Uninstall Locky virus (Uninstall Instructions) - Aug 2017 updated
Locky virus Removal Guide
Description of Locky ransomware
An investigation of the Locky ransomware virus:
After receiving multiple new reports about the Locky virus attacks on the users computers our team of experts have found that, in fact, Locky ransomware virus, a clone of the aforementioned Locky virus, is responsible for the newly arising mayhem among the computer users.
This ransomware works identically to the notorious Locky virus and majority of other malicious programs of the same category. It initially gets into the users computers as a supposedly important email attachment, containing invoice, speeding tickets or similar information. Then, the virus starts scanning the system in search of files. The primary targets are photo/video files, different documents, archives and other files that the virus considers to be valuable.
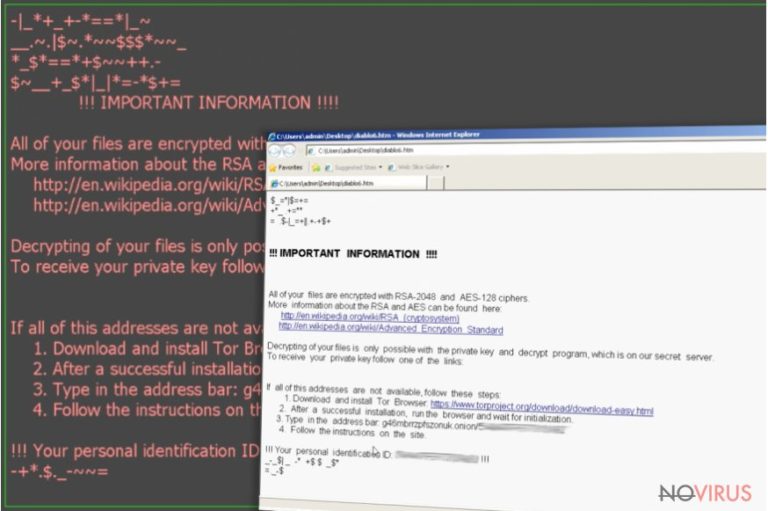
After the virus detects the files, a complex encryption process is then carried out to lock them with RSA-2048 and AES-128 algorithms, generally used for military purposes. Because of the encryption intricacy, it is virtually impossible to unlock the infected files without a special encryption key. This key can only be obtained by purchasing it from the ransomware developers themselves. However, the researchers around the world are working on the Locky ransomware decryption tool and, hopefully, one day the virus victims will have the ability to recover their files without having to pay the ransom.
In the meanwhile, if you want to be able to use your computer normally, the only solution is to remove Locky ransomware from the computer without a delay. Even though a specifically designed Locky ransomware removal tool does not exist, a quick virus elimination can be achieved by employing professional virus-fighting utilities, such as FortectIntego.
How can you tell if your computer has been infiltrated by this ransomware?
As we already mentioned, the main tell-tale sign of the Locky ransomware infection is the inability to access your files. The infected files will usually feature file extension .locky instead of the regular ones added to them. Also, you will find that every folder that contains such files also includes one non-encrypted .txt document labeled _Locky_recover_instructions.
