Uninstall Onion virus (Uninstall Guide) - May 2017 updated
Onion virus Removal Guide
Description of Onion ransomware virus
Onion ransomware renews its activities
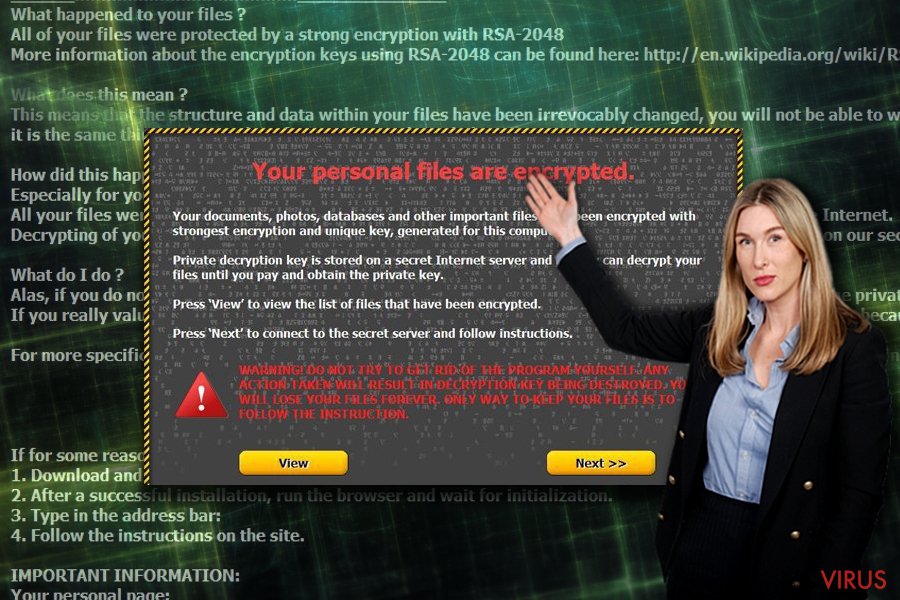
Onion virus is a name of a malicious computer program that encrypts files and appends MW_ or KK_ prefix to the filenames. Currently, known ransom notes used by this ransomware can be entitled either MW_IN FILES.txt or KK_ IN YOUR DOCUMENTS.txt. The virus usually advises the victim to pay a ransom in Bitcoins to get data recovery tools, and then get in touch with ransomware authors via one of the following email addresses: nown@ruggedinbox.com or ttk@ruggedinbox.com. This ransomware strain got its name because of usage of anonymous Tor network (also known as Onion Router) to hide identities of the attackers. The malicious virus is often associated with infamous ransomware viruses such as CryptoLocker or CTB-Locker, although its name can easily confuse ransomware victims infected by .onion file extension virus. This ransomware virus first emerged in 2015 and was recognized as one of the most greedy ransomware viruses. However, it seems that new versions of this ransomware appear from time to time, so victims are advised to protect their computers to prevent ransomware infiltration. To remove Onion virus, anti-malware programs must be used. Our team typically recommends FortectIntego or Malwarebytes software.
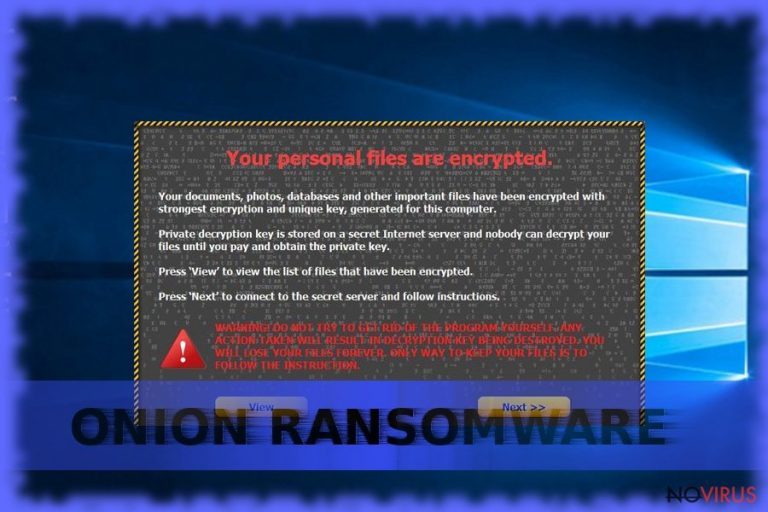
The Onion virus sneaks into the system silently and then searches for files to encrypt. It typically targets .xls, .pdf, .ppt, .pdf, .jpeg, .jpg, .txt, .mp4, .mp3, .doc, .docm, .zip and other files, which, if found, it modified using a public encryption key. This modification can be reversed only with the help of a private key, which is also known as the decryption key. This key is stored in cyber criminals’ servers, and it is impossible to get it without cybercriminals’ permission. That is why these frauds demand a ransom. However, efforts of malware analysts did pay off – there are some decryption tools that can come in handy when dealing with particular ransomware variants. We suggest looking at data recovery instructions provided below the article if you want to try and recover your files without paying the ransom.
