Foop ransomware removal instructions
Foop virus Removal Guide
Description of Foop ransomware
Foop ransomware is malicious software goal of which is to encrypt all personal files on the infected machine
Foop ransomware is malware that uses a sophisticated encryption method RSA to lock pictures, videos, music, documents, and other files on the targeted Windows computers. Being a variant of the notorious STOP/Djvu family, the virus uses a four-letter extension which is appended to each of the modified files; for example, a “picture.jpg” is turned into “picture.jpg.foop” and can no longer be accessed by its owner.
If you were unlucky enough to get infected with Foop virus, you would also notice a text file on your desktop named _readme.txt, which holds a short message from the ransomware developers. They claim that, due to the “strongest encryption,” users will not be able to access their files, as they need a unique key. However, this Foop ransomware decryptor is not free, as crooks ask to pay $490 (after 72 hours, the price doubles) in Bitcoin. If these requirements are fulfilled, victims are suggested to contact the attackers via helpmanager@firemail.cc or helpmanager@iran.ir emails.
| Name | Foop ransomware |
| Type | Cryptomalware, file locking virus |
| Distribution | Most of the users infect their machines with this ransomware after downloading an executable that pretends to be a software crack or pirated program installer. These are typically hosted on torrent or similar sites |
| First spotted | March 8, 2020 |
| File extension | Each of the encrypted files receives a .foop extension |
| Malware family | STOP/Djvu ransomware – it has been active since at least December 2017 |
| Ransom note | A small text file _readme.txt can be found in all the folders where locked data is located, as well as the desktop |
| Ransom demand | Initially, crooks ask for $490 ransom, which doubles to $980 in 72 hours after the infection |
| Contact | helpmanager@firemail.cc or helpmanager@iran.ir |
| Malware removal | The only way to get rid of the infection is by scanning the computer with reputable anti-malware software such as SpyHunter 5Combo Cleaner or Malwarebytes (in some cases, you might need to access Safe Mode – see instructions below) |
| File recovery | Foop ransomware uses sophisticated encryption algorithm RSA, so recovering data without backups or paying criminals is difficult. If the virus failed to contact its remote server, however, there is a high chance of successful recovery with Emsisoft's decryptor |
| System fix | Windows system can sustain considerable damage by malware, which may make it lag, crash, or malfunction in other ways. To fix virus damage, we recommend using FortectIntego |
Foop ransomware is the 213th version of the Djvu crypto-locking malware family, so the developers behind it are extremely experienced they began the illegal business as early as December 2017 and up to this day heavily focus on home users. As sad as it can get, this strain is one of the most successful ones, as hundreds of victims get infected each day.
Over time, the malware strain started to become an even bigger concern, prompting more security researchers to invest time into helping the infected. Prior to August 2019, malicious actors used AES cypher for data locking process, while the later versions switched to RSA (Foop file virus belongs to the latter).
This happened because Emsisoft researchers managed to create a decryptor which helped victims to recover data for free. Although all variants released before .coharos one were no longer decryptable. Lucky for some, if the virus used an offline ID to encrypt data, another decryption tool was still able to help. Thus, after you remove Foop ransomware, you should try to use it before proceeding with other recovery methods.
Before we proceed with Foop ransomware removal instructions, let's see how this malware operates.
Foop ransomware distribution methods and ways to prevent the infection
If you are questioning how did you infect your computer with Foop ransomware – it is most likely software cracks or pirated software installers that you downloaded from an insecure website. This attack vector is also one of the reasons why Djvu malware family is so successful – many users rush to torrent, warez, and similar sites to download tools like KMSPico to bypass the licencing process of paid applications.
Unfortunately, many are in complete denial when it comes to cybersecurity – users know that torrent and similar sites are dangerous and often loaded with malware. Even if you do not download the malicious executable yourself, you could be a victim of a drive-by download that is launched by a malicious JavaScript and abuses software vulnerabilities to install malware payload.
Nevertheless, Foop ransomware is typically delivered when users click on .exe, .zip, or another format file. Therefore, it is vital to avoid such practices altogether, as security software cannot determine whether a crack, loader or a keygen is secure – its principle of operation will make the program to mark it as malicious by default (at least in many cases).
