Uninstall Chromium virus (Chrome, Firefox, IE, Edge) - 2017 updated
Chromium virus Removal Guide
Description of Chromium malware
Most important information about Chromium virus

Chromium virus is a term that defines a sneaky spyware or malware program that replaces real Chrome browser with a modified copy of it. If you didn’t know this yet. Google Chrome browser draws its source code from Chromium browser project; however, anyone who wants to use the Chromium open-source code can do so. Sadly, this code is often exploited by not-so-good people, and we have seen many Chromium versions that simply work as ad-supported spyware-type tools that generate pay-per-click revenue for their authors.
Despite that Chromium project is entirely legitimate, its spin-offs can cause a lot of problems to you, and you might not even realise what causes them. You can read in detail descriptions of a few examples of Chromium browser spin-offs here: Chroomium browser virus, eFast browser. The worst part about these shady programs is that they can overwrite real Chrome browser version and place modified shortcuts instead of real ones.
Consequently, you might start using a fake Chrome copy without realising it. However, sooner or later browser reveals its true purpose – it starts displaying annoying ads, delivers modified search results, and injects sponsored content here and there every once in a while. Sometimes, you can unveil the truth by accessing browser’s “About” panel, but users do not visit this panel too often.
If you suspect that your Chrome browser behaves in a strange way and that it shouldn’t function the way it does, scan the system with an anti-spyware program, for instance, FortectIntego, and find out what happened to Chrome. Anti-spyware or anti-malware programs can help you to remove Chromium malware quickly. We added manual Chromium virus removal tutorial below this post, however, typically these viruses are hard to remove, and in such cases, automatic spyware removal programs come in handy.
These suspicious web browser might be trying to collect personally non-identifiable information such as what links do you click on, what search phrases you use, what operating system do you use, and so on. Collected data might be transmitted to third-party companies and used for market research, however, you can never know who might be interested in it and how it can be used at the end of the day.
Based on collected data, Chromium viruses might try to select catchy third-party ads and display them for you. However, remember that even if ads can look catchy, it doesn’t mean they are supposed to deliver you the best offers – they might be used as bait to convince you to click on them. You might just be redirected to hazardous websites.
General advice on how to avoid dangerous Chromium browser modifications
In short, you should watch what you click on and what files you agree to download from the Internet. We strongly advise you to save your downloads before opening them, because this way you will give your antivirus or anti-malware program to check the file and determine whether it is dangerous or not.
What is more, we advise you to modify settings in software installers at all times because Default/Standard/Basic/Recommended ones are simply designed for the software developer’s benefit. In other words, if the developer of your downloaded software collaborates with developers of ad-supported programs, he/she will use its power and supplement these installation settings with pre-selected user’s agreements to install suggested (or “recommended”) third-party software for free.
To reject bundled applications, access Custom/Advanced settings first and remove ticks from checkboxes next to suggested additional programs.
Best way to remove Chromium virus
Dealing with Chromium virus virus can be a nightmare. Such programs can add additional files to your system that helps to confuse you and keep you as a client of Chromium virus for a long time. To remove Chromium virus, we suggest using anti-malware or anti-spyware programs.
To identify the threat, just run a system scan with recommended software and wait until it finishes checking all system folders. After that, remove detected threats with a single mouse click.
You may remove virus damage with a help of FortectIntego. SpyHunter 5Combo Cleaner and Malwarebytes are recommended to detect potentially unwanted programs and viruses with all their files and registry entries that are related to them.
Getting rid of Chromium virus. Follow these steps
Uninstall Chromium in Windows systems
The best way to remove Chromium virus is to allow anti-malware software do it. Please do not try to find and delete Chromium browser related files by yourself – you can easily delete the wrong files and cause even more problems!
Terminate suspicious programs from Windows 10/8 machines by following these instructions:
- Type Control Panel into Windows search and once the result shows up hit Enter.
- Under Programs, choose Uninstall a program.
