Remove TeslaCrypt 3.0 (Free Removal Guide)
TeslaCrypt 3.0 Removal Guide
Description of TeslaCrypt 3.0
What you must know about TeslaCrypt 3.0 virus
Prepare for the bad news – TeslaCrypt 3.0 virus has been released. This malware is deemed as ransomware. In case you do not know how it works, then we are here to disclose the essential facts about the virus. The ransomware is programmed to encrypt personal information. Later on, you are obliged to pay a large sum of money supposedly for the exchange of the data. This virus has managed to wheedle out astonishing amounts of pounds. Nevertheless, few or no information about the data retrieval is known. In case you happen to be one of the victims, rest assured as we will tell you how to remove TeslaCrypt 3.0 virus. In order to do that you will need to install an anti-spyware program, for example, FortectIntego.
As you have already realised, TeslaCrypt 3.0 ransomware is a an update to previous versions. Originally, when TeslaCrypt appeared, cyber security experts have relatively quickly found main flaws and were able to come up with decryption methods escaping the option of paying the money. However, with the current edition it is not so easy. Hackers have perfectened the virus. Now it uses an elaborate ECDH algorithm. The hackers also employ a SHA-256 hash as a symmetric encryption key. Thus, it complicates matters much more.

How does the virus invade computers?
TeslaCrypt 3.0 malware slithers into an operating system via an email attachment. IT specialists have noticed that, usually, the attachment comes as a ZIP archive entitled as a lottery winning notification, a CV, or a fake invoice. Deceived that the email is legitimate, you carelessly open the attachment, the ZIP file gets extracted and TeslaCrypt 3.0 sets foot on your computer. After it starts the encryption process, you might not notice any odd signs that an aggressive virus operates behind your back. The ransomware adds an extension to your precious documents, excell files, photos, such as .micro, .ttt or .xxx. Afterward, the virus envelops a note called Howto_Restore_FILES.TXT on your screen informing of the encrypted documents. We recommend deleting this file. Though it will not eliminate the virus itself, but it will be a first step towards TeslaCrypt 3.0 removal.
Additionally, you ought to be aware that this ransomware might employ a trojan or similar malware as a transmission tool. A trojan can take a different form: it can either present itself as an script or an exploit kit. Therefore, usually it is programmed to disguise itself as an ordinary legitimate file. As a result, there might be no obstacles for it to get pass your cyber security. After it slithers, a trojan exposes its secret package – ransomware. Though such distribution method is quite rare, you still need to be cautious. That is why it is required to have a reputable anti-spyware application to block such malware.
TeslaCrypt 3.0 removal guidelines
Finally, we have come to the most essential part where we will explain more about the elimination process. Due to the elaborate structure of TeslaCrypt 3.0 virus, you might struggle to remove it manually. As mentioned before, it employs complex encryption algorithms, so detecting main malicious files might be too troublesome. However, we suggest looking up the manual guidelines developed by cyber security specialists after you remove TeslaCrypt 3.0 virus automatically. This sequence of action might be more useful and efficient. So after you enabled the system scan by the anti-spyware program, it should locate the main source files of the ransomware and remove them. Nonetheless, one problem might still remain – your encrypted files. As paying the ransom might be pointless, you might be forced to come to terms with the loss of the locked data. However, after you succeed in getting rid of the virus, you will now develop a habit to create regularly copies of the most important documents.
Getting rid of TeslaCrypt 3.0. Follow these steps
In-depth guide for the TeslaCrypt 3.0 elimination
Important! →
The elimination guide can appear too difficult if you are not tech-savvy. It requires some knowledge of computer processes since it includes system changes that need to be performed correctly. You need to take steps carefully and follow the guide avoiding any issues created due to improper setting changes. Automatic methods might suit you better if you find the guide too difficult.
