Uninstall Nagini virus (Free Removal Guide)
Nagini virus Removal Guide
Description of Nagini ransomware virus
Nagini virus is as sneaky and shady as Lord Voldemort’s pet
If you have ever dreamt about the possibility to meet characters from the magical Harry Potter’s world, now you have an opportunity – hackers has recently launched a new ransomware called the Nagini virus. Indeed, the meeting with Lord Voldemort’s pet snake is not a pleasant date. Michael Gillespie, the famous virus researcher, has recently discovered this new ransomware, and it seems malware still under development. The virus is still a mystery for virus researchers; however, the latest information claims that it might be created for testing particular systems. Nagini malware slightly differs from former ransomware viruses. After secretly infiltrating computer’s system, it locks the screen of the infected computer and targets only popular file formats, such as Microsoft Office products, various picture formats, PDF, etc. However, it encrypts only those files that are stored in C:\Users\Colosseum\Desktop\files\ directory and does not append any specific file extension to encrypted files. What is more, it seems that developers are not interested in swindling the money from the victims right now. They do not provide any ransom note and do not ask to pay the ransom in Bitcoins. All they ask for getting back access to a computer is victim’s credit card’s number. Should you tell it? Absolutely not! You should never reveal your personal information to criminals. If this malicious snake sneaked into your PC, do not let it settle here. You have to remove Nagini as soon as it appears on your computer.
Similarly to other ransomware viruses, Nagini infiltrates computer’s system without users’ knowledge and realisation. It usually spreads via malicious email campaigns and exploits its malicious file when a user downloads an infected attachment. Once inside, malware demonstratively announces about its appearance by locking the screen and delivering a picture of Voldemort and his creepy pet. The creators of Nagini virus are called ‘Colosseum.’ It’s still unknown if it’s a group of developers or a single person. However, it doesn’t change the fact that ‘Colosseum’ has some dark and secret purposes. Virus researchers are still analysing this mysterious virus and its features. For example, after successful file encryption, it creates C:\Temp\voldemort.horcrux folder. Why? We still do not have any explanation. We recommend Nagini removal until it hasn’t caused more problems and damage to your computer or personal privacy. For malware elimination, we suggest using reputable anti-malware tools such as FortectIntego.

What are the distribution techniques of the ransomware?
Nagini ransomware uses the same distribution techniques as other file-encrypting viruses. It travels via malicious email attachments and Trojans. The trickiest way to encounter the virus is to open a suspicious email attachment. Indeed, hackers became good liars and persuaders. They can pretend to be representatives from reputable organizations and rename infected files that they would not raise any suspicion for the victims. One of the ways to prevent ransomware from sneaking into your PC is to avoid opening spam emails and downloading questionable attachments. Also, the virus can travel as a Trojan horse. In this case, you have to be careful while you are browsing the Internet and installing freeware. Stay away from questionable websites, avoid clicking shady ads and for software downloads always choose reliable domains. Lastly, using a professional security program also minimizes the possibility of encountering a hazardous virus.
How to get rid of Nagini ransomware?
The creators of the virus are still developing malware, so you cannot be sure what they are planning to do. Do not risk and remove Nagini immediately. Ransomware-type viruses are one of the most dangerous types of computer infections, so they must be taken seriously. Do not consider eliminating virus manually. You should initiate Nagini removal with a help of professional malware removal tools such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes. Scan your computer with one of these programs. If you encounter some difficulties, follow instructions provided bellow. Also, you will find instructions how to recover locked files.
Getting rid of Nagini virus. Follow these steps
In-depth guide for the Nagini elimination
Nagini virus delivers lock screen every time you turn on your computer. For this reason, it might be difficult or even impossible to access security tools and scan the system. However, you can do it by rebooting your computer in the Safe Mode. Follow these steps:
Important! →
The elimination guide can appear too difficult if you are not tech-savvy. It requires some knowledge of computer processes since it includes system changes that need to be performed correctly. You need to take steps carefully and follow the guide avoiding any issues created due to improper setting changes. Automatic methods might suit you better if you find the guide too difficult.
