Uninstall Nozelesn virus (Uninstall Guide) - Jan 2019 updated
Nozelesn virus Removal Guide
Description of Nozelesn virus
Nozelesn virus is a cryptovirus that targets various users all over the world and makes their files useless by encrypting them
Nozelesn ransomware is the virus that remains active and requires ransom from companies and everyday users. When it comes to ransomware-type threats the main technique used to affect the targeted device is file encryption. For this process, crypto malware employs algorithms, and them marks encoded data with .nozelesn appendix. Since the main purpose is to gain profit from ransom payments when victims' files get locked virus generates a ransom note and delivers the message in HTML file called HOW_FIX_NOZELESN_FILES.HTML. The victim is demanded to pay for the alleged decryption and file recovery, but there is no real guarantee that criminals would do that. Another distinct feature about Nozelesn virus is the initial distribution method – using fake DHL emails.
| Name | Nozelesn ransomware |
|---|---|
| Type | Cryptovirus |
| File extension | .nozelesn |
| Ransom amount | Differs. May get up to $30 000 if the main target is a large company |
| Encryption method | AES |
| Distribution | Fake emails from services with infected file attachments |
| Newest tactics | Targets large companies and demands very large ransom sums |
| Elimination | You need a reputable anti-malware program if you want to completely remove Nozelesn ransomware. Also, fix virus damage using repair tools like FortectIntego |
Although Nozelesn ransomware was first discovered back in summer 2018, more recent events have revealed that this virus is now focused on bigger targets like companies or services. This change is due to the opportunity to request larger ransom payments.
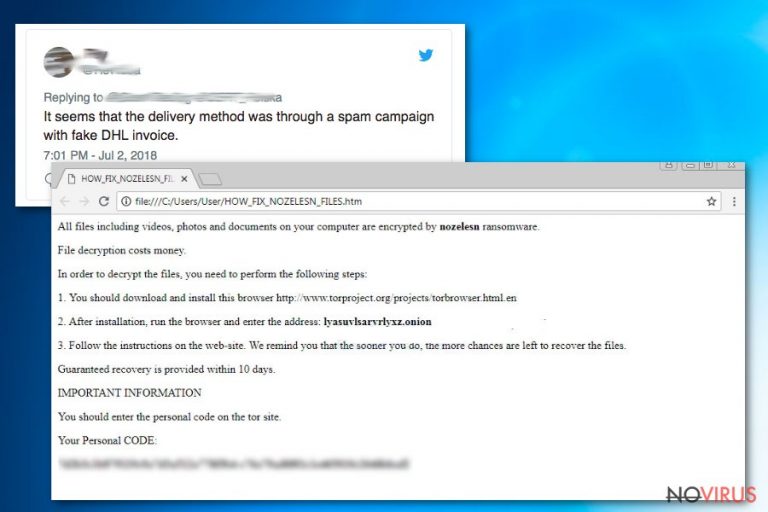
Nozelesn ransomware virus places the HTML file on every folder that contains encrypted data when the encoding is done. The ransom note includes payment instructions and more details about the attack. The ransom note is called HOW_FIX_NOZELESN_FILES.htm and reads the following:
All files including videos, photos and documents on your computer are encrypted by nozelesn ransomware.
File decryption costs money.
In order to decrypt the files, you need to perform the following steps:
1. You should download and install this browser http://www.torproject.org/projects/torbrowser.html.en
2. After installation, run the browser and enter the address: lyasuvlsarvrlyxz.onion
3. Follow the instructions on the web-site. We remind you that the sooner you do, the more chances are left to recover the files.
Guaranteed recovery is provided within 10 days.
IMPORTANT INFORMATION
You should enter the personal code on the tor site.
Your Personal CODE:
e09c5e1d187866ae38cdbcdd263d3db4-ff1fb0f01634f41f05222ca08933e4d7
Although Nozelesn ransomware developers promise to decrypt your files or provide the decryption key, you shouldn't trust these people. The best option is to get rid of the virus completely. To do so, you need a full system scan using FortectIntego because there might be additional files and programs added on the computer.
