Uninstall Nooa virus (Recovery Instructions Included)
Nooa virus Removal Guide
Description of Nooa ransomware
Nooa virus is a malicious program that attacks your files
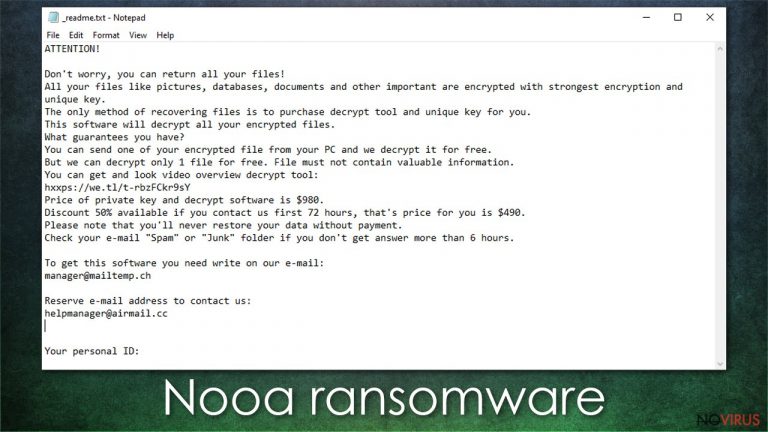
Nooa ransomware is a computer virus that locks and renames personal files. After the computer is infected, there is a _readme.txt note displayed on the screen in which cybercriminals are requesting to pay a ransom of $980 in Bitcoins in order to gain back access to your data.
This file-locking virus typically spreads through file-sharing platforms, especially through popular torrent websites. It belongs to the Djvu ransomware family, and usually, this type of cyberthreats are disguised as the latest or the most anticipated game cracks.
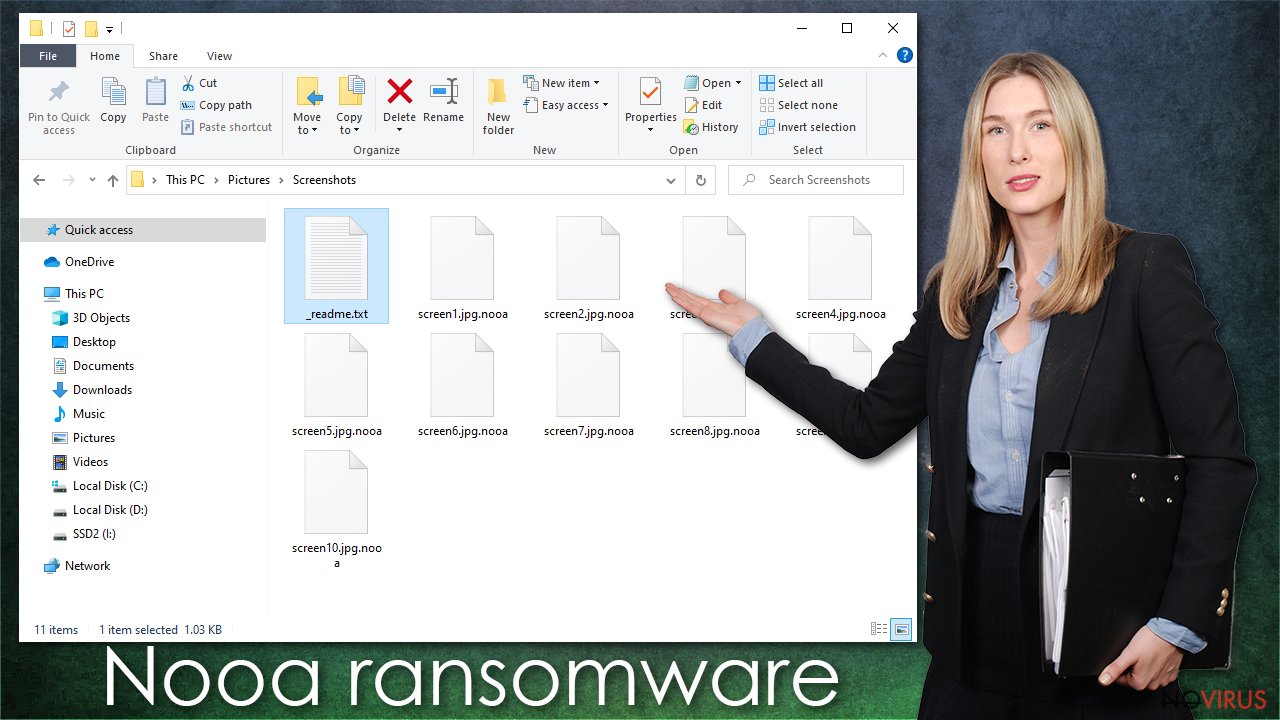
Most probably, you or someone using your Windows computer infected it by unknowingly downloading this parasite. A mistake was made, and harm had been done if pictures, documents, and other personal files are inaccessible and appended with .nooa extension.