This document is, in fact, the ransom note which the virus creators drop on the victims’ computers to explain the following steps they must take to get their files back. Essentially, there are three basic stages of the file retrieval:
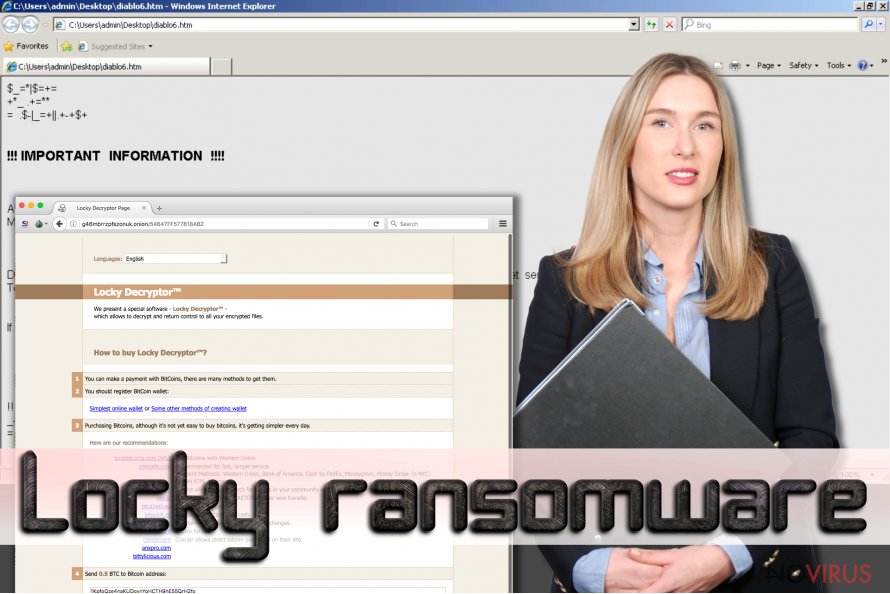
- The user has to buy virtual BitCoin money (the sum ranging from 0,5-1 Bitcoin ($142-$286), as the remittance will not otherwise be accepted.
- The ransom should be transferred to the ransomware developers only using an anonymous Tor network, through the specifically indicated websites.
- After the cyber criminals receive the payment, they send the personalized encryption key to the infected computer’s user, and the files can be decrypted.
Nevertheless, it is all just a theory. The criminals may not necessarily grant the encryption key and even if they do, this tool may be simply nonfunctional or contain some additional malware attached to it. This way, you may not even lose your files, but also suffer financial losses as well as have your computer’s system ruined completely. Needless to say that immediate Locky ransomware removal is obligatory to avoid such unpleasant consequences.
How does Locky ransomware infiltrate computers?
As already pointed out in the opening paragraph, Locky ransomware, identically to its predecessor, the Locky virus, spreads through the infected email attachments. Such spam emails contain messages like presented here:
Dear [Name],
Please see the attached invoice (Microsoft Word Document) and remit payment according to the terms listed at the bottom of the invoice.
Let us know if you have any questions.
We greatly appreciate your business!
[Randomly generated name of the sender]
Such deceptive emails push the users to download a J-[8 random numbers].doc attachment file which is, in fact, a carrier of the Locky ransomware virus. If the user has a Macros function enabled on its Word upon the opening of this file, the virus is activated instantaneously, and the malicious encryption process begins.
Otherwise, the user will see an encrypted, unreadable text with a short 'Enable macro if the data encoding is incorrect' message added to the top of the document. By no means should you follow such instructions! The Word Macros will only activate the virus code, and your files will be put at risk of being infected.
However, if you accidentally opened such a document and activated the virus, you should disconnect your computer from the network as quick as possible and run a scan of your system with a sophisticated antivirus tool.
Methods you can try to recover encrypted data:
Many users address us with questions about the file recovery after the Locky attack. After a detailed Locky ransomware analysis, we have found that some of the files may be recovered with data recovery tools such as Kaspersky virus-fighting utilities, R-Studio or Photorec.
Also, you can wait till the Locky ransomware decrypt tool is invented, yet this may take a while. Nevertheless, the best way to protect your data is by creating a backup of your files and storing it on some external drive, USB, external hard drive or similar platforms, so you can be sure that your files are safe, and can be easily recovered in case of emergency.
Either way, you choose to recover your files, you should make sure that the virus is completely eliminated from your computer before doing that. Otherwise, you may have your files locked again. So, in other words, it is better to spare some and resources into the protection of your machine before the ransomware actually hits your computer.
Ransomware virus prevention:
There are several way to protect your computer from the Locky ransomware attack. First, you have to make sure that your antivirus is updated to its latest version. Regularly update your anti-malware and antivirus suites to ensure the best protection.