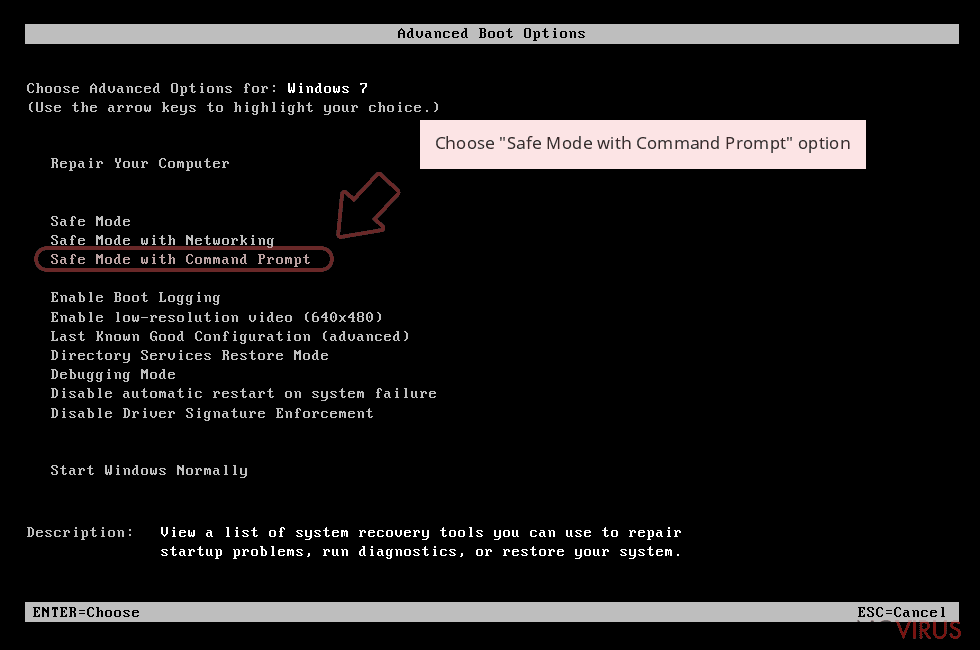
Step 1. Launch Safe Mode with Networking
Safe Mode environment offers better results of manual virus removal
Windows 7 / Vista / XP
- Go to Start.
- Choose Shutdown, then Restart, and OK.
- When your computer boots, start pressing the F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) a few times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.
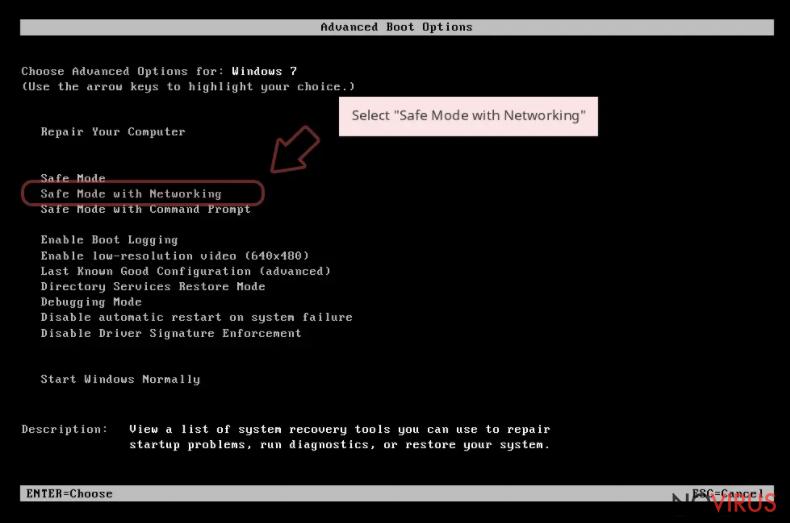
Windows 10 / Windows 8
- Right-click the Start button and choose Settings.
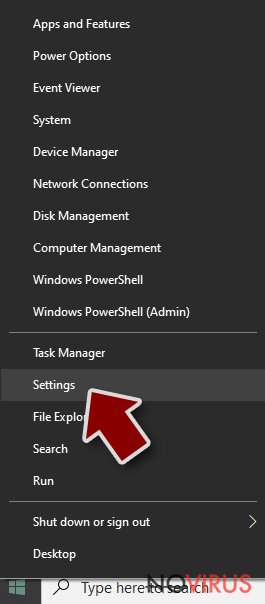
- Scroll down to find Update & Security.
