Remove SearchLock (Uninstall Guide) - Jul 2017 updated
SearchLock Removal Guide
Description of SearchLock
SearchLock virus and its features
Computer users can encounter SearchLock virus under two conditions. First, they may be looking for alternative search engine and found this suspicious search provider. Second, they may have rushed with software installation process, and this browser hijacker might have sneaked inside bundled with the recently installed program. No matter in which way it managed to get inside, it’s still quite easy to remove SearchLock.
We do not recommend delaying this process because all potentially unwanted programs (PUP) have some unpleasant issues that may lead to various computer problems and privacy-related issues. For quick and simple SearchLock removal we recommend FortectIntego or other reputable anti-malware program. It will scan the system and eliminate all malicious components. However, you can always get rid of browser hijacker manually. It may be a tricky task, but our team has prepared detailed instructions at the end of the article.
In the official website developers claim that it’s a safe search engine that filters unsafe results and delivers only reliable results. However, our research has shown that this SearchLock browser hijacker provides modified search results. It may remove relevant search results and replace them with sponsored links. When users click on third-party links, the developers generate pay-per-click revenue. There’s nothing wrong with this advertising method if it is used fairly and do not cause problems for the users.
Security specialists have concerns about SearchLock redirect issues because some of the provided search results or ads may lead to potentially dangerous websites that are created for spreading malware. Besides, the latest version of the hijacker, Searchlock 3 is known for delivering users to websites such as Results.searchlock3.com or Searchlock3.com.
All these redirects may end up badly, and computer users may encounter ransomware, Trojan or other malware attacks. Unfortunately, this browser hijacker is threatening not only computers but personal information about users as well. It may collect browsing-related information such as visited websites, search queries and so on. However, aggregated data may be shared or even sold to third-parties, and since then you may receive lots of advertisements, unwanted newsletters and so on.
Transmission methods of the browser hijacker
SearchLock has an official website that offers to download it; however, many computer users complain that it appeared out of the blue. However, this search engine may travel bundled with freeware and shareware as well. Developers of the potentially unwanted programs always add their applications as additional components.
If users installed a necessary program using ‘Quick’ or ‘Recommended’ setup, they may have encountered SearchLock hijack. However, they can easily avoid this unpleasant issue if they have chosen ‘Advanced/Custom’ settings. These settings allow monitoring and adjusting installation.
Therefore, you have to carefully follow each step and make sure that you haven’t agreed to make SearchLock.com as your homepage or default search engine. Besides, you may see the checkbox with additional programs that are suggested for you as well. You have to deselect all of these apps and statements offering to set new search provider. It’s the only way to avoid unwanted programs from getting inside the system.
Suggestions for SearchLock removal
Computer users who have been infected with SearchLock virus have two option for its removal – automatic and manual. We always recommend relying on automatic elimination because it is faster and safer. Using this method you have to install a professional malware removal tool and scan the system. Your preferred anti-malware program will remove SearchLock and all its related components.
Besides, this program will protect your computer from other infections in the future. However, we know that not all computer users prefer using additional software for virus elimination. For those computer users, who want to remove browser hijacker manually, we prepared detailed and illustrated SearchLock removal instructions.
You may remove virus damage with a help of FortectIntego. SpyHunter 5Combo Cleaner and Malwarebytes are recommended to detect potentially unwanted programs and viruses with all their files and registry entries that are related to them.
Getting rid of SearchLock. Follow these steps
Uninstall SearchLock in Windows systems
Carefully follow the instructions. You have to find and remove SearchLock virus and all its related components. Make sure you remove all suspicious entries in order to prevent another hijack. Then, don't forget to check your web browsers and remove all suspicious extensions, add-ons or plugins.
Terminate suspicious programs from Windows 10/8 machines by following these instructions:
- Type Control Panel into Windows search and once the result shows up hit Enter.
- Under Programs, choose Uninstall a program.
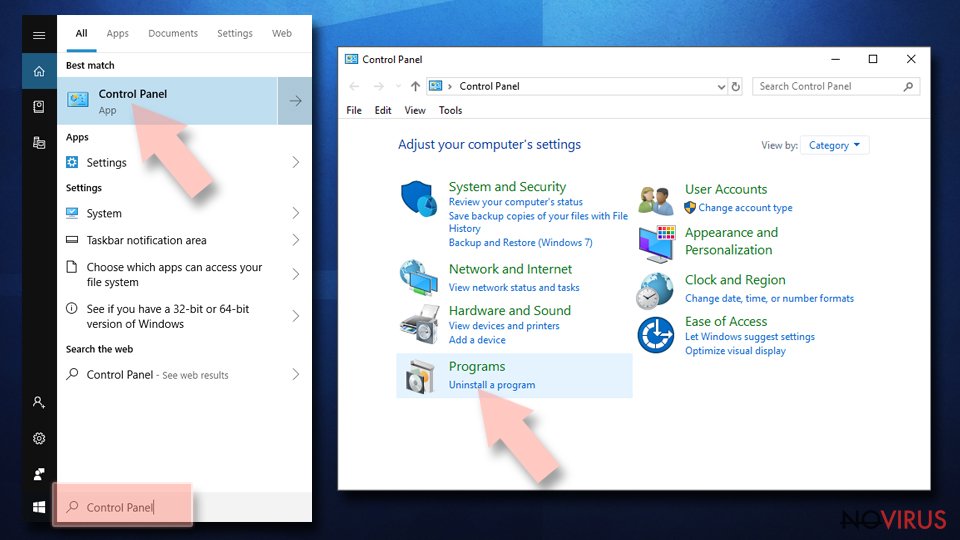
- Find components related to suspicious programs.
- Right-click on the application and select Uninstall.
- Click Yes when User Account Control shows up.
