Uninstall .locky virus (Detailed Removal Instructions)
.locky virus Removal Guide
Description of .locky file extension virus
Why should you avoid .locky file extension virus:
.locky file extension virus is a ransomware threat able to infiltrate the computer and encrypt the most valuable information. Nevertheless, it might be only beginning to all the problems that are about to appear on your system after getting infected with it. When having .locky file extension ransomware on the system, you are required to pay a ransom in exchange for the data handover. Brushing aside naïve hopes that they will delete this virus after you transmit the required payment, you should think about .locky file extension virus removal instead. Otherwise, this threat can continue its data encryption process leaving you with nothing. Also, it can infect your computer with more viruses that can lead you to even bigger computer problems.
This malware has emerged after the notoriously famous Locky virus, which struck the world in February. Thus, some IT experts have deduced that it might be just another alternative of the mentioned ransomware while others are convinced that different cyber criminals are behind this virus. According to them, they just want to get a ray of a spotlight from Locky. Despite these opinions, it doesn’t make .locky file extension ransomware less devastating. You need to stay away from this virus as far as possible. If you want to prevent its infiltration or remove its files from your computer, you should install FortectIntego. If you are interested in .locky file extension virus distribution, you should read the following paragraph explaining the most popular methods used to transmit ransomware to target computers.
How is .locky file extension virus transmitted to computers?
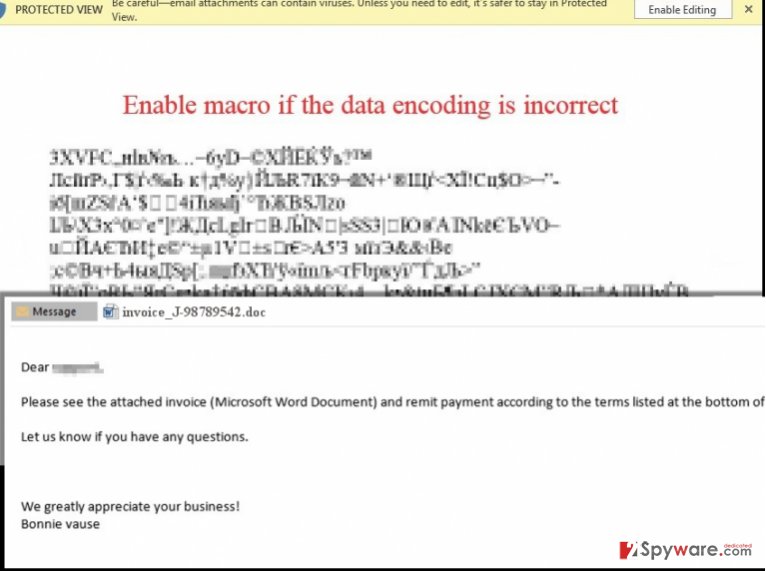
Like other ransomware of this kind, .locky file extension virus attacks victims via infected emails. Usually, victims receive a fake invoice or similar email which bears an infected attachment. One of them is a _J-98223100.doc, but there is highly possible that hackers will start using other names for their infected attachments. You should also pay attention to the subject of the email, which is entitled as ATTN: Invoice J-98223100 or similar. If the malicious file spreading .locky file extension virus is a word file, once you extract it, you can be asked to enable macro settings. If they are disabled by default, you are quite lucky as you have time to confront the virus. In case they are enabled, the .locky file extension virus activates itself and takes off into your system to do its maleficent job – encrypt your personal data. Beware that this ransomware can also spread as a JavaScript file that starts working as soon as it gets into the system. When .locky file extension malware becomes active, it starts the encryption of victim’s files. According to PC security experts, it can lock these extensions:
.7z; .rar; .m4a; .wma; .avi; .wmv; .csv; .d3dbsp; .sc2save; .sie; .sum; .ibank; .t13; .t12; .qdf; .gdb; .tax; .pkpass; .bc6; .bc7; .bkp; .qic; .bkf; .sidn; .sidd; .mddata; .itl; .itdb; .icxs; .hvpl; .hplg; .hkdb; .mdbackup; .syncdb; .gho; .cas; .svg; .map; .wmo; .itm; .sb; .fos; .mcgame; .vdf; .ztmp; .sis; .sid; .ncf; .menu; .layout; .dmp; .blob; .esm; .001; .vtf; .dazip; .fpk; .mlx; .kf; .iwd; .vpk; .tor; .psk; .rim; .w3x; .fsh; .ntl; .arch00; .lvl; .snx; .cfr; .ff; .vpp_pc; .lrf; .m2; .mcmeta; .vfs0; .mpqge; .kdb; .db0; .DayZProfile; .rofl; .hkx; .bar; .upk; .das; .iwi; .litemod; .asset; .forge; .ltx; .bsa; .apk; .re4; .sav; .lbf; .slm; .bik; .epk; .rgss3a; .pak; .big; .unity3d; .wotreplay; .xxx; .desc; .py; .m3u; .flv; .js; .css; .rb; .png; .jpeg; .txt; .p7c; .p7b; .p12; .pfx; .pem; .crt; .cer; .der; .x3f; .srw; .pef; .ptx; .r3d; .rw2; .rwl; .raw; .raf; .orf; .nrw; .mrwref; .mef; .erf; .kdc; .dcr; .cr2; .crw; .bay; .sr2; .srf; .arw; .3fr; .dng; .jpeg; .jpg; .cdr; .indd; .ai; .eps; .pdf; .pdd; .psd; .dbfv; .mdf; .wb2; .rtf; .wpd; .dxg; .xf; .dwg; .pst; .accdb; .mdb; .pptm; .pptx; .ppt; .xlk; .xlsb; .xlsm; .xlsx; .xls; .wps; .docm; .docx; .doc; .odb; .odc; .odm; .odp; .ods; .odt
Once the encryption stage is finished, ransomware delivers a message in front your screen by striking a bolt out of the blue. It says that the victim has to pay a ransom to get his/hers files back. Certainly, we do NOT recommend paying the money because there is no guarantee that you will get the data back even if you remit money. Additionally, you should be wary that the virus might infect your computer with highly disturbing trojans. That’s why we highly recommend you to remove .locky file extension virus as soon as you notice .locky file extension next to your files’ extensions. For that, check the guide on the second page.
Is there a way to remove .locky file extension virus?
If you want to stay safe, you have to make sure that your computer is protected by reliable and trustworthy anti-spyware. Also, make sure that you keep your most valuable files safe. You should keep their copies in external hard drives or simple CD to be sure that their can be restored when needed. Finally, be careful with emails from unknown people, keep your guard while browsing the web and stay away from suspicious websites. It is often the case that even official or seemingly secure websites are involved in the distribution of the ransomware and similar infections. Thus, make sure you are careful with odd-looking hyperlinks as well. When discussing .locky file extension virus removal, you should forget manual removal due to the complexity of this virus. Therefore, we suggest running a full system scan with reliable anti-spyware, such asFortectIntego or Malwarebytes. Also, don’t forget to take a glimpse of the elimination guides developed by IT experts that are given below. They are supposed to help you complete .locky file extension virus removal.
Getting rid of .locky virus. Follow these steps
In-depth guide for the .locky elimination
Important! →
The elimination guide can appear too difficult if you are not tech-savvy. It requires some knowledge of computer processes since it includes system changes that need to be performed correctly. You need to take steps carefully and follow the guide avoiding any issues created due to improper setting changes. Automatic methods might suit you better if you find the guide too difficult.
Step 1. Launch Safe Mode with Networking
Safe Mode environment offers better results of manual virus removal
Windows 7 / Vista / XP
- Go to Start.
- Choose Shutdown, then Restart, and OK.
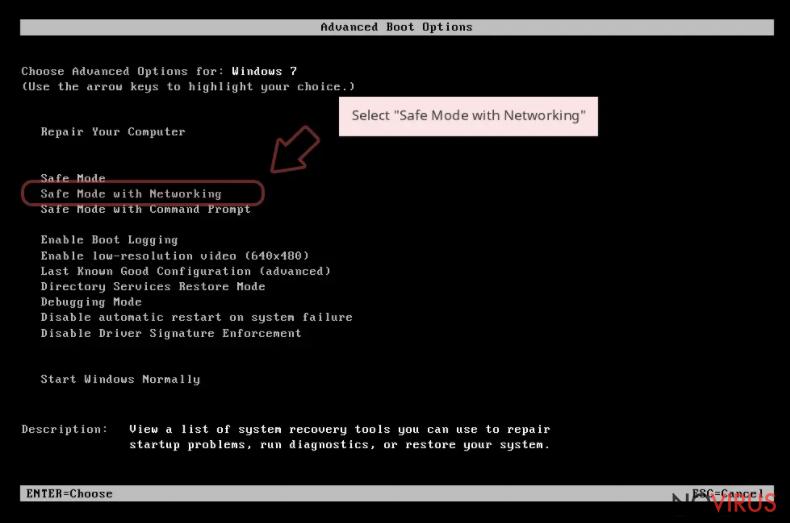
- When your computer boots, start pressing the F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) a few times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.