Do not forget the built-in system protection such as Windows Firewall and check if it is turned on. Also, stay away from the ‘Spam’ and ‘Junk’ catalogues in your email, since most of the malicious emails end up there. However, you have to be aware that the creators of the malicious programs may find a way to sneak into your regular inbox as well.
In such case, refrain from opening emails received from suspicious senders, especially the ones pushing you to download email attachments. These steps should help you keep the Locky ransomware virus at bay. However, if you are already infected with this virus, check the following page for its removal recommendations.
Locky ransomware virus removal recommendations:
Unfortunately, simply removing Locky ransomware from your computer will not help you to recover the locked files. You may have to use the already mentioned data recovery tools for that. But first, you have to take care of the thorough Locky ransomware removal. FortectIntego or Malwarebytes programs may be helpful for this purpose.
Be aware, however, that Locky ransomware is a very aggressive virus, which may try blocking your antivirus from initiating. If you are encountering similar difficulties, you can use the removal instructions provided at the end of this article. After you remove the virus manually, do not forget to scan your computer with the antivirus tool once more to detect and remove all potential residue junk files.
Getting rid of Locky virus. Follow these steps
In-depth guide for the Locky elimination
Important! →
The elimination guide can appear too difficult if you are not tech-savvy. It requires some knowledge of computer processes since it includes system changes that need to be performed correctly. You need to take steps carefully and follow the guide avoiding any issues created due to improper setting changes. Automatic methods might suit you better if you find the guide too difficult.
Step 1. Launch Safe Mode with Networking
Safe Mode environment offers better results of manual virus removal
Windows 7 / Vista / XP
- Go to Start.
- Choose Shutdown, then Restart, and OK.
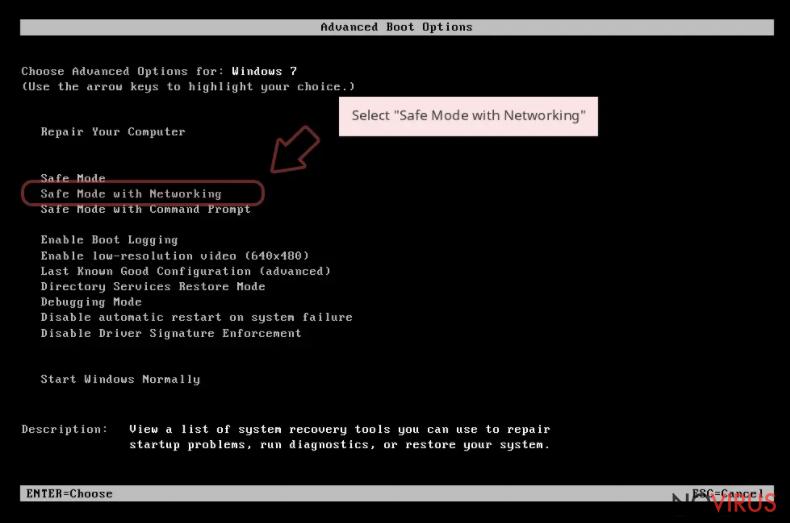
- When your computer boots, start pressing the F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) a few times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.
Windows 10 / Windows 8
- Right-click the Start button and choose Settings.
- Scroll down to find Update & Security.
- On the left, pick Recovery.
- Scroll to find Advanced Startup section.
- Click Restart now.
- Choose Troubleshoot.
- Go to Advanced options.
