Uninstall Kvag virus (Uninstall Guide) - Sep 2019 updated
Kvag virus Removal Guide
Description of Kvag virus
Kvag ransomware – a form of malware that might use the TCP port 3389 for unexpected distribution
Kvag ransomware is a malicious threat that can hack RDPs for placing itself on the targeted system. What happens next definitely is not a satisfying experience to have. Unfortunately, this malware belongs to the well-known Djvu threat family and is also rooted in the STOP ransomware category. Kvag virus seems to expand the family line by attacking random victims and locking their files with the .kvag appendix. After that, the _readme.txt message is yet to come and be inserted in every folder that holds encrypted documents and on the desktop also. If you have already read about Djvu-related malware, you might notice that ransom demand are always the same – $490 which is a 50% discount or $980 if victims do not contact the criminals in time (between three days).
If you decide to pay the criminals who are responsible for pushing Kvag ransomware on your system, do not be surprised to receive anything at all, except for useless money loss. Scamming is often the major task of malware developers as they seek to gather as much income as possible by distributing their created threats. Be aware that the hackers provide the gorentos2@firemail.cc, gorentos@bitmessage.ch email addresses, and the @datarestore Telegram for contact.
| Name | Kvag |
|---|---|
| Type | Ransomware |
| Family | This notorious threat belongs to the Djvu and STOP malware families |
| Extension | Once files are locked by using unique encryption algorithms, they appear with the .kvag extension added next to the name |
| Ransom note | Once data is encrypted, the ransomware virus places the _readme.txt message on the desktop and in every folder that holds blocked files |
| Ransom price | Hackers urge for a payment of $490 as a 50% discount from $980 if contact is made within the three day time period |
| Criminals' contacts | You can find gorentos2@firemail.cc, gorentos@bitmessage.ch email addresses, and the @datarestore Telegram included in the ransom message |
| Distribution | It is known that Kvag virus might be capable of spreading via the TCP port 3389, software and computer vulnerabilities, fake messages that claim about shipment information |
| Additional features | The malware is capable of modifying the Windows hosts file, deleting Shadow Volume Copies, and might also carry the AZORult Trojan virus |
| Detection | If you are looking for a tool that will help you to locate all malicious entries on your computer, try downloading and installing FortectIntego |
Kvag ransomware is a nasty cyber threat to deal with because it carries many different activation modules inside its core. Besides just encrypting data and placing ransom demands to your case, the malware modifies directories such as the Windows Registry and Task Manager and leaves these sections filled with malicious components.
Usually, various bogus entries and keys allow Kvag ransomware to overrun antimalware detection and boot itself automatically every time when the infected machine is turned on by the user. This way the ransom-demanding threat ensures that its activities remain successful and bring benefits all the time.
In addition, Kvag ransomware modifies that hosts file and disables the users from visiting security-related websites where they might find professional help for defeating the ransomware virus. However, if you find out that your hosts file has been changed or damaged, you should delete it from this directory on your Windows computer: C:\Windows\System32\drivers\etc.