Additionally, it is equally as important to protect your system with a sophisticated anti-malware solution that can catch the intrusion in real-time and stop it. Experts also recommend using strong passwords, updating Windows on time, not opening malicious spam email attachments and being overall more aware of online dangers like ransomware.
Infection and file encryption
Once the main executable is triggered, it will begin the infection process of Foop ransomware. Before that, however, the virus will create a new folder in %AppData%, and then place the main file inside – it can be called virtually as anything – malicious actors sometimes choose names like 8d7c.tmp.exe, c72b.tmp.exe, 1111.exe, update.exe, etc.
Before Foop file virus begins the encryption process, it performs the following changes to the host machine:
- Elevates permissions via the SE_LOAD_DRIVER_PRIVILEGE service;
- Modifies Windows registry database to be able to boot with every Windows launch;
- Deletes all Shadow Volume Copies to prevent an easy recovery;
- Adjusts Windows “hosts” file in order to stop users from visiting websites that would help with Foopr ransomware removal and recovery procedures;
- Installs a data stealing module that would harvest all the information typed in via the web browsers
- Imports, deletes and copies various files, etc.
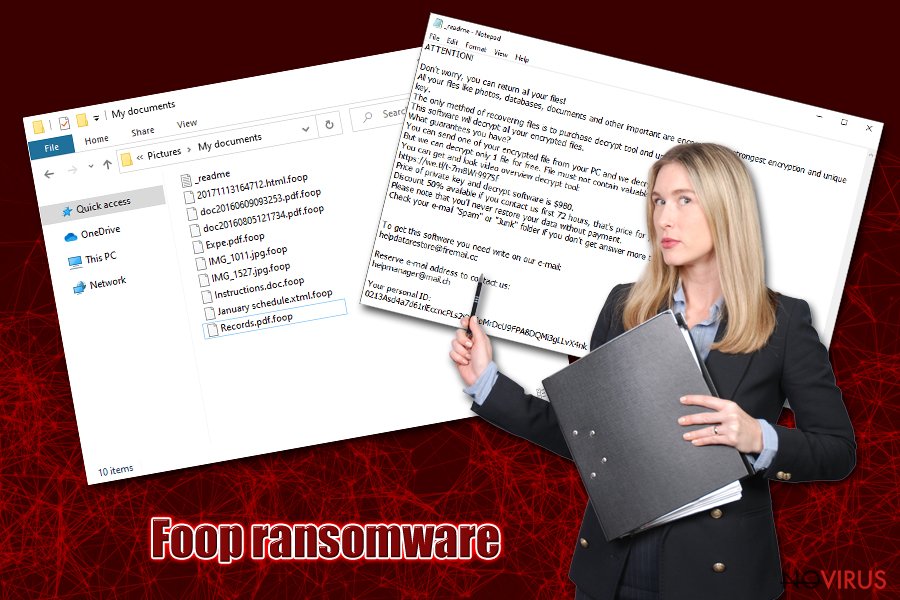
Once the preparations are complete, Foop ransomware will begin to scan the machine for files to encrypt. Typically, malware targets hundreds of various file types, including .pdf, .doc., .zip, .html, .dat, .jpg, .mp4, .ppt, .mdb, and others. During this time, victims will be displayed a fake pop-up window that looks like a Windows update prompt – this feature reduces the chance of users terminating the encryption process before it is complete.
Each of the files is appended with .foop extension – a typical practice of ransomware infection. Note that the virus will skip most of the executables and system files in order to ensure Windows is still operational. Nevertheless, it does not mean that system files do not get affected – various modifications may render the OS partially broken, even after you get rid of Foop ransomware. To remade this, we recommend using FortectIntego.