While ransomware is one of the most devastating infection types out there, you should not immediately panic and definitely not instantly hand your money to cybercriminals. In this article, we will explain the correct way of handling the situation – delete the virus, attempt to restore files in alternative ways, and repair damaged system components.
| Name | Nooa ransomware |
| Type | Ransomware, file-locking virus |
| Family | Djvu |
| Distribution | Software cracks, pirated app installers, software bundles |
| Encryption | RSA |
| File extension | .nooa is appended to each of the personal files located on your device |
| Ransom note | _readme.txt |
| Contact | manager@mailtemp.ch and managerhelper@airmail.cc |
| Malware removal | Perform a full system scan with SpyHunter 5Combo Cleaner or another reputable anti-malware |
| System fix | Malware can seriously tamper with Windows systems, causing errors, crashes, lag, and other stability issues after it is terminated. To remediate the OS and avoid its reinstallation, we recommend scanning it with the FortectIntego repair tool |
A bit of a background
This particular ransomware strain is known since late 2018, and criminals are getting better and better at pushing their victims to make rash decisions and succumb to their threats in the ransom note.
They offer free decryption of one of your corrupted files to test out if their decryptor works and provide a hyperlink to a video where the supposed tool is doing the job. The criminals also offer a 50% discount for victims who contact them via one of the two given emails (manager@mailtemp.ch, managerhelper@airmail.cc). Here's the full ransom note:
ATTENTION!
Don't worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
hxxps://we.tl/t-9CYW99VhUR
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don't get answer more than 6 hours.To get this software you need write on our e-mail:
manager@mailtemp.chReserve e-mail address to contact us:
helpmanager@airmail.ccYour personal ID:
One of the options that you may consider to do at this point is to pay the criminals demanded amount, but at the same time, you would be motivating the cybercriminals to continue their evil work and continue to hurt innocent people. Also, by forwarding money, you would be funding their whole operation, the development of more advanced malware, and research of even more effective ways to spread it.
A few facts about the Nooa virus:
- Might be spread along the dangerous banking Trojan AZORult;
- Alters Windows registry to start with every Windows boot;
- Deletes all Shadow Copies with the command vssadmin.exe Delete Shadows/All/Quiet to prevent an easy file recovery;
- Alters Windows hosts file to prevent users from visiting security-related websites, resulting in DNS_PROBE_FINISHED_NXDOMAIN browser error. In order to restore normal browser function, go to C:\Windows\System32\drivers\etc\ location and delete the “hosts” file – it will be recreated automatically;
- Inserts dozens of new processes
- Makes HTTP requests and creates DNS resolutions.
These changes can significantly impact Windows operating system. In some cases, the damage might be very severe, and a reinstall of the OS might be required. However, we recommend you instead try running a scan with powerful PC repair software that can help you restore Windows to its pre-infection stage:
- Download FortectIntego
- Click on the ReimageRepair.exe
- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process
- The analysis of your machine will begin immediately
- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.