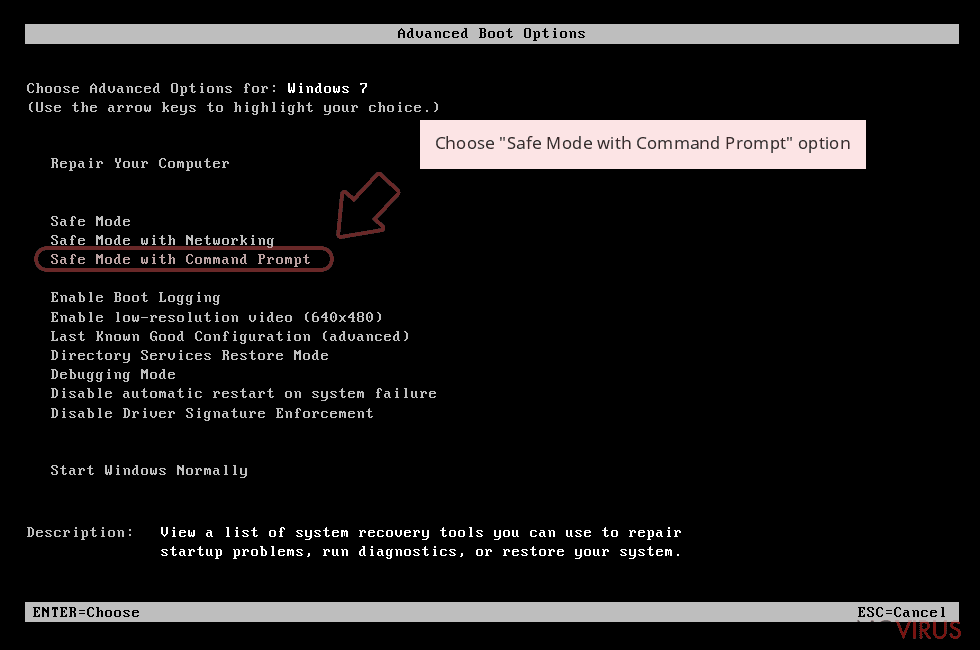
Step 1. Launch Safe Mode with Networking
Safe Mode environment offers better results of manual virus removal
Windows 7 / Vista / XP
- Go to Start.
- Choose Shutdown, then Restart, and OK.
- When your computer boots, start pressing the F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) a few times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.
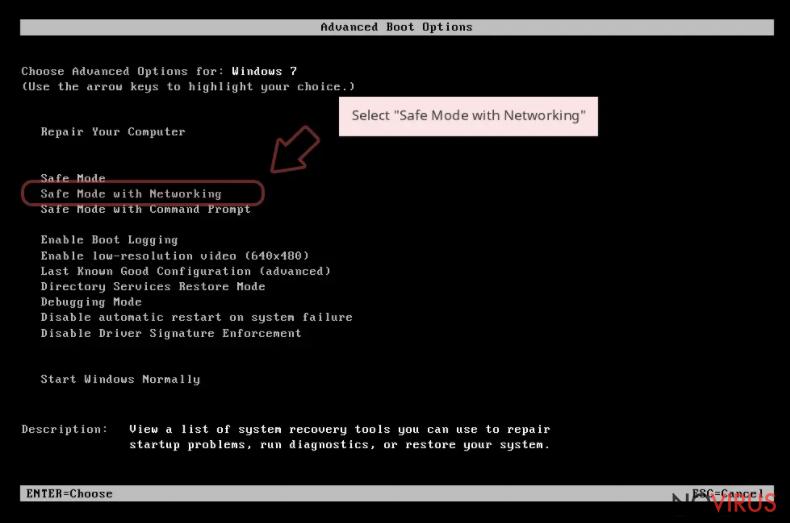
Windows 10 / Windows 8
- Right-click the Start button and choose Settings.