Distribution techniques used to disseminate ransomware
Onion ransomware is mostly distributed via exploit kits, mail spam, malvertising, and of course, illegal websites. The ransomware typically arrives in a .ZIP file along with deceptive email messages composed by cybercriminals. This is why it is extremely important to check if the sender is a reliable individual. Scammers often pretend to be employees of legitimate companies, but do not fall for such traps – even if the sender claims to be working at well-known companies or organizations and asks you to open email attachments that are presented as invoices, subpoenas or other documents, do not rush to do it. Opening such email attachments will only infect your PC with malicious programs. It is also advisable to stay away from sites that urge you to install Java, Media Player, or Flash Player updates, because such updates are typically fake. These software updates should be installed only from websites that belong to the official developer of the particular software.
Remove Onion ransomware from the affected computer
You must remove Onion virus as soon as you notice that it managed to sneak into your computer because as long as it stays on the computer system, it keeps it vulnerable and opens a path for additional malware variants to sneak in. Your computer might also become sluggish and fail to complete tasks properly. For Onion removal, you should employ a powerful anti-malware software such as FortectIntego to wipe all dangerous files, programs, and fix modified registry keys all at once. Before you start, read these tips carefully.
Getting rid of Onion virus. Follow these steps
In-depth guide for the Onion elimination
The guide provided below explains how to start the computer in Safe Mode with Networking so that you could eliminate the virus with ease.
Important! →
The elimination guide can appear too difficult if you are not tech-savvy. It requires some knowledge of computer processes since it includes system changes that need to be performed correctly. You need to take steps carefully and follow the guide avoiding any issues created due to improper setting changes. Automatic methods might suit you better if you find the guide too difficult.
Step 1. Launch Safe Mode with Networking
Safe Mode environment offers better results of manual virus removal
Windows 7 / Vista / XP
- Go to Start.
- Choose Shutdown, then Restart, and OK.
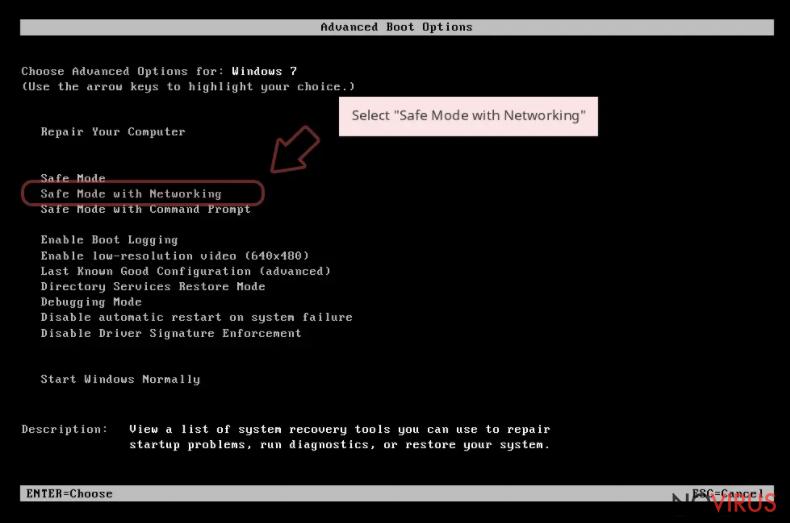
- When your computer boots, start pressing the F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) a few times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.
Windows 10 / Windows 8
- Right-click the Start button and choose Settings.