A few things you should know before you begin malware removal
Before starting any ransomware removal, you need to copy all files from your infected computer to an offline storage device. You may wonder if it’s safe to do that – the answer is yes, as the encrypted data doesn’t hold any malicious scripts. When all the files are moved, you will need to download reliable antivirus software (we recommend using SpyHunter 5Combo Cleaner or Malwarebytes) to avoid future failures like this. If you attempt to use recovery software before making file copies, they might get permanently damaged.
Next, you should proceed with Nooa virus removal – you need powerful security software for that. Note that malware might interfere with an antivirus app's operation or even disable it. If that is the case, accessing Safe Mode with Networking might help:
- Right-click on Start button and select Settings.
- Scroll down to pick Update & Security.
- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.
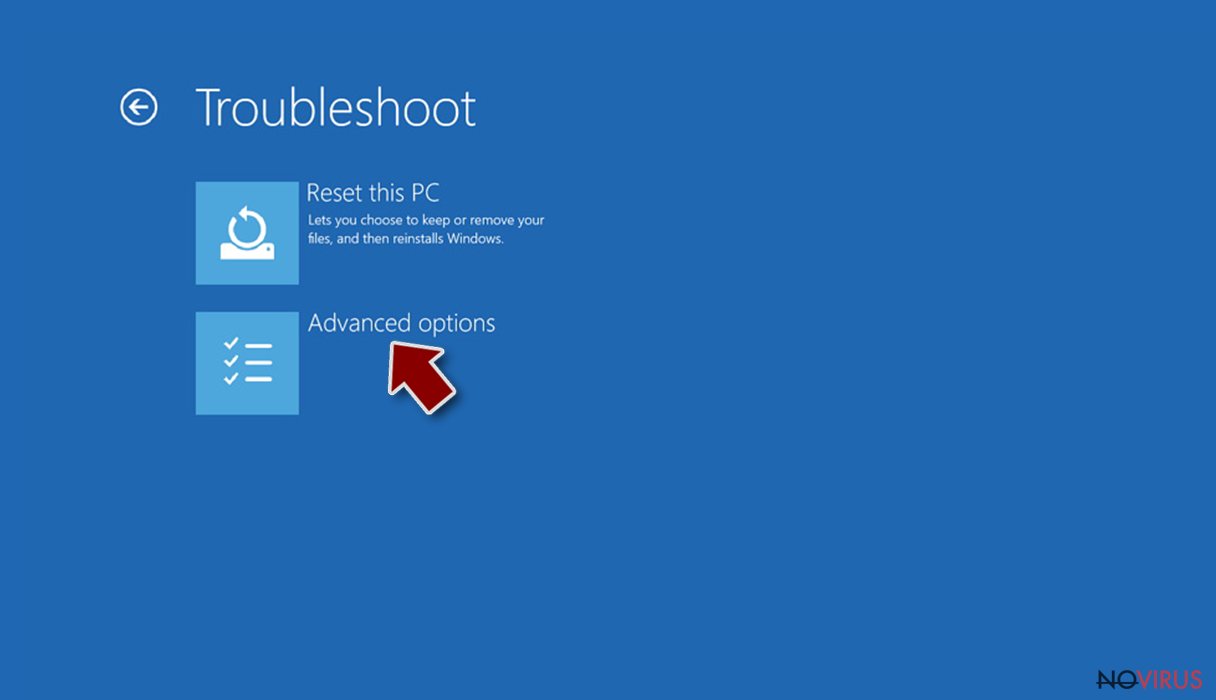
- Select Troubleshoot.