When Nozelesn ransomware alters Windows Registry entries or adds system files, you cannot remove the threat easily; it remains persistent. Entering the Safe Mode with Networking may help for the process, so follow our suggestions below the article for these tips.
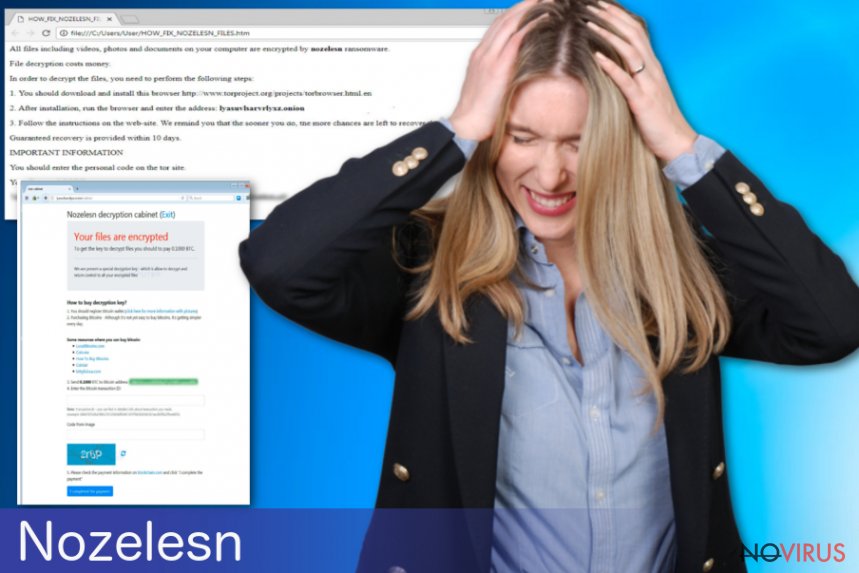
In the ransom note, Nozelesn ransomware demands paying up and the amount may differ from 0.1000 Bitcoin or even up to 1BTC. We recommend avoiding any contact between you and the malware developers. Paying the ransom cannot give you positive results because, in many cases, malicious actors disappear after the payment and you lose your data/money permanently.
You need to make sure that you remove Nozelesn ransomware entirely from the device because this threat may work in the background still. When you select the anti-malware program for the elimination, choose a reputable source and a legitimate program, so there is no risk of getting additional PUPs.
When you opt for the automatic Nozelesn ransomware removal, use anti-malware that you can rely on and possibly try a few different tools to make sure that this intruder is completely deleted from the machine. We have a few suggestions below if you need help selecting the tool.
There is a significant risk of getting malware from legitimate-looking emails
Since the beginning of virus development, the main technique to spread malware remains spam email campaigns because this method allows distributing files around the internet in a matter of minutes. When it comes to ransomware threats, this is helpful because malicious payload can be dropped once the victim opens an attached file.

The first distinct feature of the particular cryptovirus was the campaign when DHL emails named “invoice” distributed ransomware payload on computers and infected targeted devices. DHL is one of many names that malicious actors tend to use. Virus developers may include FedEx, Amazon, PayPal or eBay as the subject or sender to make the email look more legitimate.
You can avoid this infiltration if you pay more attention to details on suspicious emails. Spam email can have commercial content and intrusive ads that tell spam emails from regular emails apart. However, you need to delete emails that are sent from suspicious services, companies you are not related to or emails containing file attachments.
Those documents contain malicious macros, and you enable the script when the file gets downloaded and opened on your machine. Pay more attention to emails you were not expecting to get.
Terminate Nozelesn ransomware and make sure to clear the system
When you focus on Nozelesn ransomware removal, make sure to choose professional anti-malware tools. Programs like FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes can ensure best malware elimination results because during a full system scan all possibly dangerous files get indicated as malicious.