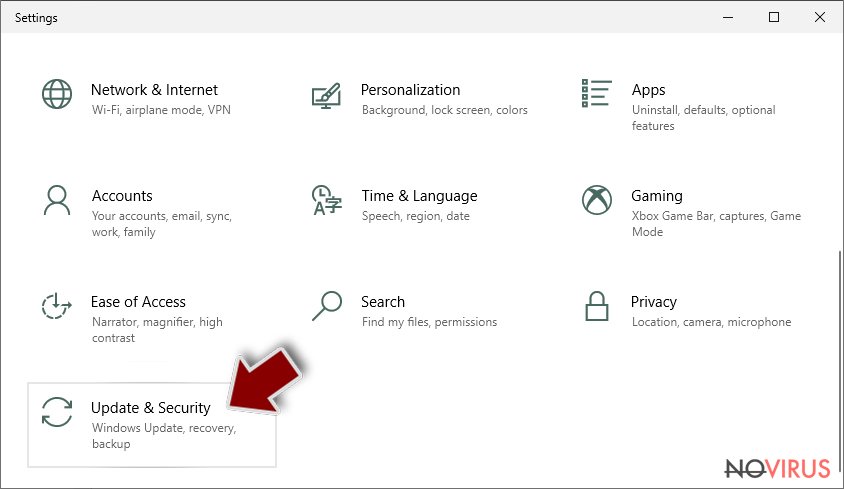
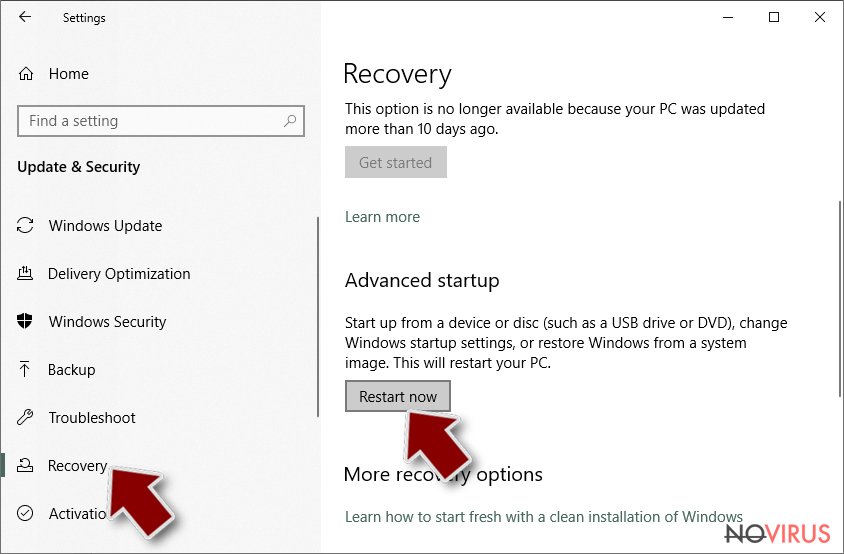
- On the left, pick Recovery.
- Scroll to find Advanced Startup section.
- Click Restart now.
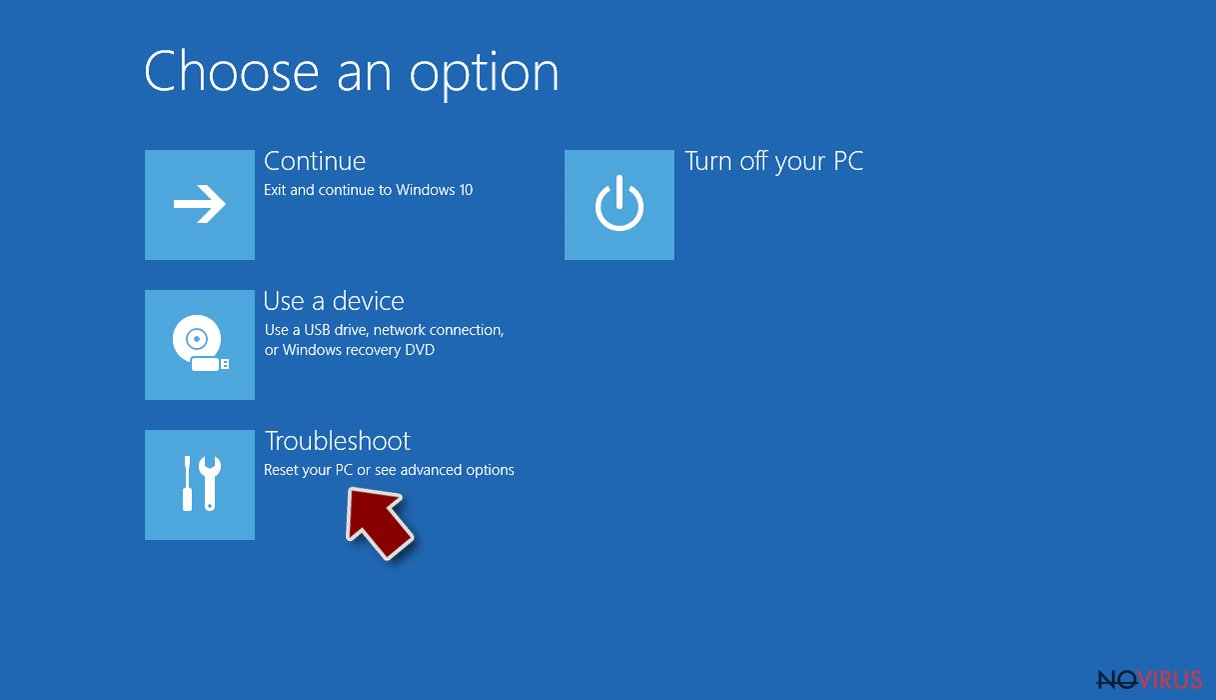
- Choose Troubleshoot.