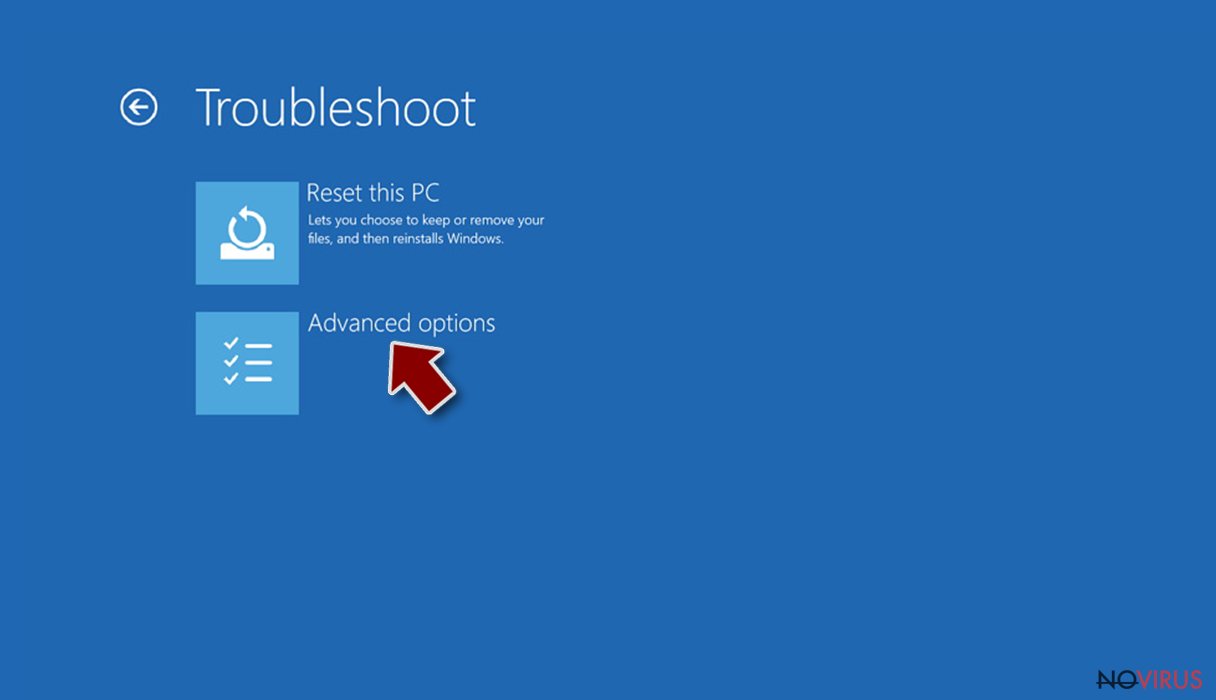
- Select Startup Settings.
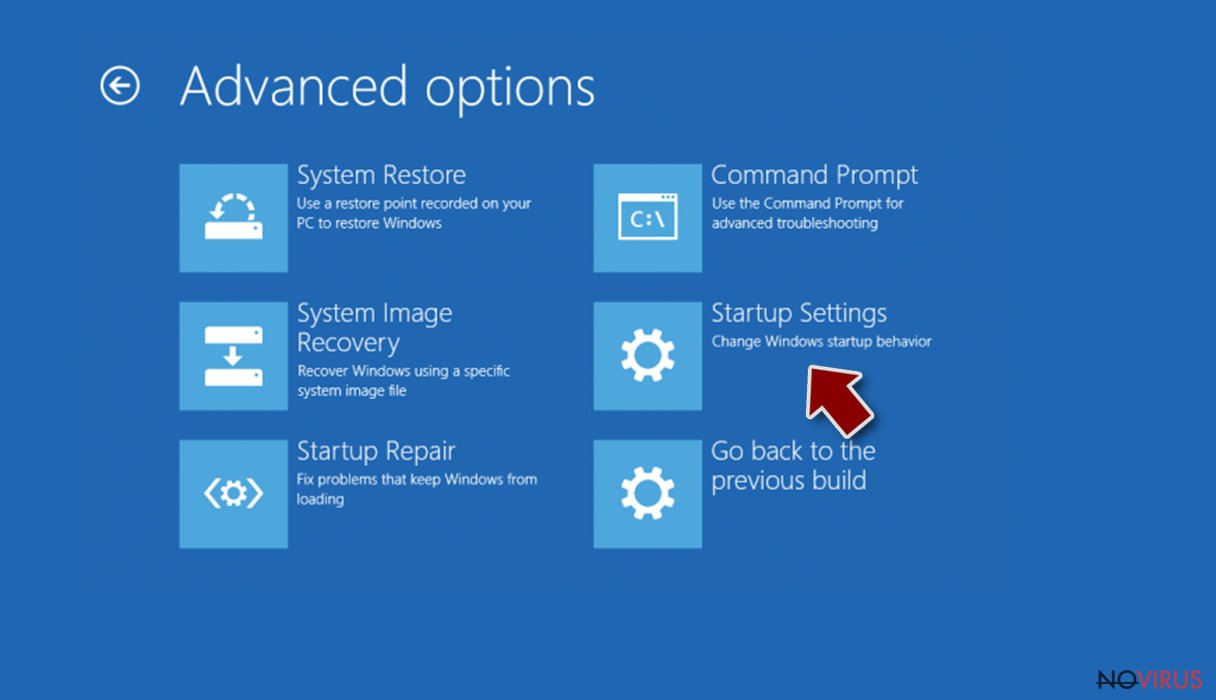