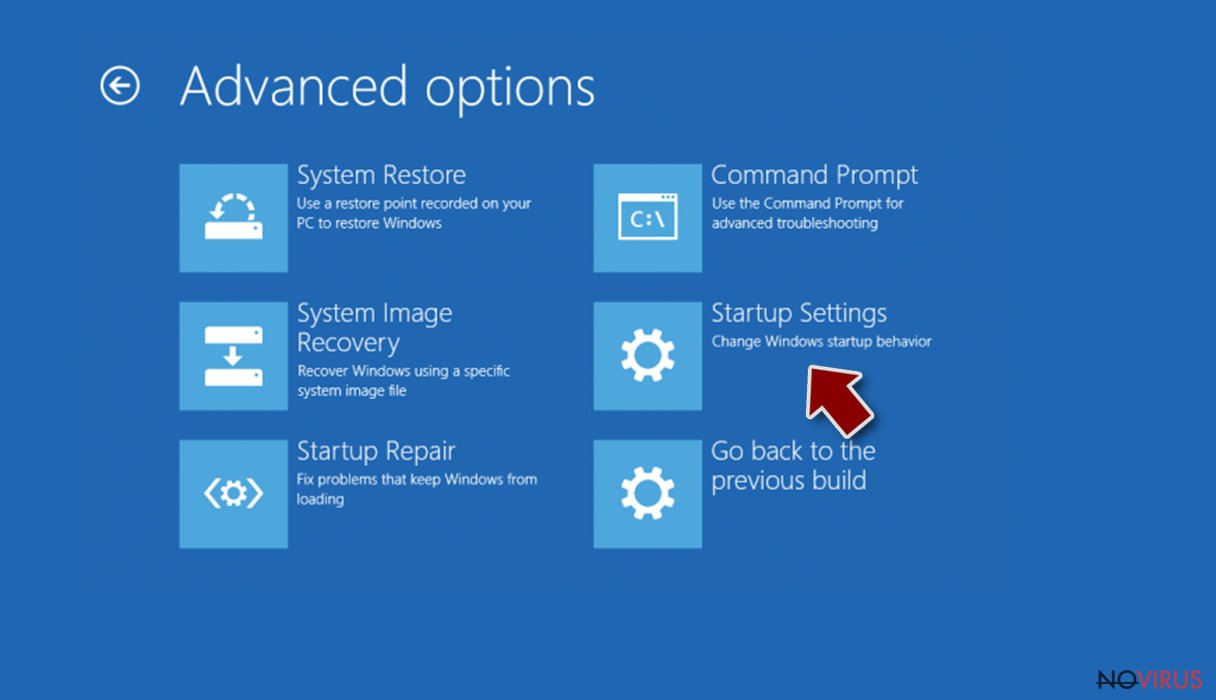
- Go to Advanced options.
- Select Startup Settings.
- Click Restart.
- Press 5 or click 5) Enable Safe Mode with Networking.
As soon as malware is deleted, you can then proceed with file recovery options.
How to restore locked files without paying cybercriminals
The Emsisoft decryptor for Djvu/STOP is a tool that you can use to unlock your data. If virus-infected files were locked with an offline ID, this software would be able to help. It is worth noting that this solution will only work only after one of the victims retrieves the key from cybercriminals after paying the ransom and shares that information with security researchers at Emsisoft. Thus, a significant amount of time might pass before the decryptor is useful.
- Download the app from the official Emsisoft website.
- After pressing Download button, a small pop-up at the bottom, titled decrypt_STOPDjvu.exe should show up – click it.
- If User Account Control (UAC) message shows up, press Yes.
- Agree to License Terms by pressing Yes.
- After Disclaimer shows up, press OK.
- The tool should automatically populate the affected folders, although you can also do it by pressing Add folder at the bottom.
- Press Decrypt.
From here, there are three available outcomes:
- “Decrypted!” will be shown under files that were decrypted successfully – they are now usable again.
- “Error: Unable to decrypt file with ID:” means that the keys for this version of the virus have not yet been retrieved, so you should try later.
- “This ID appears to be an online ID, decryption is impossible” – you are unable to decrypt files with this tool.
If your data is encrypted with an online ID, or you want to attempt to restore it right now, you should try data restore applications. This method might not always work, but in some cases, at least some portion of the locked data might be recovered, so it is always worth trying.
- Download Data Recovery Pro.
- Double-click the installer to launch it.
- Follow on-screen instructions to install the software.
- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.
- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.
- Press Scan and wait till it is complete.
- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.