- Scroll down to find Update & Security.
- On the left, pick Recovery.
- Scroll to find Advanced Startup section.
- Click Restart now.
- Choose Troubleshoot.
- Go to Advanced options.
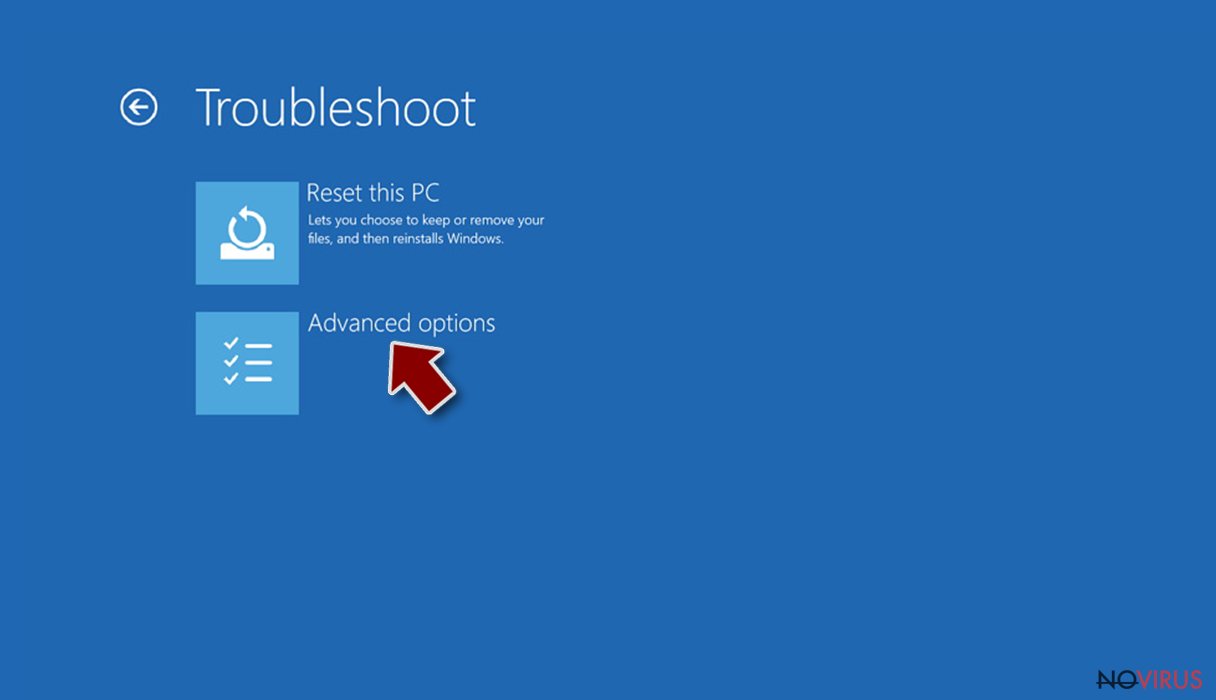
- Select Startup Settings.
