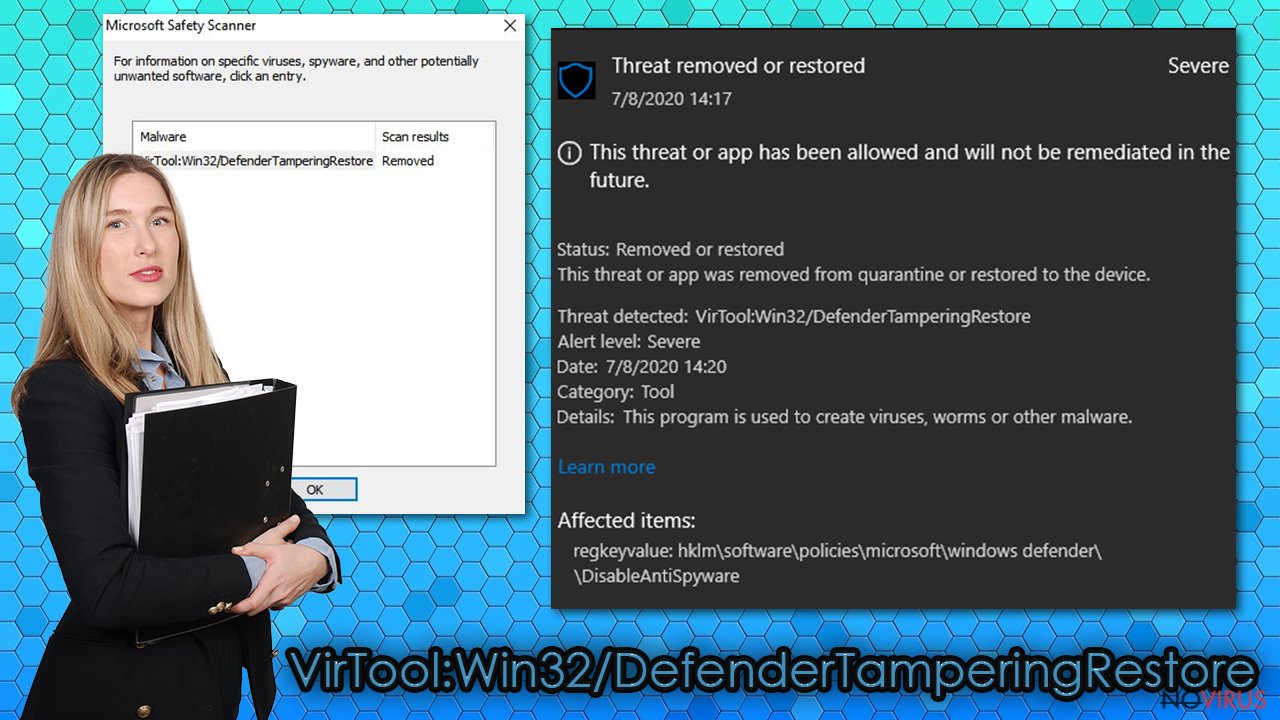
It's essential to remove VirTool:Win32/DefenderTamperingRestore as soon as possible as you and your infected computer might in real danger. Both of the suggested tools have free trials. Therefore, please don't hesitate to download them and eliminate all infections hiding on your device.
Once your device is virus-free, you have to take care of its overall health, as the article's culprit might have severely modified its system files and settings. These changes might result in crashes, errors, or even complete system failure. Luckily, you can resolve all system-related irregularities by performing system diagnostics with the FortectIntego PC repair tool.
Most popular malware distribution techniques
There are tons of different infections lurking on the internet. Your best chance to avoid them is to acquire a reliable anti-malware tool with real-time protection. Cybercriminals are creating new malware daily, and the spreading techniques are getting more and more elaborate.
One of the most prevalent malware distribution methods is still via infected email attachments and deceptive hyperlinks. The main attribute of a spam/phishing email is the sense of urgency that it creates by pushing you into downloading its attachment or clicking on a link. Please be aware of them and don't download anything if you don't know the sender, the email has grammatical mistakes, or raises any other flags.
Another sure way to catch some sort of an infection is by using file-sharing platforms, especially popular torrent websites. Cybercriminals upload their vile creations camouflaged as software cracks and wait for unaware users to download them. As soon as a payload file is executed, the infection spreads immediately. Refrain from using such platforms if you value your privacy and security.
Detailed instructions to remove VirTool:Win32/DefenderTamperingRestore
As we've already stated, VirTool:Win32/DefenderTamperingRestore might be a false positive. To find out whether the threat is real or not, you have to scan your device with alternate security software as the Windows Defender might be tampered with, and it might fail to identify and remove the hazardous infection.