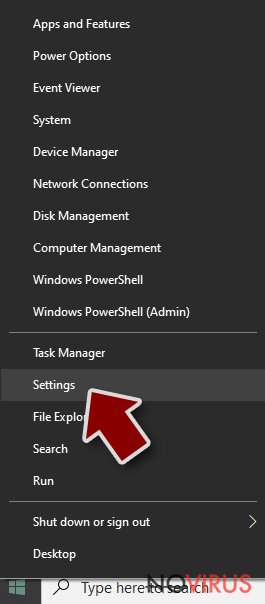
- Scroll down to find Update & Security.
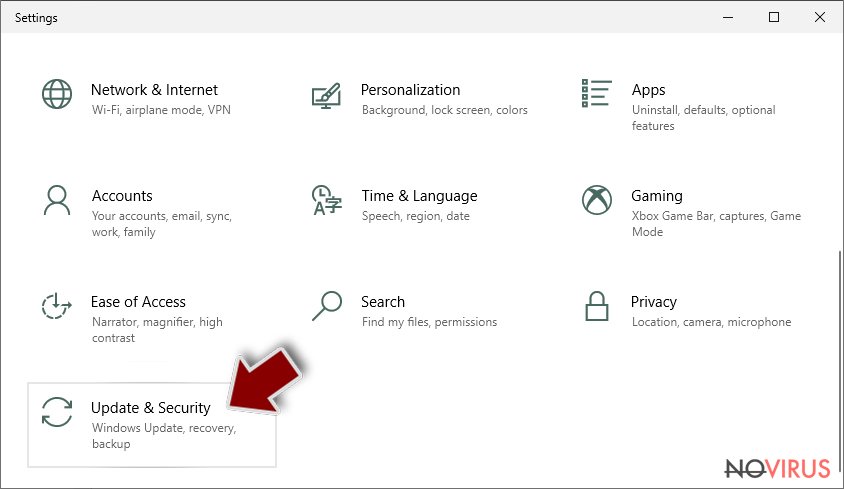
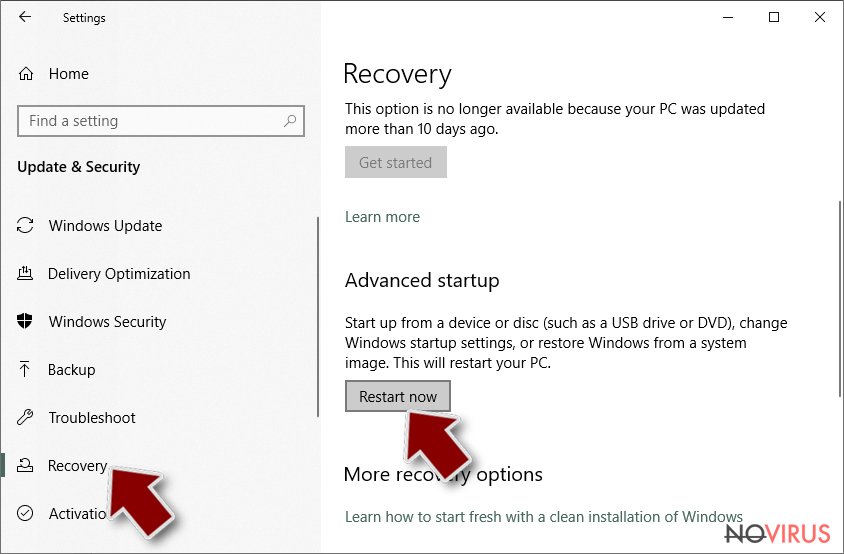
- On the left, pick Recovery.
- Scroll to find Advanced Startup section.
- Click Restart now.
