Uninstall iPhone virus (Uninstall Instructions) - Free Removal Instructions
iPhone virus Removal Guide
Description of iPhone malware
While many might not believe — iPhone virus exists!

iPhone virus is a malicious program which is designed explicitly for iOS users. It can appear in the form of a pop-up, fake security alarm or hide its presence on the compromised smartphone. According to experts, the malware can even be unconsciously distributed by known application developers in the App Store.
There are several techniques to get rid off all its variants. You can check the detailed guidelines provided below.
The most prevalent iPhone virus variant bothers users via Safari browser. Typically, it opens deceptive pop-ups and informs about malware/spyware detected on the device. Other rogue viruses display deceptive “Congratulations, You are today's lucky visitor!” messages, asking the victim to claim the “prize” within seconds.
These false virus alarm messages are just a marketing trick to lure users into downloading potentially malicious programs and generate revenue for their developers. Such viruses try to convey a sense of urgency and force the victim to follow deceptive commands that can eventually lead to data loss or a severe phone infection. You should never let it deceive you.
It is highly recommended to stay away from “iPhone virus warning” pop-ups. If you accidentally encountered one of them, close the page displaying it. The next step is to check your device for suspicious programs or corrupted settings that cause Safari to display the described pop-ups.
If you have never encountered a similar problem before and now you do not know how to remove iPhone virus, we suggest using instructions provided right below the description of this iOS threat.
Spyware for iOS actually exists
One of the most significant proofs that iPhones have their vulnerabilities and can be circumvented — CIA spyware. It was initially designed to transmit audio/text messages, geolocation, together to activate user's camera and microphone remotely.
The hacking tools used were developed by the Central Intelligence Agency (CIA) or purchased from the underground shops such as Baitshop. Moreover, the press release states that NSA and FBI supplied their arsenal to produce CIA malware as well.
Also, another variant of iPhone virus is Pegasus spyware. Researchers believe that NSO group company developed the malware, which takes advantage of ‘zero-day’ iOS vulnerabilities that are also known as ‘Trident’ and performed an attack to break through Apple’s security system. Additionally, the malicious program can stealthily destruct itself, if there is a risk to be exposed.
Similarly, as the CIA spyware, Pegasus operates to secretly transmit texts, audio and video calls, e-mails and all data on the device to the developers. It targets people working in the political sphere as well as CEOs that can provide valuable information.
Therefore, if you want to take care of your privacy, we strongly recommend you to start an iPhone virus removal process. Use the guide provided below and also scan your OS devices using FortectIntego or any other reliable security software.
The most annoying versions of iPhone virus
Free iPhone X scam. It is a new variant of iPhone virus developed to swindle money from inexperienced Apple fans. Scammers share the fake Facebook or Instagram pages offering to complete surveys. Once the user fills out the deceptive poll, s/he is redirected to a website asking to provide personal information in order to send the “prize.” Typically, these scam giveaways collect personal details and sell it in the underground market.
Additionally, the fake pages and accounts on social media can invite naive people to click on fraudulent links that might lead to malicious web pages. It goes without saying that visiting these sites increases the chances of infecting the computer unknowingly.
Finally, fake pages can be used to collect likes or followers. As a result, a fraudulent page with thousands of followers can be sold on the dark web forums and used for illegal projects.
“YOUR APPLE DEVICE HAS A VIRUS” virus. The malicious program appears in the form of a pop-up notification. This fake alert claims that your device is infected with the above mentioned Pegasus spyware and states that you need to contact “Apple Care” via +1 8333 370 777.
At this point, we want to assure you that your system is not corrupted. It is just a way scammers tend to lure people into giving remote access to their computer or purchasing useless and expensive security software to remove a non-existing malware.
“Apple Security Alert” virus. This variant of iPhone virus is a pure tech support scam virus which also tries to attack its victims by loading malicious websites via Safari. The user encounters a genuine looking fake security alarm that informs about the Trojan found on his/her gadget.
Later, the pop-up offers to start the “cleaning” process by pressing the “OK” button. Be aware that there is no reliable information about the “infections” found by these false pop-ups.
Your iPhone is not corrupted, and you shouldn’t let scammers deceive you into downloading possibly malicious apps or other high-risk computer infections.

Malware is distributed by taking advantage of authorized app developers
According to the analysts, cybercriminals created a new way to infect the system of Apple devices — they infiltrated XCodeGhost malware to the Xcode programs used by verified app developers. Thus, multiple regular applications were stealthily exploited to distribute malware on App Store. Once, Apple support was informed, several hundreds of software were eliminated.
