Uninstall Petya virus (Jun 2018 updated) - Uninstall Guide
Petya virus Removal Guide
Description of Petya virus
Petya virus blocks the access to your data and demands to pay a ransom
Cybersecurity specialists have discovered that a well known ransomware virus – Petya virus – has been recently updated. The latest its variant, Bad Rabbit, belongs to the same group of viruses. Thus, its primary mission is to encrypt confidential data and make it inaccessible for a victim unless he or she pays the ransom.
It seems that the virus targets German-speaking users, however, do not let your guard down thinking that you will escape the infection. It has also been noticed in almost every Europe's country.
Analysts have already recorded the victims — companies such as ‘Maersk’, ‘Roseneft’, ‘Saint — Gobain’, a few banks and power suppliers, as well as recently infected Odessa’s International Airport together with Russian media groups ‘Fontanka’ and ‘Interfax’.
If you wonder who hides underneath Petya, IT experts claim that they have found serious evidence of ‘MeDoc’ company being a primary ransomware distribution source. However, it still hasn't been proved at the moment.
If you have already fallen into the trap of this virus and are about to pay the money, do not proceed with the transaction! We offer you a solution – Petya removal. In order to eliminate it completely you might need an antispyware program. One of the trustworthy software is FortectIntego.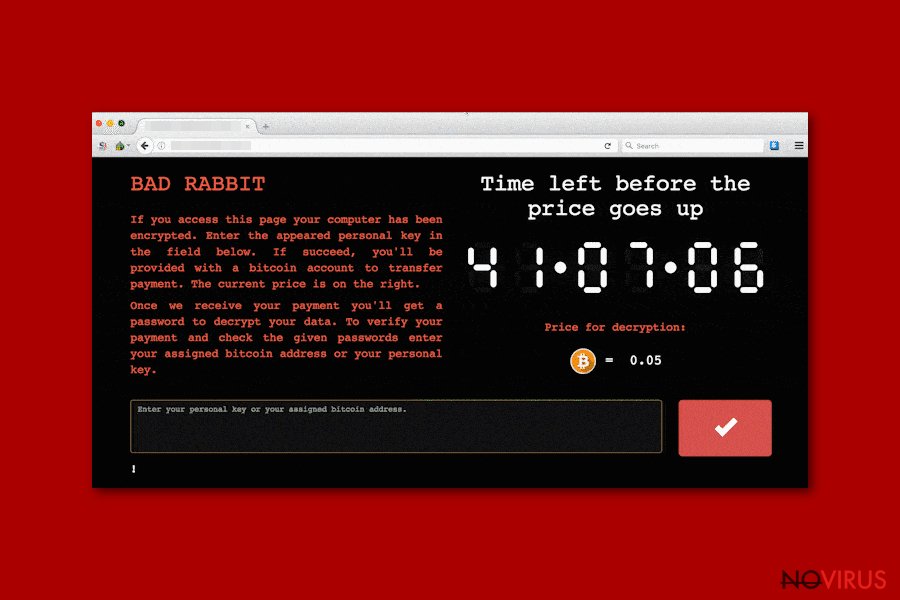
Ransomware uses complex algorithms to encode files on your computer
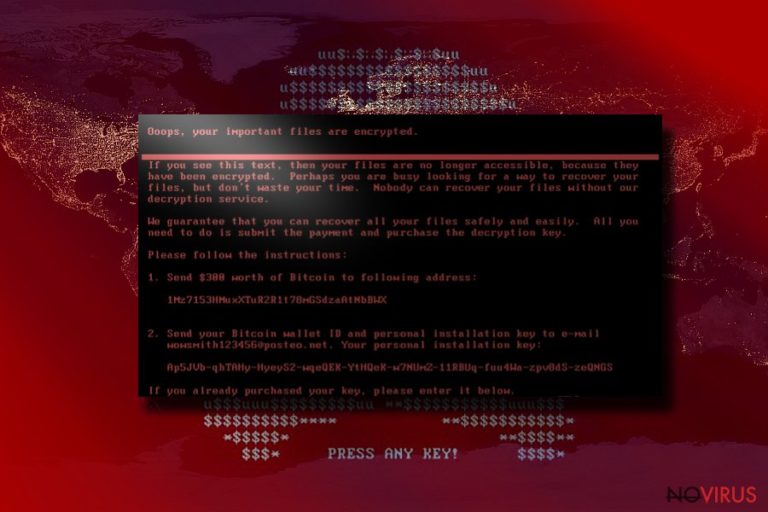
There are quite intriguing facts about Petya ransomware. It has been observed that it uses RSA-4096 and AES-256 algorithms which are said to be used by state militaries for encoding top secret files. Unlike other major ransomware threats, the virus forcefully restarts your operating system.