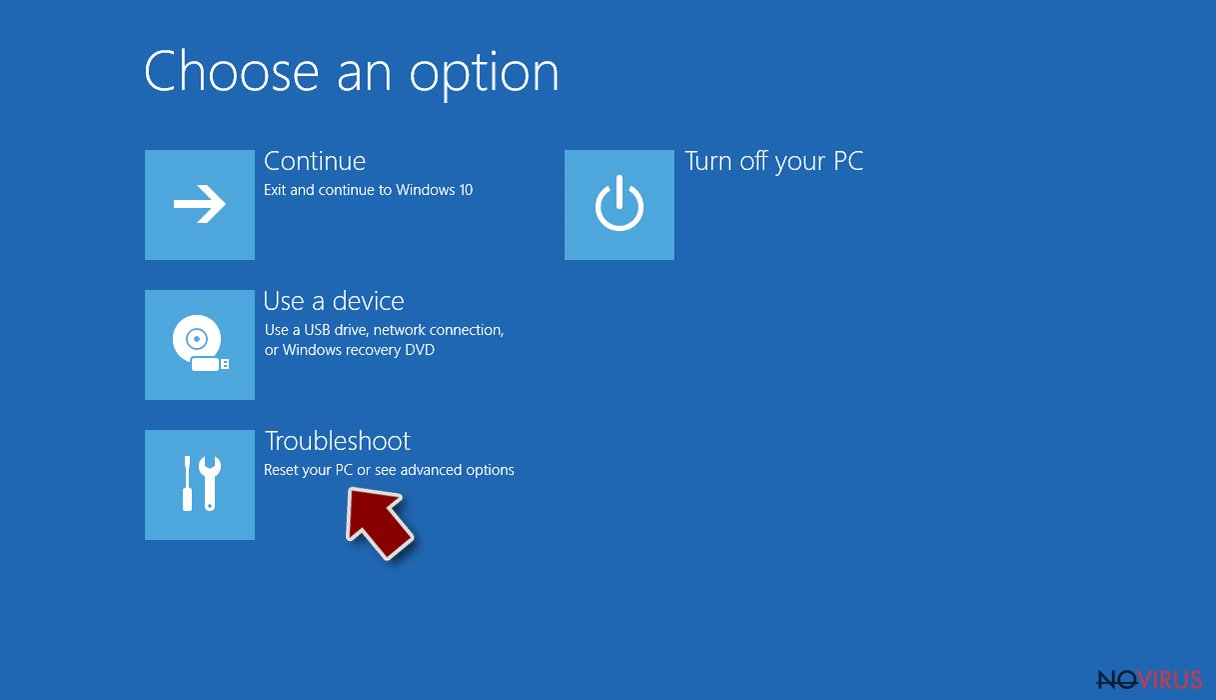
- Choose Troubleshoot.
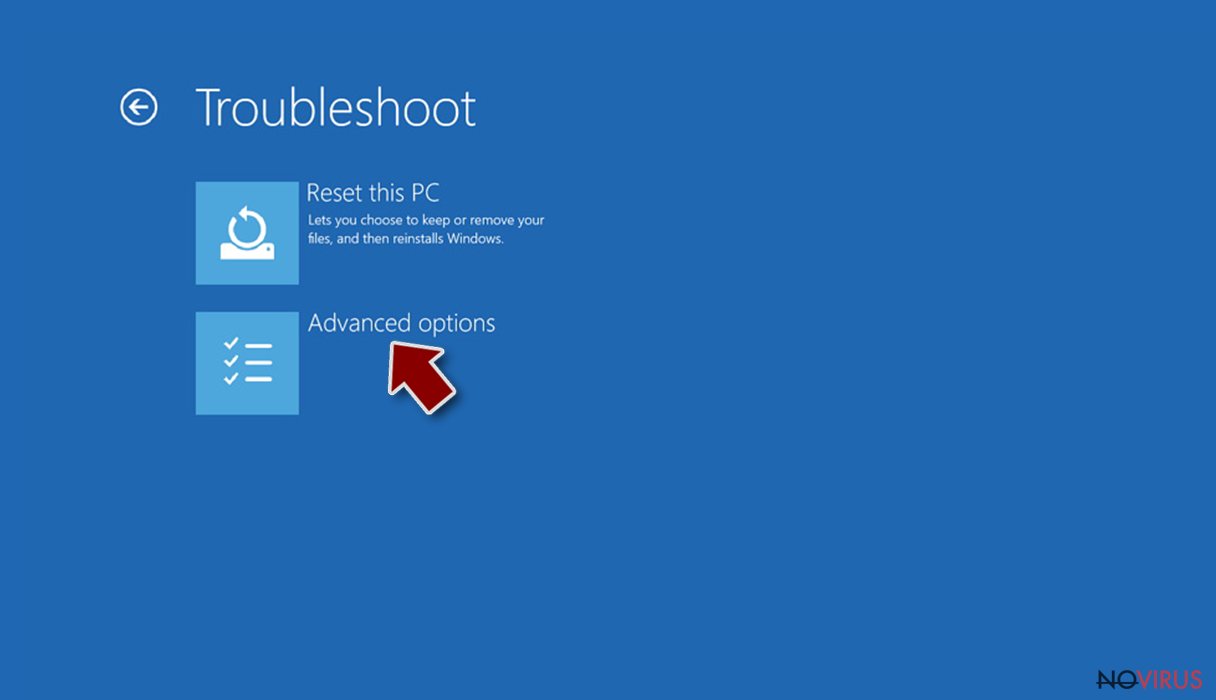