We can understand that data recovery is more important to you, but you need to remove Nozelesn ransomware and other threats from the computer before attempting any file restoring methods. Although the best tactic is to use data backups, not everyone has them up-to-date.
Nozelesn ransomware virus can encrypt your files again, so double-check if the computer is malware-free before plugging any external device or downloading data recovery tools.
Getting rid of Nozelesn virus. Follow these steps
In-depth guide for the Nozelesn elimination
Nozelesn ransomware removal could benefit from the system reboot in the Safe Mode with Networking before scanning the system with antivirus tool:
Important! →
The elimination guide can appear too difficult if you are not tech-savvy. It requires some knowledge of computer processes since it includes system changes that need to be performed correctly. You need to take steps carefully and follow the guide avoiding any issues created due to improper setting changes. Automatic methods might suit you better if you find the guide too difficult.
Step 1. Launch Safe Mode with Networking
Safe Mode environment offers better results of manual virus removal
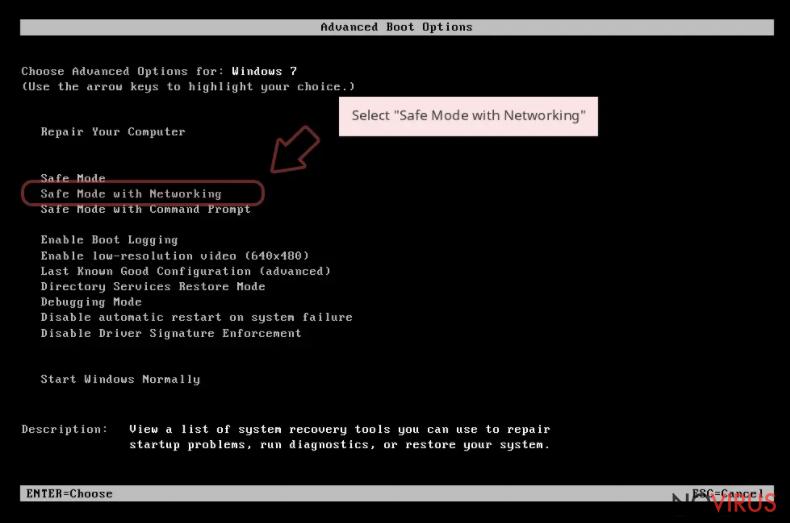
Windows 7 / Vista / XP
- Go to Start.
- Choose Shutdown, then Restart, and OK.
- When your computer boots, start pressing the F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) a few times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.
Windows 10 / Windows 8
- Right-click the Start button and choose Settings.
- Scroll down to find Update & Security.
- On the left, pick Recovery.
- Scroll to find Advanced Startup section.
- Click Restart now.
- Choose Troubleshoot.
- Go to Advanced options.