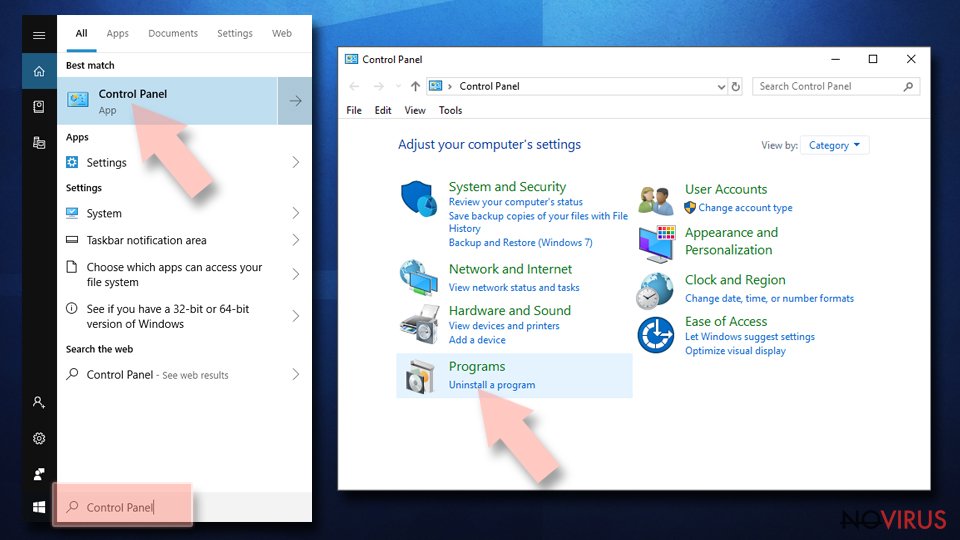
- Find components related to suspicious programs.
- Right-click on the application and select Uninstall.
- Click Yes when User Account Control shows up.
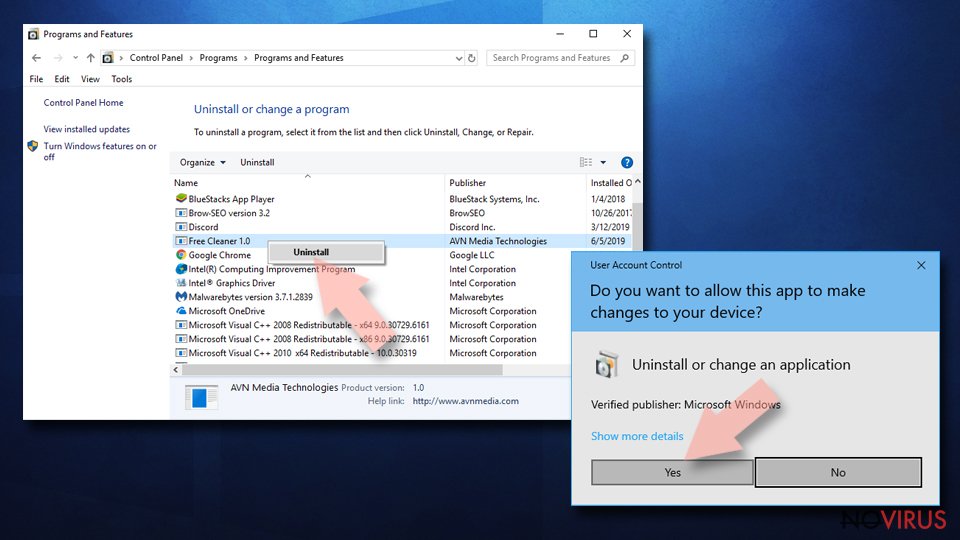
- Wait for the process of uninstallation to be done and click OK.
Windows 7/XP instructions:
- Click on Windows Start and go to Control Panel on the right pane.
- Choose Add/Remove Programs.