Nevertheless, the Shadow Volume Copies of your encrypted data also remain unsafe while Kvag ransomware is residing on your machine. The cyber threat makes sure that these components are eliminated and you are not able to recover your documents and files without purchasing the decryptor from the crooks themselves. Hackers state in the ransom note that data can be reversed only with their tool:
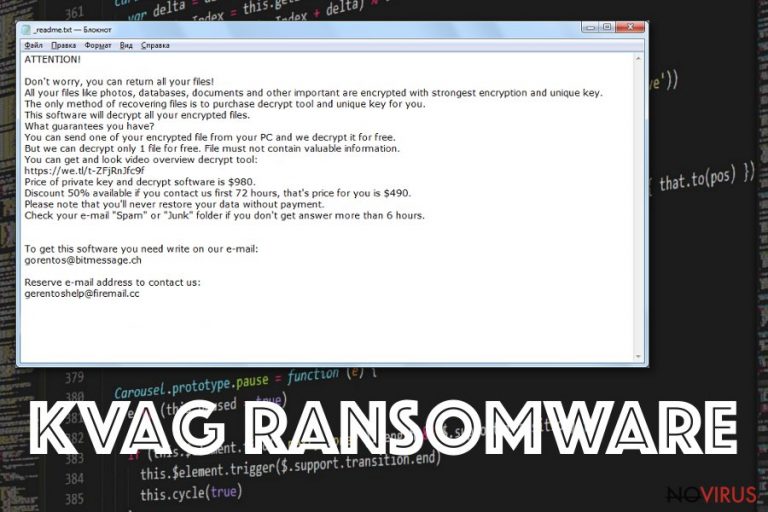
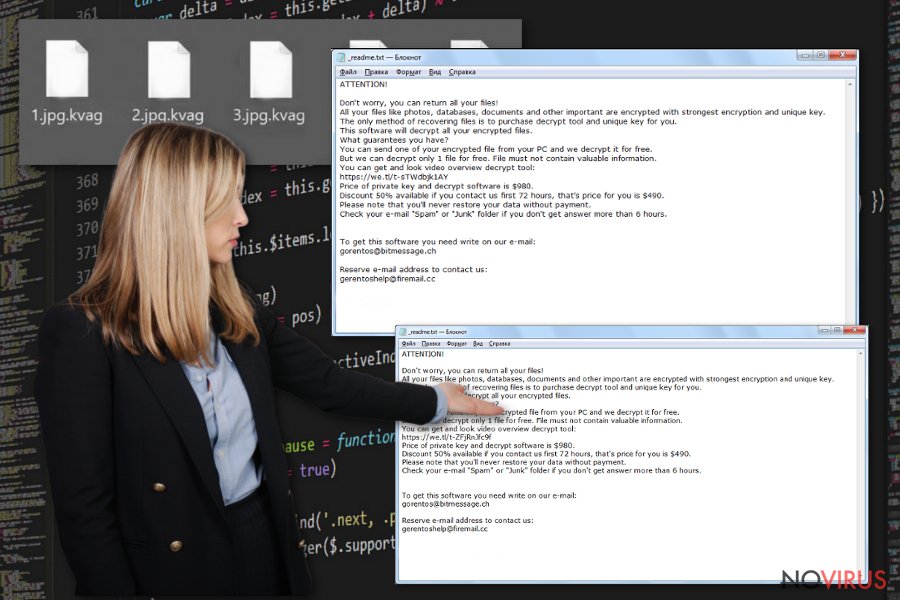
ATTENTION!
Don’t worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:https://we.tl/t-514KtsAKtH
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.
To get this software you need write on our e- mail:
gorentos@bitmessage.chReserve e-mail address to contact us:
gorentos2@firemail.cc
Our Telegram account:
@datarestoreYour personal ID:
Even though Kvag ransomware remains undecryptable at the moment, there is no need to rush and pay the crooks as they might easily scam you and just steal your money. As an alternative, we recommend trying the Rescue Pack that is offered by DrWeb. The package includes a data recovery option and 2 years of automatical computer protection.
Last but not least, malware strains that come from the STOP ransomware family are capable of carrying banking malware such as the AZORult trojan and Kvag ransomware is not an exception. If you end up with the additional threat on your system, you might suffer from money swindling and personal data theft.
Avoid all these risks by performing the Kvag ransomware removal task. However, note that no manual elimination techniques are acceptable in this case as they are too ineffective and dangerous to perform. Do not take any more risks and get a reliable antivirus program to locate the malware on your computer and remove it without causing more damage.
Besides, if you are looking for a tool that will lengthen the termination process, our offer would be to install a program such as FortectIntego. Afterward, launch this software and wait until it completes a full system scan. After a while, you will be provided with a list of all malicious objects found that will create a better view from where the antimalware needs to remove Kvag ransomware.
The most common distribution ways that are used by ransomware developers
According to various Internet sources, ransomware developers often misuse RDPs for injecting their beloved threats into the targeted machines. One of the most commonly used ports is the TCP port 3389 which is hacked and then the password is pushed in under the victim's own will.