Once the computer is rebooted, the notification emerges declaring:
DO NOT TURN OFF YOUR PC! IF YOU ABORT THIS PROCESS, YOU COULD DESTROY ALL OF YOUR DATA! PLEASE ENSURE THAT YOUR POWER CABLE IS PLUGGED IN!
This warning appears due to the fact that the virus is encrypting your files. Thus, it alarms you not to interrupt the process. Convinced that it is a system error, you wait several minutes until ‘PRESS ANY KEY’ appears on the screen. It only takes a blink of an eye until you go spare after realising that all your highly essential documents and files are encrypted.
Moreover, the ransom note sets the time period within which you are obligated to pay a 0.9 Bitcoin ransom which equals to $400. Cybersecurity experts have already reported that the criminals changed their conditions and the value of the payment decreased to $300.
Moreover, you should be aware that data encryption is not the only feature of the ransomware. Unlike other malware, Petya is designed to modify computer’s master boot record (MBD) settings. Thus, the only way to remove the ransomware is to restore them.
While many might think that malware elimination works as a decryption process as well, remember, that in most of the situations a decryption key is necessary to regain access to your files. However, in this case, even it won’t help — Petya is not able to maintain required correspondence with Command/Control servers. In other terms, victims are not identified with specific numbers which are later used to match them with proper decryption keys.
Thus, malware experts defined the ransomware as a data wiper, since it generates useless random numbers/characters instead of providing a specific decryption key. In spite of that, you should not meet cybercriminals’ expectations and rush to remove Petya because even if you pay the ransom, your files will remain encrypted.
If you haven’t enabled a function on your computer to automatically store backup copies in the cloud, you can try alternative recovery methods provided at the end of this article. IT professionals finally developed a decryptor that can be acquired as a CD disk or as windows executable file. Read instructions below in order to find out how to use it.
However, our team informs you that the victims who suffered from PetyaWrap or EternalPetya versions of the parent program, will not be able to recover their files with the decryptor.
New versions of Petya:
Bad Rabbit ransomware virus. Since October 2017, the virus has been distributed as a fake Adobe Flash Player Update. Some IT experts warn that it also spreads with a Diskcoder.D’s name. Recorded victims are mostly located in Russia and Ukraine together with neighbor countries — Bulgaria and Turkey.
The key features of the malware are: The usage of the optimal mix of AES and RSA algorithms and .encrypted extension appended at the end of the file-name. Besides, victims are demanded to pay 0.05 Bitcoin ransom and faces a risk to expose their credentials.
Mamba ransomware. This extremely malicious program targets German companies and stealthily infiltrates onto computers. The victims are not able to detect the malware since it imitates regular processes while secretly corrupting data. It has been noticed spreading via spam emails or fake updates of regular programs.
Experts noted that hackers used Salsa20 algorithm to encrypt data on the computer. This new feature got rid of vulnerabilities discovered in previous Petya versions. Once installed, the ransomware insists on paying an enormous 1 BTC ransom.
GoldenEye ransomware virus. This malware operates similarly to its original version. It detects whether User Account Control (UAC) is not secured correctly and infects the system. To circumvent highly-protected UACs, the ransomware continuously generates a pop-up asking to give administrative rights and if agreed, launches the malware.
Afterwards, YOUR_FILES_ARE_ENCRYPTED.TXT file is created, stating that the victim has to pay a 1.3 BTC ransom in order to recover its data. Criminals use AES encryption method to attack their victims.
Petrwrap ransomware. Even though this malware is not directly developed by the same group of hackers, the creators exploited Petya’s code in order to obtain revenue illegally. The ransomware is based on the replaced ECDH algorithm of the parent program. Experts say that 2000 computers have been infected already and the number is only increasing.
To infiltrate the virus hackers use vulnerable RDP networks together with the psExec tool. One of the main differences of this version is that it remains silents for 1.5 hours before starting the encryption.
Misha ransomware. This malicious program started its activity in May 2016, when Janus Cybercrime Solutions campaign invited other criminals to reinforce Petya developers. This is another way how hackers generate revenue since there is an entrance fee. The value of the ransom exceeds 1.93 BTC. Thus criminals share huge profits from distributing the malware.