However, shortly after, criminals copied third-party development framework (also known as Unity) and modified it similarly as Xcode programs. This new variant was called UnityGhost and distributed using the same method as its precursor. You should always be aware of the possible threats and carefully download apps to your phone.
There is no surprise why so many Apple smartphone users are interested “can iPhones get viruses from websites.” The answer is yes, in fact, they can. You can run into virus alerts while exploring shady Internet websites. We recommend avoiding ads promoted by suspicious websites since they may trigger redirects to phishing domains.
These usually display fake alarms designed to swindle money from you. Typically, they ask to contact “tech support” which will tell you to purchase useless apps. Other pop-ups might lead you to pages asking to provide sensitive information – make sure you close them immediately!
Get rid of different variants of iPhone virus
To start a process of a pop-up type iPhone virus removal, you should double-click the ‘Home’ button and close the Safari app by swiping it up. Later, follow the steps:
Settings>Safari>Clear History and Website Data;
Also, if you have noticed that the data on your device might be accessed by malevolent people or any other unusual behaviour of your mobile, remove iPhone virus using the steps below:
Settings>General>Erase All Contents.
You may remove virus damage with a help of FortectIntego. SpyHunter 5Combo Cleaner and Malwarebytes are recommended to detect potentially unwanted programs and viruses with all their files and registry entries that are related to them.
Getting rid of iPhone virus. Follow these steps
Uninstall iPhone in Windows systems
Terminate suspicious programs from Windows 10/8 machines by following these instructions:
- Type Control Panel into Windows search and once the result shows up hit Enter.
- Under Programs, choose Uninstall a program.
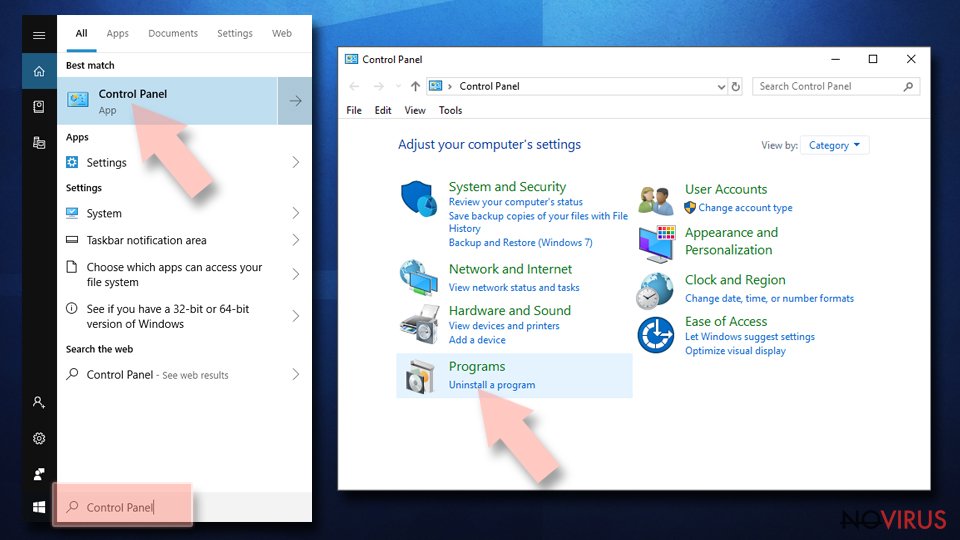
- Find components related to suspicious programs.
- Right-click on the application and select Uninstall.
- Click Yes when User Account Control shows up.
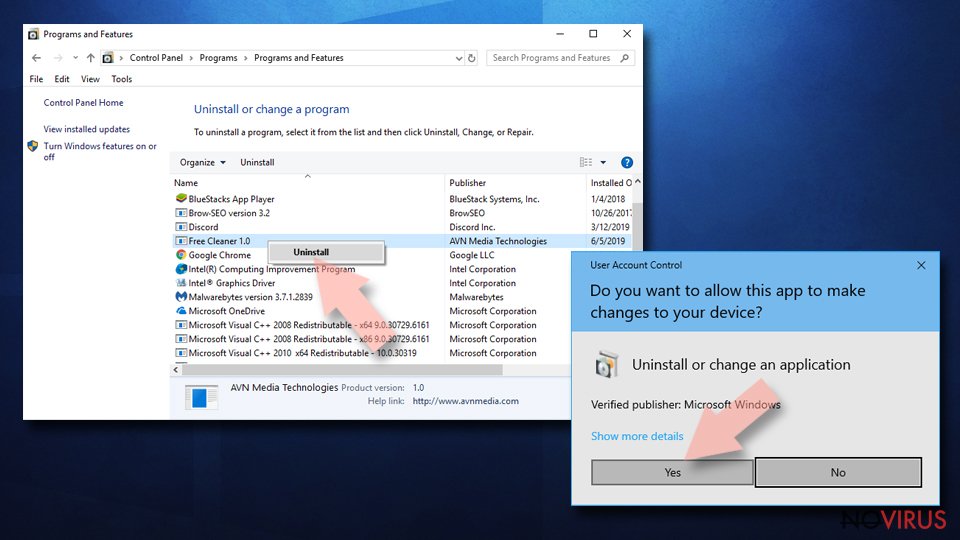
- Wait for the process of uninstallation to be done and click OK.