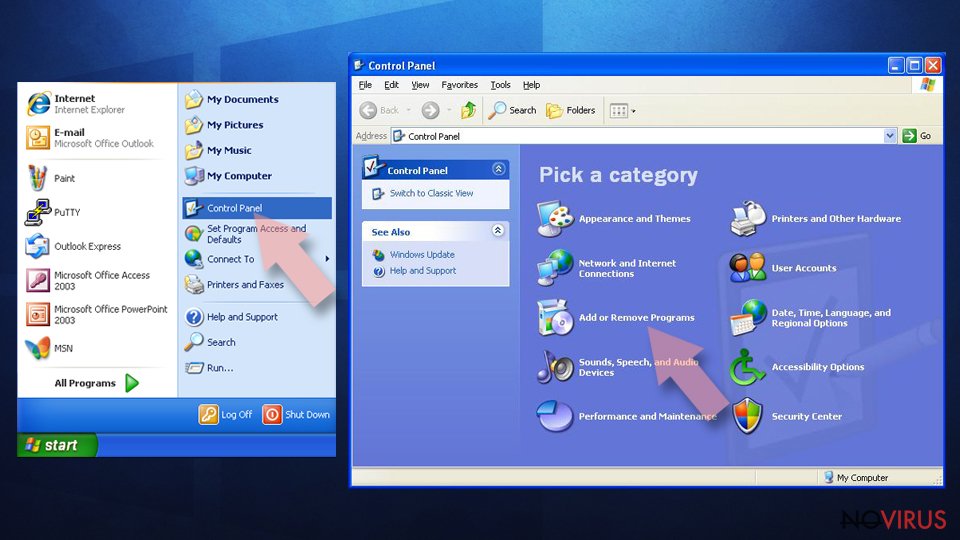
- Select Uninstall a program under Programs in Control Panel.
- Click once on the unwanted application.
- Click Uninstall/Change at the top.
- Confirm with Yes.
- Click OK and finish the removal.
Uninstall Chromium in Mac OS X system
-
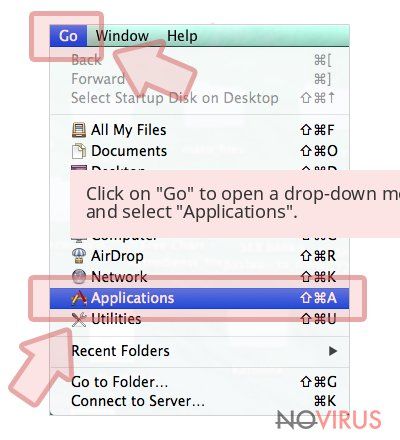
Users who use OS X should click on Go button, which can be found at the top left corner of the screen and select Applications.

-
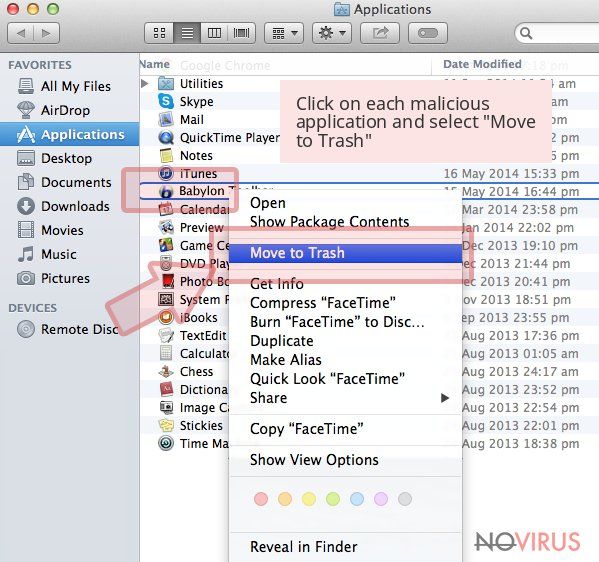
Wait until you see Applications folder and look for Chromium or any other suspicious programs on it. Now right click on every of such entries and select Move to Trash.

Chrome browser reset
If you suspect that your browser is infected/replaced, scan the system with anti-malware program.