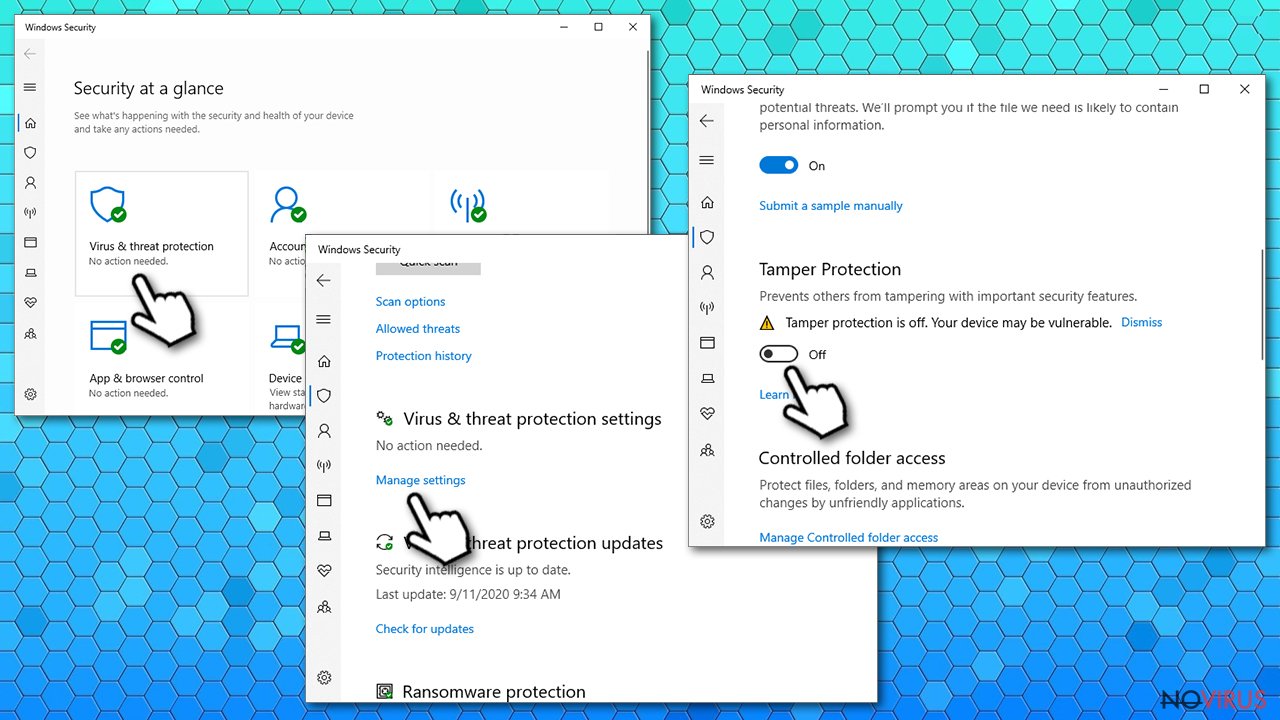
The article's culprit might change the Tamper Protection setting of Microsoft's default security software which was first introduced in 2019 with Windows 10 version 1903. Therefore, before downloading trustworthy anti-malware software, you have to turn the aforementioned setting off, and that's how it's done:
- Type in Windows Security in Windows search and hit Enter
- Pick Virus & threat protection
- Then click Manage settings
- Scroll down, locate Tamper Protection
- Turn the switch to the left to turn Tamper Protection off.
When that's done, reboot your device in Safe Mode with Networking (instructions provided below) and download Malwarebytes, SpyHunter 5Combo Cleaner, or other dependable anti-malware software of your choice and perform a full system scan. Either of the recommended security tools will automatically detect all threats and suggest removing them. Please stick with the recommendations to delete all malware safely.
Once VirTool:Win32/DefenderTamperingRestore is a thing of the past, you have to take care of the damages it might have caused to your system files and settings. Finding all system irregularities is practically impossible, even for IT professionals. That's why we highly recommend using the time-tested FortectIntego software.
Its patented technology will identify all modifications that were done to the system and advise to repair them. Moreover, it will delete all tracking cookies stored by treacherous websites to spy on your browsing activities. This app will ensure that the device runs as well as new.
Getting rid of VirTool:Win32/DefenderTamperingRestore. Follow these steps
In-depth guide for the VirTool:Win32/DefenderTamperingRestore elimination
Important! →
The elimination guide can appear too difficult if you are not tech-savvy. It requires some knowledge of computer processes since it includes system changes that need to be performed correctly. You need to take steps carefully and follow the guide avoiding any issues created due to improper setting changes. Automatic methods might suit you better if you find the guide too difficult.
