Uninstall WannaCry virus (Uninstall Guide) - Aug 2017 updated
WannaCry virus Removal Guide
Description of WannaCry ransomware
WannaCry ransomware assault results in 230 000 infected computers
WannaCry virus operates as a file-encrypting threat crafted on the basis of EternalBlue vulnerability. Due to this flaw, outdated Windows OS devices are vulnerable to the attack. Since its global launch on May 12th, the assault encompassed the entire virtual community, affecting more than 150 countries.
The malware, which is also labelled as WannaCrypt0r, WannaCryptor, WCry, and Wana Decrypt0r, has assaulted multiple governmental institutions throughout the world. Among the affected institutions were National Health Service in the UK, Interior Ministry in Russia, private institutions in Spain, Japanese 'Hitachi' company.
The success of the malware lies in the worm features of the malware which grants it the ability to infect other devices visible on the same network. Once the malware enters a device, it encodes data and marks it with .wcry, .wncrypt or .wncry file extensions. Besides launching its own program entitled as Wana Decrypt0r, the malware aplaces Please Read Me!.txt file with the instructions. At the moment, the ransom demands £232.
Victims are encouraged to remit the payment within 7 day unless they do not care about the elimination of their files. Furthermore, the malware deletes shadow volume copies which leaves fewer alternative data recovery options. At the moment there is no information what kind of encryption method was used. L
uckily, after several days of its rampage, a Twitter user under the name MalwareTech succeeded in finding a way to terminate the malware. However, at the moment, there is already subsequent versions roaming on the net, e.g – Wana Decrypt0r 2.0. On the other hand, IT experts assure that these variations are not as sophisticated as expected. They seem to be patched manually by other cyber villains but not by the original developers.
Recent news reveals that the malware might have connections to the notorious Lazarus group. Thus far, the malware only succeeded in earning £38660 in comparison with the entire scale of the virus. If this misfortune has befallen your computer as well, the first thing you should so is to remove WannaCry. For that purpose, FortectIntego or Malwarebytes might be effective.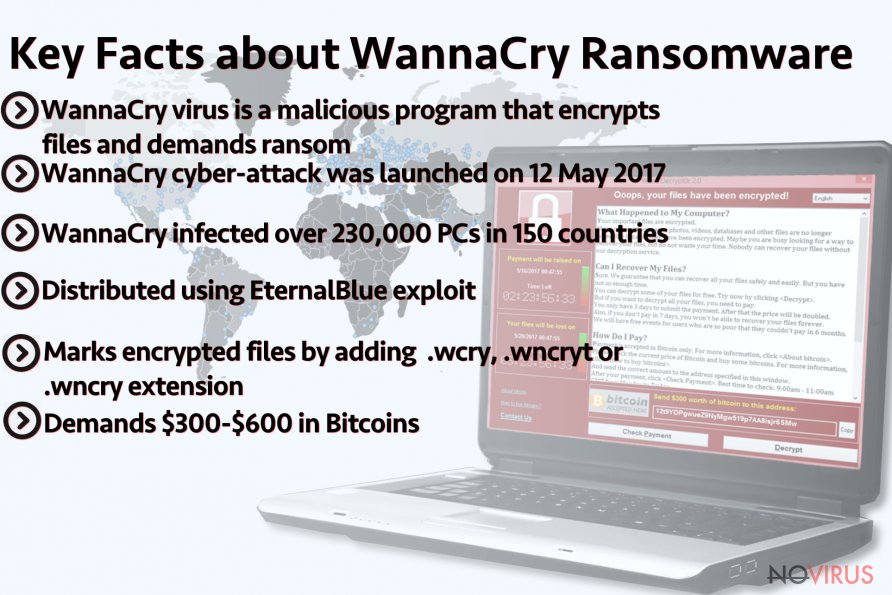
The very attack was launched on May 12th, 2017. The news about the malware broke out after National Health Service located in the Great Britain reported WannaCry ransomware to have paralysed their systems. Later on, FedEx, transportation agency, German train service “Deutsche Bahn“ and multiple others reported the attack. The initial report claimed that over 230 000 countries have fallen under the assault of this malware, though further investigations clarified that 99 countries suffered the attack.
