Uninstall Bad Rabbit virus (Oct 2017 updated) - Uninstall Instructions
Bad Rabbit virus Removal Guide
Description of Bad Rabbit ransomware
Bad Rabbit ransomware assaults Eastern Europe
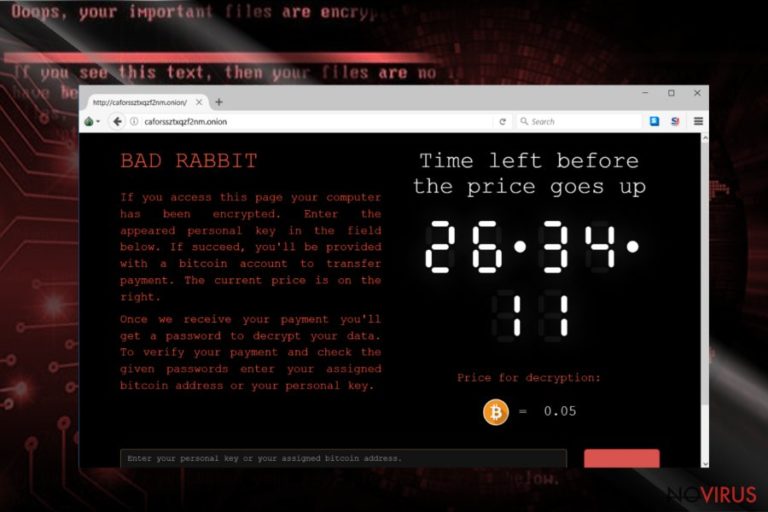
Bad Rabbit virus (also known as Win32/Diskcoder.D) is the name of a complex file-encrypting threat which ceased multiple Russian media, financial institution servers and Ukraine international airport systems on October 24th.
The malware took some ideas from Petya.A/ExPetr virus; it displays the ransom message of the latter virus instead of its own. On the other hand, it has its exceptional .onion payment site, which urges victims to pay 0.05 bitcoins within 42-hour span period.
This peculiarity and the same distribution source led IT experts think the virus might be the latest version of Petya. While some speculate that the author might be the same, the differences in the source code imply the opposite. BadRabbit also refers to WannaCry as it is likely to exploit SMB vulnerabilities.
More information about the flaws would help cybersecurity sources create counter-attack plans. If you have been struck with this cyber misfortune, remove Bad Rabbit. FortectIntego or Malwarebytes will assist you in this process.
Fake Flash player update is the main culprit
So far one distribution vector is known – http://1dnscontrol.com/flash_install.php. The infected servers would direct victims to the latter domain urging them to install BadRabbit malware executable – install_flash_player.exe. Later on, the latter generates three more crucial executing files:
- C:\Windows\infpub.dat
- C:\Windows\cscc.dat
- C:\Windows\dispci.exe
The second file is modified dcrypt.sys file which suggests that the felons used legitimate DiskCryptor service to encrypt files.
Interestingly, the malware directs its daggers to the same countries as Petya or WannaCry – Ukraine and Russia. It ceased Ukraine’s Odessa International Airport system and invaded several media corporations, including Interfax, Fontanka.ru et al., servers. Note that the malware is not limited to these countries. Germany, Turkey, and Bulgaria also reported detecting BadRabbit malware.
The malware exhibits interesting disguise tactics. Besides mentioned fake Flash player updates, the malware also might hide under different dubious installation and removal executables. According to VirusTotal, the malware has been detected as Uninstaller 27.0 file.
Diskcoder.D author – Game of Thrones fan
After necessary executable files are activated, the file-encrypting threat also exhibits peculiar feature. Its commands include names of three dragons from Game of Throne series: Rhaegal, Drogon, and Viserion.
Additionally, the ransomware displays other amusing features. When launched in a virtual machine, it would display the alert to ‘disable anti-virus and anti-malware programs.’
Other features of the malware are not so entertaining. The above mentioned .dat files begin the process of altering Master Boot Record (MBR) settings. As a result, after rebooting the computer, Petya.A ransom notification emerges. Take a look at the below instructions to regain the access to the computer.