Step 1. Launch Safe Mode with Networking
Safe Mode environment offers better results of manual virus removal
Windows 7 / Vista / XP
- Go to Start.
- Choose Shutdown, then Restart, and OK.
- When your computer boots, start pressing the F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) a few times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.
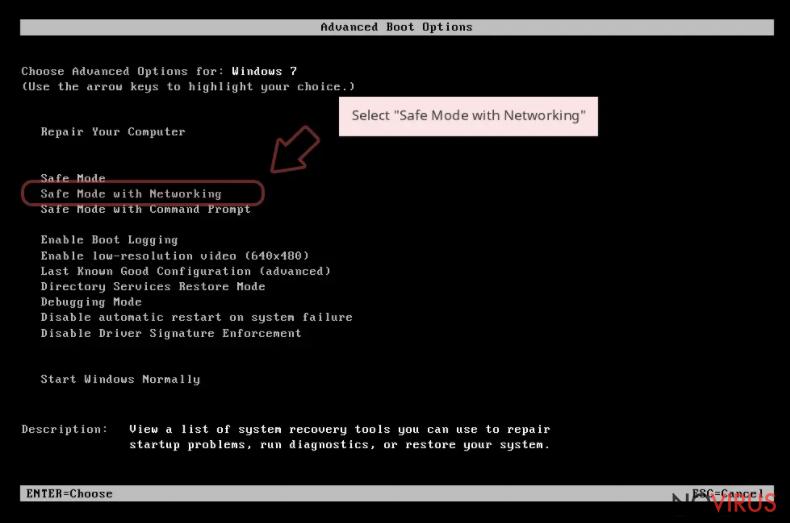
Windows 10 / Windows 8
- Right-click the Start button and choose Settings.
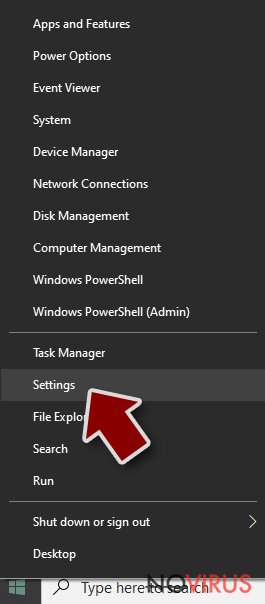
- Scroll down to find Update & Security.
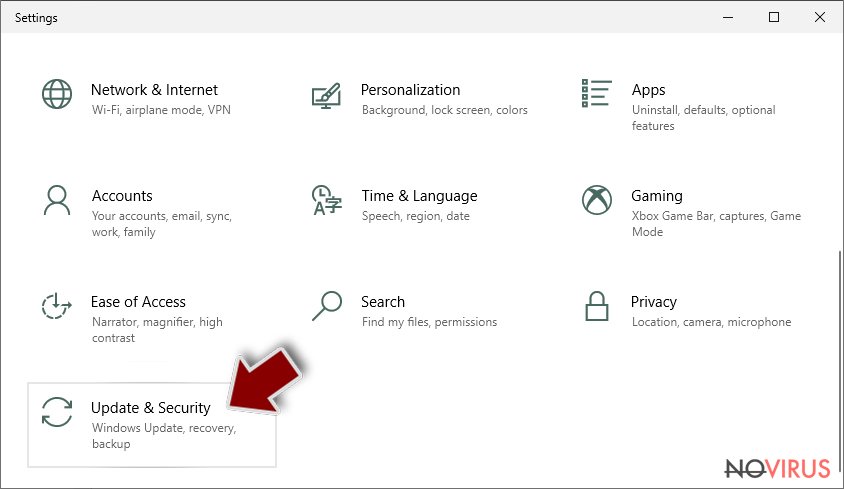
- On the left, pick Recovery.
- Scroll to find Advanced Startup section.
- Click Restart now.