Getting rid of Nooa virus. Follow these steps
In-depth guide for the Nooa elimination
Important! →
The elimination guide can appear too difficult if you are not tech-savvy. It requires some knowledge of computer processes since it includes system changes that need to be performed correctly. You need to take steps carefully and follow the guide avoiding any issues created due to improper setting changes. Automatic methods might suit you better if you find the guide too difficult.
Step 1. Launch Safe Mode with Networking
Safe Mode environment offers better results of manual virus removal
Windows 7 / Vista / XP
- Go to Start.
- Choose Shutdown, then Restart, and OK.
- When your computer boots, start pressing the F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) a few times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.
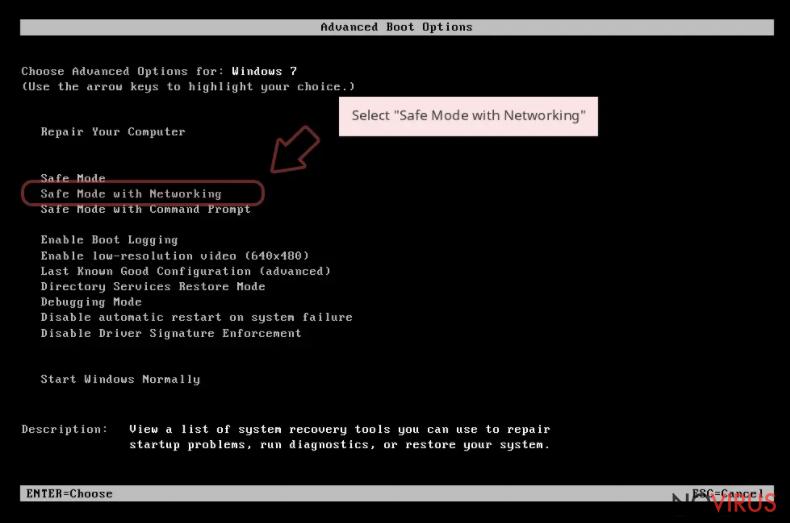
Windows 10 / Windows 8
- Right-click the Start button and choose Settings.
- Scroll down to find Update & Security.
- On the left, pick Recovery.
- Scroll to find Advanced Startup section.
- Click Restart now.
- Choose Troubleshoot.
- Go to Advanced options.
- Select Startup Settings.
- Press Restart.
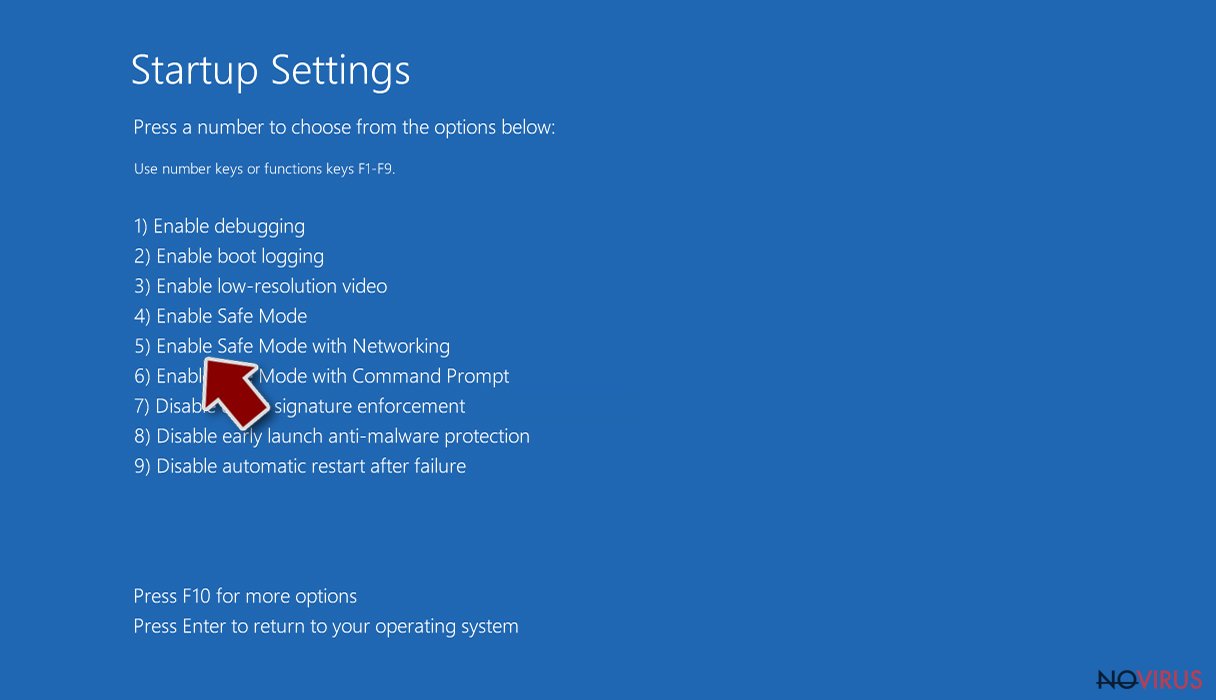
- Choose 5) Enable Safe Mode with Networking.