- Go to Advanced options.
- Select Startup Settings.
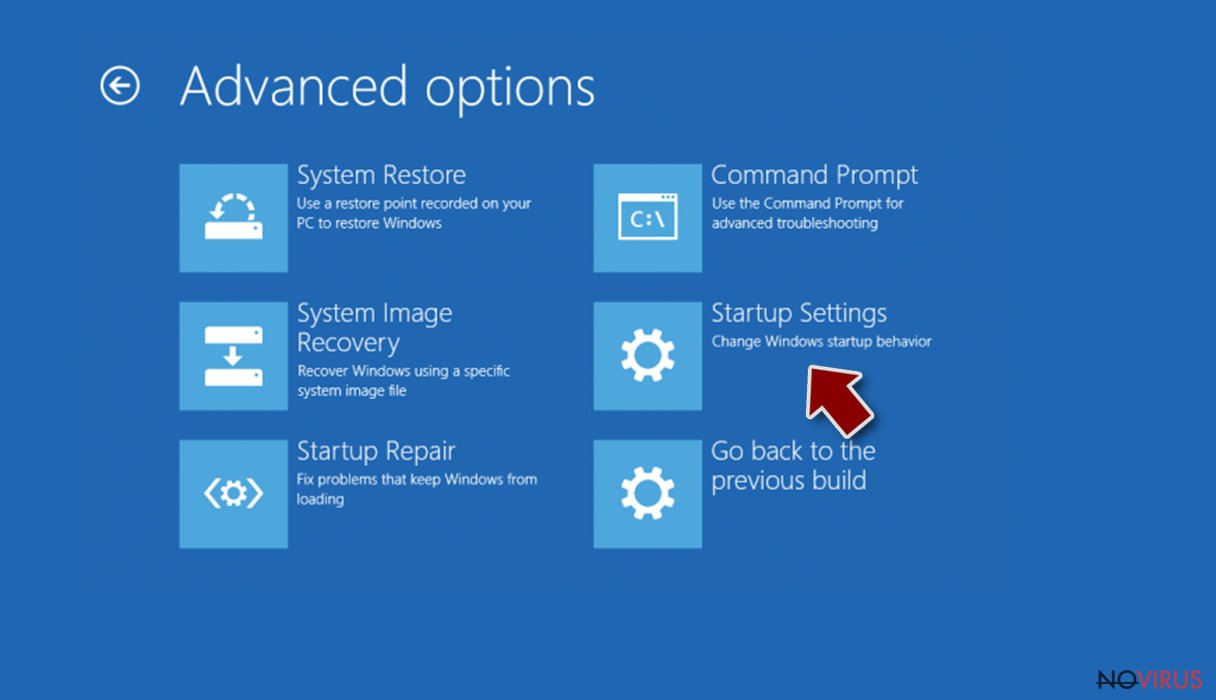
- Press Restart.