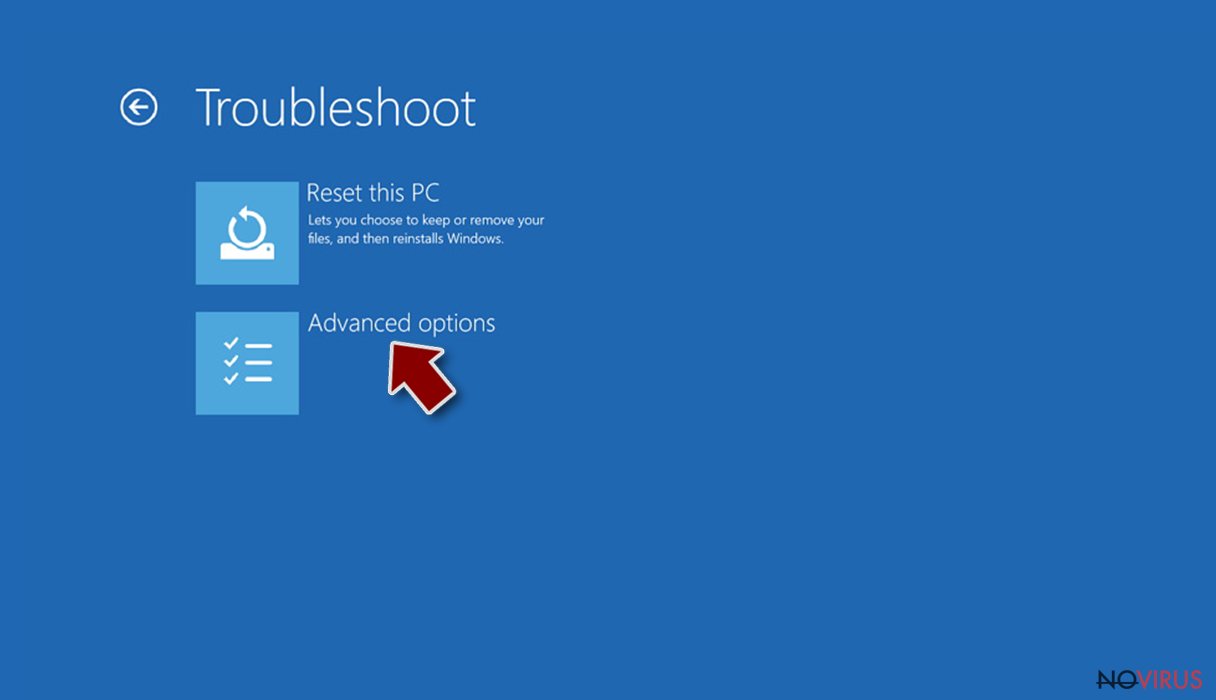
- Select Startup Settings.
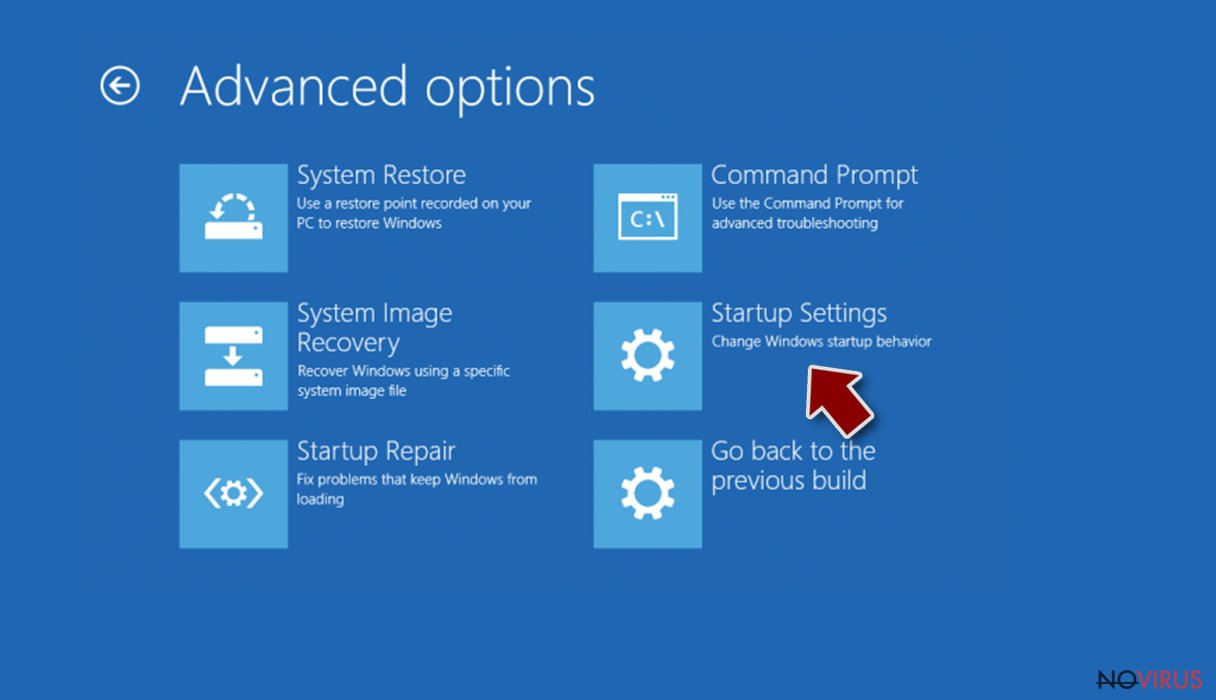
- Press Restart.