Step 2. End questionable processes
You can rely on Windows Task Manager that finds all the random processes in the background. When the intruder is triggering any processes, you can shut them down:
- Press Ctrl + Shift + Esc keys to open Windows Task Manager.
- Click on More details.
- Scroll down to Background processes.
- Look for anything suspicious.
- Right-click and select Open file location.
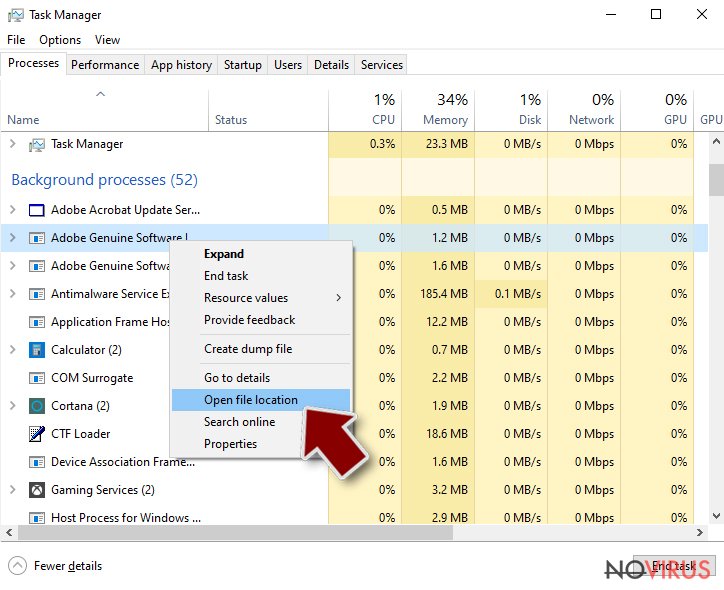
- Go back to the Process tab, right-click and pick End Task.
- Delete the contents of the malicious folder.
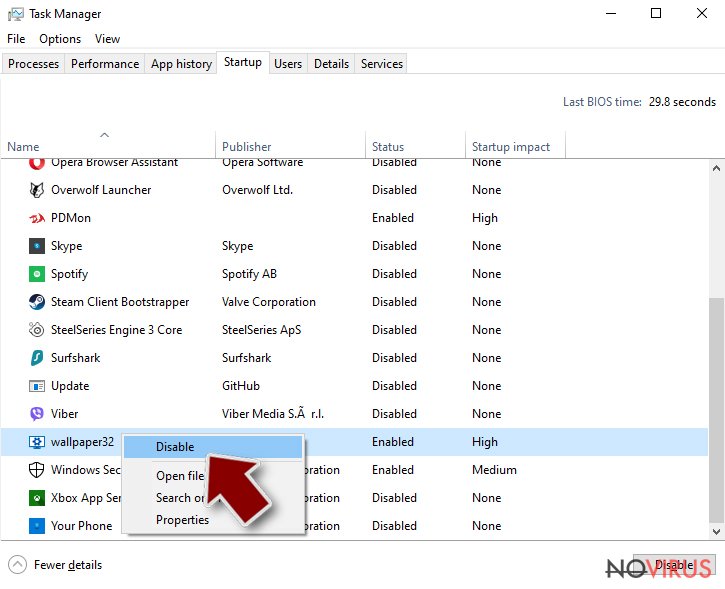
Step 3. Check the program in Startup
- Press Ctrl + Shift + Esc on your keyboard again.