Though at the moment the malware was detected only in a comparatively low number of countries, but the overall number of infected systems is alarming. BadRabbit ransomware retrieves technical information about the infected computer which grants the insight about other devises visible on the network.
Since the vulnerabilities allowing the infection to execute are still unknown, it is possible that the malware might soon extend its reach to more countries. On the other, it is fortune that BadRabbit main distribution vector has been discovered. Such knowledge will allow the virtual community to apply certain prevention measures reducing Bad Rabbit hijack possibilities. 
Different prevention measures
If you work in a major company in Ukraine, Russia, Germany or another targeted country, you are likely to encounter the malware. Therefore, remain vigilant before adding a new extension or downloading a new app. Bear in mind that legitimate Flash Player updates are not delivered in random pages.
Furthermore, you should be very careful when installing new applications. The above case of Uninstaller 24.0 suggests that BadRabbit virus might disguise under any app. The case of CCleaner v5.33 revealed that it is not so difficult to foist malware in a legitimate application. Now let us move on to Bad Rabbit removal discussion.
Performing BadRabbit elimination
Before you can remove Bad Rabbit virus completely, you will need to recover access to the device. In order to do that, follow below instructions. After that, restart the system in Safe Mode. Then launch a security application and initiate BadRabbit removal.
At the moment, there is no available free decryption tool. It would be unwise to remit the payment since there is no information whether Diskcoder.D developers send the decryption tool after payment. If you did not back up files, you might find some solutions below the article.
On Windows 7:
- Insert the Windows 7 DVD.
- Launch DVD.
- Select you language and keyboard layout preferences. Click Next.
- Select the operating system, place the checkmark on Use recovery tools and click Next.
- Wait for the System Recovery Options to open and select Command Prompt.
- Type in the following commands and click Enter after each of them: bootrec /rebuildbcd, bootrec /fixmbr,andbootrec /fixboot.
- Eject the installation DVD and reboot the PC.
On Windows 8/10 system:
- Insert the installation DVD disk or recovery USB.
- Choose Repair your computer option.
- SelectTroubleshoot and select Command Prompt.
- Enter the listed commands one by one and press Enter after each: bootrec /FixMbr, bootrec /FixBoot, bootrec /ScanOs, and bootrec /RebuildBcd.
- Eject the DVD or recovery USB.
- Type exit and press Enter.
- Restart the computer.
Getting rid of Bad Rabbit virus. Follow these steps
In-depth guide for the Bad Rabbit elimination
Important! →
The elimination guide can appear too difficult if you are not tech-savvy. It requires some knowledge of computer processes since it includes system changes that need to be performed correctly. You need to take steps carefully and follow the guide avoiding any issues created due to improper setting changes. Automatic methods might suit you better if you find the guide too difficult.
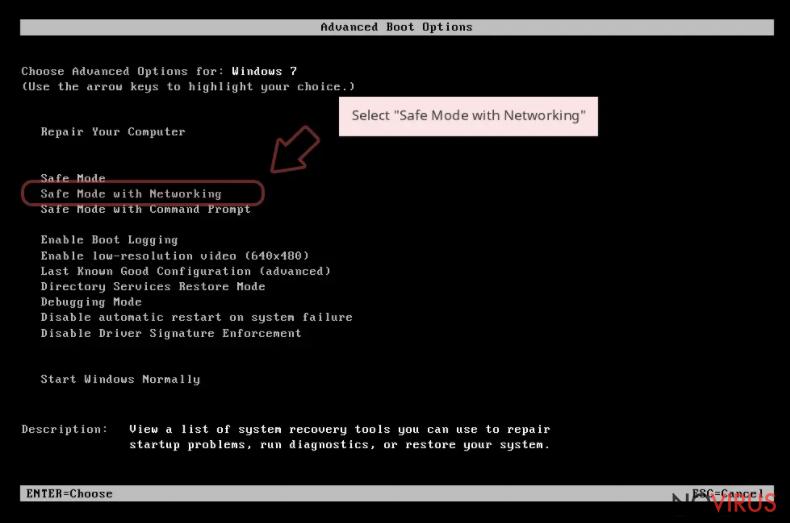
Step 1. Launch Safe Mode with Networking
Safe Mode environment offers better results of manual virus removal
Windows 7 / Vista / XP
- Go to Start.