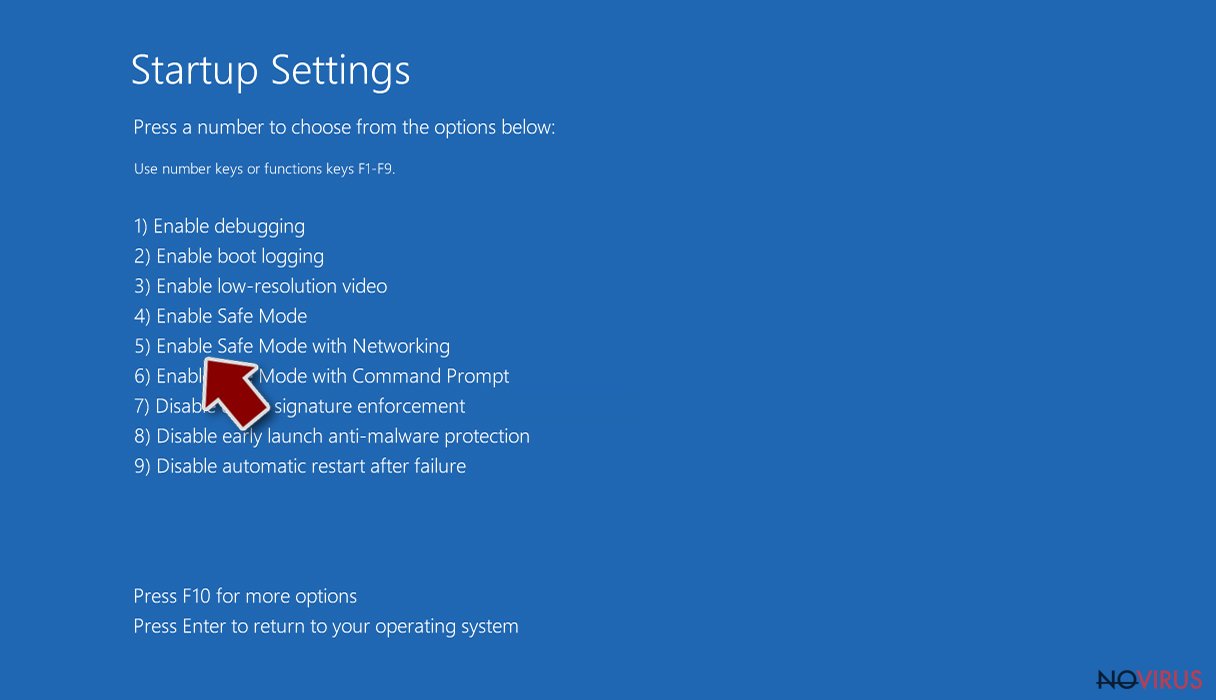
- Choose 5) Enable Safe Mode with Networking.
Step 2. End questionable processes
You can rely on Windows Task Manager that finds all the random processes in the background. When the intruder is triggering any processes, you can shut them down:
- Press Ctrl + Shift + Esc keys to open Windows Task Manager.
- Click on More details.
- Scroll down to Background processes.
- Look for anything suspicious.
- Right-click and select Open file location.