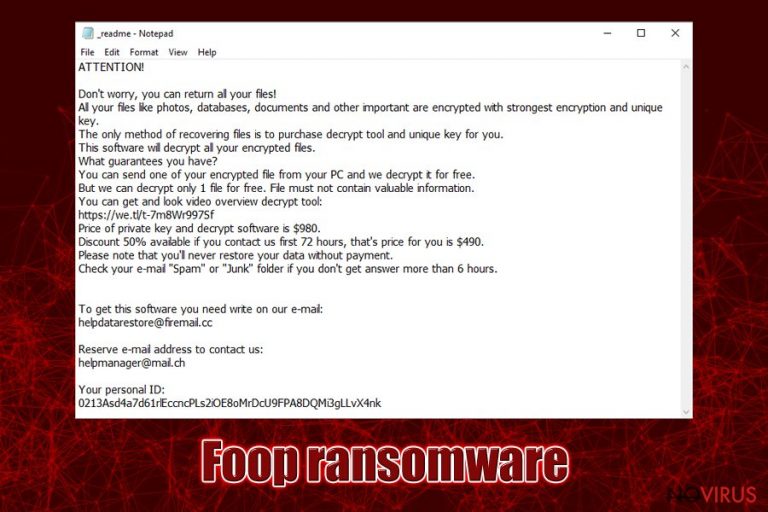
After the data locking process, Foop file virus will drop the _readme.txt file which reads:
ATTENTION!
Don't worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-7m8Wr997Sf
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don't get answer more than 6 hours.To get this software you need write on our e-mail:
helpdatarestore@firemail.ccReserve e-mail address to contact us:
helpmanager@mail.chYour personal ID:
As you can see, malicious actors behind Foop ransomware play friendly people who are willing to help you – this is done purposely in order to make you pay the ransom. However, we advise you not to, as these people cannot be trusted. You might end up scammed and lose not only your files but also the money, so twink twice before considering contacting cybercriminals.
Delete the Foop ransomware infection and attempt to recover your data
After you get infected with the Foop virus and your data is encrypted, reverting the process might not be as easy. Nevertheless, you might be wondering what you should do now? It is not that surprising considering that the vast majority of ransomware victims usually never encountered malware of this type before (they also firmly believe that Foop ransomware removal will also grant access to the encrypted files – these two processes are separate and do not correlate with one another backward).
First of all, you need to check if you have backups of your data – if you do, simply remove Foop ransomware with reputable anti-malware software and then copy it over (remember, this sequence is important, as your recovered files would get encrypted as well otherwise). If no backups were ready, you should first make a copy of the encrypted data and only then terminate the infection. In some cases, you might get lucky, and third-party software might help you, or a free decryption tool for STOP/Djvu might also work for you.
Getting rid of Foop virus. Follow these steps
In-depth guide for the Foop elimination
You can access Safe Mode with Networking if Foop file virus is tampering with your security software:
Important! →
The elimination guide can appear too difficult if you are not tech-savvy. It requires some knowledge of computer processes since it includes system changes that need to be performed correctly. You need to take steps carefully and follow the guide avoiding any issues created due to improper setting changes. Automatic methods might suit you better if you find the guide too difficult.
Step 1. Launch Safe Mode with Networking
Safe Mode environment offers better results of manual virus removal
Windows 7 / Vista / XP
- Go to Start.
- Choose Shutdown, then Restart, and OK.
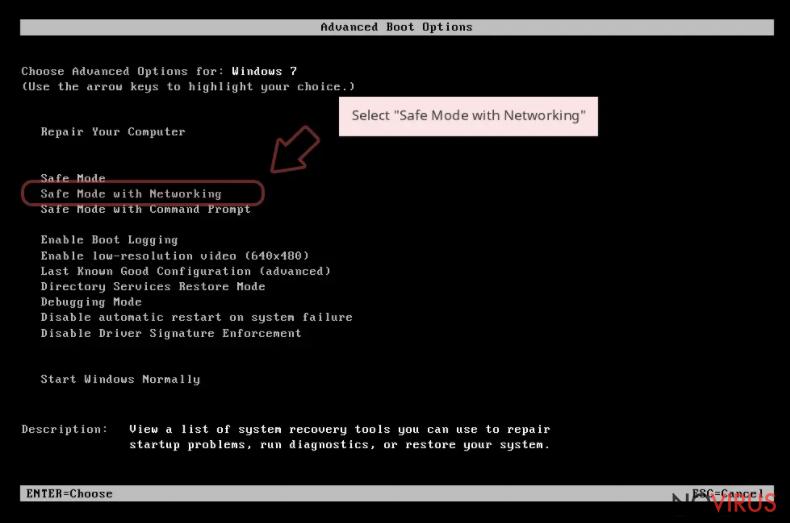
- When your computer boots, start pressing the F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) a few times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.