Windows 10 / Windows 8
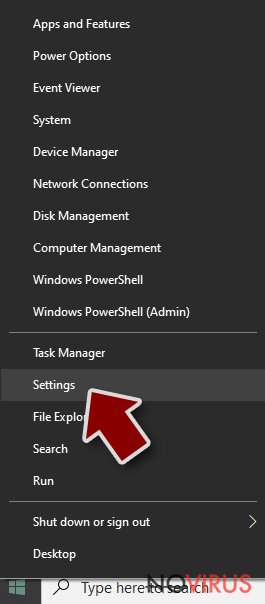
- Right-click the Start button and choose Settings.
- Scroll down to find Update & Security.
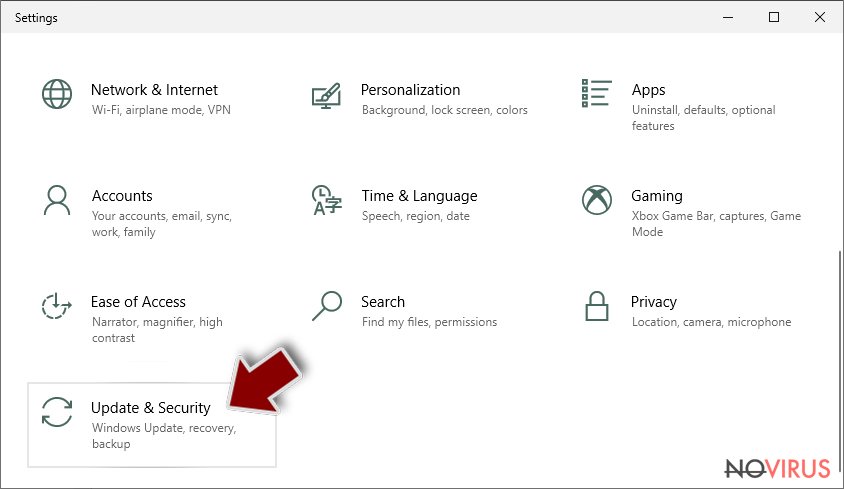
- On the left, pick Recovery.
- Scroll to find Advanced Startup section.
- Click Restart now.
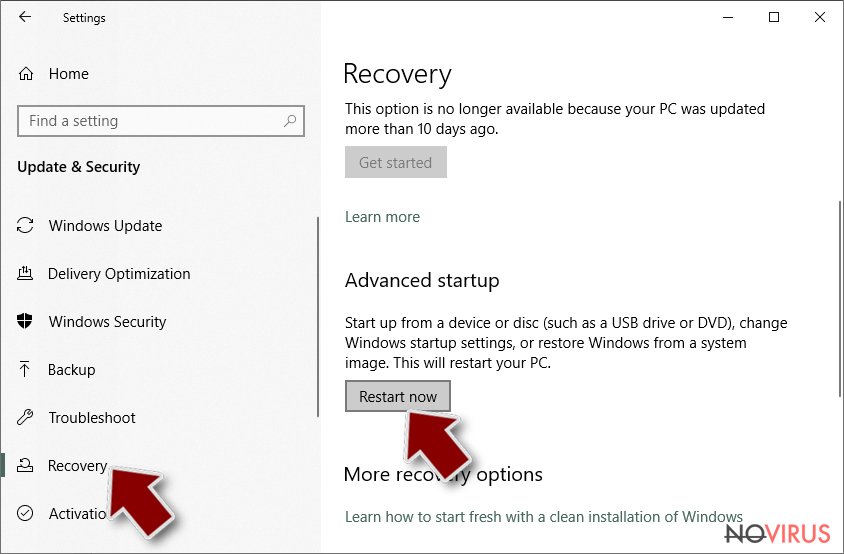
- Choose Troubleshoot.