- Press Restart.
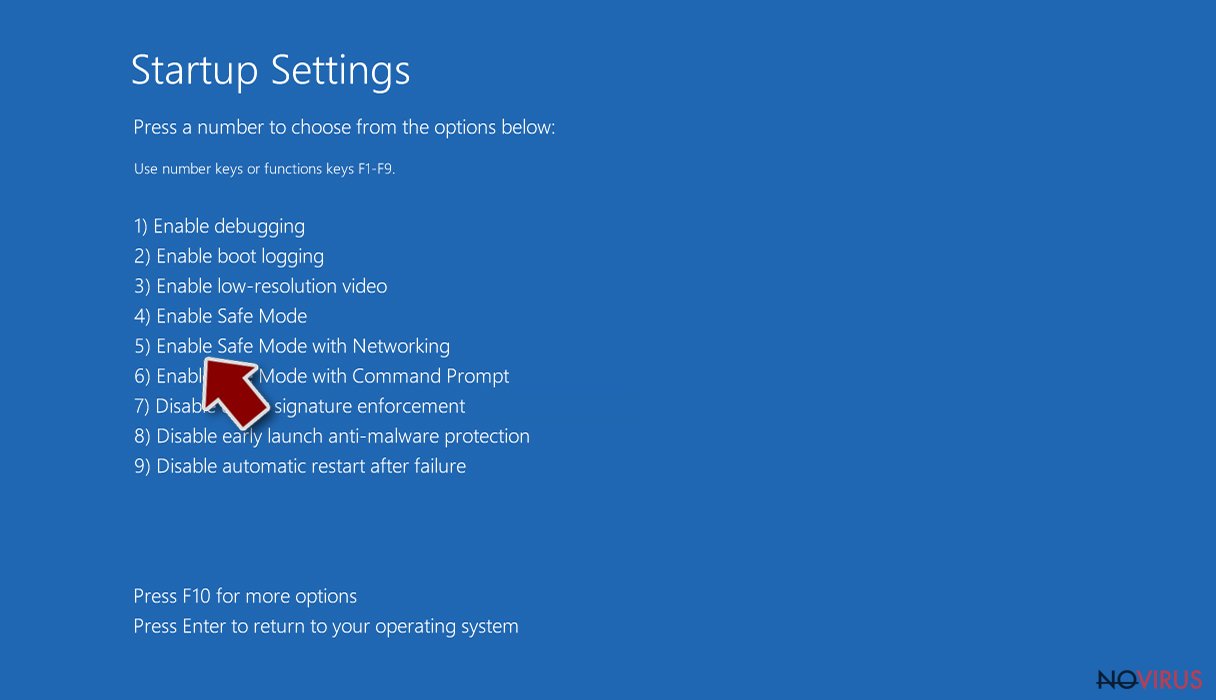
- Choose 5) Enable Safe Mode with Networking.