- Choose Shutdown, then Restart, and OK.
- When your computer boots, start pressing the F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) a few times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.
Windows 10 / Windows 8
- Right-click the Start button and choose Settings.
- Scroll down to find Update & Security.
- On the left, pick Recovery.
- Scroll to find Advanced Startup section.
- Click Restart now.
- Choose Troubleshoot.
- Go to Advanced options.
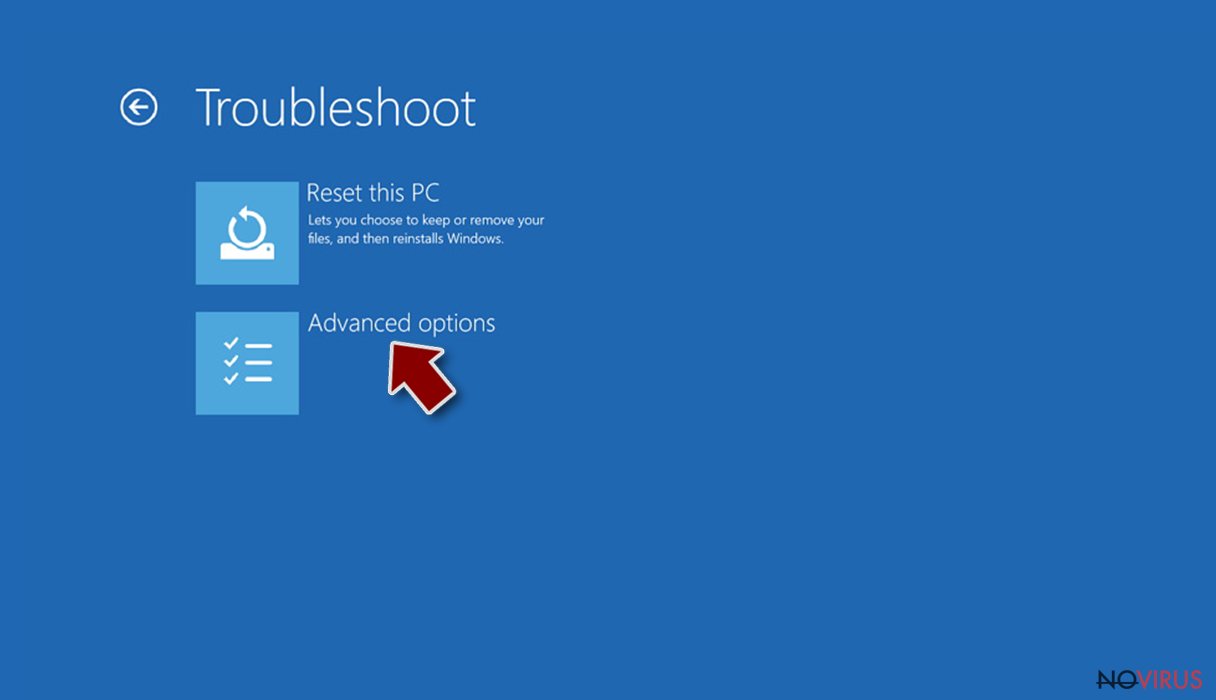
- Select Startup Settings.