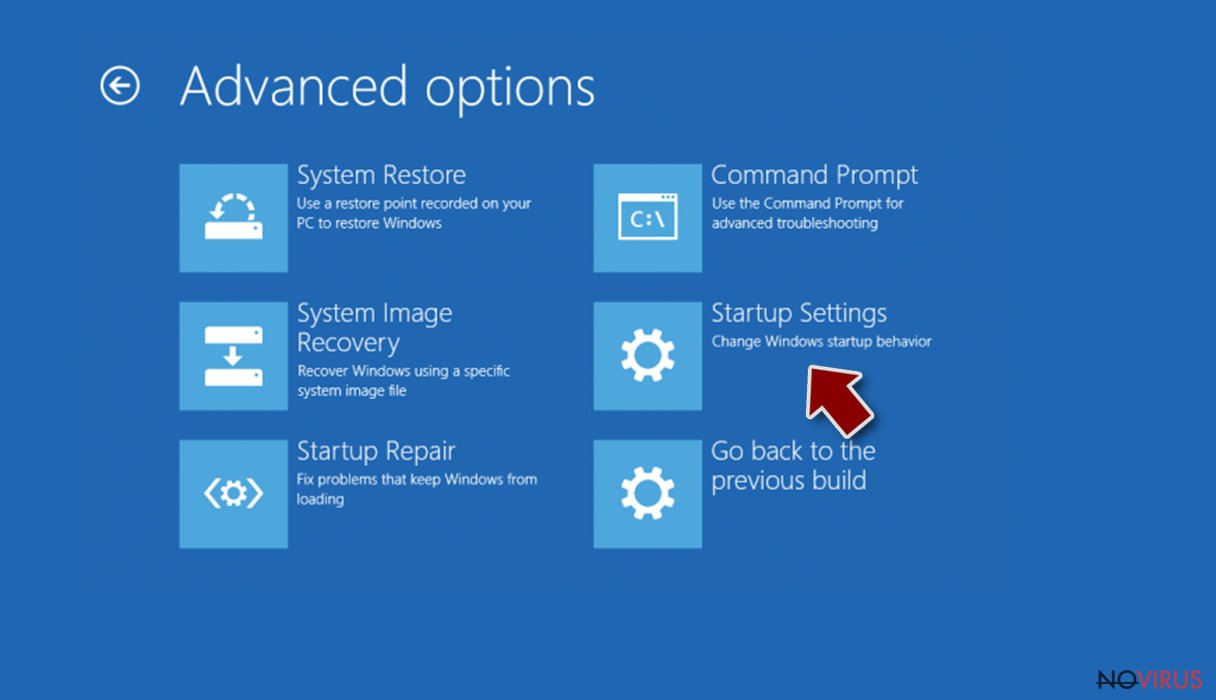
- Press Restart.
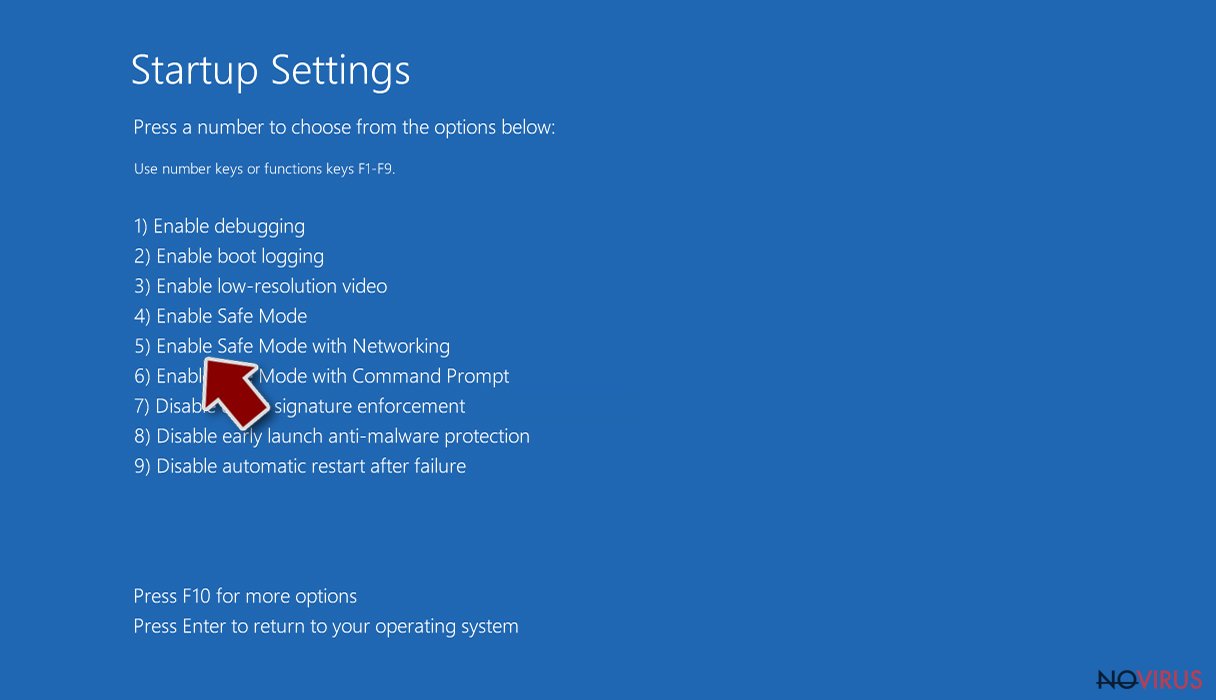
- Choose 5) Enable Safe Mode with Networking.