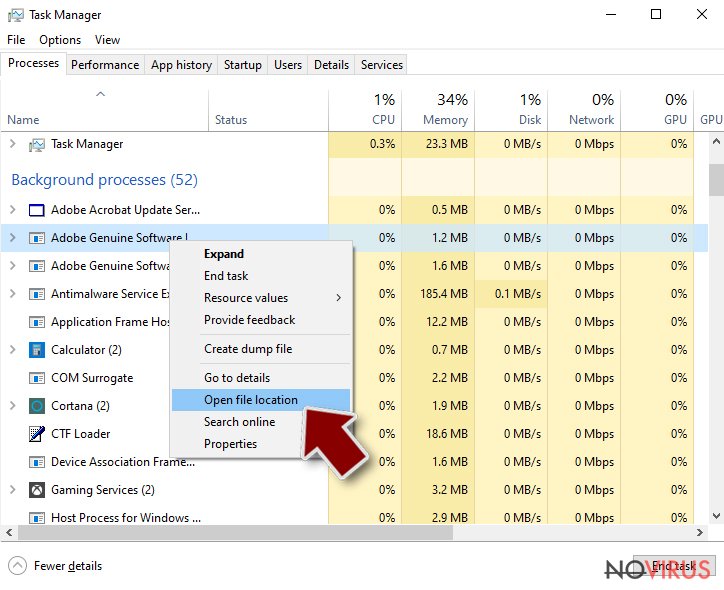
- Go back to the Process tab, right-click and pick End Task.
- Delete the contents of the malicious folder.
Step 3. Check the program in Startup
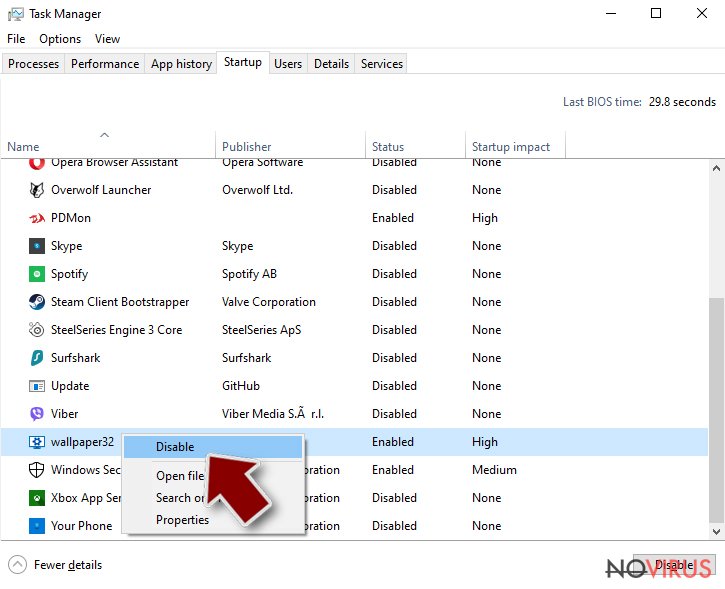
- Press Ctrl + Shift + Esc on your keyboard again.
- Go to the Startup tab.
- Right-click on the suspicious app and pick Disable.
Step 4. Find and eliminate virus files
Data related to the infection can be hidden in various places. Follow the steps and you can find them:
- Type in Disk Cleanup in Windows search and press Enter.