Another important detail is that victims are asked to use a Tor browser in order to gain further information on how to decrypt their files. The ransomware employs AES and CBC encryption algorithms to perform an attack.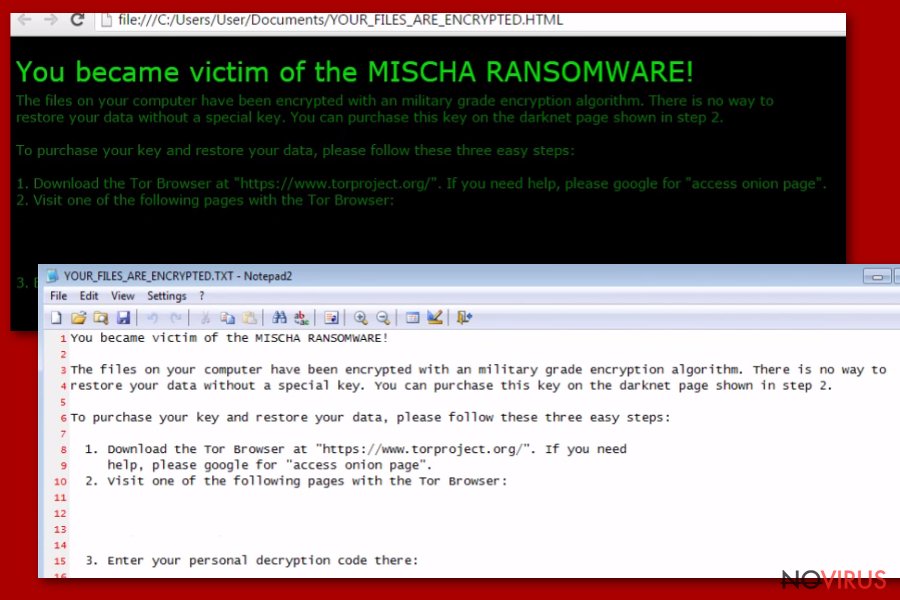
Malicious program spreads via corrupted Dropbox links and fake Adobe Flash update
Before proceeding to the removal part, it is vital to be aware of the transmission methods. IT experts have detected that the ransomware spreads via infected email attachments. Once criminals updated Petya virus, they provided wowsmith123456@posteo.net e-mail address to receive further information about payments. However, be wary that it might come in either format.
Furthermore, the virus is spotted traveling via Dropbox link with ‘application folder-gepackt.exe’ attached. After you open it, the virus starts its dreadful job. Recent reports inform that new versions of this ransomware use the CVE-2017-0199 Office RTF vulnerability to infect the systems. Now you know one of the leading channels how Petya malware might attack you. Likewise, it is crucial to be extremely cautious opening the emails received from unknown senders.
Moreover, one of your acquaintances might be infected with the virus. With the help of a malicious computer worm, the virus might come hidden under a file which was seemingly sent from your friend. All in all, it doesn’t take much time to inquire him or her directly. As a result, you can minimize the risk of getting infected with Petya virus.
Additionally, our team suggests downloading MS17-010 and other Microsoft patches to fix SMB vulnerability that is discovered as being exploited by different versions of the ransomware. Of course, use a powerful antispyware application, this way you will fully protect your system from malevolent programs.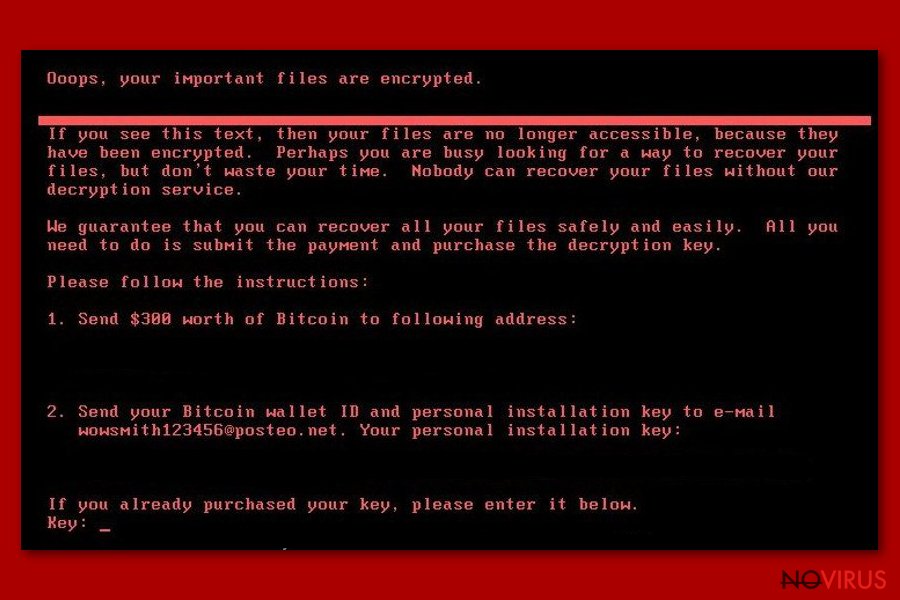
A reliable security software can help you get rid of Petya virus
You should take into account that the ransomware has a significantly complex and exquisite structure so eliminating it by yourself might turn into quite a challenge. If you are prepared to remove Petya, you might perform elimination by following the instructions delivered by IT specialists. However, you will need to pay attention and follow each step with utmost precision.