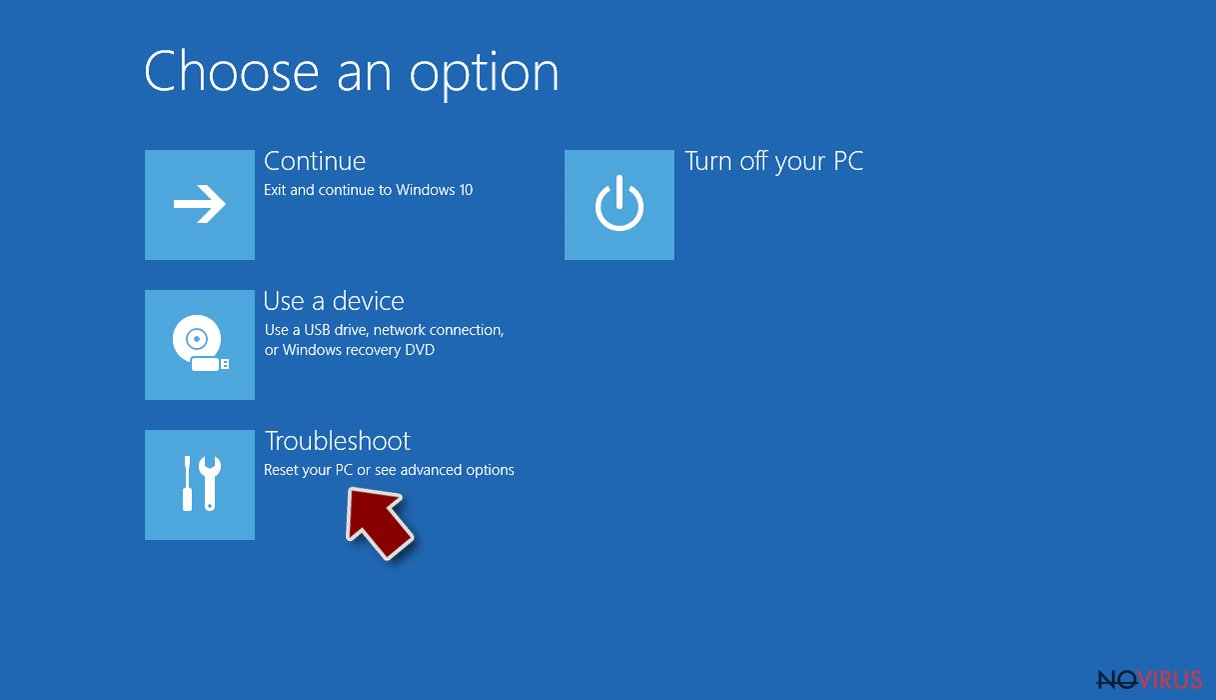
- Go to Advanced options.
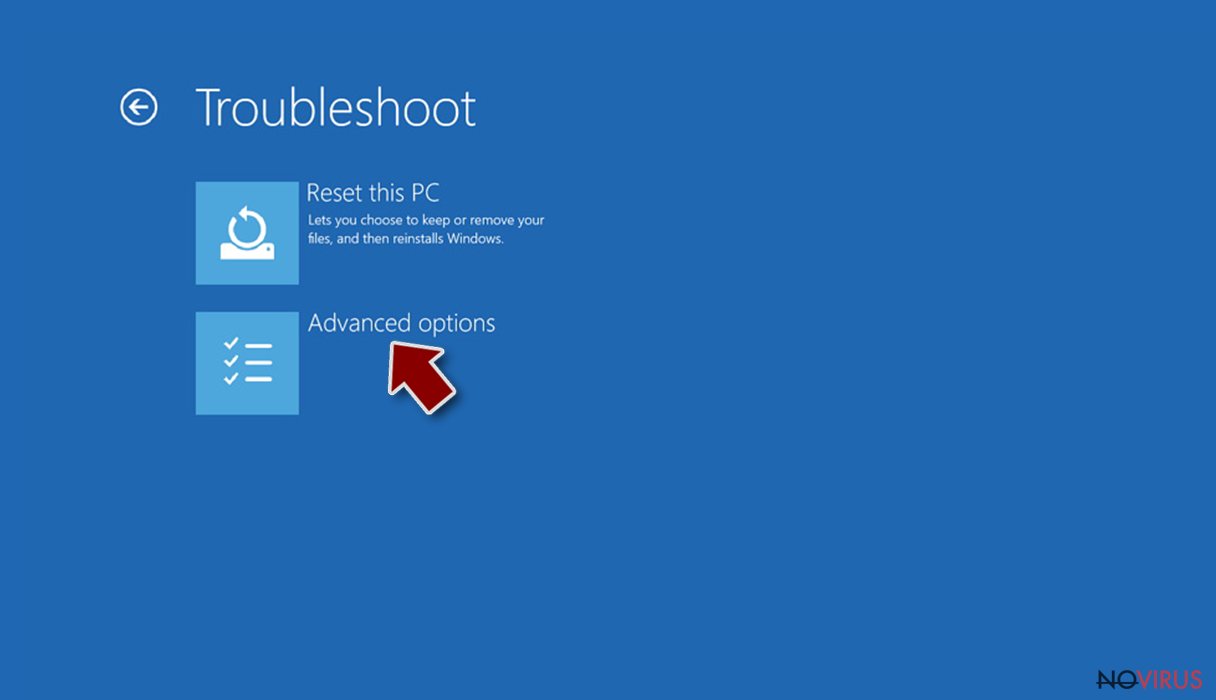
- Select Startup Settings.