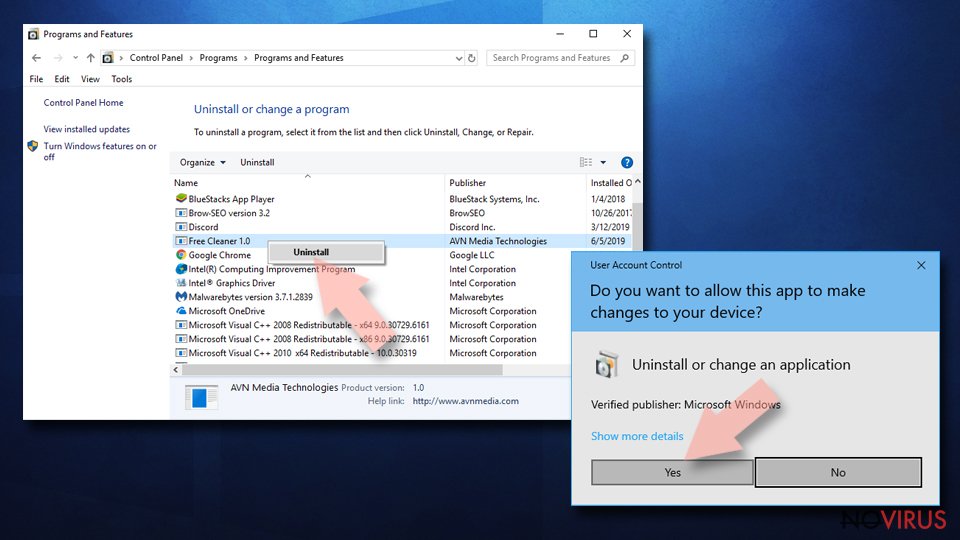
- Wait for the process of uninstallation to be done and click OK.
Windows 7/XP instructions:
- Click on Windows Start and go to Control Panel on the right pane.
- Choose Add/Remove Programs.
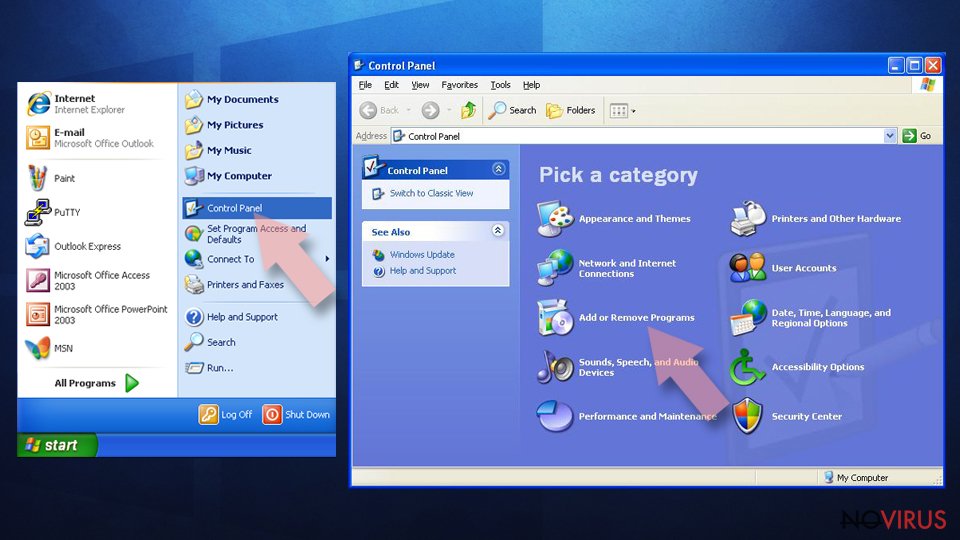
- Select Uninstall a program under Programs in Control Panel.
- Click once on the unwanted application.
- Click Uninstall/Change at the top.
- Confirm with Yes.
- Click OK and finish the removal.
Uninstall SearchLock in Mac OS X system
-
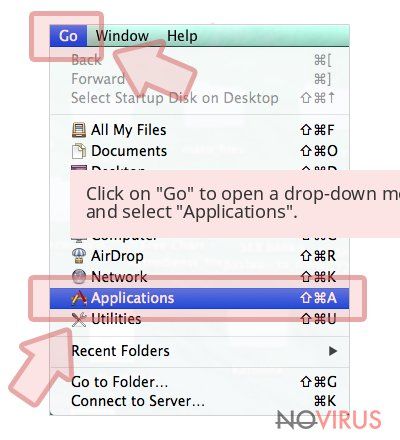
Users who use OS X should click on Go button, which can be found at the top left corner of the screen and select Applications.

-
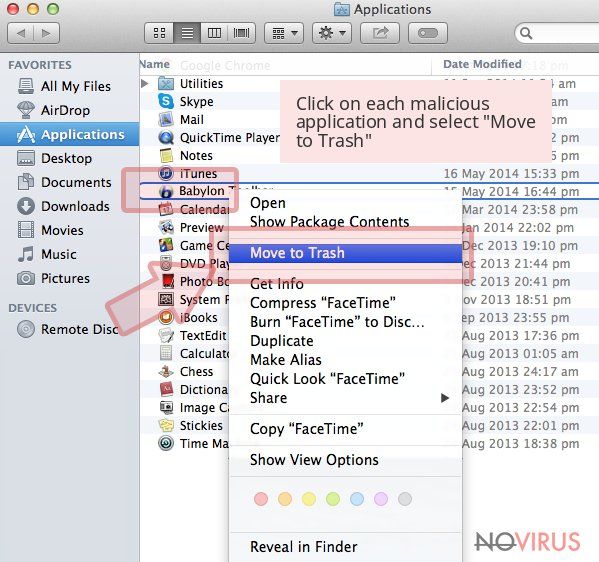
Wait until you see Applications folder and look for SearchLock or any other suspicious programs on it. Now right click on every of such entries and select Move to Trash.

Delete SearchLock from Microsoft Edge
Delete suspicious extensions from MS Edge:
- Go to the Menu by clicking on the three horizontal dots at the top-right.
- Then pick Extensions.