Alternatively, there is another choice – automatic Petya removal. For that purpose, it is necessary to choose a powerful anti-spyware program. Mostly, all of them are created to block and delete various sorts of malware, including ransomware as well.
Additionally, you will need to check regularly whether the software is updated. This is crucial since the program requires to maintain proper protection of your operating system and block you from future virus assaults. Lastly, we remind you to back up your files regularly and cautiously reading emails.
Getting rid of Petya virus. Follow these steps
In-depth guide for the Petya elimination
Important! →
The elimination guide can appear too difficult if you are not tech-savvy. It requires some knowledge of computer processes since it includes system changes that need to be performed correctly. You need to take steps carefully and follow the guide avoiding any issues created due to improper setting changes. Automatic methods might suit you better if you find the guide too difficult.
Step 1. Launch Safe Mode with Networking
Safe Mode environment offers better results of manual virus removal
Windows 7 / Vista / XP
- Go to Start.
- Choose Shutdown, then Restart, and OK.
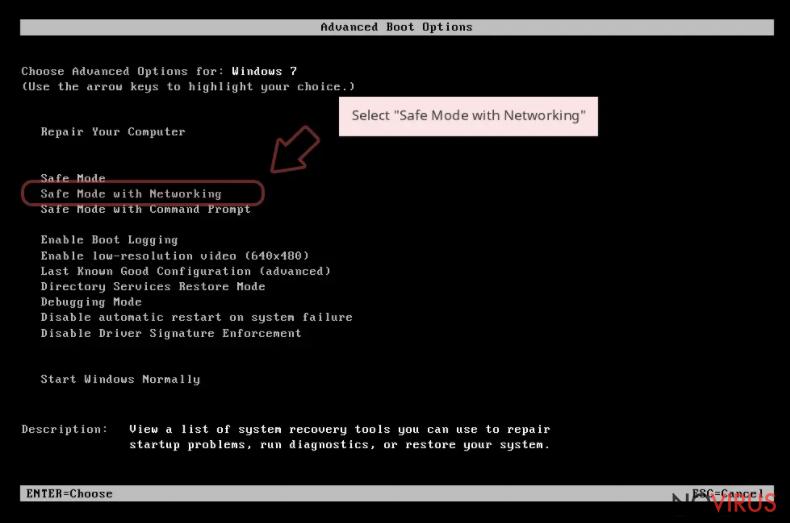
- When your computer boots, start pressing the F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) a few times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.
Windows 10 / Windows 8
- Right-click the Start button and choose Settings.
- Scroll down to find Update & Security.
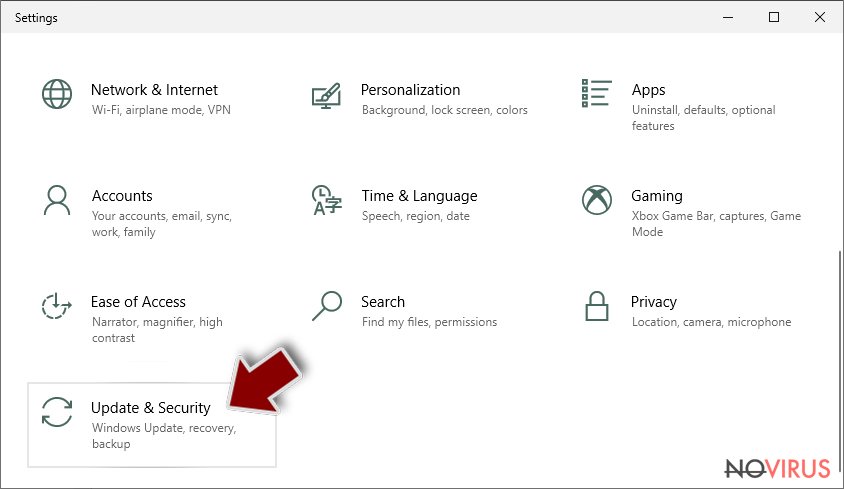
- On the left, pick Recovery.
- Scroll to find Advanced Startup section.
- Click Restart now.