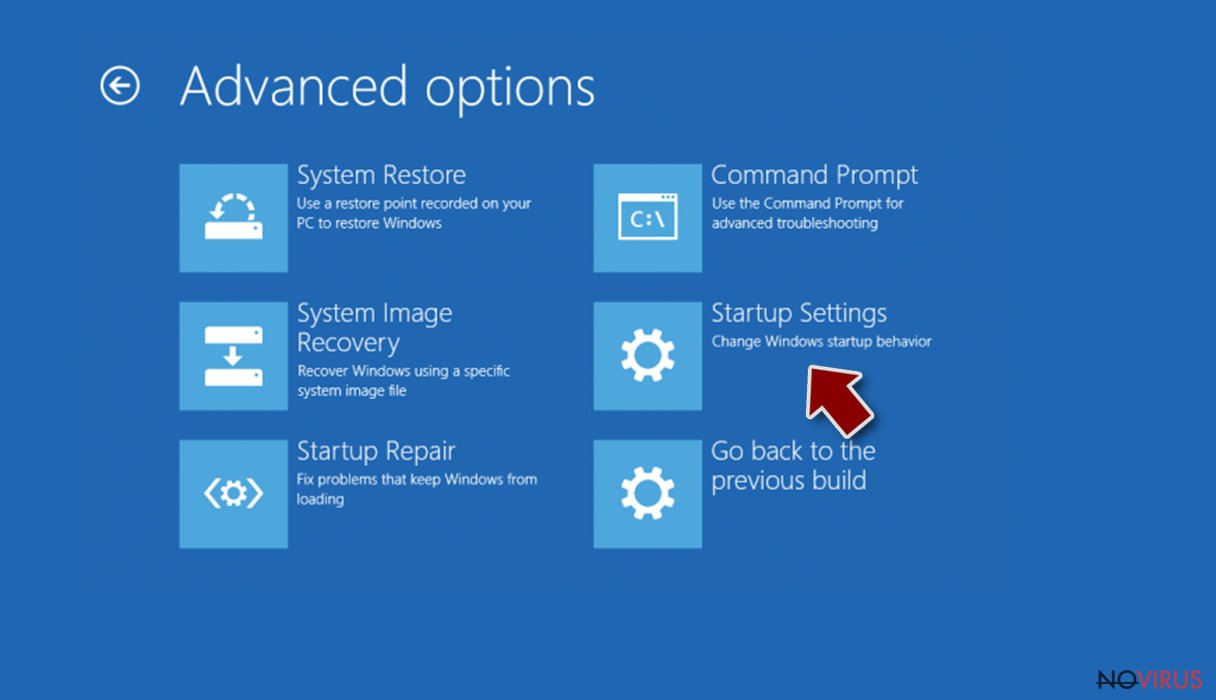
- Press Restart.