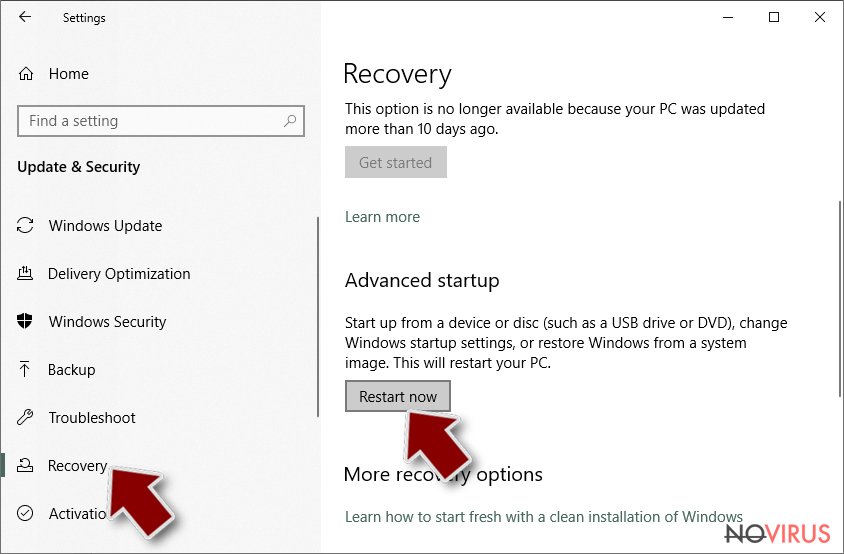
- Choose Troubleshoot.
- Go to Advanced options.
- Select Startup Settings.
- Press Restart.
- Choose 5) Enable Safe Mode with Networking.
Step 2. End questionable processes
You can rely on Windows Task Manager that finds all the random processes in the background. When the intruder is triggering any processes, you can shut them down:
- Press Ctrl + Shift + Esc keys to open Windows Task Manager.
- Click on More details.
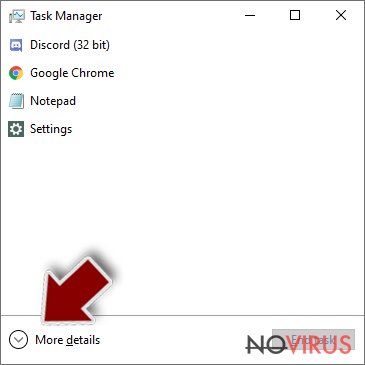
- Scroll down to Background processes.
- Look for anything suspicious.
- Right-click and select Open file location.
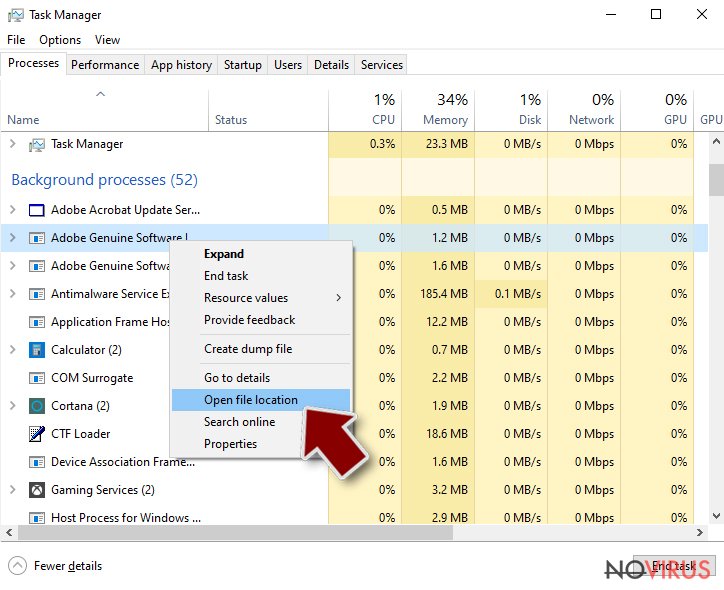
- Go back to the Process tab, right-click and pick End Task.
- Delete the contents of the malicious folder.
Step 3. Check the program in Startup
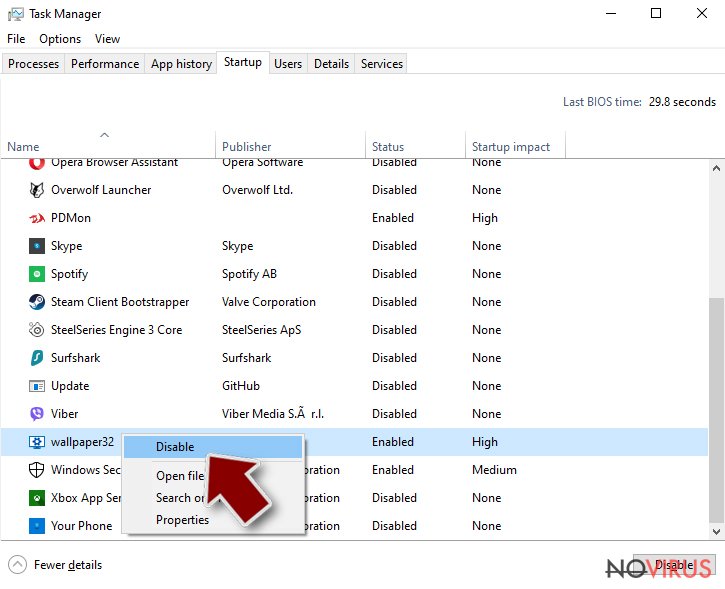
- Press Ctrl + Shift + Esc on your keyboard again.