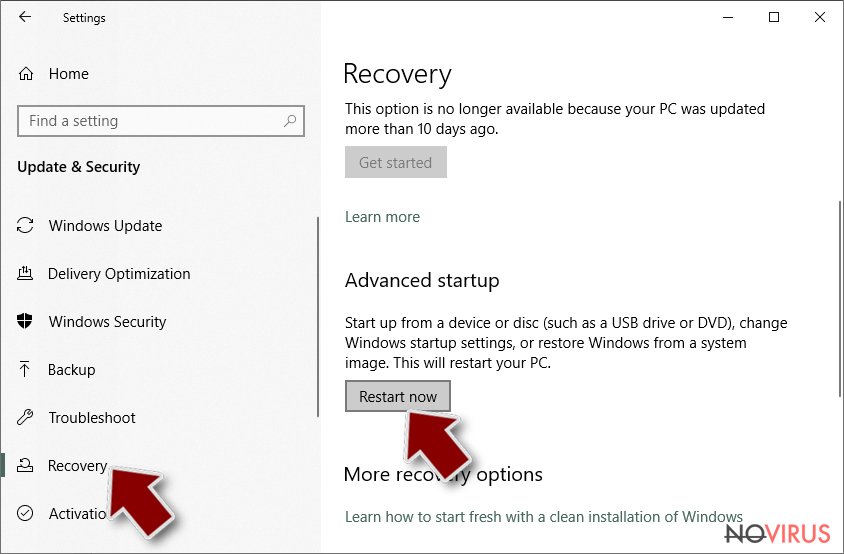
- Choose Troubleshoot.
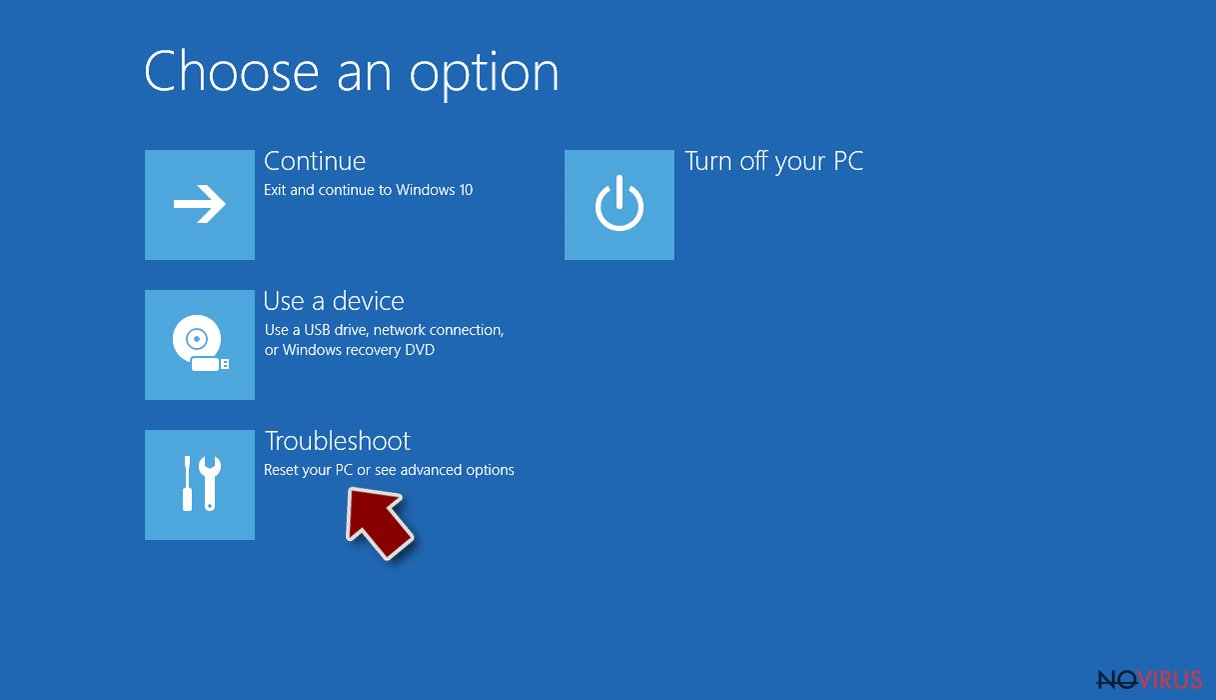
- Go to Advanced options.