Windows 10 / Windows 8
- Right-click the Start button and choose Settings.
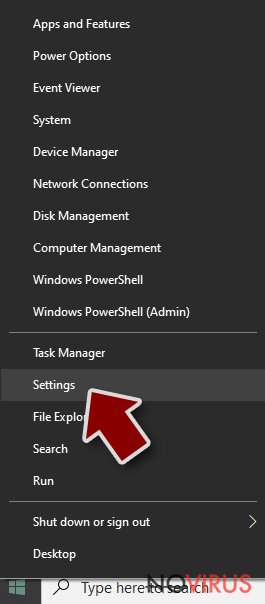
- Scroll down to find Update & Security.
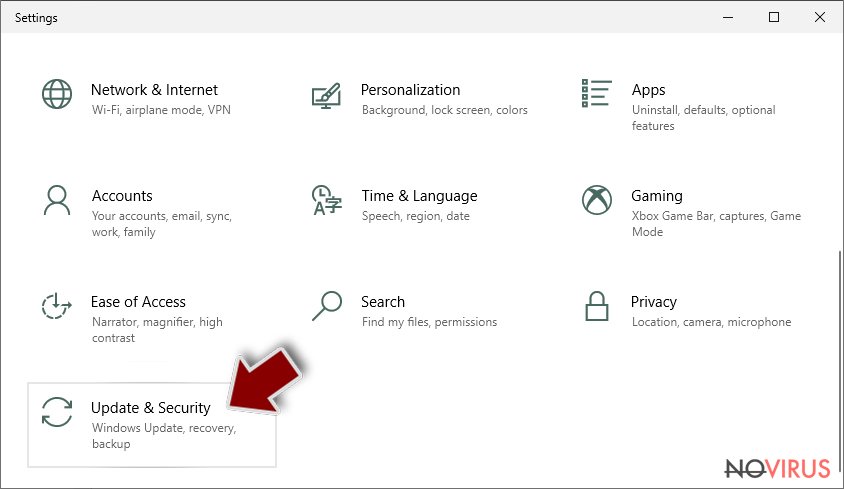
- On the left, pick Recovery.
- Scroll to find Advanced Startup section.
- Click Restart now.
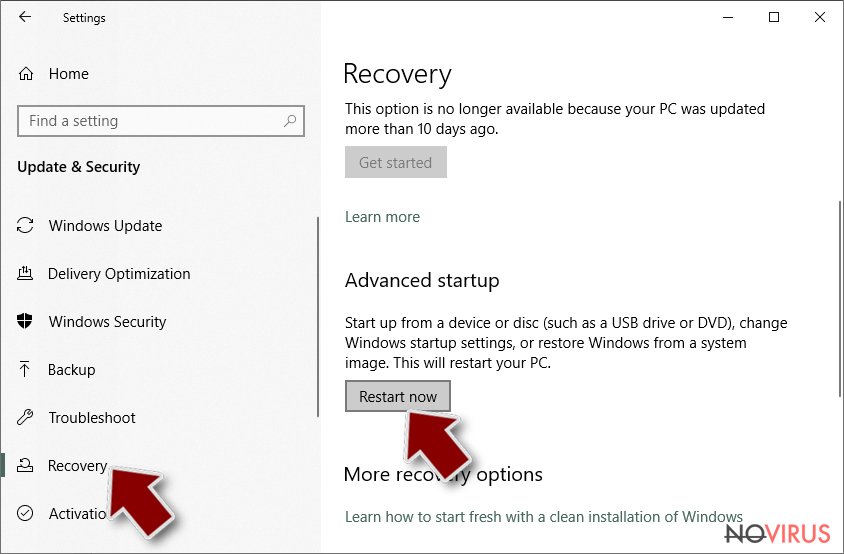
- Choose Troubleshoot.
- Go to Advanced options.
- Select Startup Settings.
- Press Restart.
- Choose 5) Enable Safe Mode with Networking.
Step 2. End questionable processes
You can rely on Windows Task Manager that finds all the random processes in the background. When the intruder is triggering any processes, you can shut them down:
- Press Ctrl + Shift + Esc keys to open Windows Task Manager.