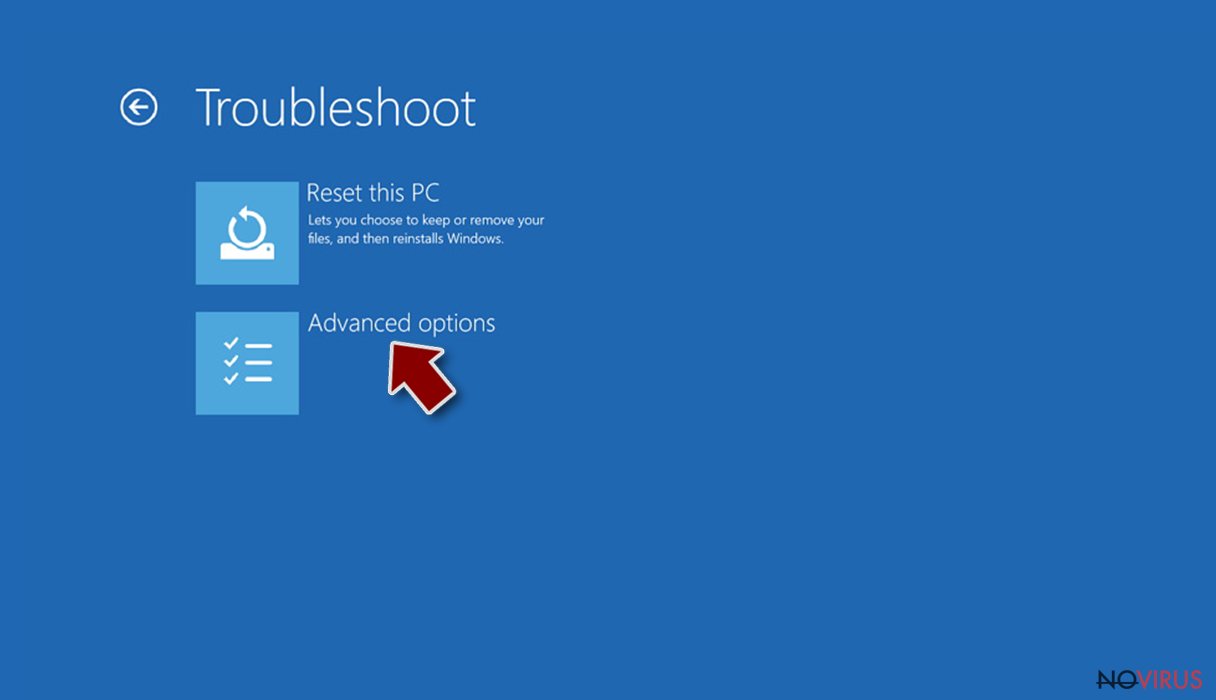
- Go to Advanced options.
- Select Startup Settings.