- Go to the Startup tab.
- Right-click on the suspicious app and pick Disable.
Step 4. Find and eliminate virus files
Data related to the infection can be hidden in various places. Follow the steps and you can find them:
- Type in Disk Cleanup in Windows search and press Enter.
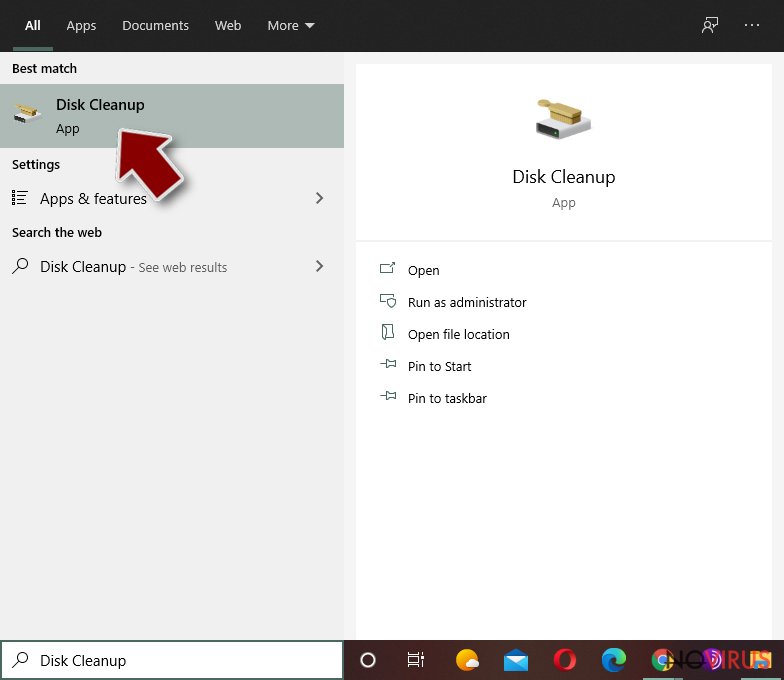
- Select the drive (C: is your main drive by default and is likely to be the one that has malicious files in) you want to clean.
- Scroll through the Files to delete and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.
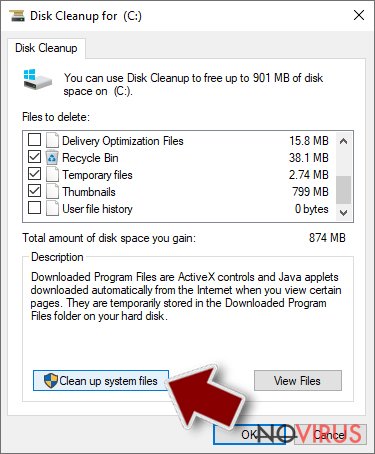
- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
It is strongly recommended to take precautions and secure your computer from malware attacks. To protect your PC from VirTool:Win32/DefenderTamperingRestore and other dangerous viruses, you should install and keep a powerful malware removal tool, for instance, FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes.
How to prevent from getting malware
A proper web browser and VPN tool can guarantee better safety
As online spying becomes an increasing problem, people are becoming more interested in how to protect their privacy. One way to increase your online security is to choose the most secure and private web browser. But if you want complete anonymity and security when surfing the web, you need Private Internet Access VPN service. This tool successfully reroutes traffic across different servers, so your IP address and location remain protected. It is also important that this tool is based on a strict no-log policy, so no data is collected and cannot be leaked or made available to first or third parties. If you want to feel safe on the internet, a combination of a secure web browser and a Private Internet Access VPN will help you.
Recover files damaged by a dangerous malware attack
Despite the fact that there are various circumstances that can cause data to be lost on a system, including accidental deletion, the most common reason people lose photos, documents, videos, and other important data is the infection of malware.
Some malicious programs can delete files and prevent the software from running smoothly. However, there is a greater threat from the dangerous viruses that can encrypt documents, system files, and images. Ransomware-type viruses focus on encrypting data and restricting users’ access to files, so you can permanently lose personal data when you download such a virus to your computer.
The ability to unlock encrypted files is very limited, but some programs have a data recovery feature. In some cases, the Data Recovery Pro program can help recover at least some of the data that has been locked by a virus or other cyber infection.