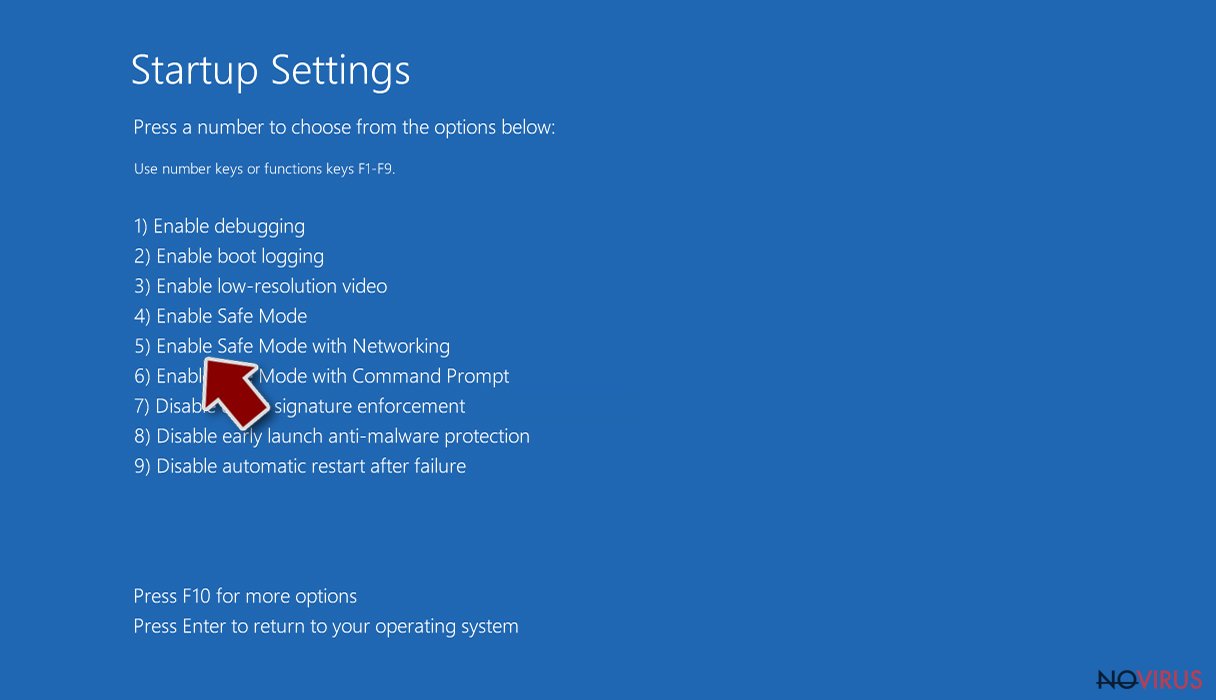
- Choose 5) Enable Safe Mode with Networking.
Step 2. End questionable processes
You can rely on Windows Task Manager that finds all the random processes in the background. When the intruder is triggering any processes, you can shut them down:
- Press Ctrl + Shift + Esc keys to open Windows Task Manager.
- Click on More details.
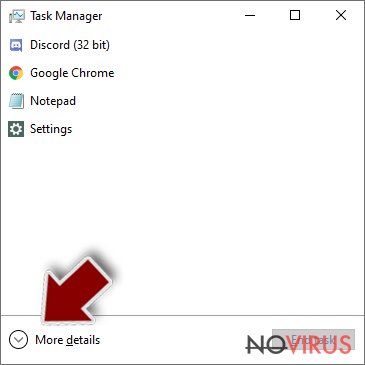
- Scroll down to Background processes.
- Look for anything suspicious.
- Right-click and select Open file location.
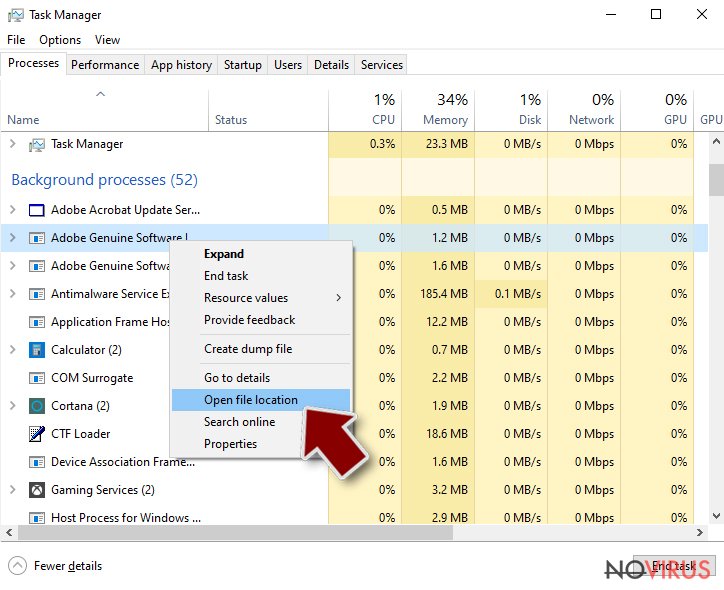
- Go back to the Process tab, right-click and pick End Task.
- Delete the contents of the malicious folder.