Windows 7/XP instructions:
- Click on Windows Start and go to Control Panel on the right pane.
- Choose Add/Remove Programs.
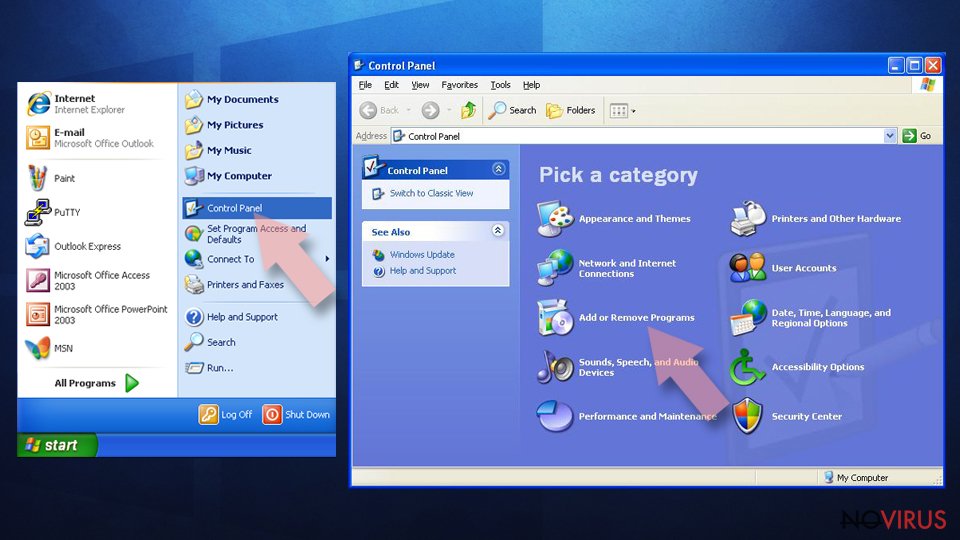
- Select Uninstall a program under Programs in Control Panel.
- Click once on the unwanted application.
- Click Uninstall/Change at the top.
- Confirm with Yes.
- Click OK and finish the removal.
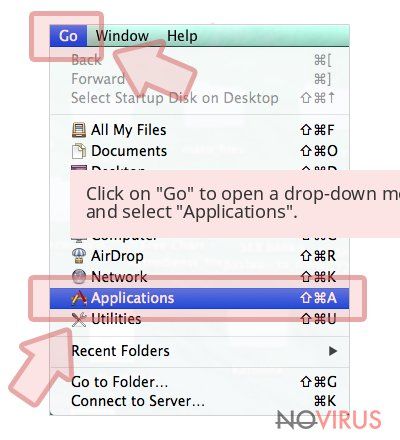
Uninstall iPhone in Mac OS X system
-
Users who use OS X should click on Go button, which can be found at the top left corner of the screen and select Applications.

-
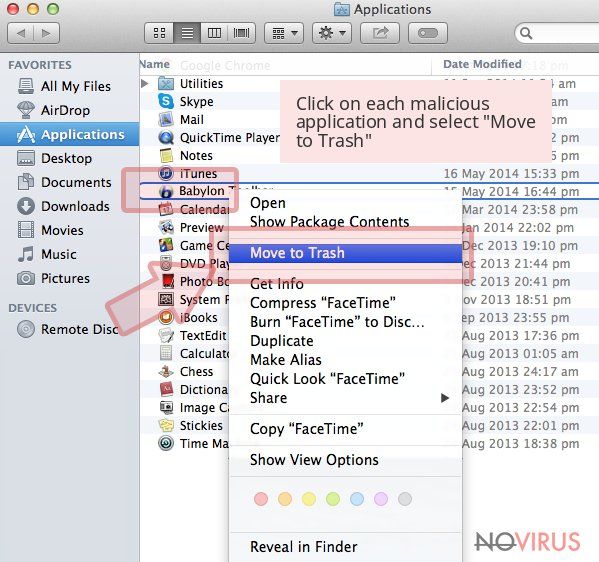
Wait until you see Applications folder and look for iPhone or any other suspicious programs on it. Now right click on every of such entries and select Move to Trash.