Find and remove suspicious extensions from Google Chrome:
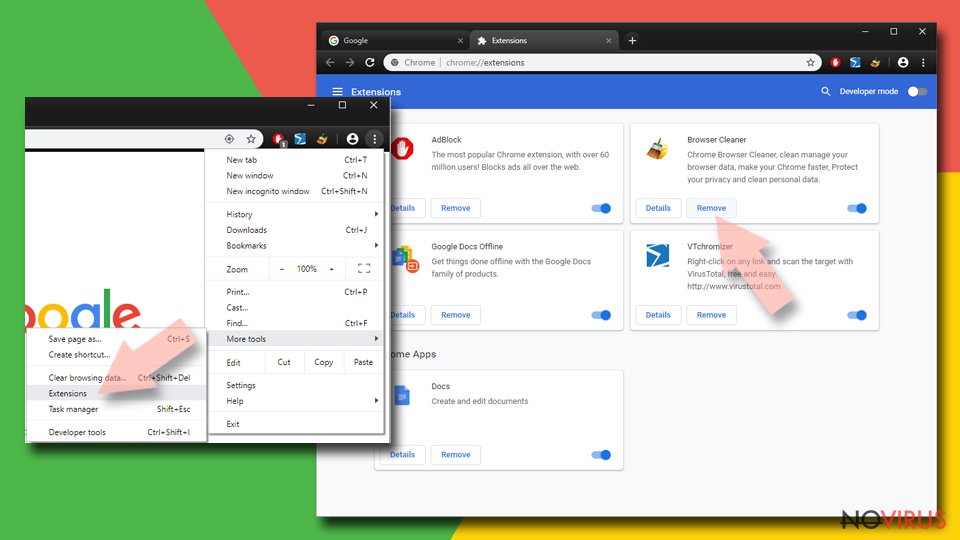
- In Google Chrome, open the Menu by clicking three vertical dots at the top-right corner.
- Select More tools > Extensions.
- Once the window opens, you will see all the installed extensions.
- Find any suspicious add-ons related to any PUP.
- Uninstall them by clicking Remove.
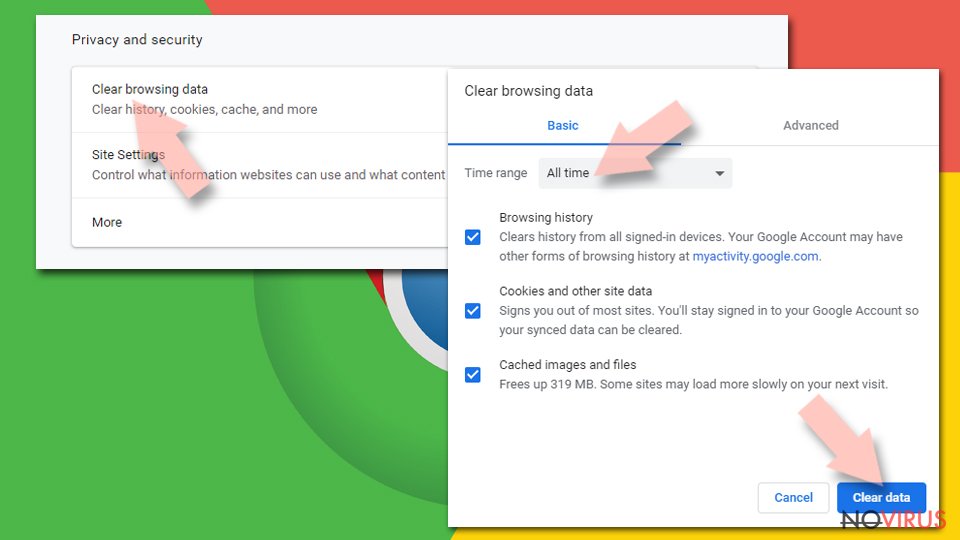
Clear cache and web data from Chrome:
- Click the Menu and select Settings.
- Find Privacy and security section.
- Choose Clear browsing data.
- Select Browsing history.
- Cookies and other site data, also Cached images and files.