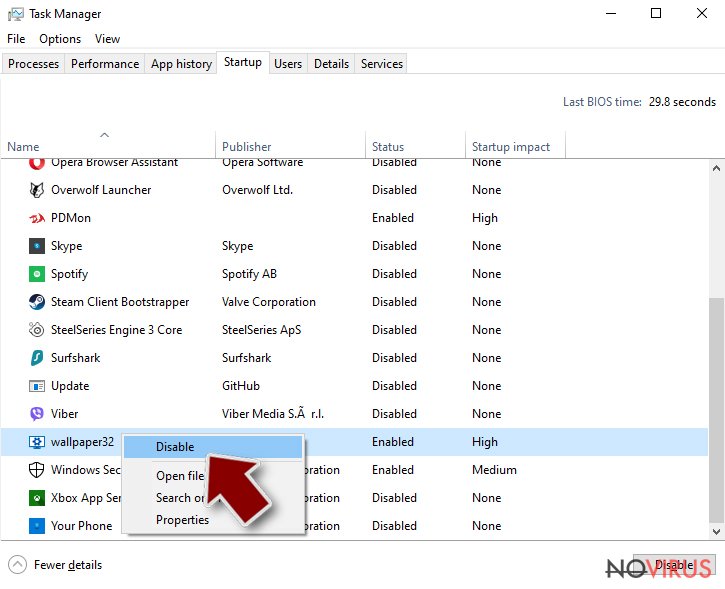
Step 3. Check the program in Startup
- Press Ctrl + Shift + Esc on your keyboard again.
- Go to the Startup tab.
- Right-click on the suspicious app and pick Disable.
Step 4. Find and eliminate virus files
Data related to the infection can be hidden in various places. Follow the steps and you can find them:
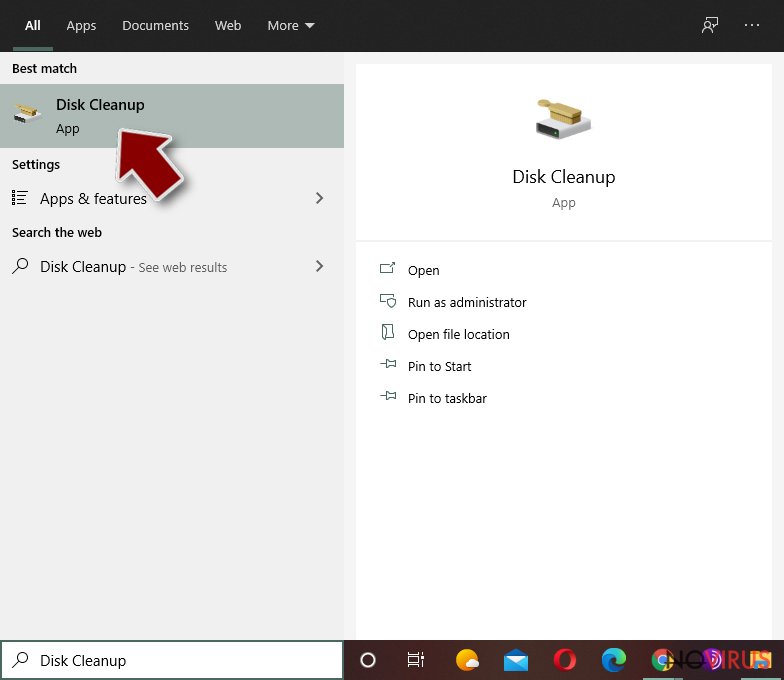
- Type in Disk Cleanup in Windows search and press Enter.
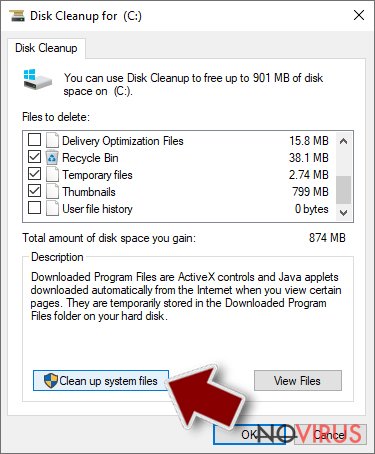
- Select the drive (C: is your main drive by default and is likely to be the one that has malicious files in) you want to clean.
- Scroll through the Files to delete and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.
- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Eliminate .locky using System Restore
-
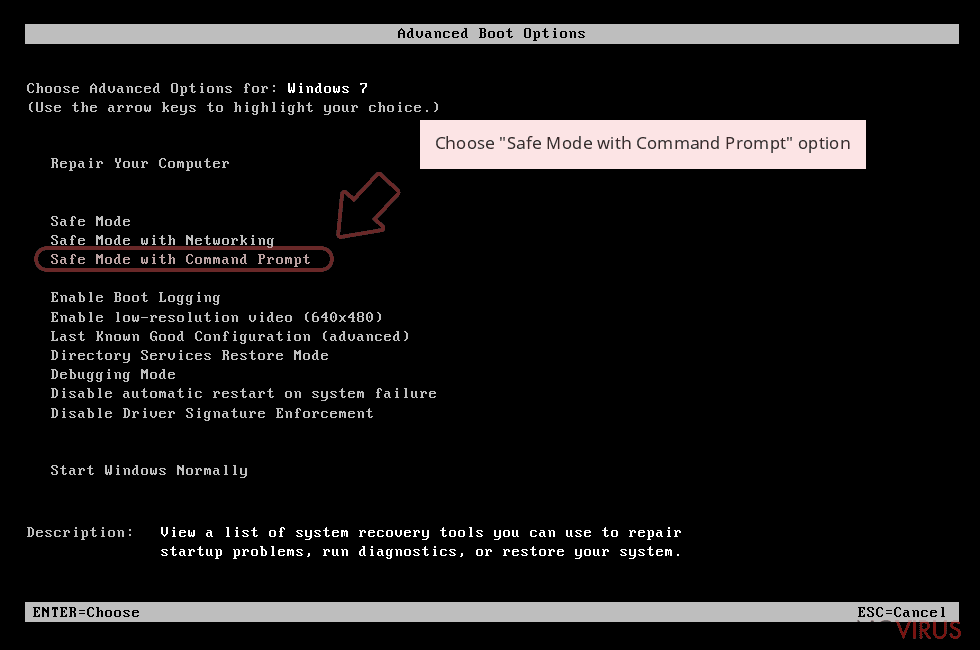
Step 1: Restart your computer in Safe Mode with Command Prompt
Windows 7 / Vista / XP- Go to Start → Shutdown → Restart → OK.
- As soon as your computer starts, start pressing F8 key repeatedly before the Windows logo shows up.
-
Choose Command Prompt from the list

Windows 10 / Windows 8- Click on the Power button at the Windows login screen, and then press and hold Shift key on your keyboard. Then click Restart.
- Then select Troubleshoot → Advanced options → Startup Settings and click Restart.
-
Once your computer starts, select Enable Safe Mode with Command Prompt from the list of options in Startup Settings.

-
Step 2: Perform a system restore to recover files and settings
-
When the Command Prompt window appears, type in cd restore and press Enter.

-
Then type rstrui.exe and hit Enter..

-
In a new window that shows up, click the Next button and choose a restore point that was created before the infiltration of .locky and then click on the Next button again.


-
To start system restore, click Yes.

-
When the Command Prompt window appears, type in cd restore and press Enter.
It is strongly recommended to take precautions and secure your computer from malware attacks. To protect your PC from .locky and other dangerous viruses, you should install and keep a powerful malware removal tool, for instance, FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes.
How to prevent from getting browser hijacker
Prevent the government from spying on you
As there is a growing debate in government about collecting users' data and spying on citizens, you should take a closer look at this issue and find out what shady ways of gathering information can be used to collect information about you. You need to browse anonymously if you want to avoid any government-initiated spying and tracking of information.
You can enjoy secure internet browsing and minimize the risk of intrusion into your system if you use Private Internet Access VPN program. This VPN application creates a virtual private network and provides access to the required data without any content restrictions.
Control government and other third party access to your data and ensure safe web browsing. Even if you do not engage in illegal activities and trust your ISP, we recommend being careful about your security. You should take extra precautions and start using a VPN program.
Recover files damaged by a dangerous malware attack
Despite the fact that there are various circumstances that can cause data to be lost on a system, including accidental deletion, the most common reason people lose photos, documents, videos, and other important data is the infection of malware.
Some malicious programs can delete files and prevent the software from running smoothly. However, there is a greater threat from the dangerous viruses that can encrypt documents, system files, and images. Ransomware-type viruses focus on encrypting data and restricting users’ access to files, so you can permanently lose personal data when you download such a virus to your computer.
The ability to unlock encrypted files is very limited, but some programs have a data recovery feature. In some cases, the Data Recovery Pro program can help recover at least some of the data that has been locked by a virus or other cyber infection.