Eliminate iPhone virus from Microsoft Edge browser
Delete suspicious extensions from MS Edge:
- Go to the Menu by clicking on the three horizontal dots at the top-right.
- Then pick Extensions.
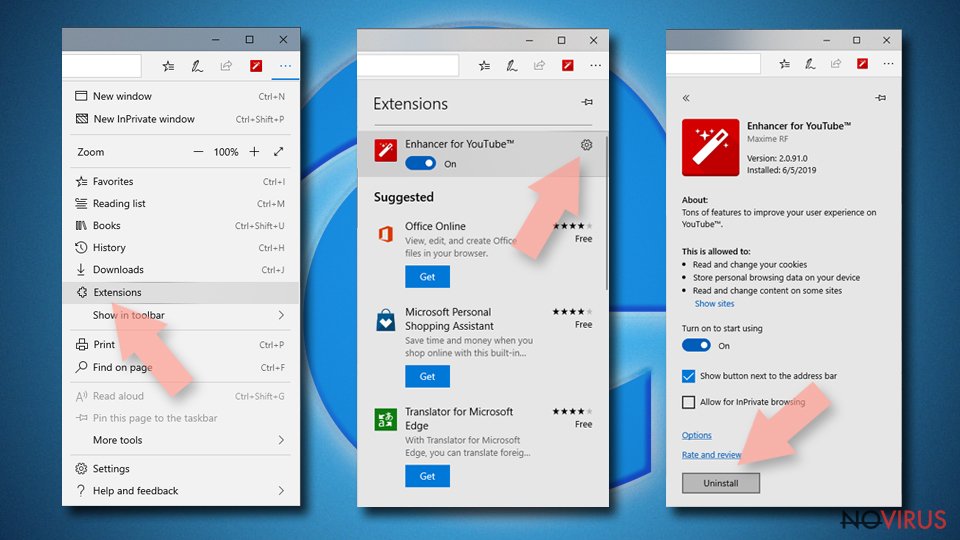
- Choose the unwanted add-ons on the list and click on the Gear icon.
- Click on Uninstall at the bottom.
Clear cookies and other data:
- Click on the Menu and from the context menu select Privacy & security.
- Under Clear browsing data, select Choose what to clear.
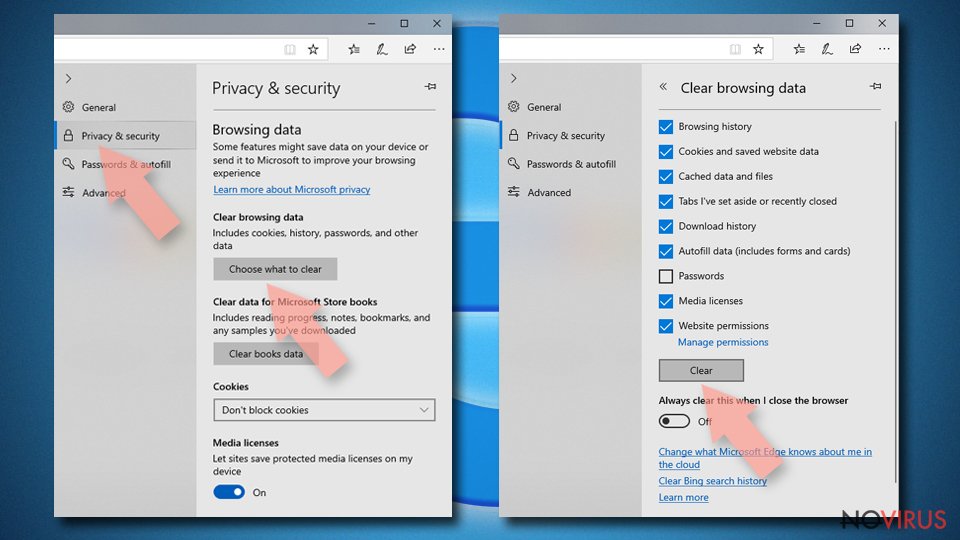
- Choose everything except passwords, and click on Clear.
Alter new tab and homepage settings:
- Click the menu icon and choose Settings.
- Then find On startup section.
- Click Disable if you found any suspicious domain.
Reset MS Edge fully:
- Click on the keyboard Ctrl + Shift + Esc to open Task Manager.