Step 2. End questionable processes
You can rely on Windows Task Manager that finds all the random processes in the background. When the intruder is triggering any processes, you can shut them down:
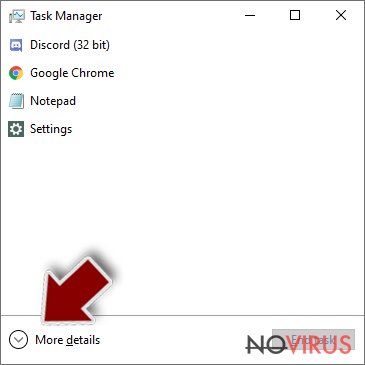
- Press Ctrl + Shift + Esc keys to open Windows Task Manager.
- Click on More details.
- Scroll down to Background processes.
- Look for anything suspicious.
- Right-click and select Open file location.
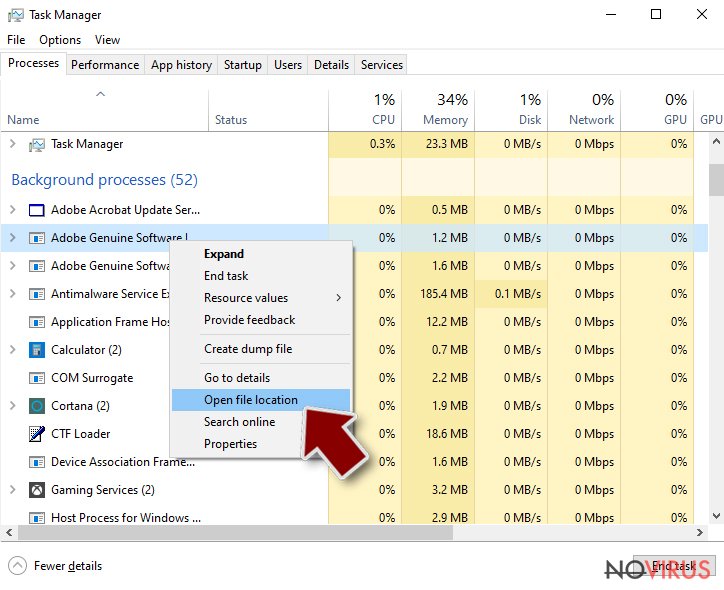
- Go back to the Process tab, right-click and pick End Task.
- Delete the contents of the malicious folder.
Step 3. Check the program in Startup
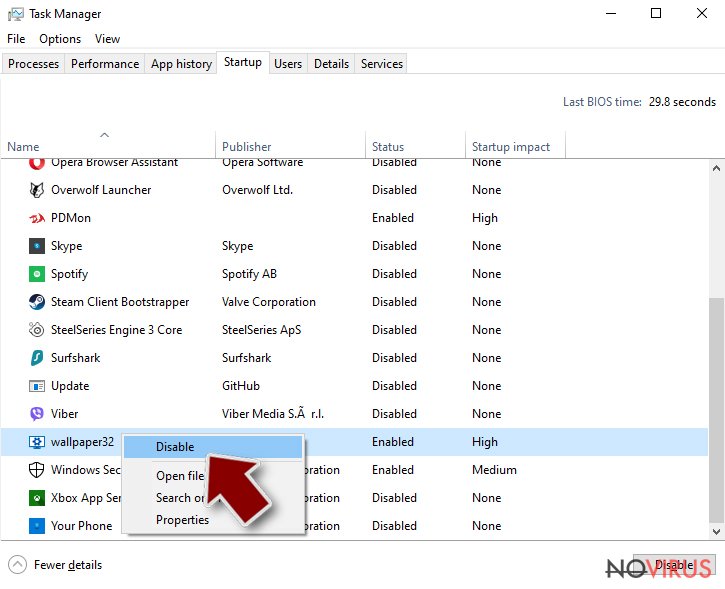
- Press Ctrl + Shift + Esc on your keyboard again.
- Go to the Startup tab.
- Right-click on the suspicious app and pick Disable.
Step 4. Find and eliminate virus files
Data related to the infection can be hidden in various places. Follow the steps and you can find them:
- Type in Disk Cleanup in Windows search and press Enter.