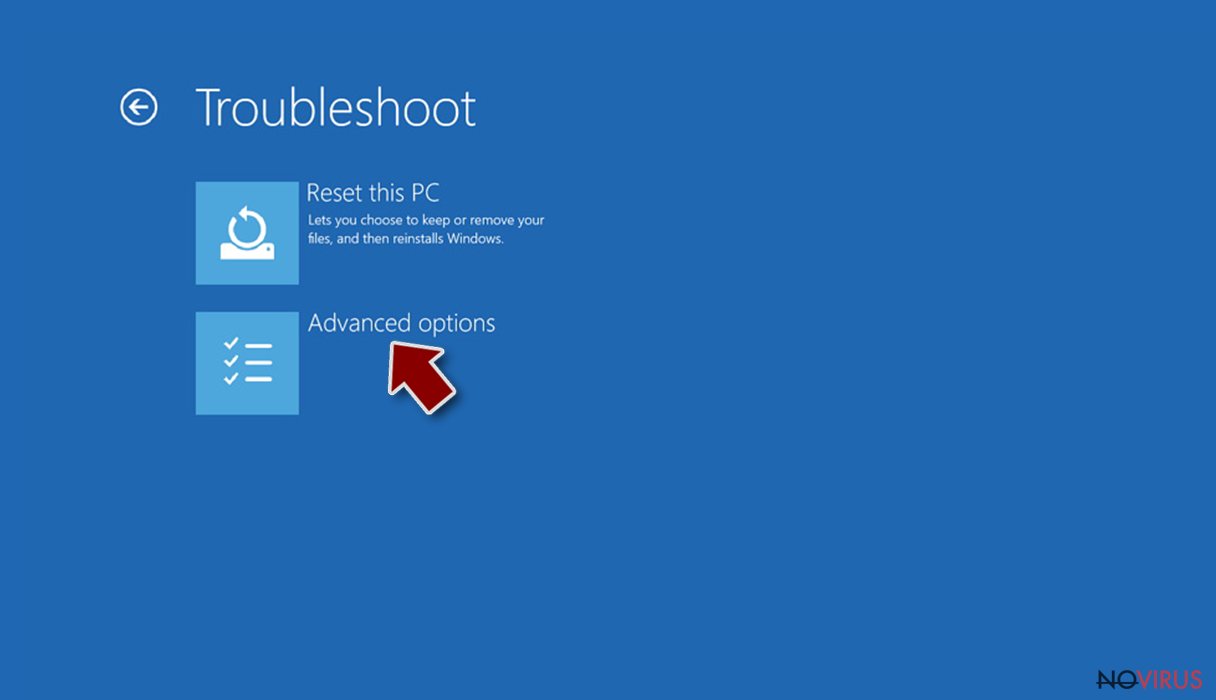
- Select Startup Settings.
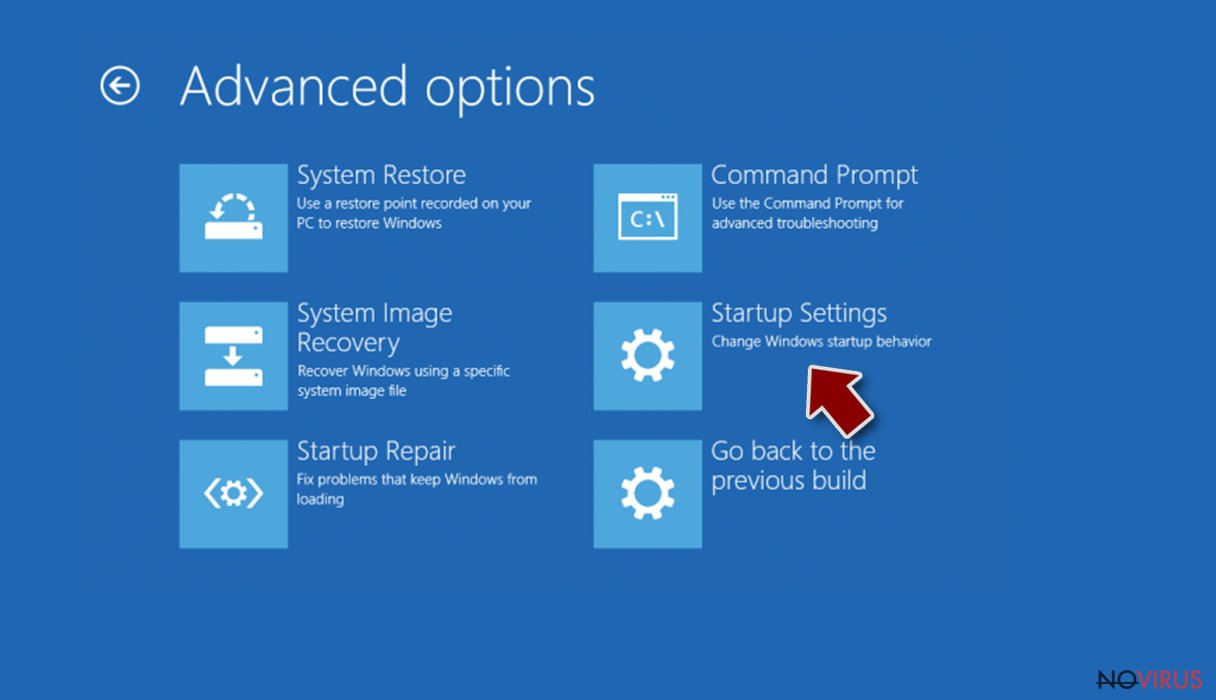
- Press Restart.