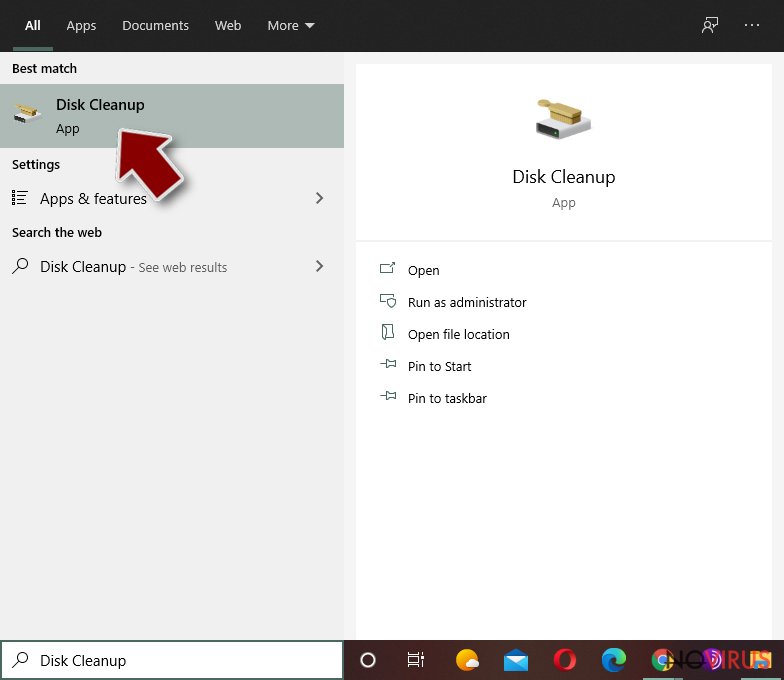
- Select the drive (C: is your main drive by default and is likely to be the one that has malicious files in) you want to clean.
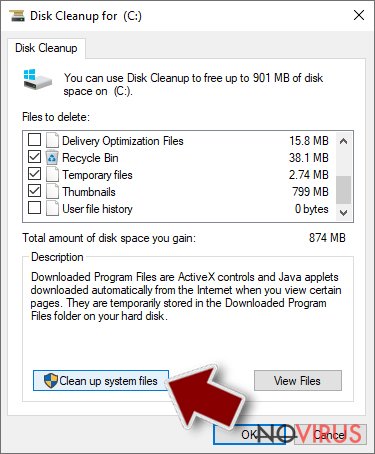
- Scroll through the Files to delete and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.
- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Eliminate Nozelesn using System Restore
System restore should help when dealing with Nozelesn ransomware:
-
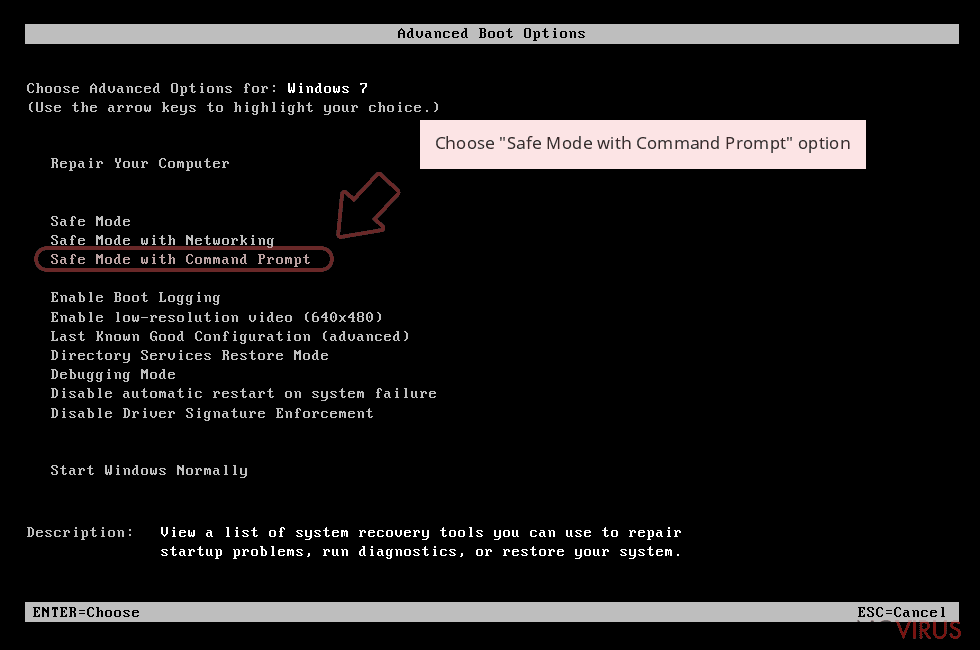
Step 1: Restart your computer in Safe Mode with Command Prompt
Windows 7 / Vista / XP- Go to Start → Shutdown → Restart → OK.