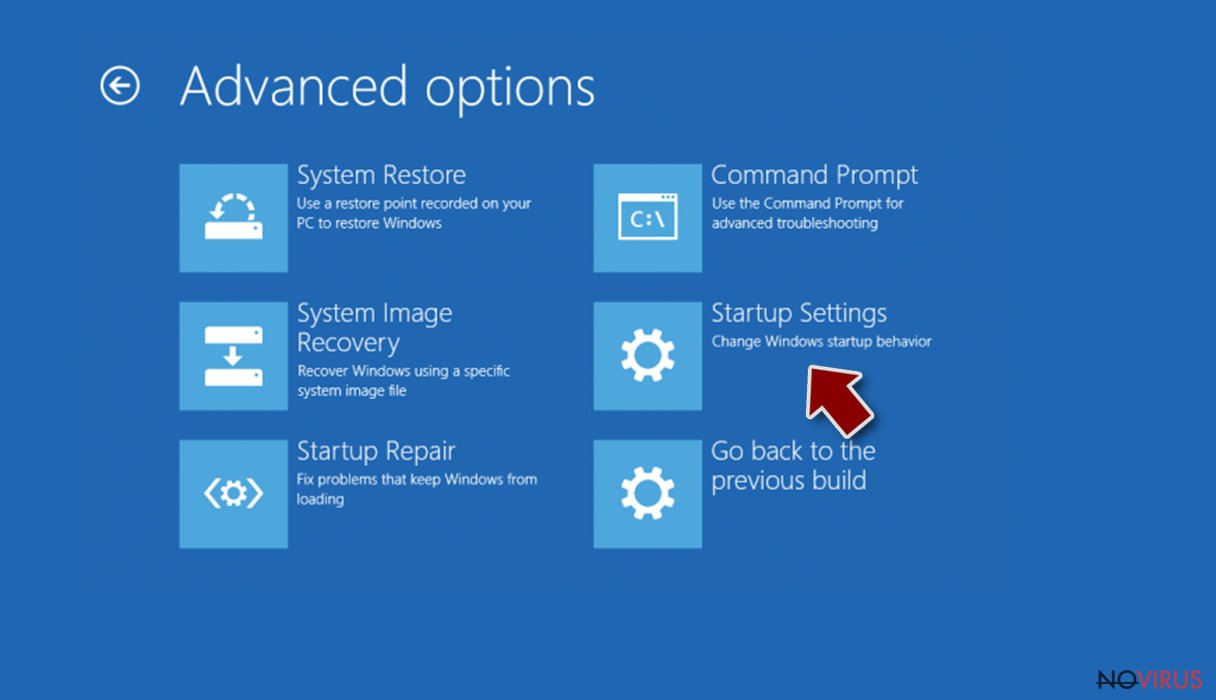
- Press Restart.
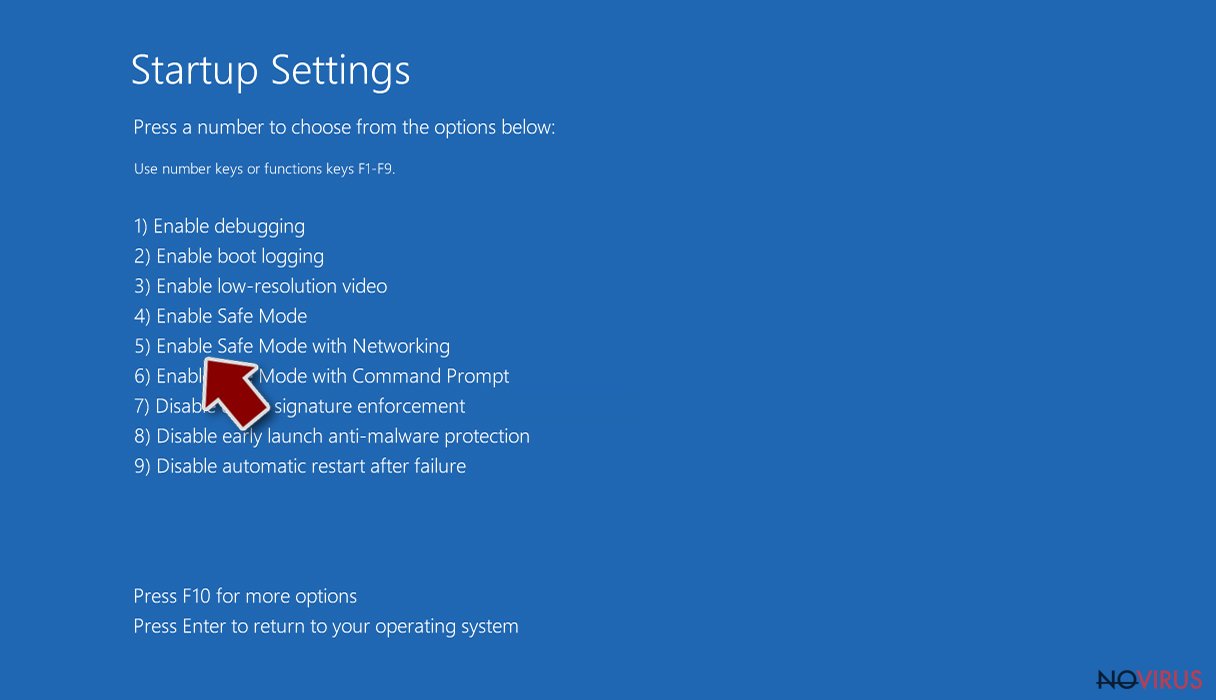
- Choose 5) Enable Safe Mode with Networking.