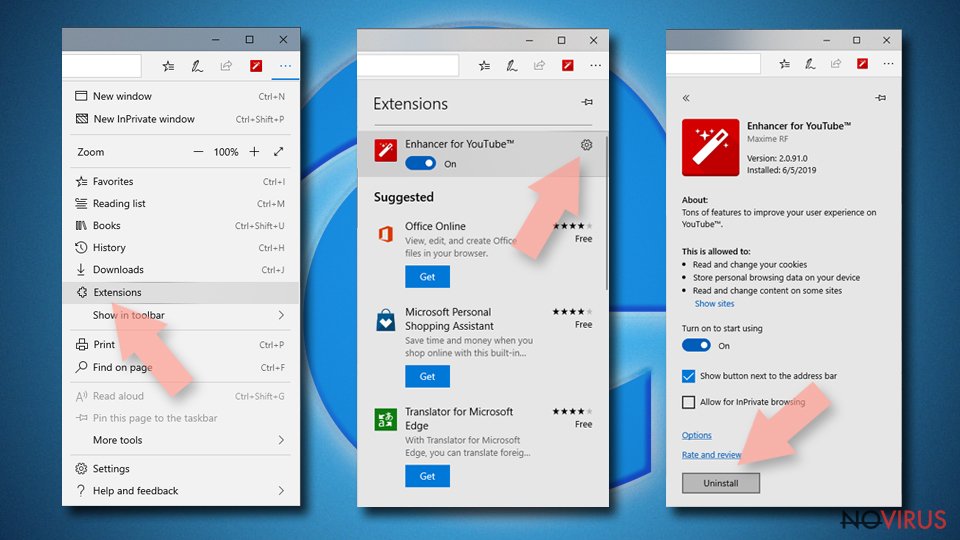
- Choose the unwanted add-ons on the list and click on the Gear icon.
- Click on Uninstall at the bottom.
Clear cookies and other data:
- Click on the Menu and from the context menu select Privacy & security.
- Under Clear browsing data, select Choose what to clear.
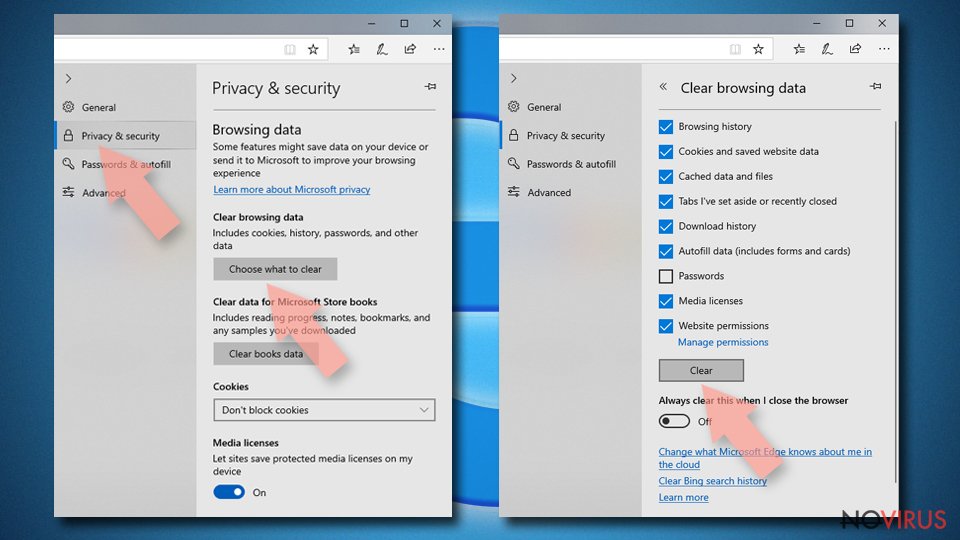
- Choose everything except passwords, and click on Clear.
Alter new tab and homepage settings:
- Click the menu icon and choose Settings.
- Then find On startup section.
- Click Disable if you found any suspicious domain.
Reset MS Edge fully:
- Click on the keyboard Ctrl + Shift + Esc to open Task Manager.
- Choose More details arrow at the bottom.
- Go to Details tab.
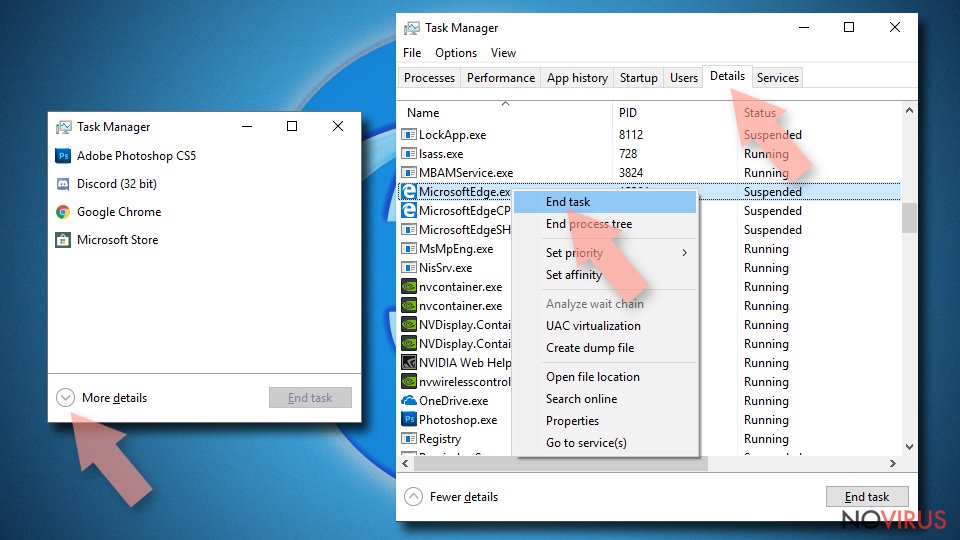
- Now scroll down and locate every entry with Microsoft Edge name in it.
- Right-click on each of them and select End Task to stop MS Edge from running.
When none of the above solves the issue, you might need an advanced Edge reset method, but you need to backup your data before proceeding.
- Find the following folder on the PC: C:\\Users\\%username%\\AppData\\Local\\Packages\\Microsoft.MicrosoftEdge_8wekyb3d8bbwe.