- Click on More details.
- Scroll down to Background processes.
- Look for anything suspicious.
- Right-click and select Open file location.
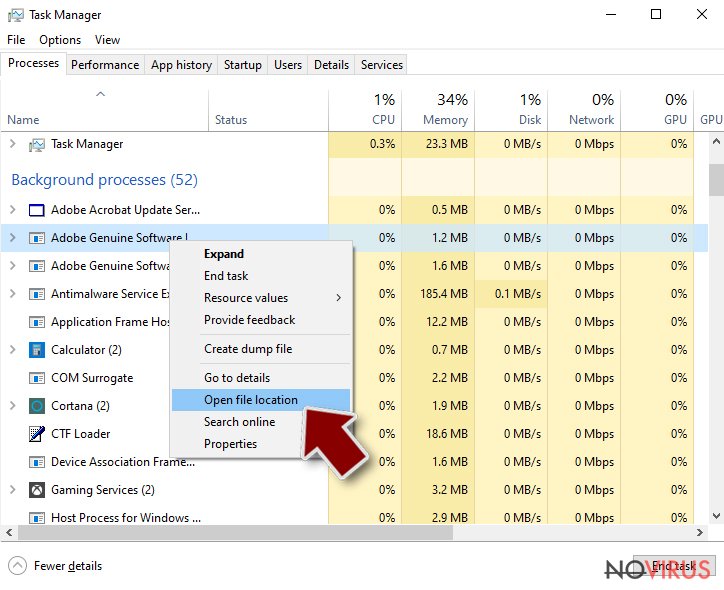
- Go back to the Process tab, right-click and pick End Task.
- Delete the contents of the malicious folder.
Step 3. Check the program in Startup
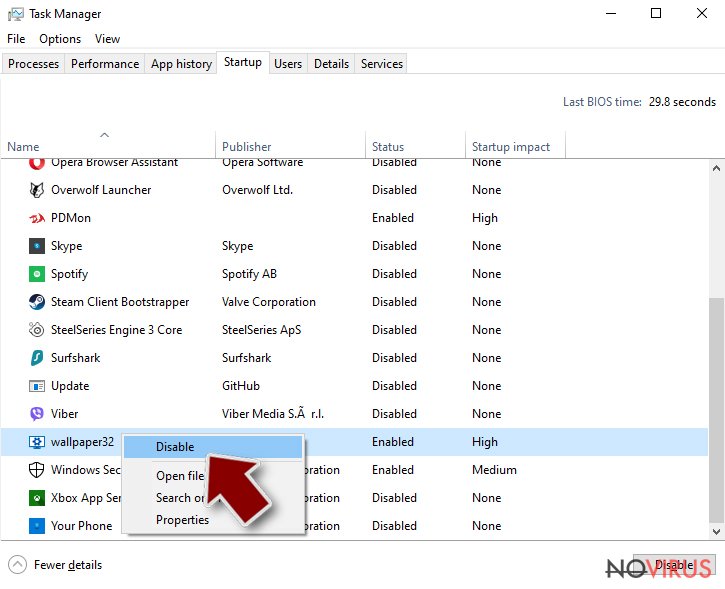
- Press Ctrl + Shift + Esc on your keyboard again.
- Go to the Startup tab.
- Right-click on the suspicious app and pick Disable.
Step 4. Find and eliminate virus files
Data related to the infection can be hidden in various places. Follow the steps and you can find them:
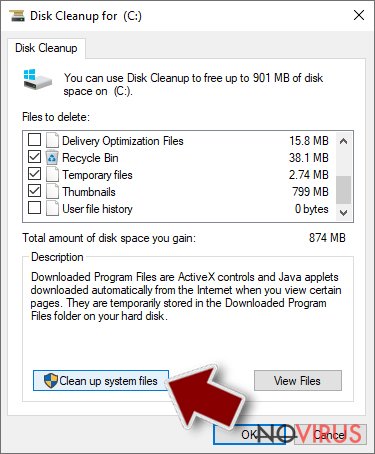
- Type in Disk Cleanup in Windows search and press Enter.
- Select the drive (C: is your main drive by default and is likely to be the one that has malicious files in) you want to clean.
- Scroll through the Files to delete and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.
- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Eliminate Foop using System Restore
-
Step 1: Restart your computer in Safe Mode with Command Prompt
Windows 7 / Vista / XP- Go to Start → Shutdown → Restart → OK.
- As soon as your computer starts, start pressing F8 key repeatedly before the Windows logo shows up.
-
Choose Command Prompt from the list

Windows 10 / Windows 8- Click on the Power button at the Windows login screen, and then press and hold Shift key on your keyboard. Then click Restart.
- Then select Troubleshoot → Advanced options → Startup Settings and click Restart.
-
Once your computer starts, select Enable Safe Mode with Command Prompt from the list of options in Startup Settings.

-
Step 2: Perform a system restore to recover files and settings
-
When the Command Prompt window appears, type in cd restore and press Enter.

-
Then type rstrui.exe and hit Enter..

-
In a new window that shows up, click the Next button and choose a restore point that was created before the infiltration of Foop and then click on the Next button again.


-
To start system restore, click Yes.

-
When the Command Prompt window appears, type in cd restore and press Enter.
Bonus: Restore your files
Using the tutorial provided above you should be able to eliminate Foop from the infected device. novirus.uk team has also prepared an in-depth data recovery guide which you will also find above.There are a couple of methods you can apply to recover data encrypted by Foop:
Data Recovery Pro is a useful recovery tool
This method might sometimes help you recover at least some portion of the locked data, although the more you use your computer after the infection, the fewer chances are that you will be successful.
- Download Data Recovery Pro;
- Install Data Recovery on your computer following the steps indicated in the software’s Setup;
- Run the program to scan your device for the data encrypted by Foop ransomware;
- Recover the data.
Windows Previous Versions feature could be of use
Shadow Volume Copies are functional only if the virus failed to delete Shadow Volume Copies.
- Right-click on the encrypted document you want to recover;
- Click “Properties” and navigate to “Previous versions” tab;
- In the “Folder versions” section look for the available file copies. Choose the desired version and press “Restore”.
ShadowExplorer may be successful in recovering your encrypted files
ShadowExplorer can be used as an alternative for Previous Windows Versions – it may be much easier to recover a large number of files using it.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Install Shadow Explorer on your computer following the instructions in the software’s Setup Wizard;
- Run the program. Navigate to the menu on the top-left corner and select a disk containing your encrypted files. Look through the available folders;
- When you find the folder you want to recover, right-click it and select “Export”. Also, choose where the recovered data will be stored.
Emsisoft's decryption tool works for offline IDs
In case Foop ransomware fails to contact its remote server, it will use an offline ID to lock your data. In such a case, Emsisoft's decryptor should be successful in recovering your files. Additionally, Dr.Web may also help with certain file types (mainly PDF and MS Office files).
It is strongly recommended to take precautions and secure your computer from malware attacks. To protect your PC from Foop and other dangerous viruses, you should install and keep a powerful malware removal tool, for instance, FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes.
How to prevent from getting ransomware
A proper web browser and VPN tool can guarantee better safety
As online spying becomes an increasing problem, people are becoming more interested in how to protect their privacy. One way to increase your online security is to choose the most secure and private web browser. But if you want complete anonymity and security when surfing the web, you need Private Internet Access VPN service. This tool successfully reroutes traffic across different servers, so your IP address and location remain protected. It is also important that this tool is based on a strict no-log policy, so no data is collected and cannot be leaked or made available to first or third parties. If you want to feel safe on the internet, a combination of a secure web browser and a Private Internet Access VPN will help you.
Recover files damaged by a dangerous malware attack
Despite the fact that there are various circumstances that can cause data to be lost on a system, including accidental deletion, the most common reason people lose photos, documents, videos, and other important data is the infection of malware.
Some malicious programs can delete files and prevent the software from running smoothly. However, there is a greater threat from the dangerous viruses that can encrypt documents, system files, and images. Ransomware-type viruses focus on encrypting data and restricting users’ access to files, so you can permanently lose personal data when you download such a virus to your computer.
The ability to unlock encrypted files is very limited, but some programs have a data recovery feature. In some cases, the Data Recovery Pro program can help recover at least some of the data that has been locked by a virus or other cyber infection.