- Choose More details arrow at the bottom.
- Go to Details tab.
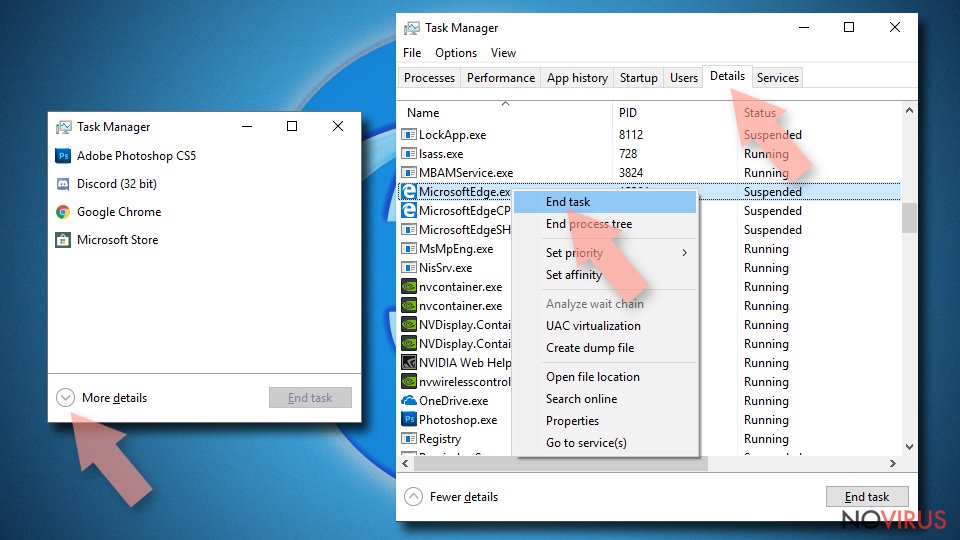
- Now scroll down and locate every entry with Microsoft Edge name in it.
- Right-click on each of them and select End Task to stop MS Edge from running.
When none of the above solves the issue, you might need an advanced Edge reset method, but you need to backup your data before proceeding.
- Find the following folder on the PC: C:\\Users\\%username%\\AppData\\Local\\Packages\\Microsoft.MicrosoftEdge_8wekyb3d8bbwe.
- Press Ctrl + A on your keyboard to select all folders.
- Right-click on the selection and choose Delete
- Right-click on the Start button and pick Windows PowerShell (Admin).
- Copy and paste the following command, and then press Enter:
Get-AppXPackage -AllUsers -Name Microsoft.MicrosoftEdge | Foreach {Add-AppxPackage -DisableDevelopmentMode -Register “$($_.InstallLocation)\\AppXManifest.xml” -Verbose
Instructions for Chromium-based Edge
Delete extensions:
- Open Edge and click Settings.
- Then find Extensions.
- Delete unwanted extensions with the Remove.
Clear cache and site data:
- Click on Menu and then Settings.
- Find Privacy and services.
- Locate Clear browsing data, then click Choose what to clear.
- Time range.
- Click All time.
- Select Clear now.
Reset Chromium-based MS Edge browser fully:
- Go to Settings.
- On the left side, choose Reset settings.
- Select Restore settings to their default values.
- Click Reset.
Delete iPhone from Mozilla Firefox (FF)
Remove suspicious Firefox extensions:
- Open Mozilla Firefox browser and click on the three horizontal lines at the top-right to open the menu.
- Select Add-ons in the context menu.
- Choose plugins that are creating issues and select Remove.
Reset the homepage on the browser:
- Click three horizontal lines at the top right corner.
- This time select Options.
- Under Home section, enter your preferred site for the homepage that will open every time you launch Mozilla Firefox.
Clear cookies and site data:
- Click Menu and pick Options.
- Find the Privacy & Security section.
- Scroll down to choose Cookies and Site Data.
- Click on Clear Data… option.
- Click Cookies and Site Data, Cached Web Content and press Clear.