- Press Ctrl + A on your keyboard to select all folders.
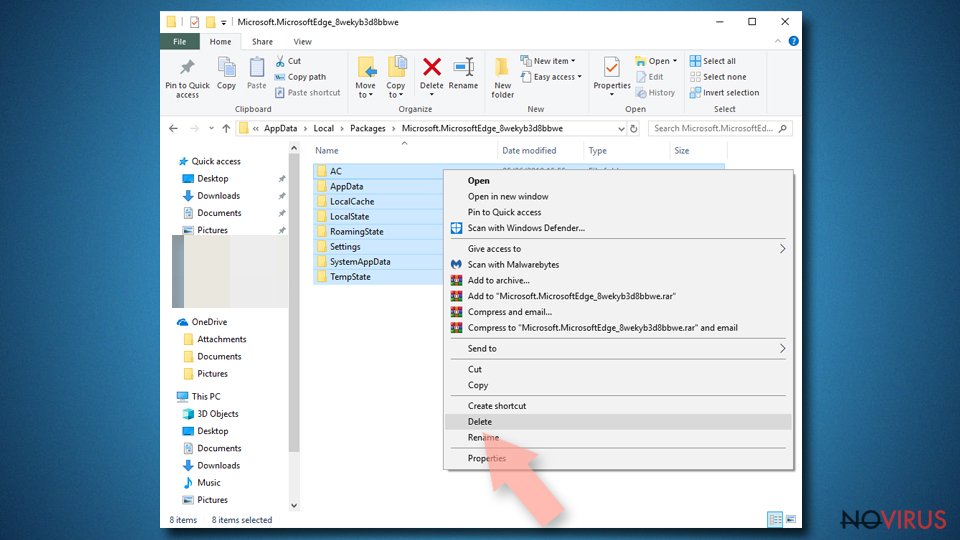
- Right-click on the selection and choose Delete
- Right-click on the Start button and pick Windows PowerShell (Admin).
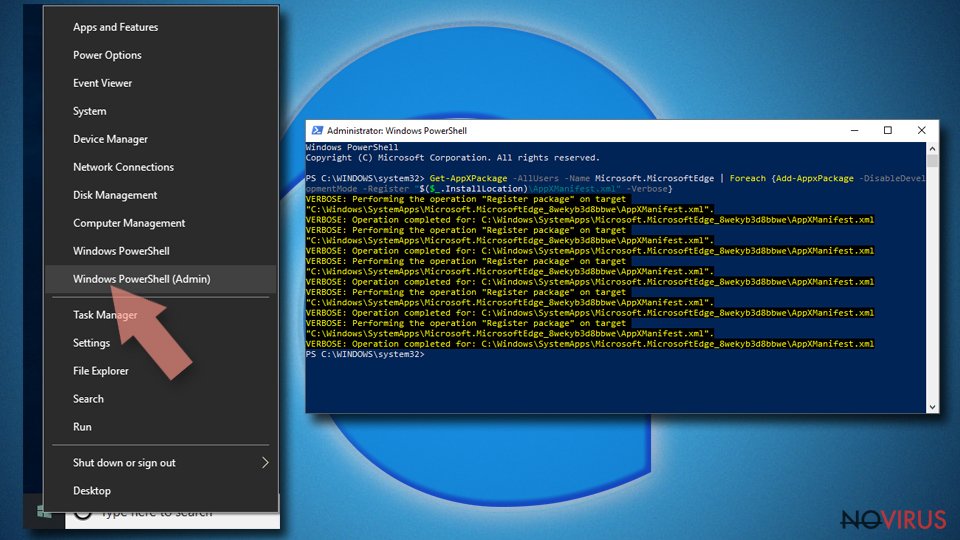
- Copy and paste the following command, and then press Enter:
Get-AppXPackage -AllUsers -Name Microsoft.MicrosoftEdge | Foreach {Add-AppxPackage -DisableDevelopmentMode -Register “$($_.InstallLocation)\\AppXManifest.xml” -Verbose
Instructions for Chromium-based Edge
Delete extensions:
- Open Edge and click Settings.
- Then find Extensions.
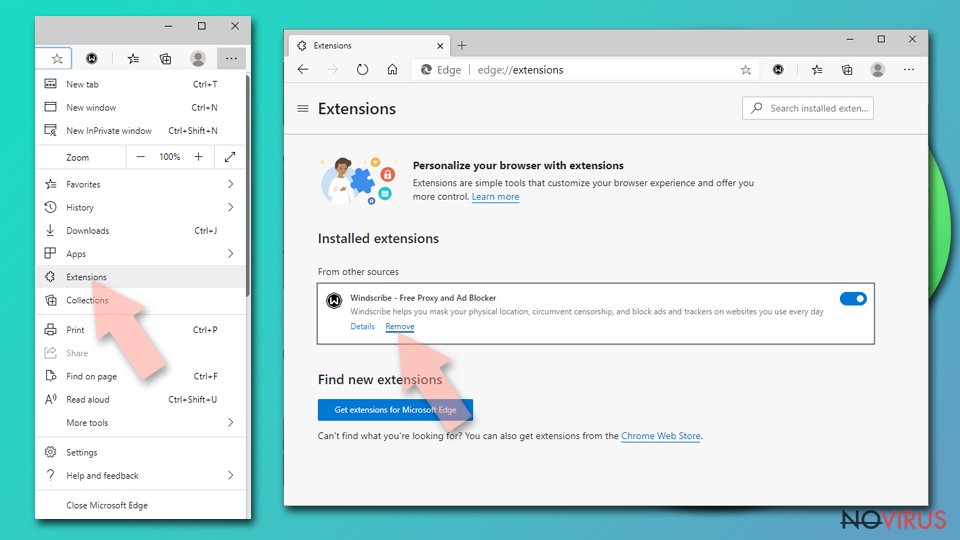
- Delete unwanted extensions with the Remove.
Clear cache and site data:
- Click on Menu and then Settings.
- Find Privacy and services.
- Locate Clear browsing data, then click Choose what to clear.