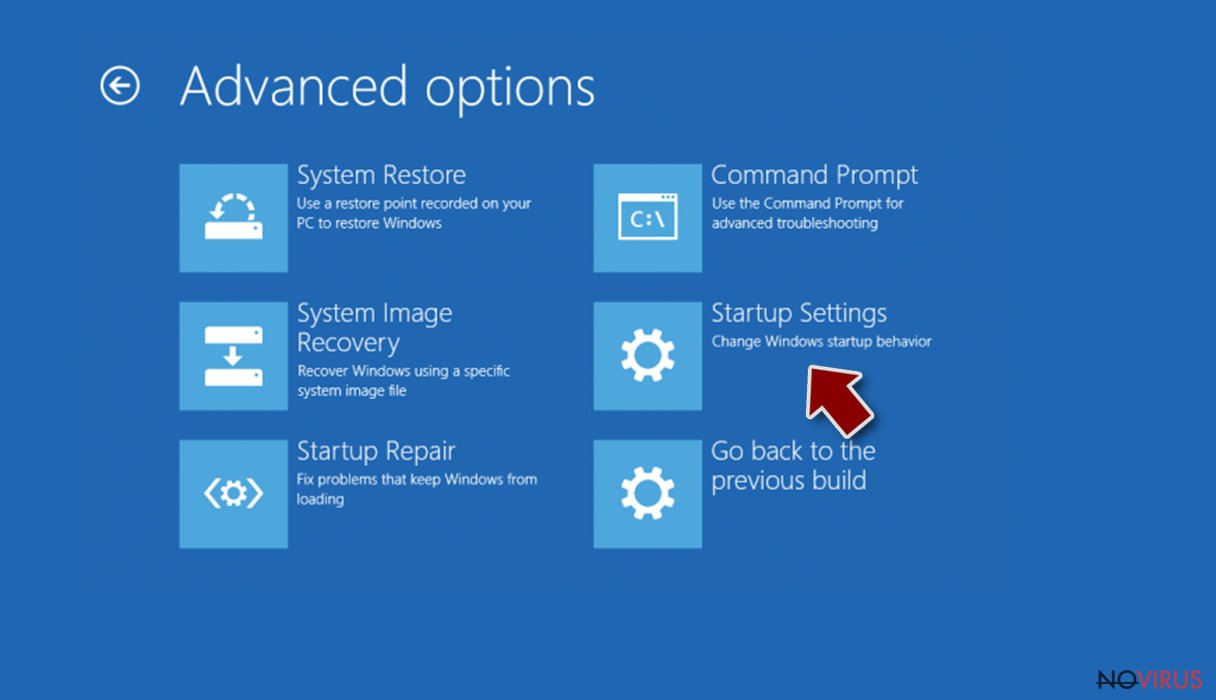
- Press Restart.
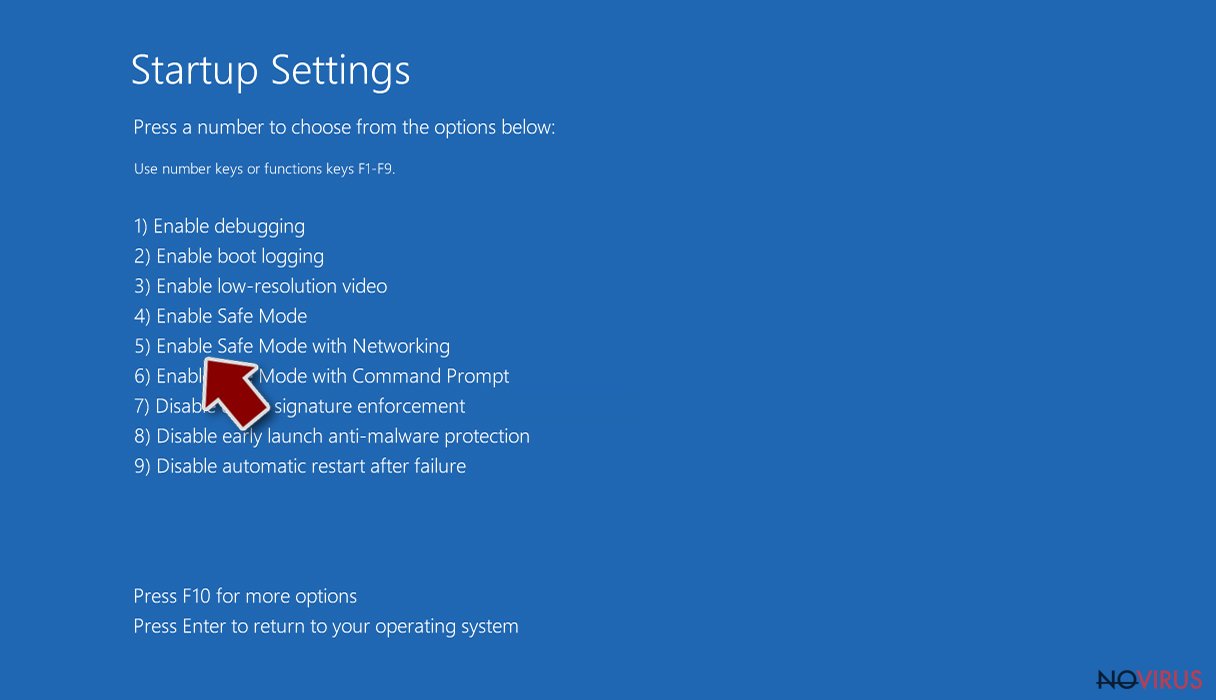
- Choose 5) Enable Safe Mode with Networking.