Reset Mozilla Firefox:
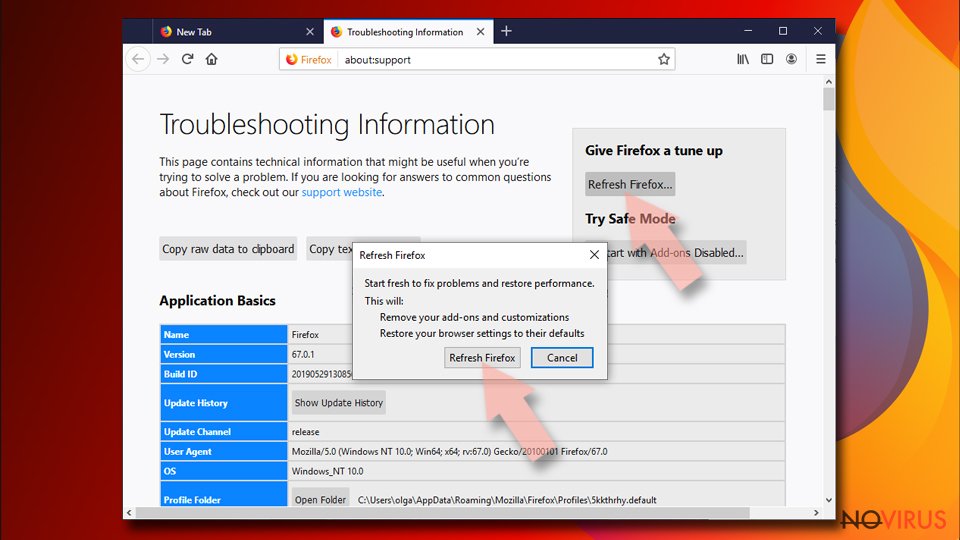
If none of the steps above helped you, reset Mozilla Firefox as follows:
- Open Mozilla Firefox and go to the menu.
- Click Help and then choose Troubleshooting Information.
- Locate Give Firefox a tune-up section, click on Refresh Firefox…
- Confirm the action by pressing on Refresh Firefox on the pop-up.
Chrome browser reset
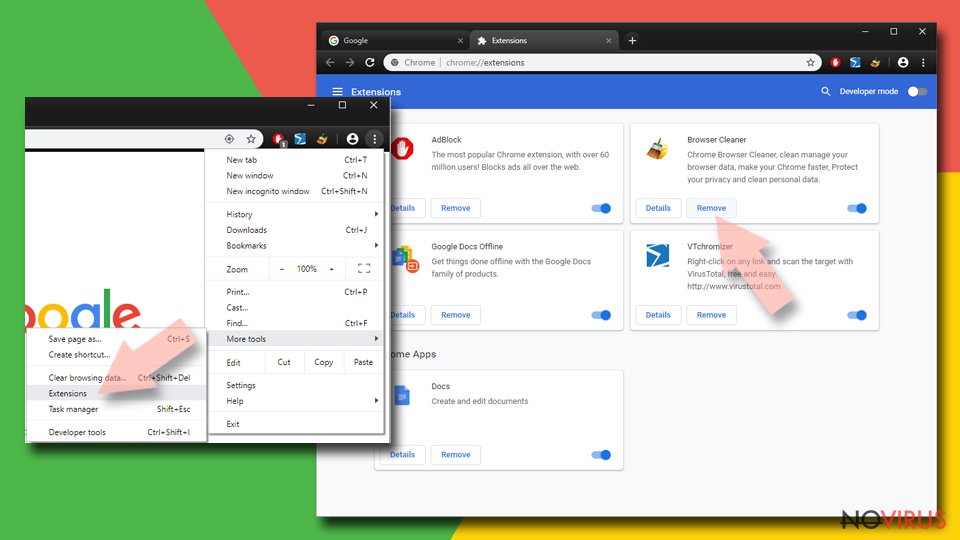
Find and remove suspicious extensions from Google Chrome:
- In Google Chrome, open the Menu by clicking three vertical dots at the top-right corner.
- Select More tools > Extensions.
- Once the window opens, you will see all the installed extensions.
- Find any suspicious add-ons related to any PUP.
- Uninstall them by clicking Remove.
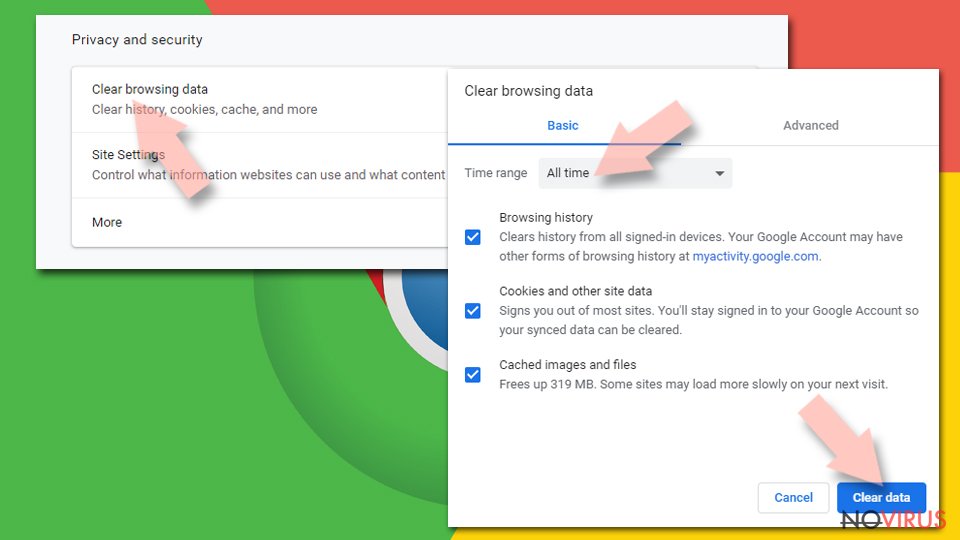
Clear cache and web data from Chrome:
- Click the Menu and select Settings.