- Click Clear data.
Alter settings of the homepage:
- Go to the menu and choose Settings.
- Find odd entries in the On startup section.
- Click on Open a specific or set of pages.
- Then click on three dots and look for the Remove option.
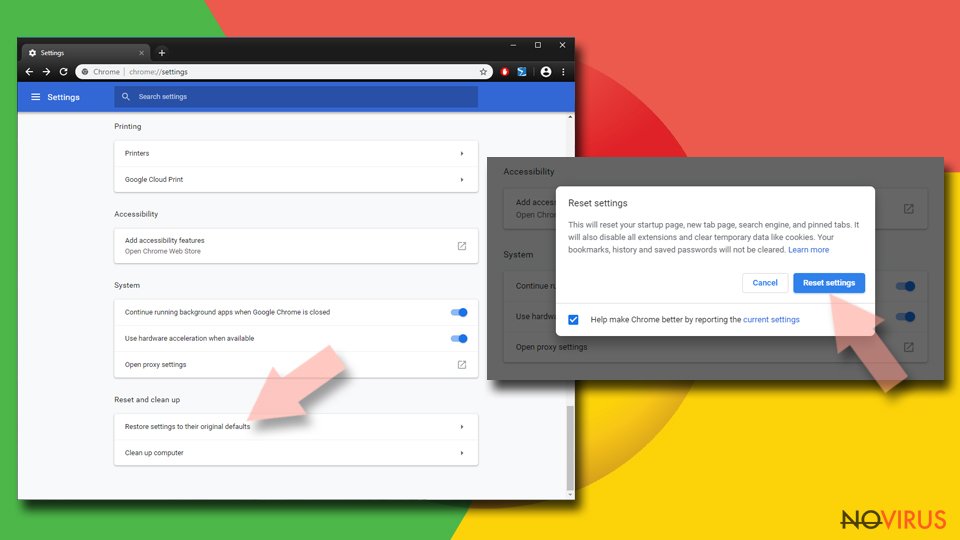
Reset Google Chrome fully:
You might need to reset Google Chrome and properly eliminate all the unwanted components:
- Go to Chrome Settings.
- Once there, scroll down to expand Advanced section.
- Scroll down to choose Reset and clean up.
- Click Restore settings to their original defaults.
- Click Reset settings again.
Even if you have completed all the steps above, we still strongly recommend you to scan your computer system with a powerful anti-malware software. It is advisable to do that because an automatic malware removal tool can detect and delete all remains of Chromium, for instance, its registry keys. The anti-malware program can help you to easily detect and eliminate possibly dangerous software and malicious viruses in an easy way. You can use any of our top-rated malware removal programs: FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes.
How to prevent from getting browser hijackers
Prevent the government from spying on you
As there is a growing debate in government about collecting users' data and spying on citizens, you should take a closer look at this issue and find out what shady ways of gathering information can be used to collect information about you. You need to browse anonymously if you want to avoid any government-initiated spying and tracking of information.
You can enjoy secure internet browsing and minimize the risk of intrusion into your system if you use Private Internet Access VPN program. This VPN application creates a virtual private network and provides access to the required data without any content restrictions.
Control government and other third party access to your data and ensure safe web browsing. Even if you do not engage in illegal activities and trust your ISP, we recommend being careful about your security. You should take extra precautions and start using a VPN program.
Reduce the threat of viruses by backing up your data
Due to their own careless behavior, computer users can suffer various losses caused by cyber infections. Viruses can affect the functionality of the software or directly corrupt data on your system by encrypting it. These problems can disrupt the system and cause you to lose personal data permanently. There is no such threat if you have the latest backups, as you can easily recover lost data and get back to work.
It is recommended to update the backups in parallel each time the system is modified. This way, you will be able to access the latest saved data after an unexpected virus attack or system failure. By having the latest copies of important documents and projects, you will avoid serious inconveniences. File backups are especially useful if malware attacks your system unexpectedly. We recommend using the Data Recovery Pro program to restore the system.