Step 2. End questionable processes
You can rely on Windows Task Manager that finds all the random processes in the background. When the intruder is triggering any processes, you can shut them down:
- Press Ctrl + Shift + Esc keys to open Windows Task Manager.
- Click on More details.
- Scroll down to Background processes.
- Look for anything suspicious.
- Right-click and select Open file location.
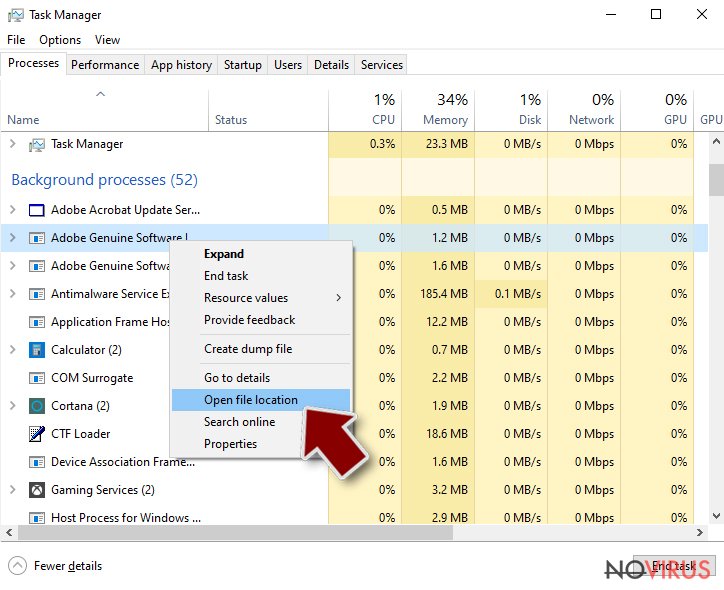
- Go back to the Process tab, right-click and pick End Task.
- Delete the contents of the malicious folder.
Step 3. Check the program in Startup
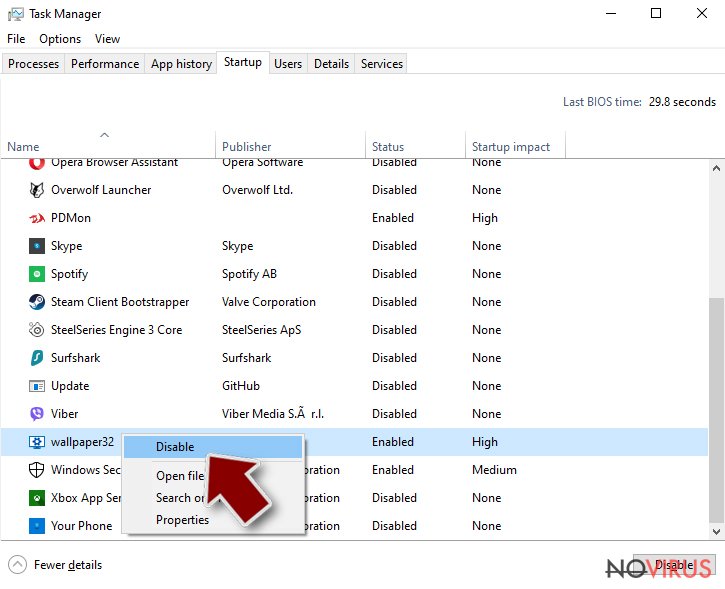
- Press Ctrl + Shift + Esc on your keyboard again.
- Go to the Startup tab.
- Right-click on the suspicious app and pick Disable.