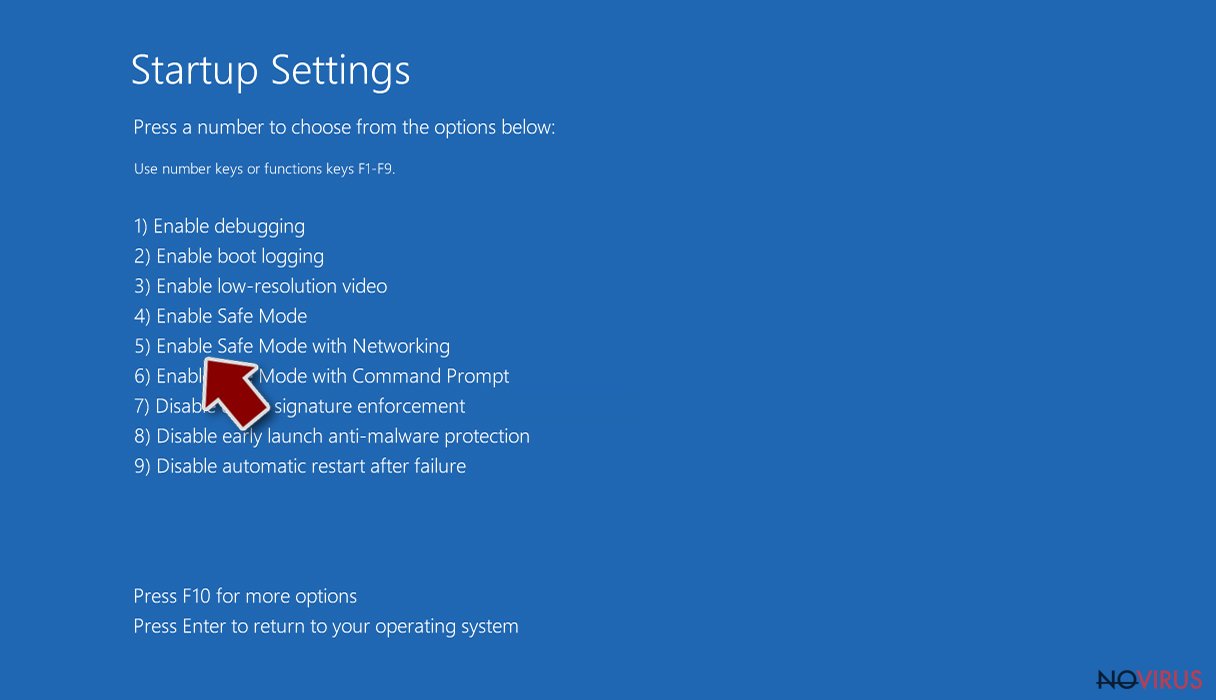
- Choose 5) Enable Safe Mode with Networking.
Step 2. End questionable processes
You can rely on Windows Task Manager that finds all the random processes in the background. When the intruder is triggering any processes, you can shut them down:
- Press Ctrl + Shift + Esc keys to open Windows Task Manager.
- Click on More details.
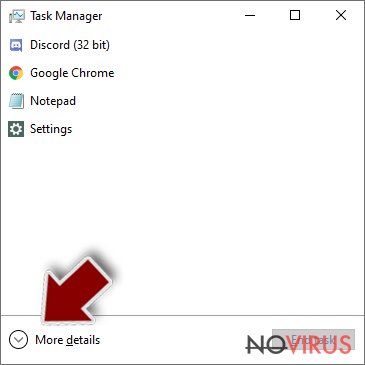
- Scroll down to Background processes.
- Look for anything suspicious.
- Right-click and select Open file location.