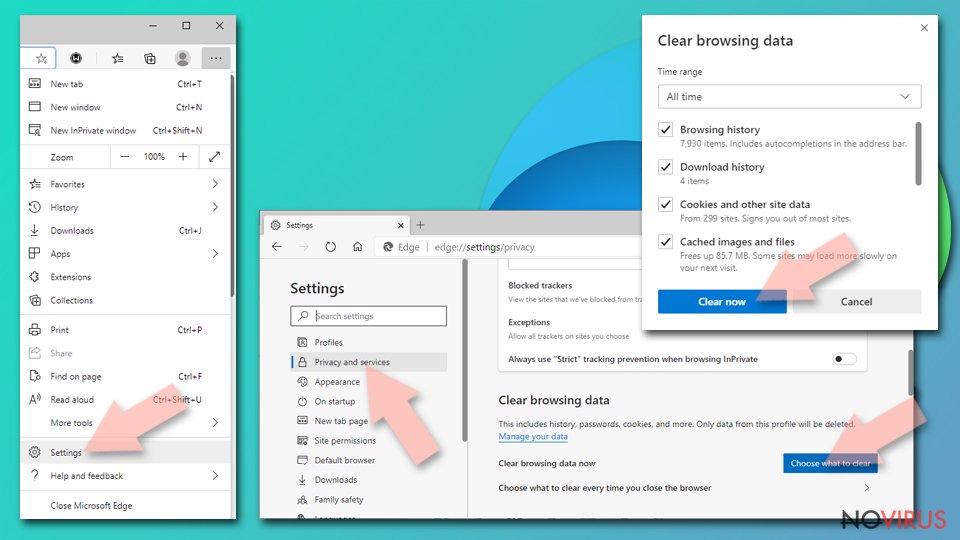
- Time range.
- Click All time.
- Select Clear now.
Reset Chromium-based MS Edge browser fully:
- Go to Settings.
- On the left side, choose Reset settings.
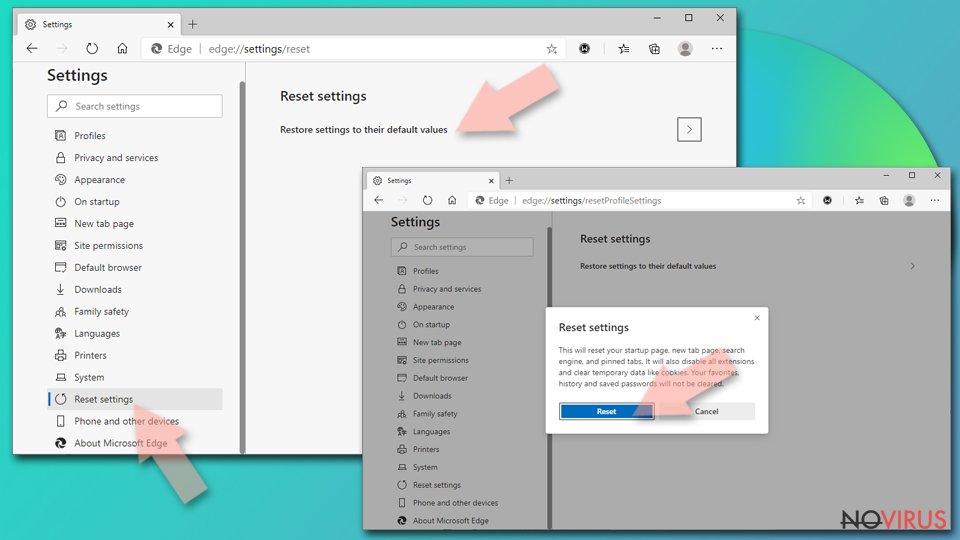
- Select Restore settings to their default values.
- Click Reset.
Delete SearchLock from Mozilla Firefox (FF)
Check the list of extensions. Do you see some suspicious entries? If yes, remove them as shown below because they may be related to the SearchLock hijacker.
Remove suspicious Firefox extensions:
- Open Mozilla Firefox browser and click on the three horizontal lines at the top-right to open the menu.
- Select Add-ons in the context menu.
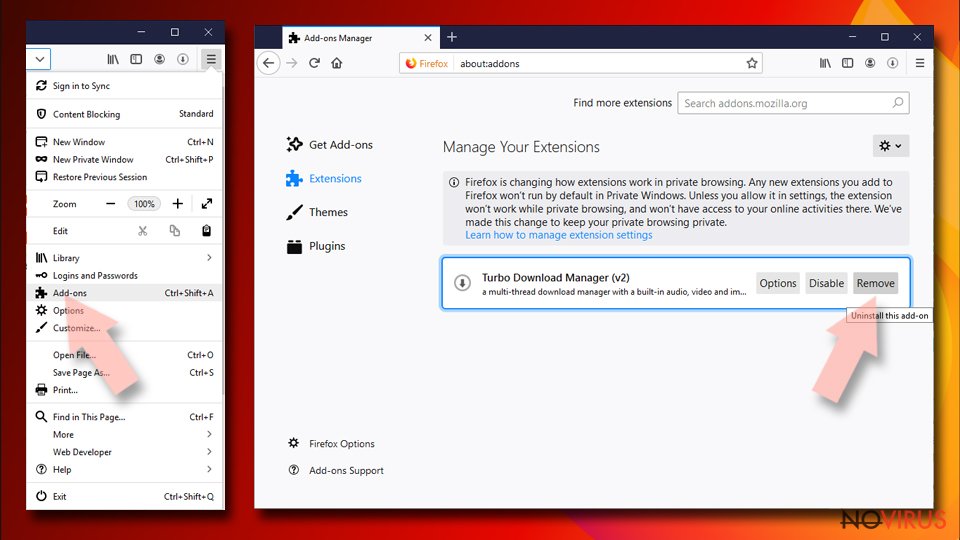
- Choose plugins that are creating issues and select Remove.
Reset the homepage on the browser:
- Click three horizontal lines at the top right corner.
- This time select Options.