The virus successfully spread in all parts of the world: less popular targets such as Latin American countries or Central Asia states were struck as well. Regarding such enormous number of the malware, IT experts have no information whether the racketeers returned data. Luckily, most of the companies had backup copies which, limited the scale of inflicted damage. Therefore, it reminds the virtual community to stay vigilant and backup their important documents.
Peculiar distribution techniques of WannaCry malware
The cause of this malware attack is no less interesting than the very virus. EternalBlue, or SMBv1, specifically, CVE-2017-0145, is the core element which let the cyber criminals to wreak havoc on a global scale. Due to it, a perpetrator gains access to a computer. The world would have never known about this vulnerability if not the data leak occurred on March 2017.
Interestingly, that the data was stolen by Shadow Brokers from the US National Security Agency. It also sparked theories that the NSA developed this exploit for possible cyber attacks on outdated Windows 7 and Windows 8 systems. When the data leak became evident, Microsoft urgently issued MS17-010 patch. Though the patch was said to have eliminated the flaw, current situation reveals a high number of outdated systems throughout the world. Thus, it is necessary to arm up with the knowledge to prevent the cyber assault:
- Check whether MS17-010 security patch is installed. It serves as crucial element evading the attack. Install it to evade WannaCry hijack.
- Update your system as well cyber security programs.
- Install malware elimination utility. It might be effective not only in battling the malware but in reducing the risk of infection.
- Use Microsoft instructions to disable SMBv1.
WannaCry variations
.wcry file extension virus. It is regarded as the initial version of this cyber menace. Interestingly, that it entered the cyber space already on February this year. Nonetheless, it was not developed into an enormous threat. With the assistance of AES-128 encryption technique, the malware encodes users files. In exchange for the data, 0.1 Bitcoin was required. At that time, the threat was transmitted via corrupted spam email attachments. However, this attack did not make a huge profit for the hackers. Thus, cyber criminal lost interest in improving it.
WanaCrypt0r ransomware virus. It did not take long for the hackers to come up with new ideas, as they made use of the NSA exploit tool data leak. Contrary to the previous version, the malware uses a much more efficient method of infiltration. In the previous case, users may prevent the attack simply by ignoring spam emails, but in this case, every user who delayed updating his or her system is subject to the attack. Once the malware invades the system, it encodes personal files and appends .wncry, .wncryt, or .wcry file extension.
Unfortunately, there is no decryption tool released yet. Thus, the only viable way to recover files is to use backup copies or alternative data decryption tools. This version also contains its GUI interface with elapsing time. Victims are urged to pay the ransom which usually amounts £238 within 7 days. Payment delay after 3 days results in doubling the price. There is already WannaCrypt0r 2.0 version released.
Wana Decrypt0r ransomware. It is an analogous version of the previous alternations. The perpetrators were quick to launch WanaDecrypt0r 2.0 as well. It also contains a clock counting time until final data elimination to expert pressure on the victims. £238 ransom payments are usually required. IT experts note that there are no reports of retrieved data. Thus, it might be futile to pay the ransom. This version was seized by the earlier-mentioned IT expert ‘MalwareTech.’
Though the malware has been terminated, there is no decryption tool released yet. Specialists note that the ransomware contained ‘kill switch’ which granted a chance to terminate the attack. Though cyber security specialists expect more elaborate versions to surface, latest editions reveal that they lack sophistication. In any case, when encountering one of the versions of this crypto-malware, WannaCry removal should become a priority.
Eliminating WannaCry and data recovery
When it comes to ransomware, manual elimination is never a recommended option. Therefore, it would be better to remove WannaCry virus with the assistance of the malware elimination utility. The key fact is whether the program is updated.
On May 12th few anti-virus programs were able to detect the infect, but now the majority of them detect this ransomware-trojan. It is not surprising if you cannot launch the software.
Ransomware threats tend to disable anti-virus programs. In that case, take a look at below instructions to recover access. After that, you will be able to complete WannaCry removal. Note that data decryption is only effective when the virus is completely eradicated.