In addition, this is not the only way how particular ransomware strains might end up on your computer system. You might also receive some reputable-looking but fake email messages from various shipping organizations such as FedEx that ask to confirm your order. If you press on the confirmation link, the ransomware will be loaded on your computer.
Besides, the malicious payload can come delivered in attachments such as JavaScript files, ZIP, RAR, Word, Excel, or PowerPoint files. The criminals might think of attaching a fake payment information message. So be aware that not everything that looks reliable is truly worth opening.
Continuously, ransomware-related content can be found on peer-to-peer networks, including The Pirate Bay. Here, software downloading hyperlinks are free and because of that, they come unprotected. By installing products from such networks, you take a risk of receiving malicious programs also.
Avoiding ransomware is necessary. Secure your computer with these steps
Technology experts claim that avoiding ransomware and other malware should be a necessity for every user. First of all, ensure that you have reputable antivirus protection working on your computer system. Make sure that you update your antimalware program once in a while.
Furthermore, always sort out your received email. If you have received a message from some type of a reputable organization but do not remember expecting any news lately, better contact the firm directly and ask about the email message. Also, always check the sender and avoid opening any bogus attachments/links.
Continuously, keep a distance from bogus downloading sources as cracked software might carry malicious programs. Besides, by activating a non-original downloading link, you might launch the ransomware straight to your computer system.
Data recovery possibilities for .kvag files that you should know about
Kvag ransomware is a currently undecryptable malware strain, so you might have some difficulties while trying to recover files and documents that have been touched by this malicious threat. While you are waiting for decryption tool updates, there are some things that you can try.
We have found out that DrWeb offers a specific Rescue Pack for $150. This includes a data restoring tool and 2 years of automatical system protection. The company claims that they allow the users to try recovering some files for free and if the tool works, they can purchase the Rescue Pack. Even if the free program does not work, the victims are not charged with any type of fee.
In addition, we have provided three data recovery options at the end of this article that you can also try. However, make sure that you use the automatical removal instructions before you begin with the file restoring process, otherwise, the cyber threat will just renew the encryption during the next computer boot.
The advanced removal process for Kvag ransomware
Kvag ransomware removal is a process to which you need to put all of your attention. However, first, we recommend scanning the entire system with a reputable program so that it will inform you about all the locations that have been touched by the ransomware virus. You can choose one of these tools: FortectIntego, SpyHunter 5Combo Cleaner, Malwarebytes.
After you remove Kvag ransomware from your Windows computer system, it is about time to think about the safety of your future data. Purchase a portable drive and store copies of important information on the device. Additionally, you can use Dropbox or iCloud services for keeping the copies of valuable files/documents.
Getting rid of Kvag virus. Follow these steps
In-depth guide for the Kvag elimination
Use the Safe Mode with Networking feature to disable all malicious changes that were performed by Kvag ransomware virus:
Important! →
The elimination guide can appear too difficult if you are not tech-savvy. It requires some knowledge of computer processes since it includes system changes that need to be performed correctly. You need to take steps carefully and follow the guide avoiding any issues created due to improper setting changes. Automatic methods might suit you better if you find the guide too difficult.
Step 1. Launch Safe Mode with Networking
Safe Mode environment offers better results of manual virus removal
Windows 7 / Vista / XP
- Go to Start.
- Choose Shutdown, then Restart, and OK.
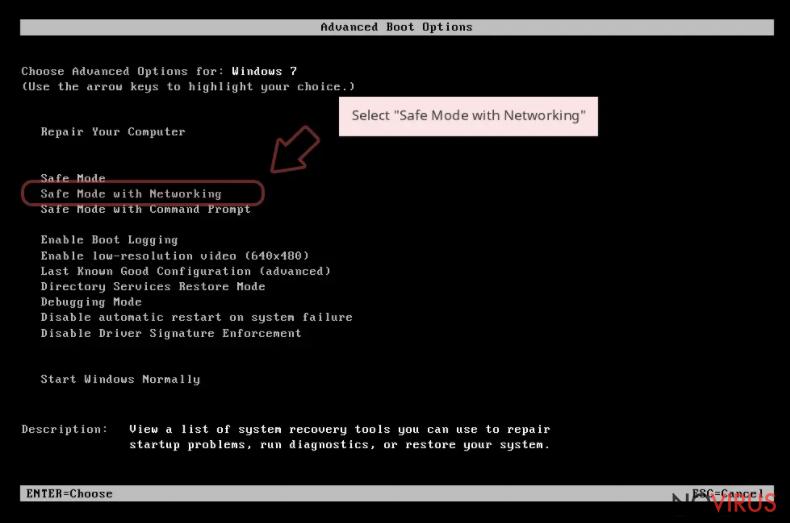
- When your computer boots, start pressing the F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) a few times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.