Step 4. Find and eliminate virus files
Data related to the infection can be hidden in various places. Follow the steps and you can find them:
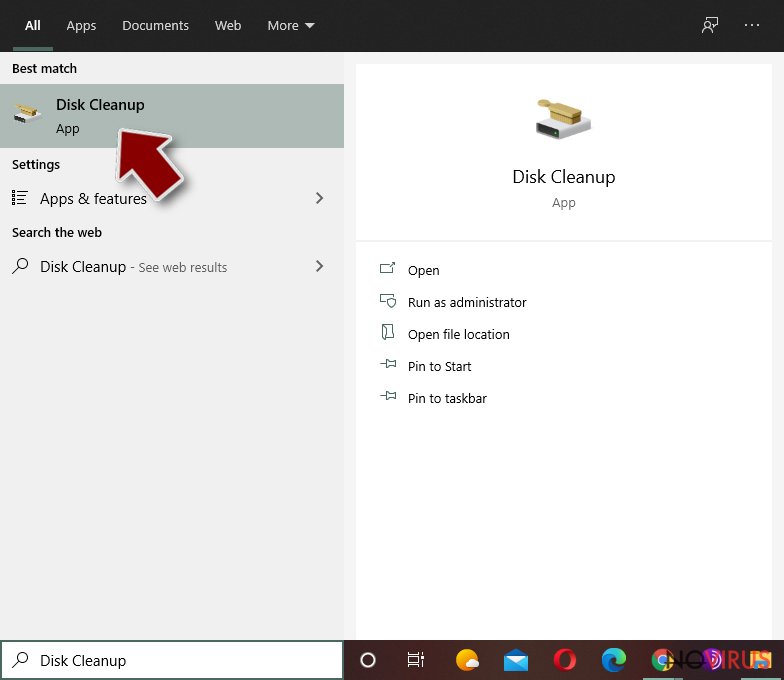
- Type in Disk Cleanup in Windows search and press Enter.
- Select the drive (C: is your main drive by default and is likely to be the one that has malicious files in) you want to clean.
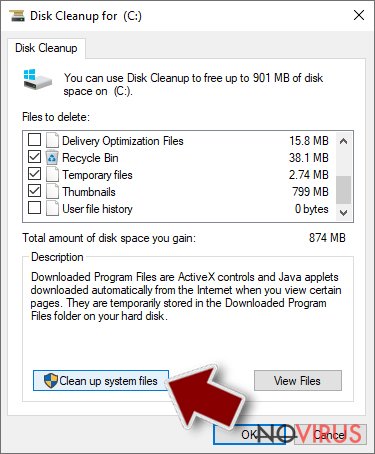
- Scroll through the Files to delete and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.
- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Eliminate Bad Rabbit using System Restore
Restart the device in Safe Mode and initiate BadRabbit removal.
-
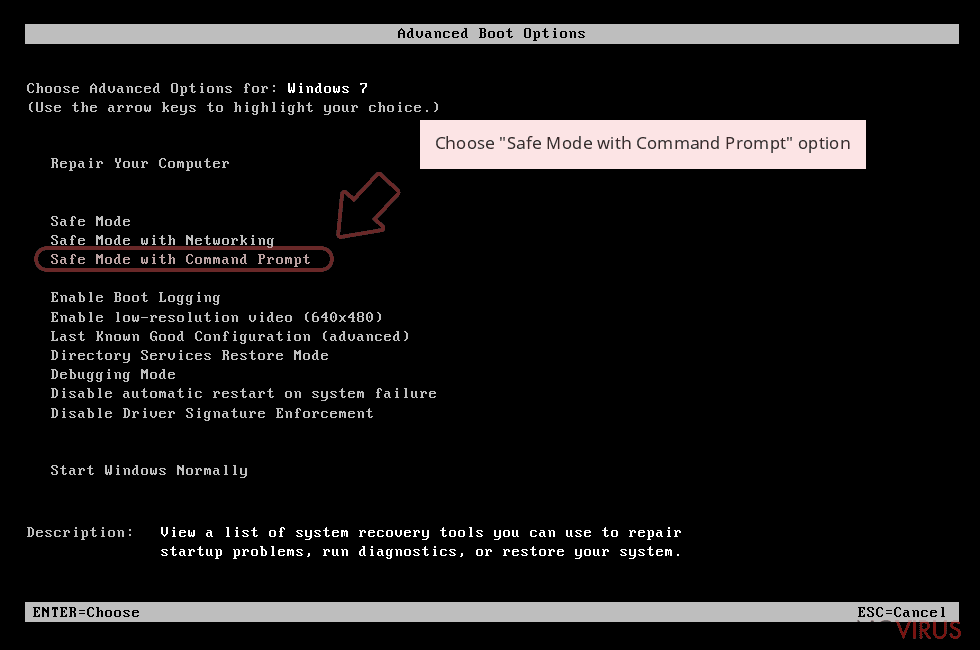
Step 1: Restart your computer in Safe Mode with Command Prompt
Windows 7 / Vista / XP- Go to Start → Shutdown → Restart → OK.