- Under Home section, enter your preferred site for the homepage that will open every time you launch Mozilla Firefox.
Clear cookies and site data:
- Click Menu and pick Options.
- Find the Privacy & Security section.
- Scroll down to choose Cookies and Site Data.
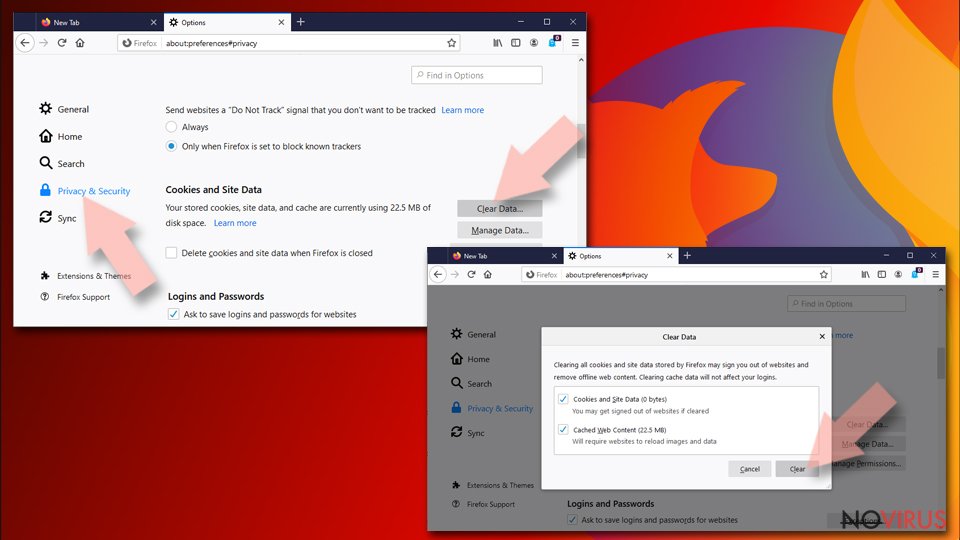
- Click on Clear Data… option.
- Click Cookies and Site Data, Cached Web Content and press Clear.
Reset Mozilla Firefox:
If none of the steps above helped you, reset Mozilla Firefox as follows:
- Open Mozilla Firefox and go to the menu.
- Click Help and then choose Troubleshooting Information.
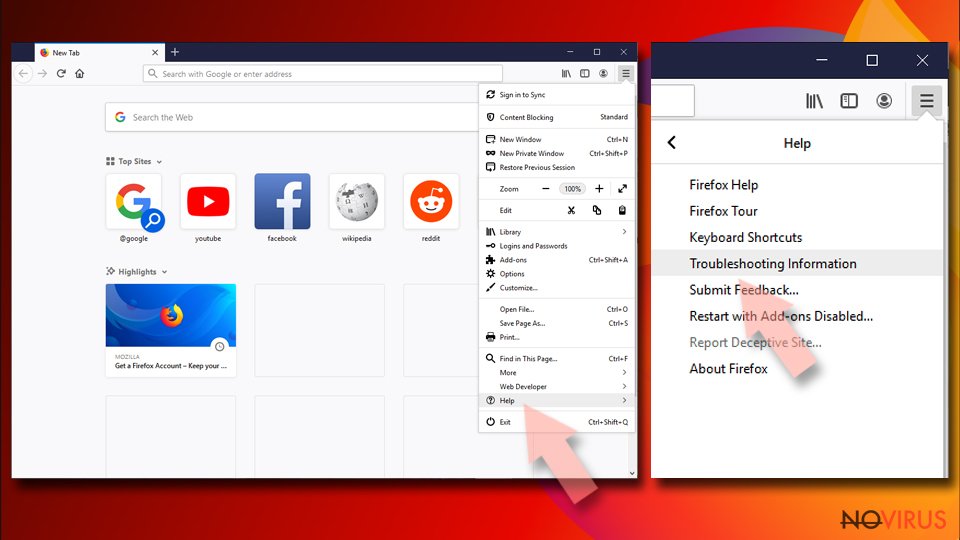
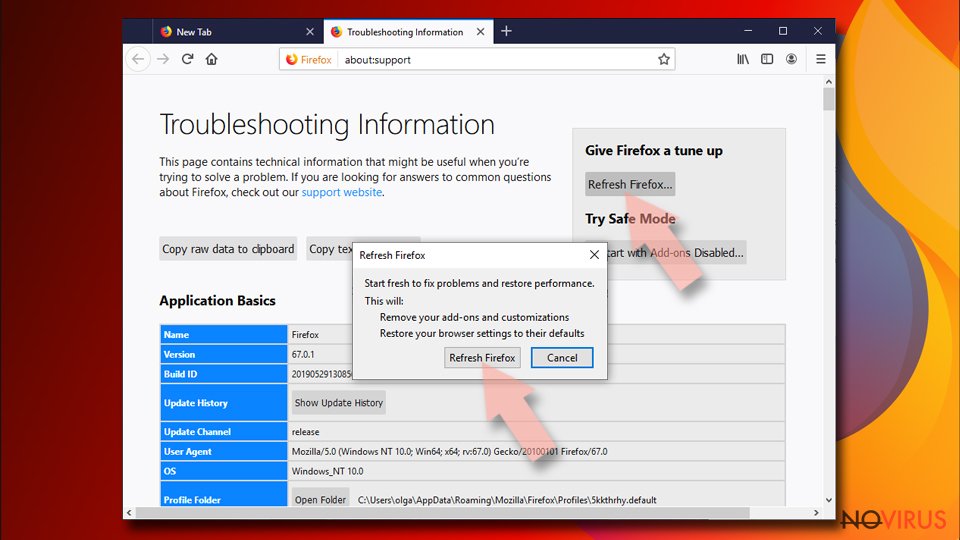
- Locate Give Firefox a tune-up section, click on Refresh Firefox…
- Confirm the action by pressing on Refresh Firefox on the pop-up.
Chrome browser reset
The hijacker may have installed questionable extensions and plugins, so your task is to remove them all.