Step 2. End questionable processes
You can rely on Windows Task Manager that finds all the random processes in the background. When the intruder is triggering any processes, you can shut them down:
- Press Ctrl + Shift + Esc keys to open Windows Task Manager.
- Click on More details.
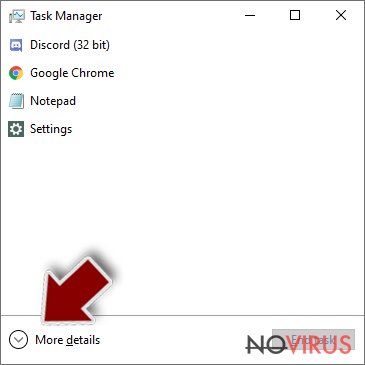
- Scroll down to Background processes.
- Look for anything suspicious.
- Right-click and select Open file location.
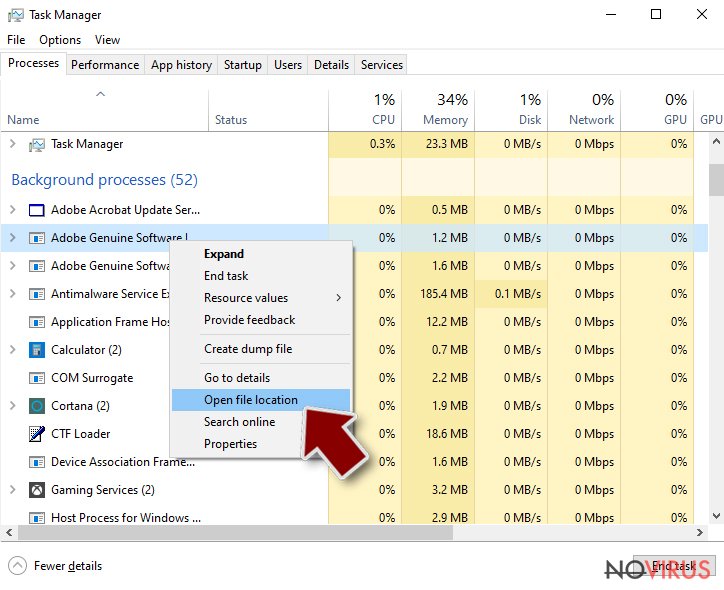
- Go back to the Process tab, right-click and pick End Task.
- Delete the contents of the malicious folder.
Step 3. Check the program in Startup
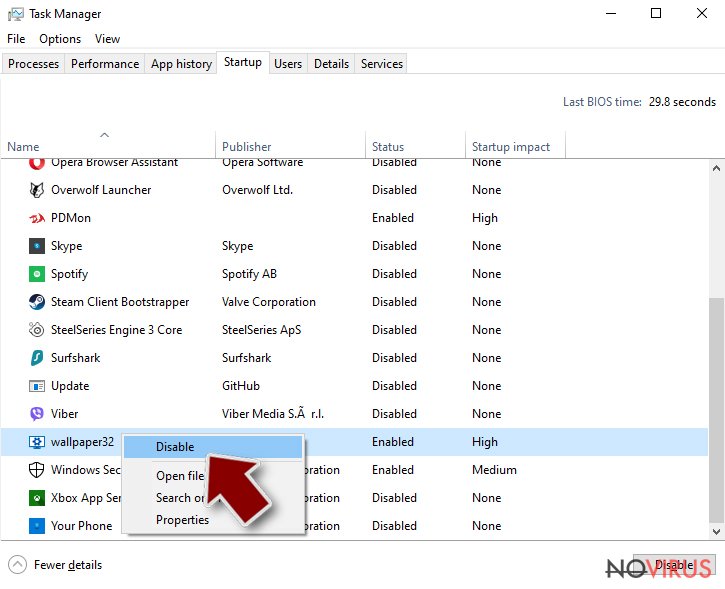
- Press Ctrl + Shift + Esc on your keyboard again.