Windows 10 / Windows 8
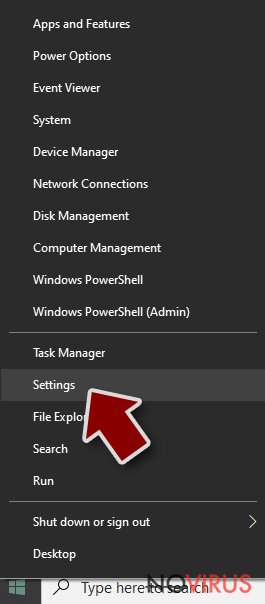
- Right-click the Start button and choose Settings.
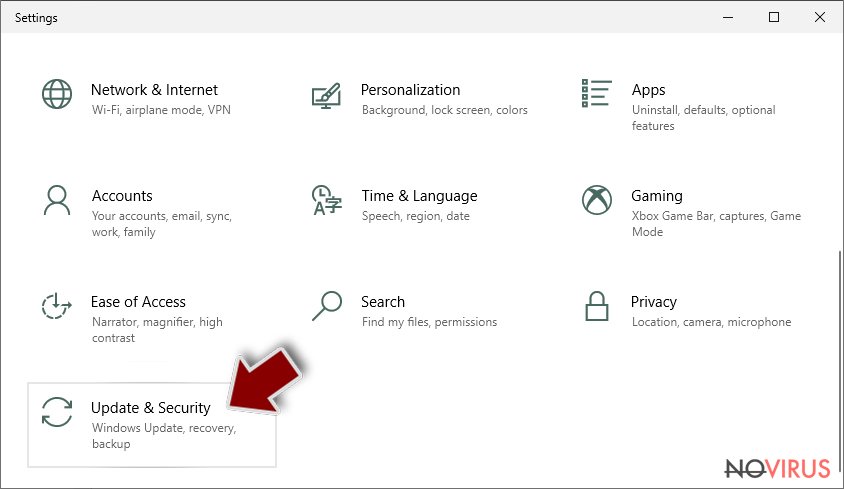
- Scroll down to find Update & Security.
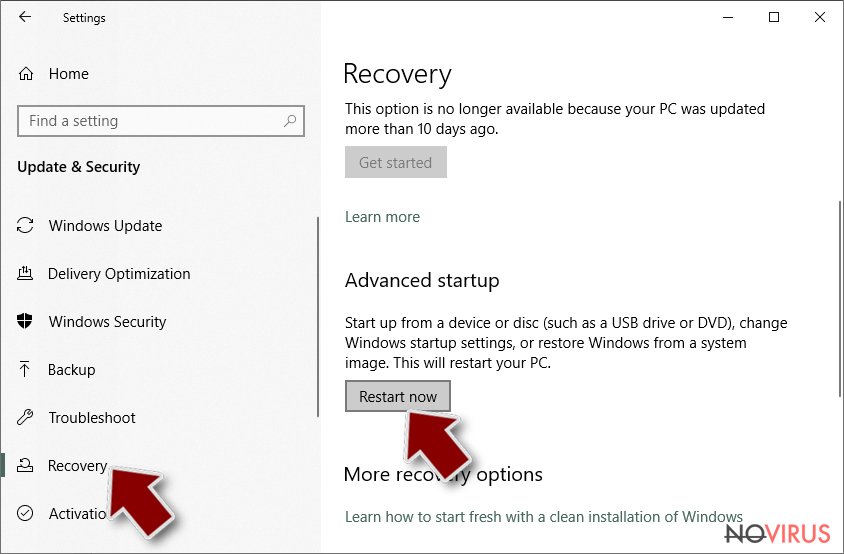
- On the left, pick Recovery.