- Go to the Startup tab.
- Right-click on the suspicious app and pick Disable.
Step 4. Find and eliminate virus files
Data related to the infection can be hidden in various places. Follow the steps and you can find them:
- Type in Disk Cleanup in Windows search and press Enter.
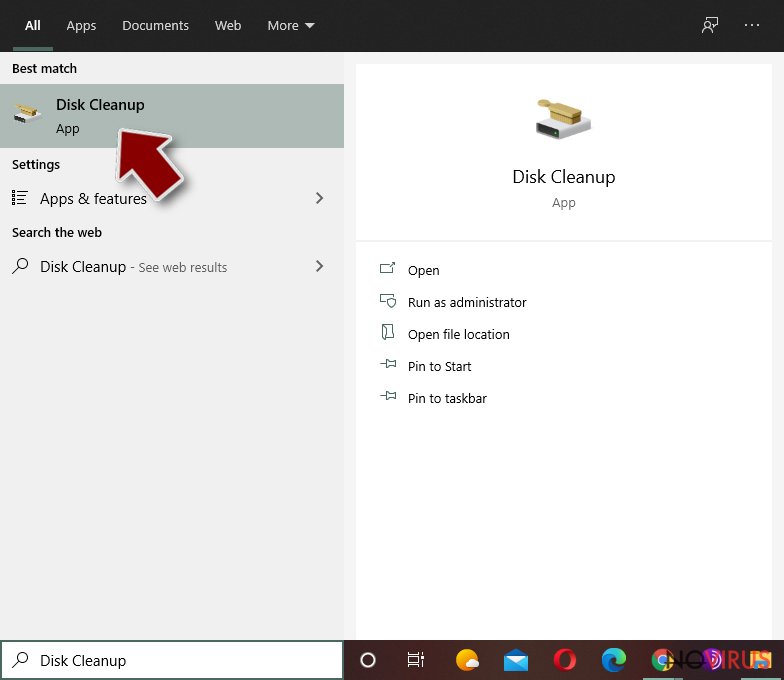
- Select the drive (C: is your main drive by default and is likely to be the one that has malicious files in) you want to clean.
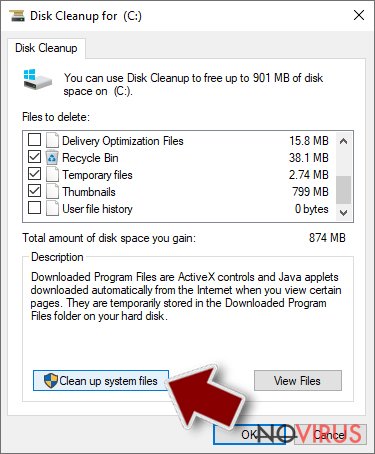
- Scroll through the Files to delete and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.
- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Eliminate Nooa using System Restore
-
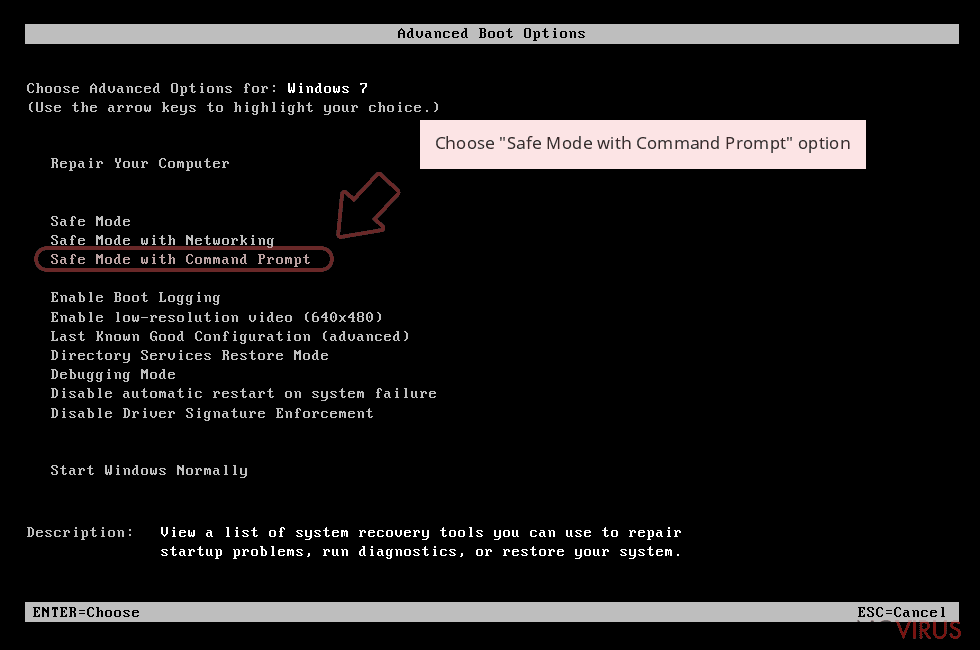
Step 1: Restart your computer in Safe Mode with Command Prompt
Windows 7 / Vista / XP- Go to Start → Shutdown → Restart → OK.
- As soon as your computer starts, start pressing F8 key repeatedly before the Windows logo shows up.
-
Choose Command Prompt from the list

Windows 10 / Windows 8- Click on the Power button at the Windows login screen, and then press and hold Shift key on your keyboard. Then click Restart.
- Then select Troubleshoot → Advanced options → Startup Settings and click Restart.
-
Once your computer starts, select Enable Safe Mode with Command Prompt from the list of options in Startup Settings.

-
Step 2: Perform a system restore to recover files and settings
-
When the Command Prompt window appears, type in cd restore and press Enter.

-
Then type rstrui.exe and hit Enter..

-
In a new window that shows up, click the Next button and choose a restore point that was created before the infiltration of Nooa and then click on the Next button again.


-
To start system restore, click Yes.

-
When the Command Prompt window appears, type in cd restore and press Enter.
It is strongly recommended to take precautions and secure your computer from malware attacks. To protect your PC from Nooa and other dangerous viruses, you should install and keep a powerful malware removal tool, for instance, FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes.
How to prevent from getting ransomware
Prevent the government from spying on you
As there is a growing debate in government about collecting users' data and spying on citizens, you should take a closer look at this issue and find out what shady ways of gathering information can be used to collect information about you. You need to browse anonymously if you want to avoid any government-initiated spying and tracking of information.
You can enjoy secure internet browsing and minimize the risk of intrusion into your system if you use Private Internet Access VPN program. This VPN application creates a virtual private network and provides access to the required data without any content restrictions.
Control government and other third party access to your data and ensure safe web browsing. Even if you do not engage in illegal activities and trust your ISP, we recommend being careful about your security. You should take extra precautions and start using a VPN program.
Reduce the threat of viruses by backing up your data
Due to their own careless behavior, computer users can suffer various losses caused by cyber infections. Viruses can affect the functionality of the software or directly corrupt data on your system by encrypting it. These problems can disrupt the system and cause you to lose personal data permanently. There is no such threat if you have the latest backups, as you can easily recover lost data and get back to work.
It is recommended to update the backups in parallel each time the system is modified. This way, you will be able to access the latest saved data after an unexpected virus attack or system failure. By having the latest copies of important documents and projects, you will avoid serious inconveniences. File backups are especially useful if malware attacks your system unexpectedly. We recommend using the Data Recovery Pro program to restore the system.