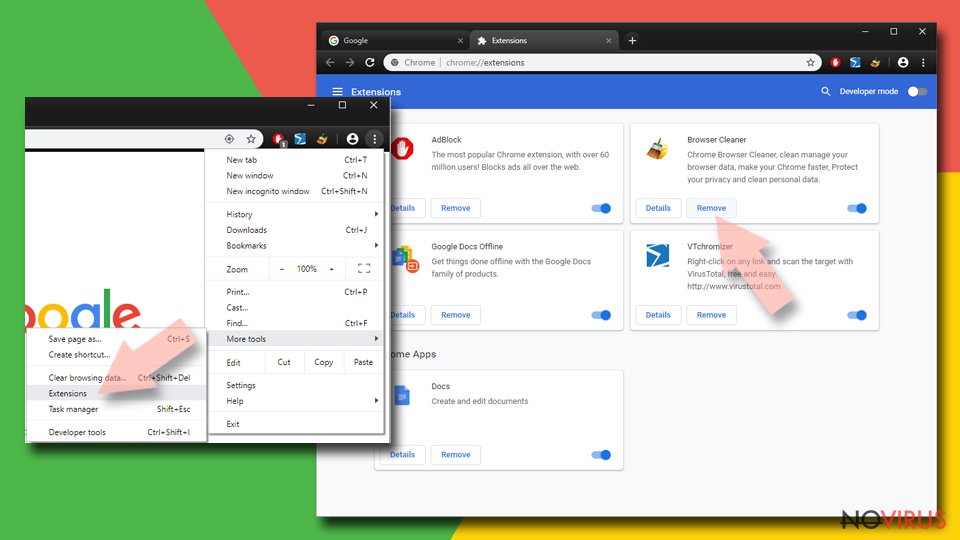
Find and remove suspicious extensions from Google Chrome:
- In Google Chrome, open the Menu by clicking three vertical dots at the top-right corner.
- Select More tools > Extensions.
- Once the window opens, you will see all the installed extensions.
- Find any suspicious add-ons related to any PUP.
- Uninstall them by clicking Remove.
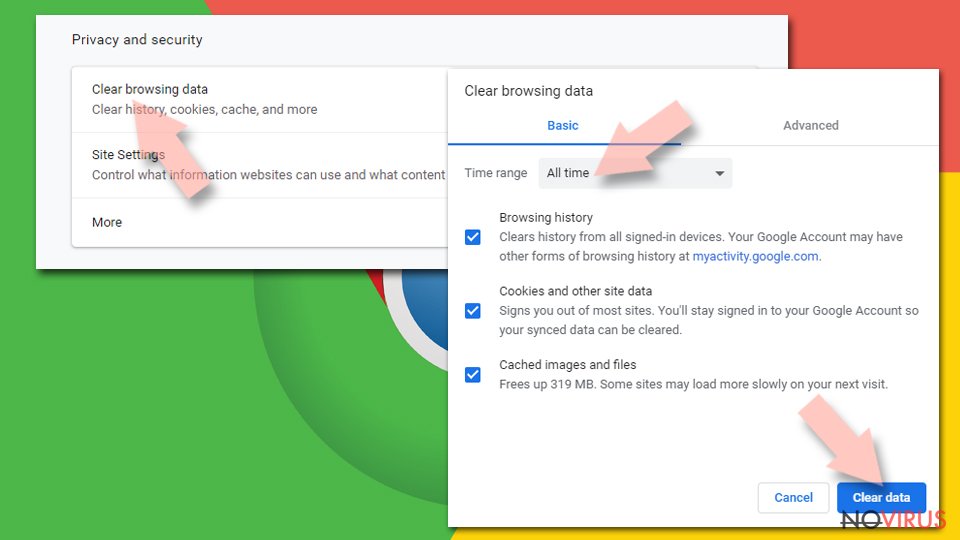
Clear cache and web data from Chrome:
- Click the Menu and select Settings.
- Find Privacy and security section.
- Choose Clear browsing data.
- Select Browsing history.
- Cookies and other site data, also Cached images and files.
- Click Clear data.
Alter settings of the homepage:
- Go to the menu and choose Settings.
- Find odd entries in the On startup section.
- Click on Open a specific or set of pages.
- Then click on three dots and look for the Remove option.
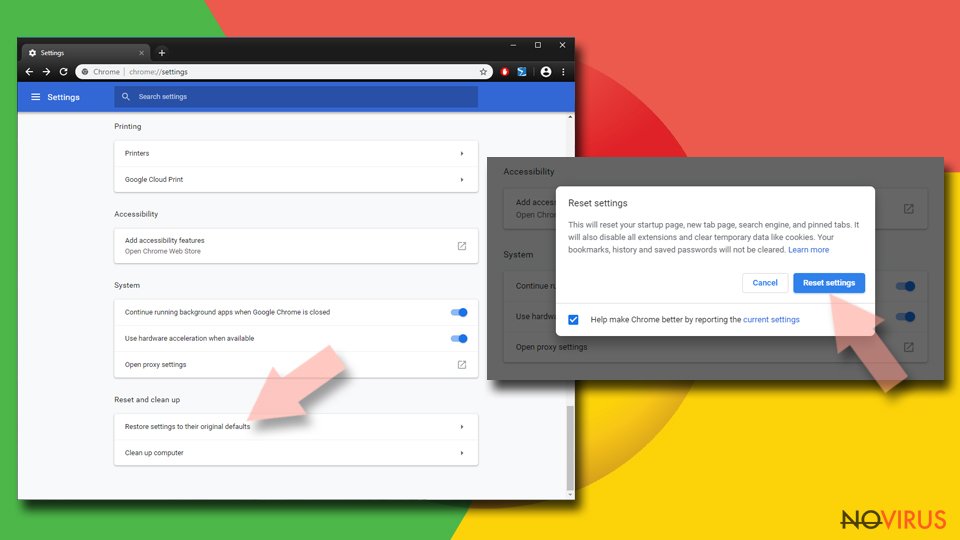
Reset Google Chrome fully:
You might need to reset Google Chrome and properly eliminate all the unwanted components:
- Go to Chrome Settings.