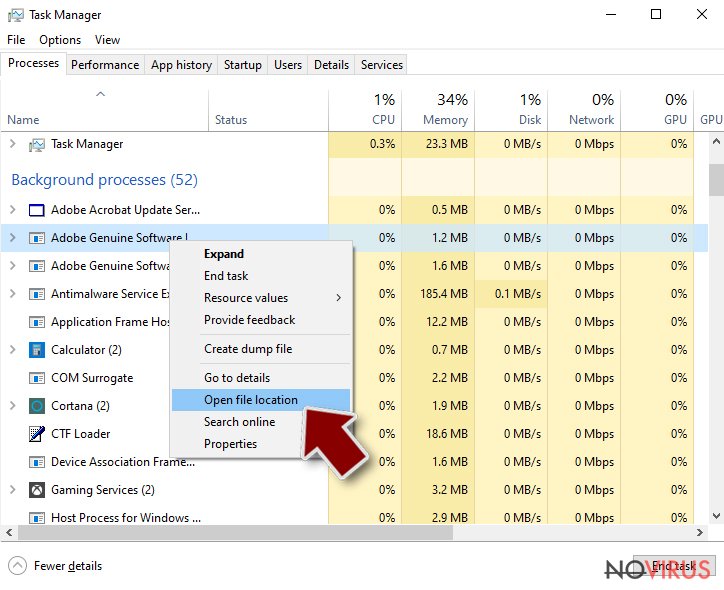
- Go back to the Process tab, right-click and pick End Task.
- Delete the contents of the malicious folder.
Step 3. Check the program in Startup
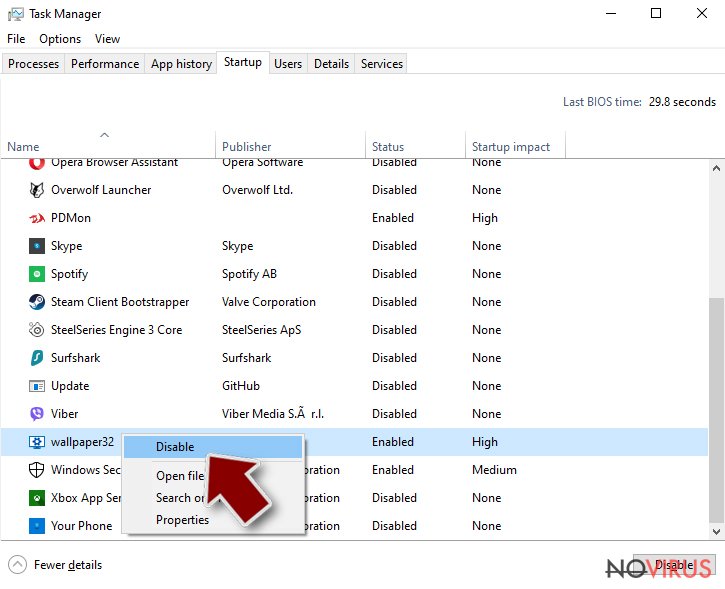
- Press Ctrl + Shift + Esc on your keyboard again.
- Go to the Startup tab.
- Right-click on the suspicious app and pick Disable.
Step 4. Find and eliminate virus files
Data related to the infection can be hidden in various places. Follow the steps and you can find them:
- Type in Disk Cleanup in Windows search and press Enter.
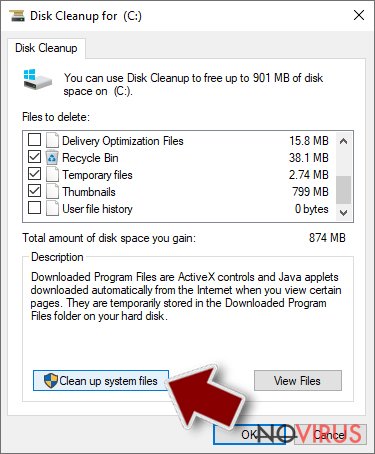
- Select the drive (C: is your main drive by default and is likely to be the one that has malicious files in) you want to clean.
- Scroll through the Files to delete and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.
- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Eliminate Nagini using System Restore
You have to find and remove these malicious files from your computer:
c:/Temp/voldemort.horcrux
%UserProfile%\Nagini.exe
-
Step 1: Restart your computer in Safe Mode with Command Prompt
Windows 7 / Vista / XP- Go to Start → Shutdown → Restart → OK.