- As soon as your computer starts, start pressing F8 key repeatedly before the Windows logo shows up.
-
Choose Command Prompt from the list

Windows 10 / Windows 8- Click on the Power button at the Windows login screen, and then press and hold Shift key on your keyboard. Then click Restart.
- Then select Troubleshoot → Advanced options → Startup Settings and click Restart.
-
Once your computer starts, select Enable Safe Mode with Command Prompt from the list of options in Startup Settings.

-
Step 2: Perform a system restore to recover files and settings
-
When the Command Prompt window appears, type in cd restore and press Enter.

-
Then type rstrui.exe and hit Enter..

-
In a new window that shows up, click the Next button and choose a restore point that was created before the infiltration of Bad Rabbit and then click on the Next button again.


-
To start system restore, click Yes.

-
When the Command Prompt window appears, type in cd restore and press Enter.
Bonus: Restore your files
Using the tutorial provided above you should be able to eliminate Bad Rabbit from the infected device. novirus.uk team has also prepared an in-depth data recovery guide which you will also find above.There are a couple of methods you can apply to recover data encrypted by Bad Rabbit:
Will Data Recovery Pro decode files encrypted by BadRabbit virus?
The software is practical when restoring data after an unexpected system crash. It might be of use this time as well.
- Download Data Recovery Pro;
- Install Data Recovery on your computer following the steps indicated in the software’s Setup;
- Run the program to scan your device for the data encrypted by Bad Rabbit ransomware;
- Recover the data.
The usefulness of ShadowExplorer
Though Bad Rabbit/Diskcoder.D malware manifests complex features, it does not yet execute the command which deletes shadow volume copies in advance. Therefore, it is possible that Shadow Explorer might prove to be of service since it uses the latter to create the copies of the original files.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Install Shadow Explorer on your computer following the instructions in the software’s Setup Wizard;
- Run the program. Navigate to the menu on the top-left corner and select a disk containing your encrypted files. Look through the available folders;
- When you find the folder you want to recover, right-click it and select “Export”. Also, choose where the recovered data will be stored.
It is strongly recommended to take precautions and secure your computer from malware attacks. To protect your PC from Bad Rabbit and other dangerous viruses, you should install and keep a powerful malware removal tool, for instance, FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes.
How to prevent from getting ransomware
Prevent the government from spying on you
As there is a growing debate in government about collecting users' data and spying on citizens, you should take a closer look at this issue and find out what shady ways of gathering information can be used to collect information about you. You need to browse anonymously if you want to avoid any government-initiated spying and tracking of information.
You can enjoy secure internet browsing and minimize the risk of intrusion into your system if you use Private Internet Access VPN program. This VPN application creates a virtual private network and provides access to the required data without any content restrictions.
Control government and other third party access to your data and ensure safe web browsing. Even if you do not engage in illegal activities and trust your ISP, we recommend being careful about your security. You should take extra precautions and start using a VPN program.
Recover files damaged by a dangerous malware attack
Despite the fact that there are various circumstances that can cause data to be lost on a system, including accidental deletion, the most common reason people lose photos, documents, videos, and other important data is the infection of malware.
Some malicious programs can delete files and prevent the software from running smoothly. However, there is a greater threat from the dangerous viruses that can encrypt documents, system files, and images. Ransomware-type viruses focus on encrypting data and restricting users’ access to files, so you can permanently lose personal data when you download such a virus to your computer.
The ability to unlock encrypted files is very limited, but some programs have a data recovery feature. In some cases, the Data Recovery Pro program can help recover at least some of the data that has been locked by a virus or other cyber infection.