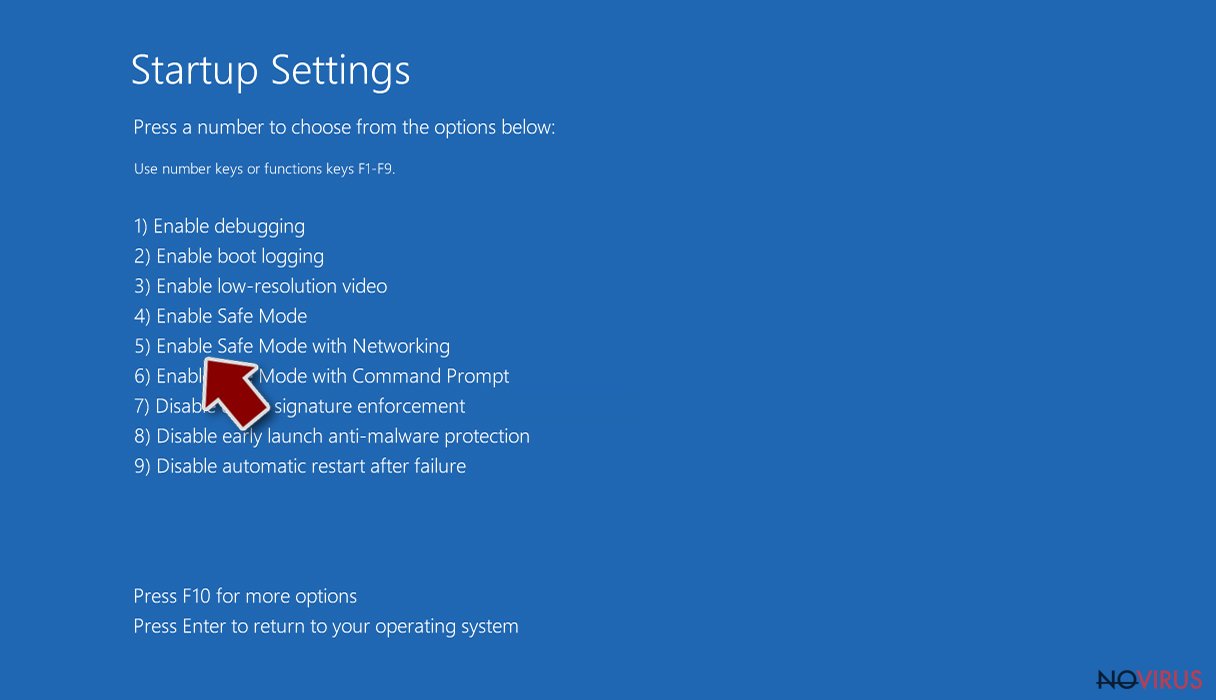
- Choose 5) Enable Safe Mode with Networking.
Step 2. End questionable processes
You can rely on Windows Task Manager that finds all the random processes in the background. When the intruder is triggering any processes, you can shut them down:
- Press Ctrl + Shift + Esc keys to open Windows Task Manager.
- Click on More details.
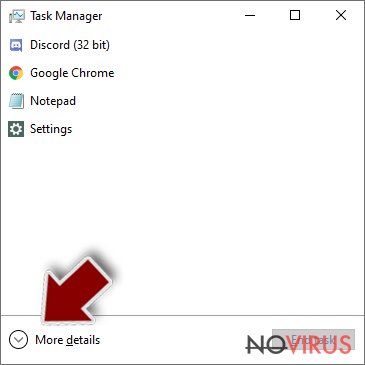
- Scroll down to Background processes.
- Look for anything suspicious.
- Right-click and select Open file location.
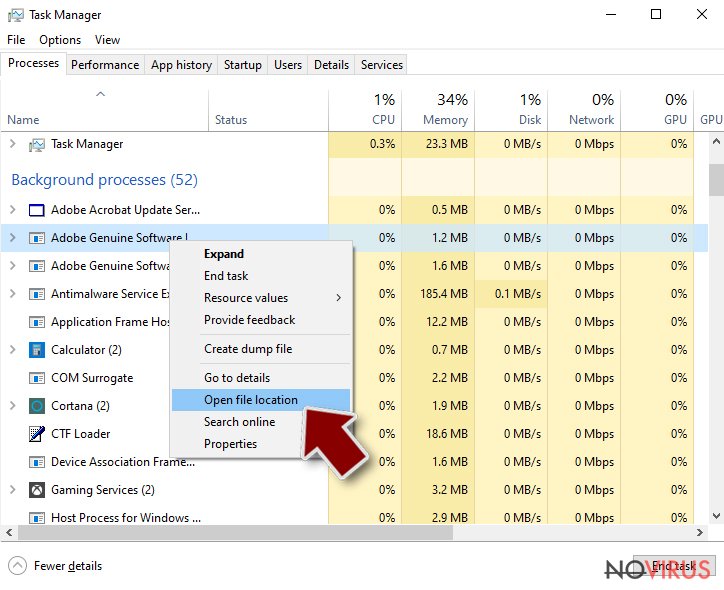
- Go back to the Process tab, right-click and pick End Task.