- Scroll to find Advanced Startup section.
- Click Restart now.
- Choose Troubleshoot.
- Go to Advanced options.
- Select Startup Settings.
- Press Restart.
- Choose 5) Enable Safe Mode with Networking.
Step 2. End questionable processes
You can rely on Windows Task Manager that finds all the random processes in the background. When the intruder is triggering any processes, you can shut them down:
- Press Ctrl + Shift + Esc keys to open Windows Task Manager.
- Click on More details.
- Scroll down to Background processes.
- Look for anything suspicious.
- Right-click and select Open file location.
- Go back to the Process tab, right-click and pick End Task.
- Delete the contents of the malicious folder.
Step 3. Check the program in Startup
- Press Ctrl + Shift + Esc on your keyboard again.
- Go to the Startup tab.
- Right-click on the suspicious app and pick Disable.
Step 4. Find and eliminate virus files
Data related to the infection can be hidden in various places. Follow the steps and you can find them:
- Type in Disk Cleanup in Windows search and press Enter.
- Select the drive (C: is your main drive by default and is likely to be the one that has malicious files in) you want to clean.
- Scroll through the Files to delete and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.
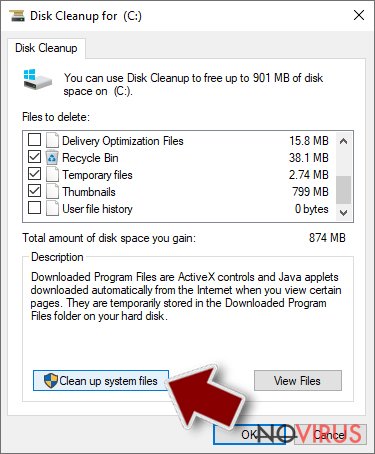
- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Eliminate Kvag using System Restore
Activating System Restore might help you to disable Kvag malware on your Windows computer:
-
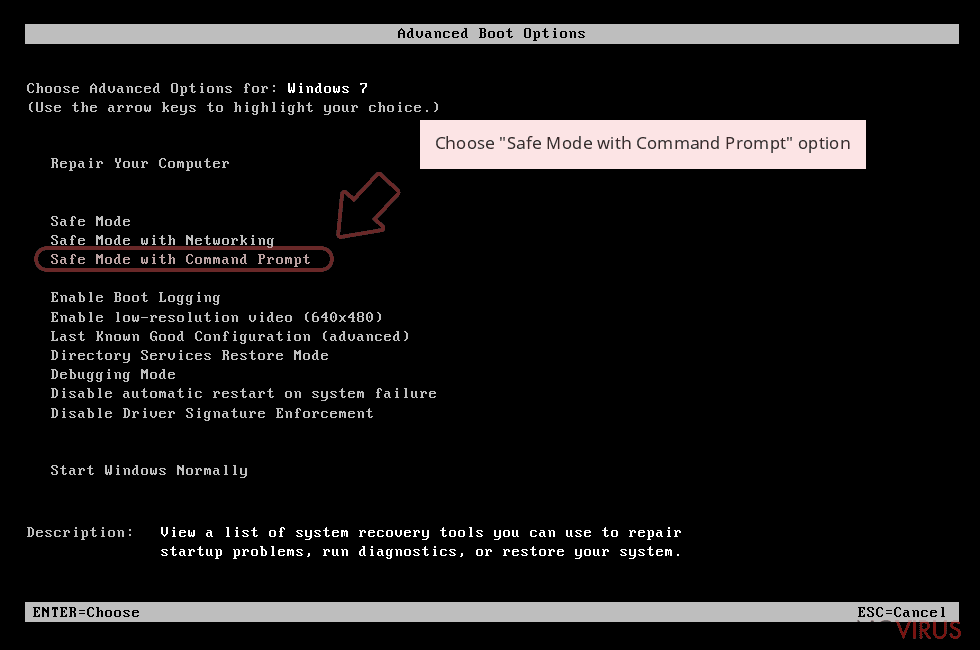
Step 1: Restart your computer in Safe Mode with Command Prompt
Windows 7 / Vista / XP- Go to Start → Shutdown → Restart → OK.