Step 2. End questionable processes
You can rely on Windows Task Manager that finds all the random processes in the background. When the intruder is triggering any processes, you can shut them down:
- Press Ctrl + Shift + Esc keys to open Windows Task Manager.
- Click on More details.
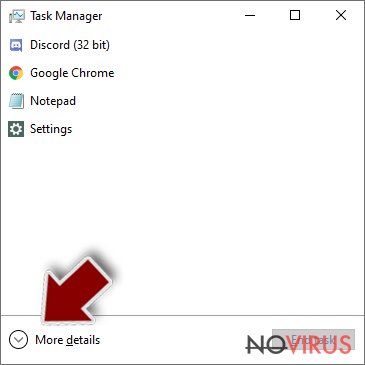
- Scroll down to Background processes.
- Look for anything suspicious.
- Right-click and select Open file location.
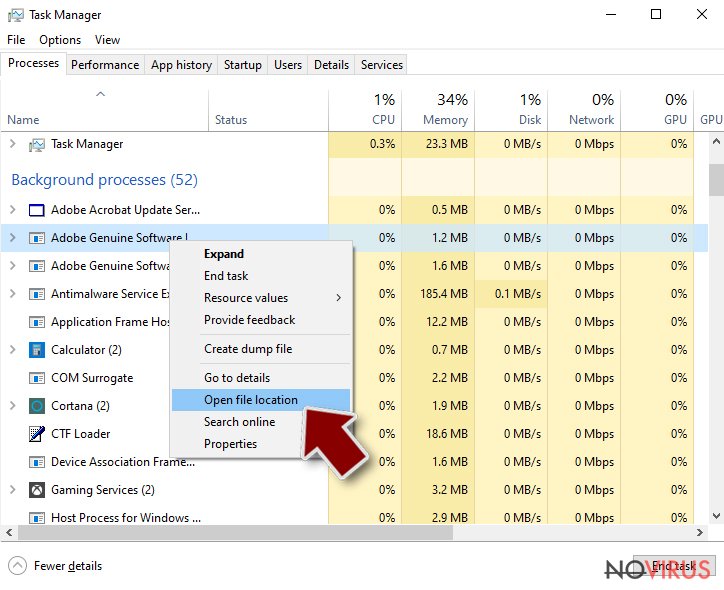
- Go back to the Process tab, right-click and pick End Task.
- Delete the contents of the malicious folder.
Step 3. Check the program in Startup
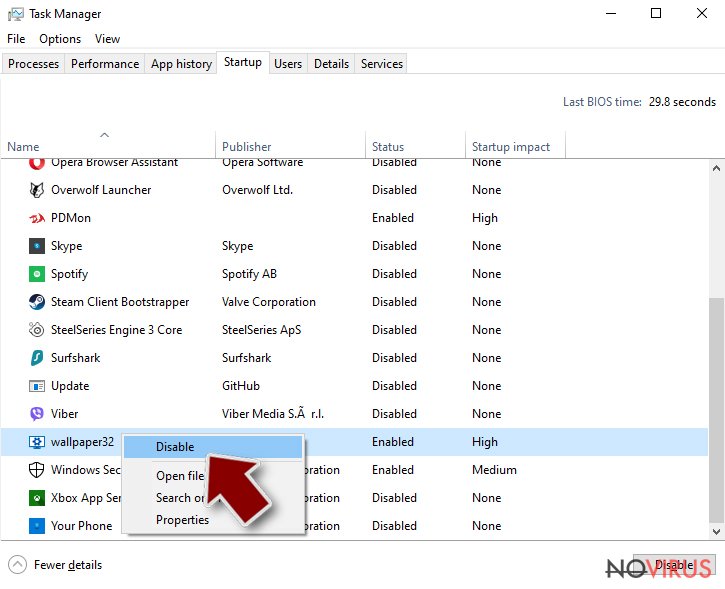
- Press Ctrl + Shift + Esc on your keyboard again.