- Find Privacy and security section.
- Choose Clear browsing data.
- Select Browsing history.
- Cookies and other site data, also Cached images and files.
- Click Clear data.
Alter settings of the homepage:
- Go to the menu and choose Settings.
- Find odd entries in the On startup section.
- Click on Open a specific or set of pages.
- Then click on three dots and look for the Remove option.
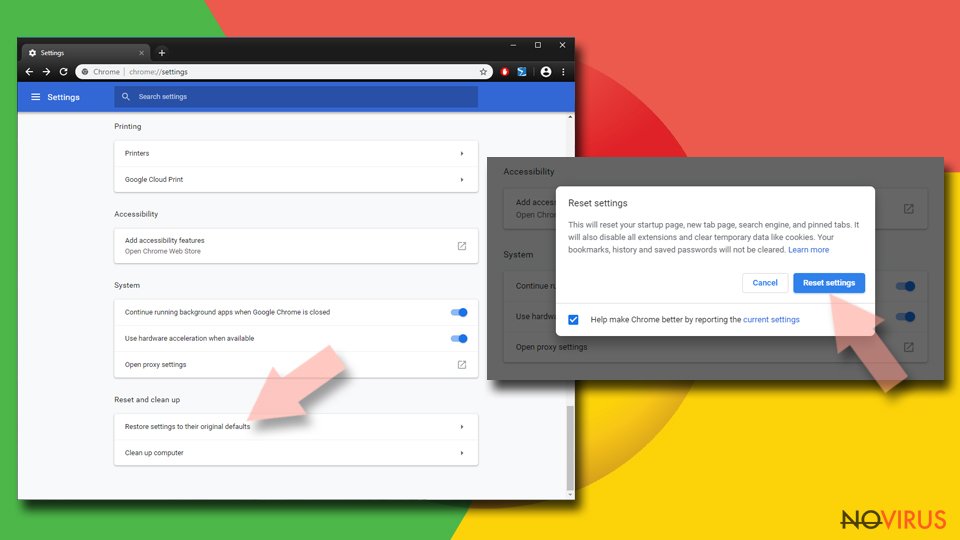
Reset Google Chrome fully:
You might need to reset Google Chrome and properly eliminate all the unwanted components:
- Go to Chrome Settings.
- Once there, scroll down to expand Advanced section.
- Scroll down to choose Reset and clean up.
- Click Restore settings to their original defaults.
- Click Reset settings again.
Delete iPhone from Safari
Get rid of questionable extensions from Safari:
- Click Safari.
- Then go to Preferences…
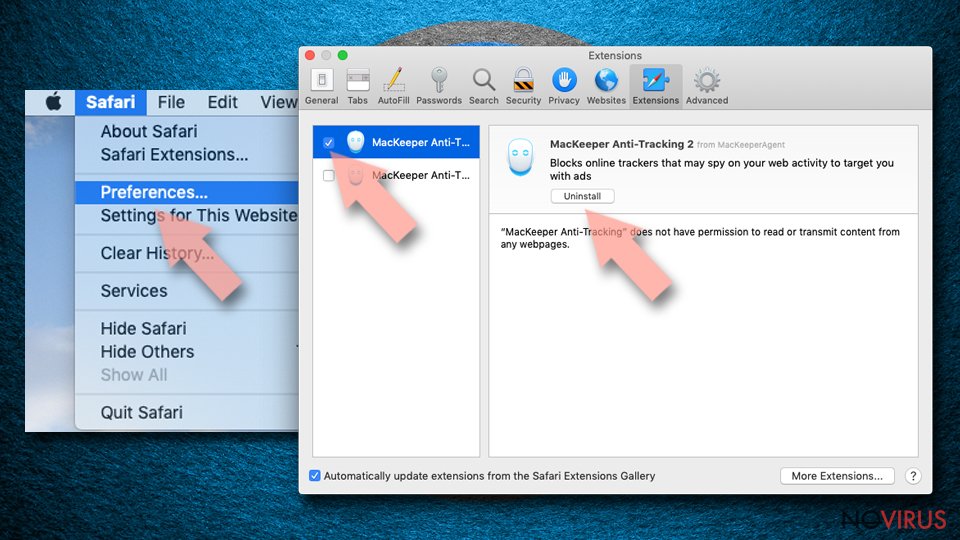
- Choose Extensions on the menu.