- As soon as your computer starts, start pressing F8 key repeatedly before the Windows logo shows up.
-
Choose Command Prompt from the list

Windows 10 / Windows 8- Click on the Power button at the Windows login screen, and then press and hold Shift key on your keyboard. Then click Restart.
- Then select Troubleshoot → Advanced options → Startup Settings and click Restart.
-
Once your computer starts, select Enable Safe Mode with Command Prompt from the list of options in Startup Settings.

-
Step 2: Perform a system restore to recover files and settings
-
When the Command Prompt window appears, type in cd restore and press Enter.

-
Then type rstrui.exe and hit Enter..

-
In a new window that shows up, click the Next button and choose a restore point that was created before the infiltration of Kvag and then click on the Next button again.


-
To start system restore, click Yes.

-
When the Command Prompt window appears, type in cd restore and press Enter.
Bonus: Restore your files
Using the tutorial provided above you should be able to eliminate Kvag from the infected device. novirus.uk team has also prepared an in-depth data recovery guide which you will also find above.There are a couple of methods you can apply to recover data encrypted by Kvag:
Data Recovery Pro can help you to recover some encrypted components:
Use this piece of software for restoring files that have been touched by Kvag virus.
- Download Data Recovery Pro;
- Install Data Recovery on your computer following the steps indicated in the software’s Setup;
- Run the program to scan your device for the data encrypted by Kvag ransomware;
- Recover the data.
Using Windows Previous might allow you to bring some locked files back:
If you have enabled the System Restore option in the past, you can try using this data recovery method for bringing some of your data back to its previous state.
- Right-click on the encrypted document you want to recover;
- Click “Properties” and navigate to “Previous versions” tab;
- In the “Folder versions” section look for the available file copies. Choose the desired version and press “Restore”.
Try to recover your data with Shadow Explorer:
This method might work only if the ransomware virus did not affect the Shadow Volume Copies of your encrypted files. So, check them first.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Install Shadow Explorer on your computer following the instructions in the software’s Setup Wizard;
- Run the program. Navigate to the menu on the top-left corner and select a disk containing your encrypted files. Look through the available folders;
- When you find the folder you want to recover, right-click it and select “Export”. Also, choose where the recovered data will be stored.
The decryption tool for .kvag files is still in the development mode.
It is strongly recommended to take precautions and secure your computer from malware attacks. To protect your PC from Kvag and other dangerous viruses, you should install and keep a powerful malware removal tool, for instance, FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes.
How to prevent from getting ransomware
Prevent the government from spying on you
As there is a growing debate in government about collecting users' data and spying on citizens, you should take a closer look at this issue and find out what shady ways of gathering information can be used to collect information about you. You need to browse anonymously if you want to avoid any government-initiated spying and tracking of information.
You can enjoy secure internet browsing and minimize the risk of intrusion into your system if you use Private Internet Access VPN program. This VPN application creates a virtual private network and provides access to the required data without any content restrictions.
Control government and other third party access to your data and ensure safe web browsing. Even if you do not engage in illegal activities and trust your ISP, we recommend being careful about your security. You should take extra precautions and start using a VPN program.
Reduce the threat of viruses by backing up your data
Due to their own careless behavior, computer users can suffer various losses caused by cyber infections. Viruses can affect the functionality of the software or directly corrupt data on your system by encrypting it. These problems can disrupt the system and cause you to lose personal data permanently. There is no such threat if you have the latest backups, as you can easily recover lost data and get back to work.
It is recommended to update the backups in parallel each time the system is modified. This way, you will be able to access the latest saved data after an unexpected virus attack or system failure. By having the latest copies of important documents and projects, you will avoid serious inconveniences. File backups are especially useful if malware attacks your system unexpectedly. We recommend using the Data Recovery Pro program to restore the system.