- Once there, scroll down to expand Advanced section.
- Scroll down to choose Reset and clean up.
- Click Restore settings to their original defaults.
- Click Reset settings again.
Delete SearchLock from Safari
Get rid of questionable extensions from Safari:
- Click Safari.
- Then go to Preferences…
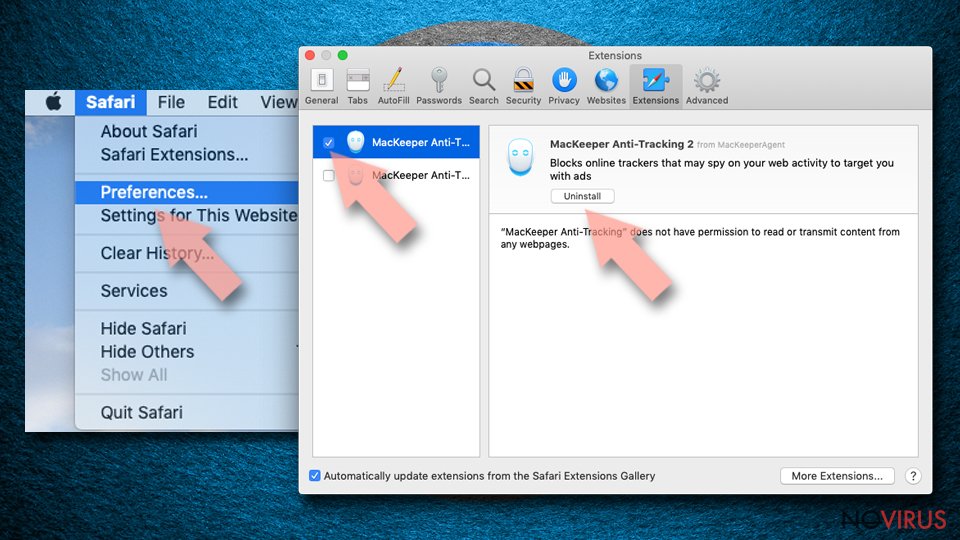
- Choose Extensions on the menu.
- Select the unwanted extension and then pick Uninstall.
Clear cookies from Safari:
- Click Safari.
- Choose Clear History…

- From the drop-down menu under Clear, find and pick all history.
- Confirm with Clear History.
Reset Safari fully:
- Click Safari and then Preferences…
- Choose the Advanced tab.
- Tick the Show Develop menu in the menu bar.
- From the menu bar, click Develop.
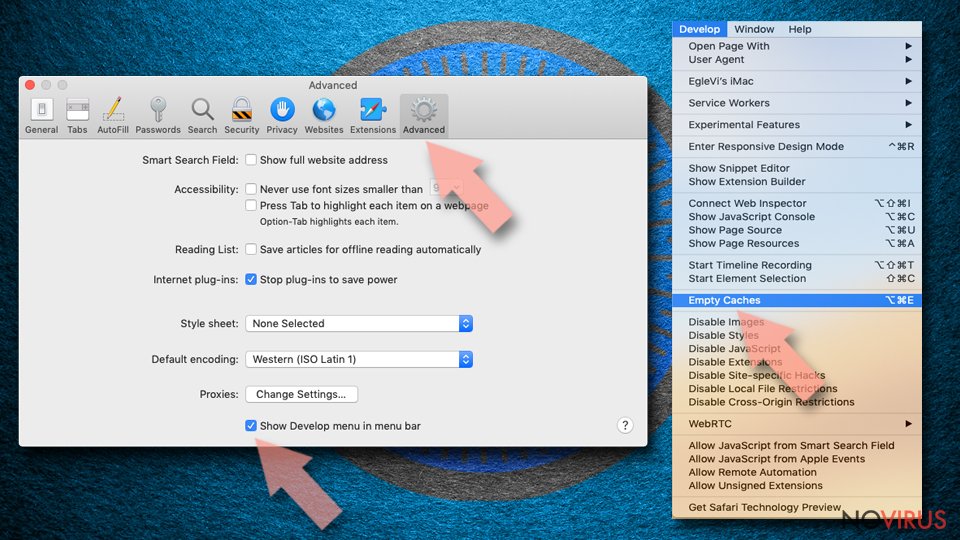
- Then select Empty Caches.
Even if you have completed all the steps above, we still strongly recommend you to scan your computer system with a powerful anti-malware software. It is advisable to do that because an automatic malware removal tool can detect and delete all remains of SearchLock, for instance, its registry keys. The anti-malware program can help you to easily detect and eliminate possibly dangerous software and malicious viruses in an easy way. You can use any of our top-rated malware removal programs: FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes.
How to prevent from getting browser hijacker
Securely connect to your website wherever you are
Sometimes you may need to log in to a content management system or server more often, especially if you are actively working on a blog, website, or different project that needs constant maintenance or that requires frequent content updates or other changes. Avoiding this problem can be easy if you choose a dedicated/fixed IP address. It's a static IP address that only belongs to a specific device and does not change when you are in different locations.
VPN service providers such as Private Internet Access can help you with these settings. This tool can help you control your online reputation and successfully manage your projects wherever you are. It is important to prevent different IP addresses from connecting to your website. With a dedicated/fixed IP address, VPN service, and secure access to a content management system, your project will remain secure.
Reduce the threat of viruses by backing up your data
Due to their own careless behavior, computer users can suffer various losses caused by cyber infections. Viruses can affect the functionality of the software or directly corrupt data on your system by encrypting it. These problems can disrupt the system and cause you to lose personal data permanently. There is no such threat if you have the latest backups, as you can easily recover lost data and get back to work.
It is recommended to update the backups in parallel each time the system is modified. This way, you will be able to access the latest saved data after an unexpected virus attack or system failure. By having the latest copies of important documents and projects, you will avoid serious inconveniences. File backups are especially useful if malware attacks your system unexpectedly. We recommend using the Data Recovery Pro program to restore the system.