- Select the unwanted extension and then pick Uninstall.
Clear cookies from Safari:
- Click Safari.
- Choose Clear History…

- From the drop-down menu under Clear, find and pick all history.
- Confirm with Clear History.
Reset Safari fully:
- Click Safari and then Preferences…
- Choose the Advanced tab.
- Tick the Show Develop menu in the menu bar.
- From the menu bar, click Develop.
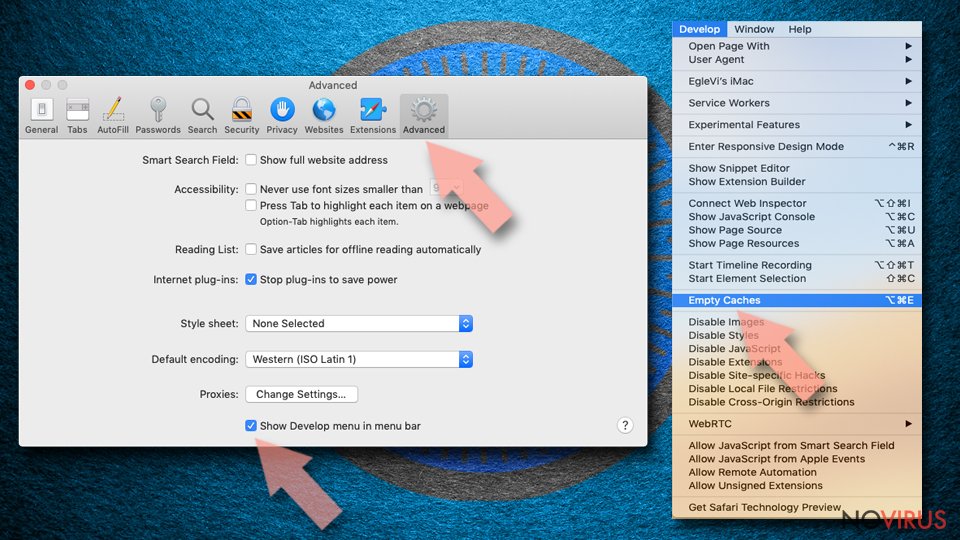
- Then select Empty Caches.
Even if you have completed all the steps above, we still strongly recommend you to scan your computer system with a powerful anti-malware software. It is advisable to do that because an automatic malware removal tool can detect and delete all remains of iPhone, for instance, its registry keys. The anti-malware program can help you to easily detect and eliminate possibly dangerous software and malicious viruses in an easy way. You can use any of our top-rated malware removal programs: FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes.
How to prevent from getting malware
Prevent the government from spying on you
As there is a growing debate in government about collecting users' data and spying on citizens, you should take a closer look at this issue and find out what shady ways of gathering information can be used to collect information about you. You need to browse anonymously if you want to avoid any government-initiated spying and tracking of information.
You can enjoy secure internet browsing and minimize the risk of intrusion into your system if you use Private Internet Access VPN program. This VPN application creates a virtual private network and provides access to the required data without any content restrictions.
Control government and other third party access to your data and ensure safe web browsing. Even if you do not engage in illegal activities and trust your ISP, we recommend being careful about your security. You should take extra precautions and start using a VPN program.
Reduce the threat of viruses by backing up your data
Due to their own careless behavior, computer users can suffer various losses caused by cyber infections. Viruses can affect the functionality of the software or directly corrupt data on your system by encrypting it. These problems can disrupt the system and cause you to lose personal data permanently. There is no such threat if you have the latest backups, as you can easily recover lost data and get back to work.
It is recommended to update the backups in parallel each time the system is modified. This way, you will be able to access the latest saved data after an unexpected virus attack or system failure. By having the latest copies of important documents and projects, you will avoid serious inconveniences. File backups are especially useful if malware attacks your system unexpectedly. We recommend using the Data Recovery Pro program to restore the system.