- Go to the Startup tab.
- Right-click on the suspicious app and pick Disable.
Step 4. Find and eliminate virus files
Data related to the infection can be hidden in various places. Follow the steps and you can find them:
- Type in Disk Cleanup in Windows search and press Enter.
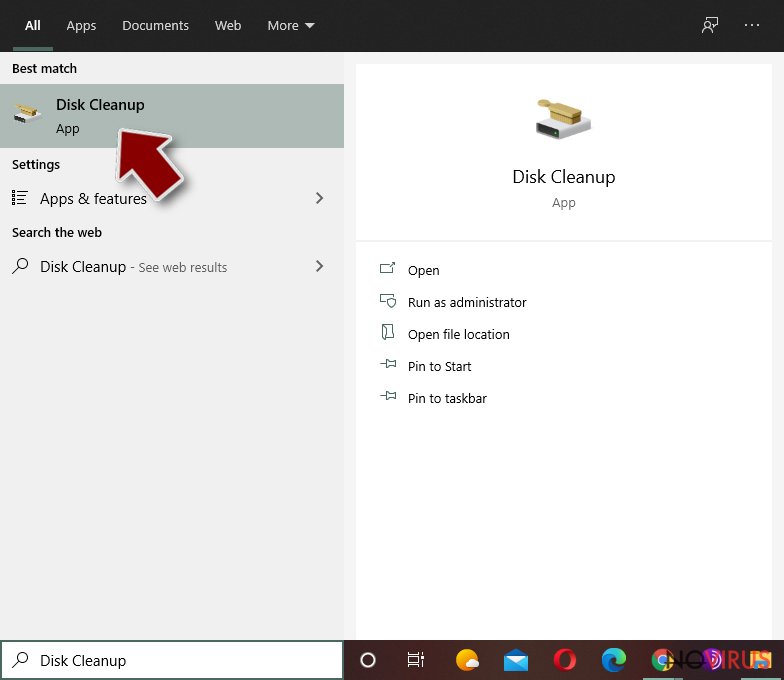
- Select the drive (C: is your main drive by default and is likely to be the one that has malicious files in) you want to clean.
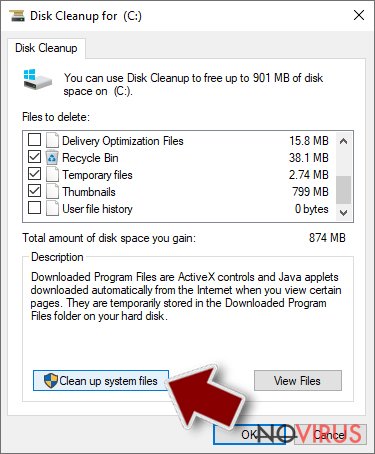
- Scroll through the Files to delete and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.
- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Eliminate Locky using System Restore
-
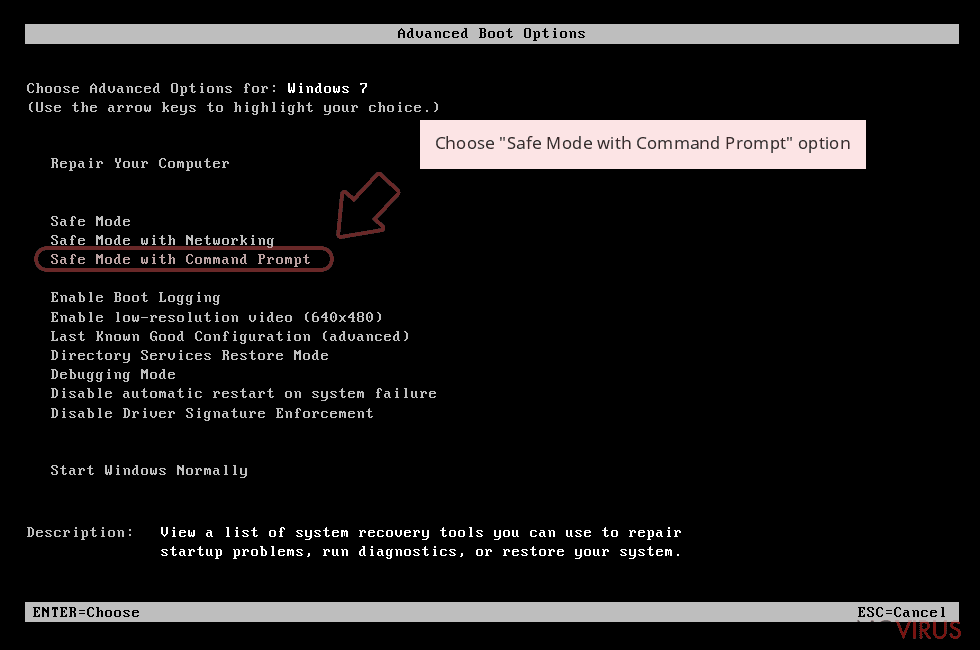
Step 1: Restart your computer in Safe Mode with Command Prompt
Windows 7 / Vista / XP- Go to Start → Shutdown → Restart → OK.
- As soon as your computer starts, start pressing F8 key repeatedly before the Windows logo shows up.
-
Choose Command Prompt from the list

Windows 10 / Windows 8- Click on the Power button at the Windows login screen, and then press and hold Shift key on your keyboard. Then click Restart.
- Then select Troubleshoot → Advanced options → Startup Settings and click Restart.
-
Once your computer starts, select Enable Safe Mode with Command Prompt from the list of options in Startup Settings.

-
Step 2: Perform a system restore to recover files and settings
-
When the Command Prompt window appears, type in cd restore and press Enter.

-
Then type rstrui.exe and hit Enter..

-
In a new window that shows up, click the Next button and choose a restore point that was created before the infiltration of Locky and then click on the Next button again.


-
To start system restore, click Yes.

-
When the Command Prompt window appears, type in cd restore and press Enter.
It is strongly recommended to take precautions and secure your computer from malware attacks. To protect your PC from Locky and other dangerous viruses, you should install and keep a powerful malware removal tool, for instance, FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes.
How to prevent from getting ransomware
A proper web browser and VPN tool can guarantee better safety
As online spying becomes an increasing problem, people are becoming more interested in how to protect their privacy. One way to increase your online security is to choose the most secure and private web browser. But if you want complete anonymity and security when surfing the web, you need Private Internet Access VPN service. This tool successfully reroutes traffic across different servers, so your IP address and location remain protected. It is also important that this tool is based on a strict no-log policy, so no data is collected and cannot be leaked or made available to first or third parties. If you want to feel safe on the internet, a combination of a secure web browser and a Private Internet Access VPN will help you.
Recover files damaged by a dangerous malware attack
Despite the fact that there are various circumstances that can cause data to be lost on a system, including accidental deletion, the most common reason people lose photos, documents, videos, and other important data is the infection of malware.
Some malicious programs can delete files and prevent the software from running smoothly. However, there is a greater threat from the dangerous viruses that can encrypt documents, system files, and images. Ransomware-type viruses focus on encrypting data and restricting users’ access to files, so you can permanently lose personal data when you download such a virus to your computer.
The ability to unlock encrypted files is very limited, but some programs have a data recovery feature. In some cases, the Data Recovery Pro program can help recover at least some of the data that has been locked by a virus or other cyber infection.