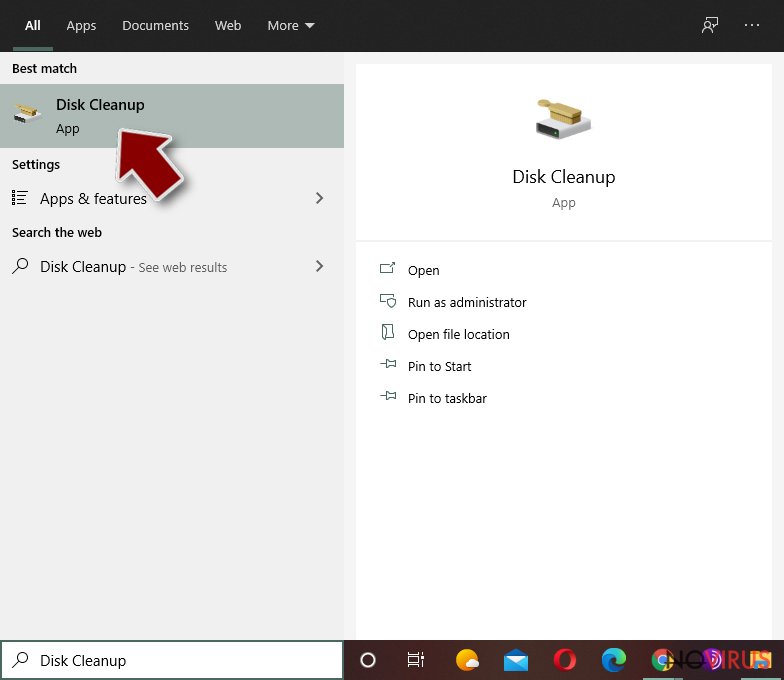
- Select the drive (C: is your main drive by default and is likely to be the one that has malicious files in) you want to clean.
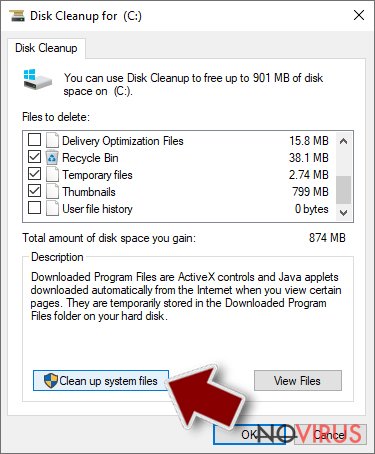
- Scroll through the Files to delete and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.
- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Eliminate Onion using System Restore
-
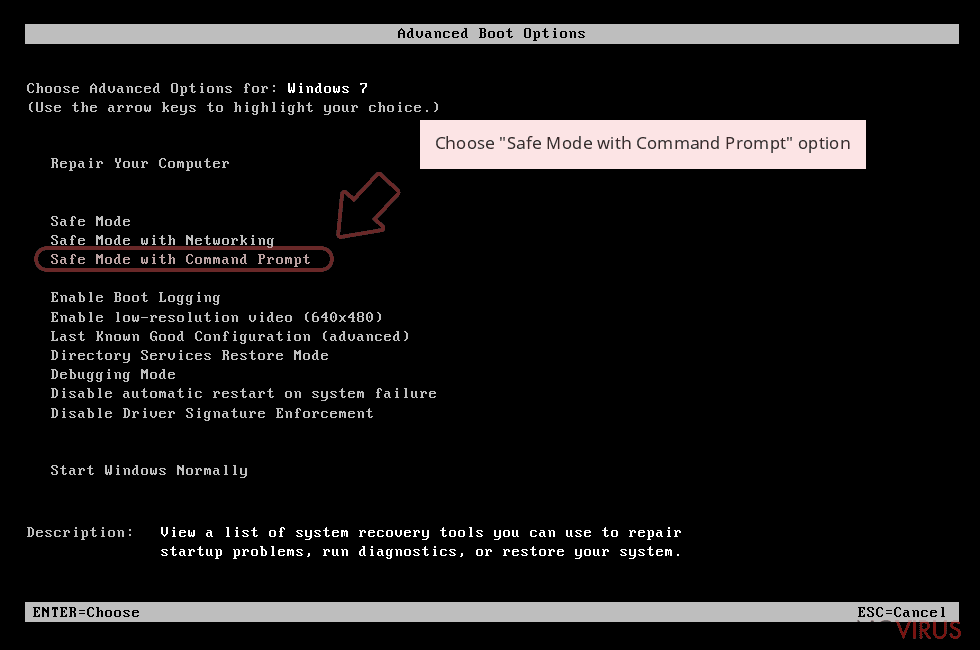
Step 1: Restart your computer in Safe Mode with Command Prompt
Windows 7 / Vista / XP- Go to Start → Shutdown → Restart → OK.