- As soon as your computer starts, start pressing F8 key repeatedly before the Windows logo shows up.
-
Choose Command Prompt from the list

Windows 10 / Windows 8- Click on the Power button at the Windows login screen, and then press and hold Shift key on your keyboard. Then click Restart.
- Then select Troubleshoot → Advanced options → Startup Settings and click Restart.
-
Once your computer starts, select Enable Safe Mode with Command Prompt from the list of options in Startup Settings.

-
Step 2: Perform a system restore to recover files and settings
-
When the Command Prompt window appears, type in cd restore and press Enter.

-
Then type rstrui.exe and hit Enter..

-
In a new window that shows up, click the Next button and choose a restore point that was created before the infiltration of Nozelesn and then click on the Next button again.


-
To start system restore, click Yes.

-
When the Command Prompt window appears, type in cd restore and press Enter.
Bonus: Restore your files
Using the tutorial provided above you should be able to eliminate Nozelesn from the infected device. novirus.uk team has also prepared an in-depth data recovery guide which you will also find above.There are a couple of methods you can apply to recover data encrypted by Nozelesn:
Data Recovery Pro can be a perfect alternative for file backup
- Download Data Recovery Pro;
- Install Data Recovery on your computer following the steps indicated in the software’s Setup;
- Run the program to scan your device for the data encrypted by Nozelesn ransomware;
- Recover the data.
Try Windows Previous Versions feature for locked files
- Right-click on the encrypted document you want to recover;
- Click “Properties” and navigate to “Previous versions” tab;
- In the “Folder versions” section look for the available file copies. Choose the desired version and press “Restore”.
ShadowExplorer could be helpful
- Download Shadow Explorer (http://shadowexplorer.com/);
- Install Shadow Explorer on your computer following the instructions in the software’s Setup Wizard;
- Run the program. Navigate to the menu on the top-left corner and select a disk containing your encrypted files. Look through the available folders;
- When you find the folder you want to recover, right-click it and select “Export”. Also, choose where the recovered data will be stored.
There is no decryption tool for Nozelesn ransomware
It is strongly recommended to take precautions and secure your computer from malware attacks. To protect your PC from Nozelesn and other dangerous viruses, you should install and keep a powerful malware removal tool, for instance, FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes.
How to prevent from getting ransomware
Prevent the government from spying on you
As there is a growing debate in government about collecting users' data and spying on citizens, you should take a closer look at this issue and find out what shady ways of gathering information can be used to collect information about you. You need to browse anonymously if you want to avoid any government-initiated spying and tracking of information.
You can enjoy secure internet browsing and minimize the risk of intrusion into your system if you use Private Internet Access VPN program. This VPN application creates a virtual private network and provides access to the required data without any content restrictions.
Control government and other third party access to your data and ensure safe web browsing. Even if you do not engage in illegal activities and trust your ISP, we recommend being careful about your security. You should take extra precautions and start using a VPN program.
Recover files damaged by a dangerous malware attack
Despite the fact that there are various circumstances that can cause data to be lost on a system, including accidental deletion, the most common reason people lose photos, documents, videos, and other important data is the infection of malware.
Some malicious programs can delete files and prevent the software from running smoothly. However, there is a greater threat from the dangerous viruses that can encrypt documents, system files, and images. Ransomware-type viruses focus on encrypting data and restricting users’ access to files, so you can permanently lose personal data when you download such a virus to your computer.
The ability to unlock encrypted files is very limited, but some programs have a data recovery feature. In some cases, the Data Recovery Pro program can help recover at least some of the data that has been locked by a virus or other cyber infection.