Getting rid of WannaCry virus. Follow these steps
In-depth guide for the WannaCry elimination
In case you do not succeed in eliminating WannaCry from the first attempt, restart the device in Safe Mode which restores access to key system functions. Then, you will be able to launch malware elimination software.
Important! →
The elimination guide can appear too difficult if you are not tech-savvy. It requires some knowledge of computer processes since it includes system changes that need to be performed correctly. You need to take steps carefully and follow the guide avoiding any issues created due to improper setting changes. Automatic methods might suit you better if you find the guide too difficult.
Step 1. Launch Safe Mode with Networking
Safe Mode environment offers better results of manual virus removal
Windows 7 / Vista / XP
- Go to Start.
- Choose Shutdown, then Restart, and OK.
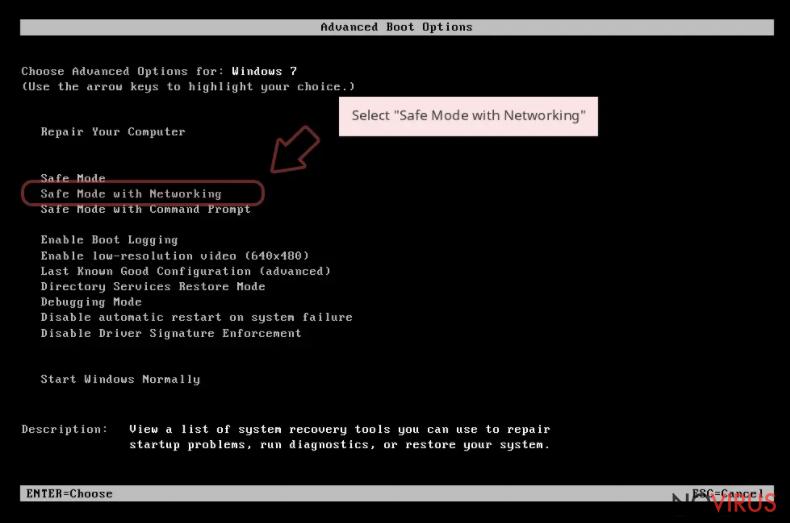
- When your computer boots, start pressing the F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) a few times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.
Windows 10 / Windows 8
- Right-click the Start button and choose Settings.
- Scroll down to find Update & Security.
- On the left, pick Recovery.
- Scroll to find Advanced Startup section.
- Click Restart now.
- Choose Troubleshoot.
- Go to Advanced options.
- Select Startup Settings.
- Press Restart.
- Choose 5) Enable Safe Mode with Networking.
Step 2. End questionable processes
You can rely on Windows Task Manager that finds all the random processes in the background. When the intruder is triggering any processes, you can shut them down:
- Press Ctrl + Shift + Esc keys to open Windows Task Manager.
- Click on More details.
- Scroll down to Background processes.
- Look for anything suspicious.
- Right-click and select Open file location.
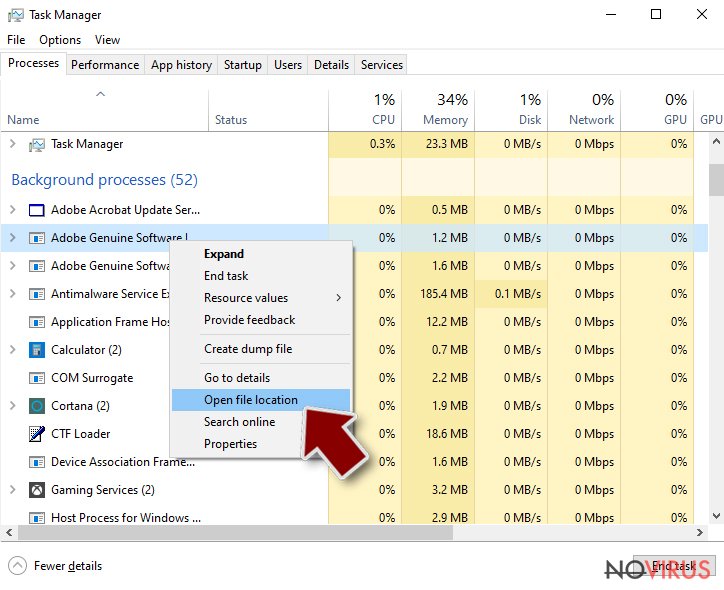
- Go back to the Process tab, right-click and pick End Task.