- As soon as your computer starts, start pressing F8 key repeatedly before the Windows logo shows up.
-
Choose Command Prompt from the list

Windows 10 / Windows 8- Click on the Power button at the Windows login screen, and then press and hold Shift key on your keyboard. Then click Restart.
- Then select Troubleshoot → Advanced options → Startup Settings and click Restart.
-
Once your computer starts, select Enable Safe Mode with Command Prompt from the list of options in Startup Settings.

-
Step 2: Perform a system restore to recover files and settings
-
When the Command Prompt window appears, type in cd restore and press Enter.

-
Then type rstrui.exe and hit Enter..

-
In a new window that shows up, click the Next button and choose a restore point that was created before the infiltration of Onion and then click on the Next button again.


-
To start system restore, click Yes.

-
When the Command Prompt window appears, type in cd restore and press Enter.
Bonus: Restore your files
Using the tutorial provided above you should be able to eliminate Onion from the infected device. novirus.uk team has also prepared an in-depth data recovery guide which you will also find above.There are a couple of methods you can apply to recover data encrypted by Onion:
Recovering data with Data Recovery Pro
The software we suggest in this data recovery option usually helps to restore modified, deleted, or corrupted files. You should definitely give it a try.
- Download Data Recovery Pro;
- Install Data Recovery on your computer following the steps indicated in the software’s Setup;
- Run the program to scan your device for the data encrypted by Onion ransomware;
- Recover the data.
Test ShadowExplorer’s capabilities
If you’re lucky, the ransomware may have left some Volume Shadow Copies on the system, which can come in handy when trying to restore encrypted files. Let ShadowExplorer assist you in finding these copies on the system.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Install Shadow Explorer on your computer following the instructions in the software’s Setup Wizard;
- Run the program. Navigate to the menu on the top-left corner and select a disk containing your encrypted files. Look through the available folders;
- When you find the folder you want to recover, right-click it and select “Export”. Also, choose where the recovered data will be stored.
Use Onion Decryption tool
In case you were infected with Onion ransomware that happens to be Dharma’s spin-off, you should definitely try Dharma Decryptor. Keep in mind that this decryption tool might not work – if so, you should know that your PC was affected by an updated ransomware version.
It is strongly recommended to take precautions and secure your computer from malware attacks. To protect your PC from Onion and other dangerous viruses, you should install and keep a powerful malware removal tool, for instance, FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes.
How to prevent from getting ransomware
A proper web browser and VPN tool can guarantee better safety
As online spying becomes an increasing problem, people are becoming more interested in how to protect their privacy. One way to increase your online security is to choose the most secure and private web browser. But if you want complete anonymity and security when surfing the web, you need Private Internet Access VPN service. This tool successfully reroutes traffic across different servers, so your IP address and location remain protected. It is also important that this tool is based on a strict no-log policy, so no data is collected and cannot be leaked or made available to first or third parties. If you want to feel safe on the internet, a combination of a secure web browser and a Private Internet Access VPN will help you.
Recover files damaged by a dangerous malware attack
Despite the fact that there are various circumstances that can cause data to be lost on a system, including accidental deletion, the most common reason people lose photos, documents, videos, and other important data is the infection of malware.
Some malicious programs can delete files and prevent the software from running smoothly. However, there is a greater threat from the dangerous viruses that can encrypt documents, system files, and images. Ransomware-type viruses focus on encrypting data and restricting users’ access to files, so you can permanently lose personal data when you download such a virus to your computer.
The ability to unlock encrypted files is very limited, but some programs have a data recovery feature. In some cases, the Data Recovery Pro program can help recover at least some of the data that has been locked by a virus or other cyber infection.