- As soon as your computer starts, start pressing F8 key repeatedly before the Windows logo shows up.
-
Choose Command Prompt from the list

Windows 10 / Windows 8- Click on the Power button at the Windows login screen, and then press and hold Shift key on your keyboard. Then click Restart.
- Then select Troubleshoot → Advanced options → Startup Settings and click Restart.
-
Once your computer starts, select Enable Safe Mode with Command Prompt from the list of options in Startup Settings.

-
Step 2: Perform a system restore to recover files and settings
-
When the Command Prompt window appears, type in cd restore and press Enter.

-
Then type rstrui.exe and hit Enter..

-
In a new window that shows up, click the Next button and choose a restore point that was created before the infiltration of Nagini and then click on the Next button again.


-
To start system restore, click Yes.

-
When the Command Prompt window appears, type in cd restore and press Enter.
Bonus: Restore your files
Using the tutorial provided above you should be able to eliminate Nagini from the infected device. novirus.uk team has also prepared an in-depth data recovery guide which you will also find above.There are a couple of methods you can apply to recover data encrypted by Nagini:
Recover locked files with Data Recovery Pro
Nagini is not as dangerous as other ransomware viruses, so you can retrieve locked files with Data Recovery Pro. Instructions how to use this software are presented bellow:
- Download Data Recovery Pro;
- Install Data Recovery on your computer following the steps indicated in the software’s Setup;
- Run the program to scan your device for the data encrypted by Nagini ransomware;
- Recover the data.
Use Windows Previous Versions feature to recover your files
If you have enabled System Restore function before ransomware attack, you can use this technique to recover your data. Follow these steps and recover files locked by Nagini virus:
- Right-click on the encrypted document you want to recover;
- Click “Properties” and navigate to “Previous versions” tab;
- In the “Folder versions” section look for the available file copies. Choose the desired version and press “Restore”.
Recover your data using ShadowExplorer
Windows OS users can use ShadowExplorer for recovering data from the Volum Shadow Copies. Follow short instructions how to do it:
- Download Shadow Explorer (http://shadowexplorer.com/);
- Install Shadow Explorer on your computer following the instructions in the software’s Setup Wizard;
- Run the program. Navigate to the menu on the top-left corner and select a disk containing your encrypted files. Look through the available folders;
- When you find the folder you want to recover, right-click it and select “Export”. Also, choose where the recovered data will be stored.
It is strongly recommended to take precautions and secure your computer from malware attacks. To protect your PC from Nagini and other dangerous viruses, you should install and keep a powerful malware removal tool, for instance, FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes.
How to prevent from getting ransomware
A proper web browser and VPN tool can guarantee better safety
As online spying becomes an increasing problem, people are becoming more interested in how to protect their privacy. One way to increase your online security is to choose the most secure and private web browser. But if you want complete anonymity and security when surfing the web, you need Private Internet Access VPN service. This tool successfully reroutes traffic across different servers, so your IP address and location remain protected. It is also important that this tool is based on a strict no-log policy, so no data is collected and cannot be leaked or made available to first or third parties. If you want to feel safe on the internet, a combination of a secure web browser and a Private Internet Access VPN will help you.
Recover files damaged by a dangerous malware attack
Despite the fact that there are various circumstances that can cause data to be lost on a system, including accidental deletion, the most common reason people lose photos, documents, videos, and other important data is the infection of malware.
Some malicious programs can delete files and prevent the software from running smoothly. However, there is a greater threat from the dangerous viruses that can encrypt documents, system files, and images. Ransomware-type viruses focus on encrypting data and restricting users’ access to files, so you can permanently lose personal data when you download such a virus to your computer.
The ability to unlock encrypted files is very limited, but some programs have a data recovery feature. In some cases, the Data Recovery Pro program can help recover at least some of the data that has been locked by a virus or other cyber infection.