- Delete the contents of the malicious folder.
Step 3. Check the program in Startup
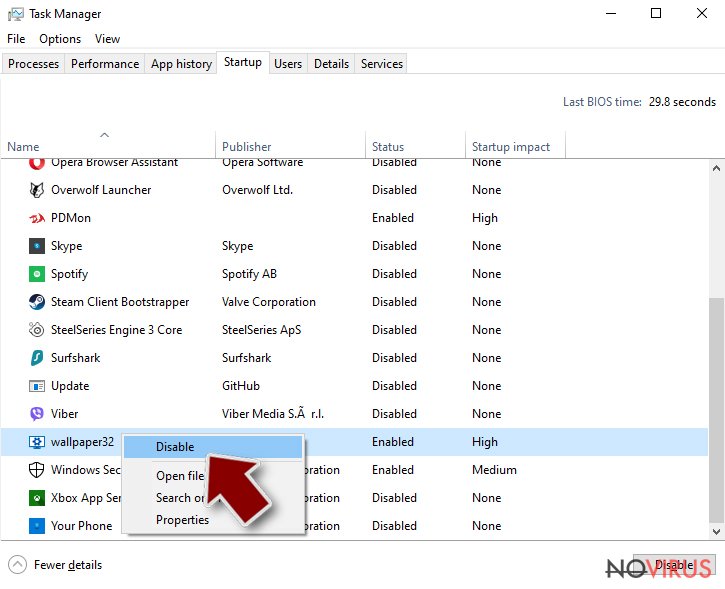
- Press Ctrl + Shift + Esc on your keyboard again.
- Go to the Startup tab.
- Right-click on the suspicious app and pick Disable.
Step 4. Find and eliminate virus files
Data related to the infection can be hidden in various places. Follow the steps and you can find them:
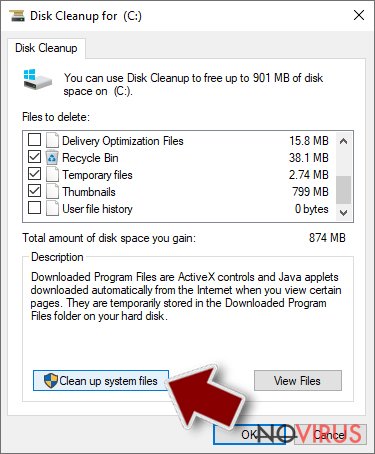
- Type in Disk Cleanup in Windows search and press Enter.
- Select the drive (C: is your main drive by default and is likely to be the one that has malicious files in) you want to clean.
- Scroll through the Files to delete and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.
- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Eliminate WannaCry using System Restore
System Restore method should serve as an alternative version for you to recover access.