- Go to the Startup tab.
- Right-click on the suspicious app and pick Disable.
Step 4. Find and eliminate virus files
Data related to the infection can be hidden in various places. Follow the steps and you can find them:
- Type in Disk Cleanup in Windows search and press Enter.
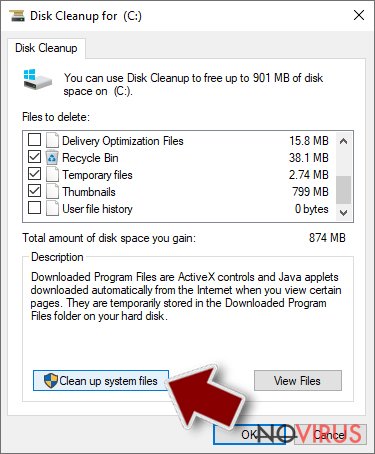
- Select the drive (C: is your main drive by default and is likely to be the one that has malicious files in) you want to clean.
- Scroll through the Files to delete and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.
- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Eliminate TeslaCrypt 3.0 using System Restore
-
Step 1: Restart your computer in Safe Mode with Command Prompt
Windows 7 / Vista / XP- Go to Start → Shutdown → Restart → OK.
- As soon as your computer starts, start pressing F8 key repeatedly before the Windows logo shows up.
-
Choose Command Prompt from the list

Windows 10 / Windows 8- Click on the Power button at the Windows login screen, and then press and hold Shift key on your keyboard. Then click Restart.
- Then select Troubleshoot → Advanced options → Startup Settings and click Restart.
-
Once your computer starts, select Enable Safe Mode with Command Prompt from the list of options in Startup Settings.

-
Step 2: Perform a system restore to recover files and settings
-
When the Command Prompt window appears, type in cd restore and press Enter.

-
Then type rstrui.exe and hit Enter..

-
In a new window that shows up, click the Next button and choose a restore point that was created before the infiltration of TeslaCrypt 3.0 and then click on the Next button again.


-
To start system restore, click Yes.

-
When the Command Prompt window appears, type in cd restore and press Enter.
It is strongly recommended to take precautions and secure your computer from malware attacks. To protect your PC from TeslaCrypt 3.0 and other dangerous viruses, you should install and keep a powerful malware removal tool, for instance, FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes.
How to prevent from getting browser hijacker
A proper web browser and VPN tool can guarantee better safety
As online spying becomes an increasing problem, people are becoming more interested in how to protect their privacy. One way to increase your online security is to choose the most secure and private web browser. But if you want complete anonymity and security when surfing the web, you need Private Internet Access VPN service. This tool successfully reroutes traffic across different servers, so your IP address and location remain protected. It is also important that this tool is based on a strict no-log policy, so no data is collected and cannot be leaked or made available to first or third parties. If you want to feel safe on the internet, a combination of a secure web browser and a Private Internet Access VPN will help you.
Reduce the threat of viruses by backing up your data
Due to their own careless behavior, computer users can suffer various losses caused by cyber infections. Viruses can affect the functionality of the software or directly corrupt data on your system by encrypting it. These problems can disrupt the system and cause you to lose personal data permanently. There is no such threat if you have the latest backups, as you can easily recover lost data and get back to work.
It is recommended to update the backups in parallel each time the system is modified. This way, you will be able to access the latest saved data after an unexpected virus attack or system failure. By having the latest copies of important documents and projects, you will avoid serious inconveniences. File backups are especially useful if malware attacks your system unexpectedly. We recommend using the Data Recovery Pro program to restore the system.