-
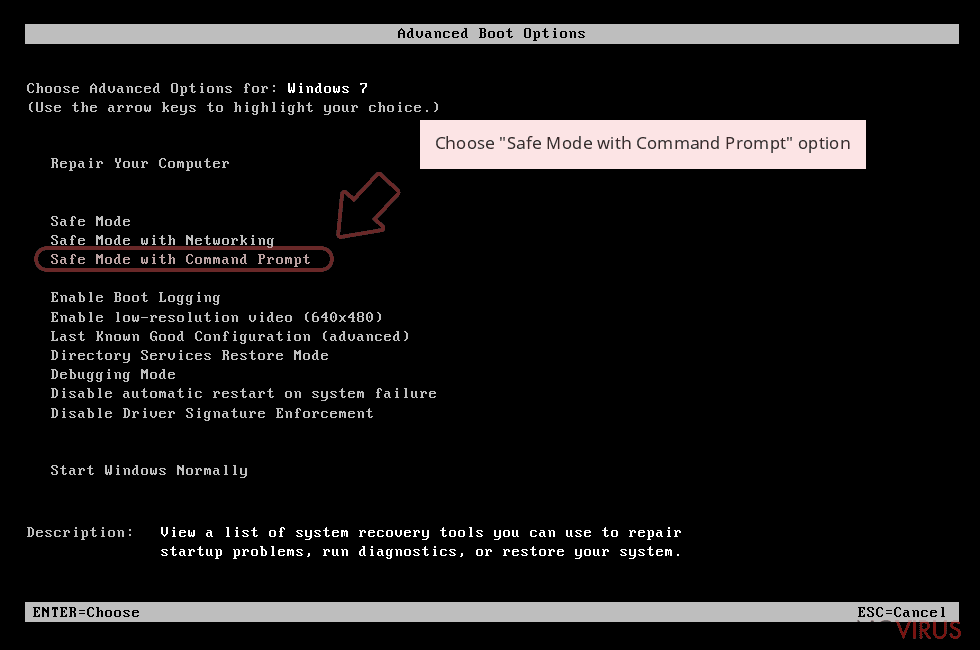
Step 1: Restart your computer in Safe Mode with Command Prompt
Windows 7 / Vista / XP- Go to Start → Shutdown → Restart → OK.
- As soon as your computer starts, start pressing F8 key repeatedly before the Windows logo shows up.
-
Choose Command Prompt from the list

Windows 10 / Windows 8- Click on the Power button at the Windows login screen, and then press and hold Shift key on your keyboard. Then click Restart.
- Then select Troubleshoot → Advanced options → Startup Settings and click Restart.
-
Once your computer starts, select Enable Safe Mode with Command Prompt from the list of options in Startup Settings.

-
Step 2: Perform a system restore to recover files and settings
-
When the Command Prompt window appears, type in cd restore and press Enter.

-
Then type rstrui.exe and hit Enter..

-
In a new window that shows up, click the Next button and choose a restore point that was created before the infiltration of WannaCry and then click on the Next button again.


-
To start system restore, click Yes.

-
When the Command Prompt window appears, type in cd restore and press Enter.
Bonus: Restore your files
Using the tutorial provided above you should be able to eliminate WannaCry from the infected device. novirus.uk team has also prepared an in-depth data recovery guide which you will also find above.There are a couple of methods you can apply to recover data encrypted by WannaCry:
Data Recovery Pro option
In case you do not have backup copies or can't come up with an alternative method to restore the files, this program may help you to retrieve some of the files.
- Download Data Recovery Pro;
- Install Data Recovery on your computer following the steps indicated in the software’s Setup;
- Run the program to scan your device for the data encrypted by WannaCry ransomware;
- Recover the data.
There is no official WannaCry decryption tool released yet
It is strongly recommended to take precautions and secure your computer from malware attacks. To protect your PC from WannaCry and other dangerous viruses, you should install and keep a powerful malware removal tool, for instance, FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes.
How to prevent from getting ransomware
A proper web browser and VPN tool can guarantee better safety
As online spying becomes an increasing problem, people are becoming more interested in how to protect their privacy. One way to increase your online security is to choose the most secure and private web browser. But if you want complete anonymity and security when surfing the web, you need Private Internet Access VPN service. This tool successfully reroutes traffic across different servers, so your IP address and location remain protected. It is also important that this tool is based on a strict no-log policy, so no data is collected and cannot be leaked or made available to first or third parties. If you want to feel safe on the internet, a combination of a secure web browser and a Private Internet Access VPN will help you.
Recover files damaged by a dangerous malware attack
Despite the fact that there are various circumstances that can cause data to be lost on a system, including accidental deletion, the most common reason people lose photos, documents, videos, and other important data is the infection of malware.
Some malicious programs can delete files and prevent the software from running smoothly. However, there is a greater threat from the dangerous viruses that can encrypt documents, system files, and images. Ransomware-type viruses focus on encrypting data and restricting users’ access to files, so you can permanently lose personal data when you download such a virus to your computer.
The ability to unlock encrypted files is very limited, but some programs have a data recovery feature. In some cases, the Data Recovery Pro program can help recover at least some of the data that has been locked by a virus or other cyber infection.