- Delete the contents of the malicious folder.
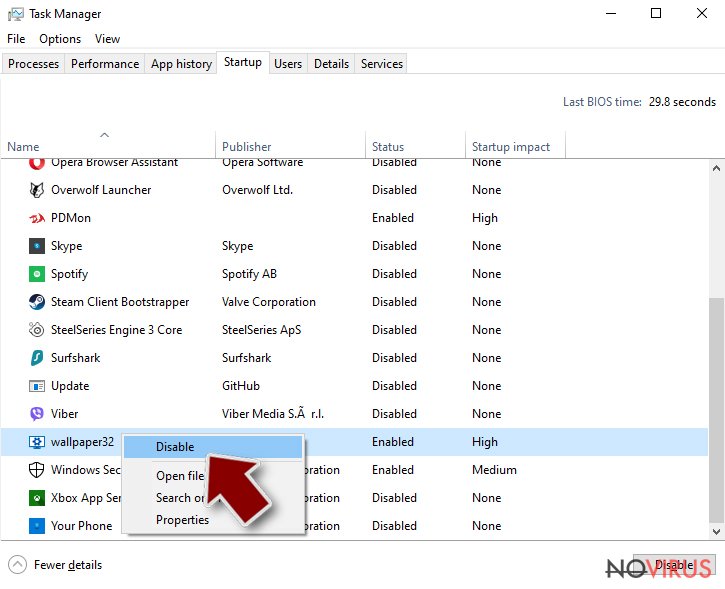
Step 3. Check the program in Startup
- Press Ctrl + Shift + Esc on your keyboard again.
- Go to the Startup tab.
- Right-click on the suspicious app and pick Disable.
Step 4. Find and eliminate virus files
Data related to the infection can be hidden in various places. Follow the steps and you can find them:
- Type in Disk Cleanup in Windows search and press Enter.
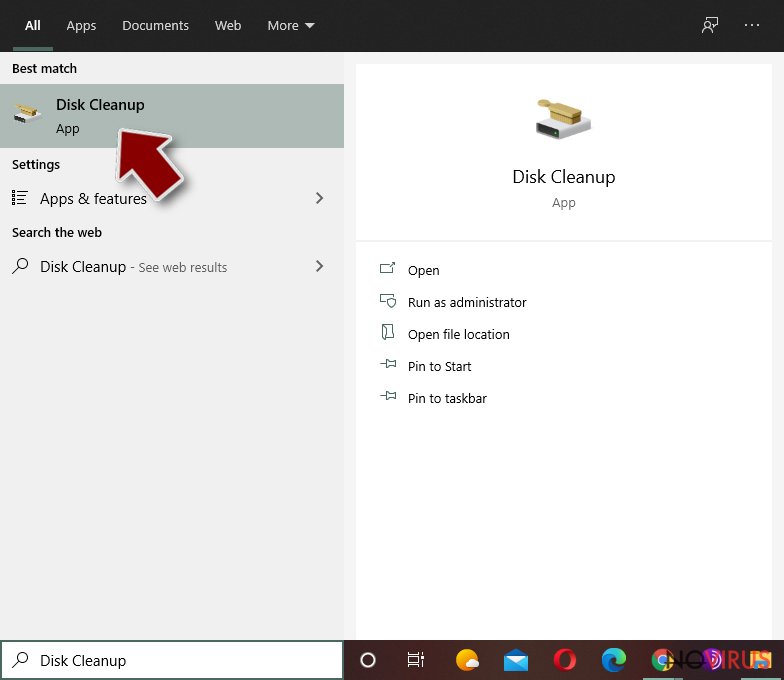
- Select the drive (C: is your main drive by default and is likely to be the one that has malicious files in) you want to clean.
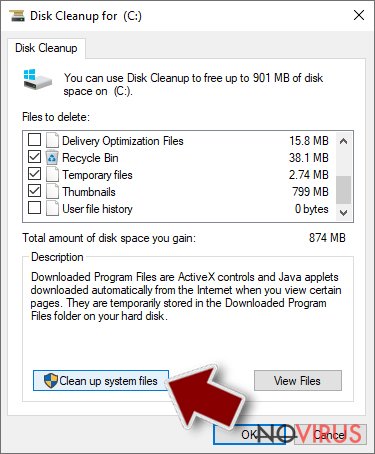
- Scroll through the Files to delete and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.
- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Eliminate Petya using System Restore
-
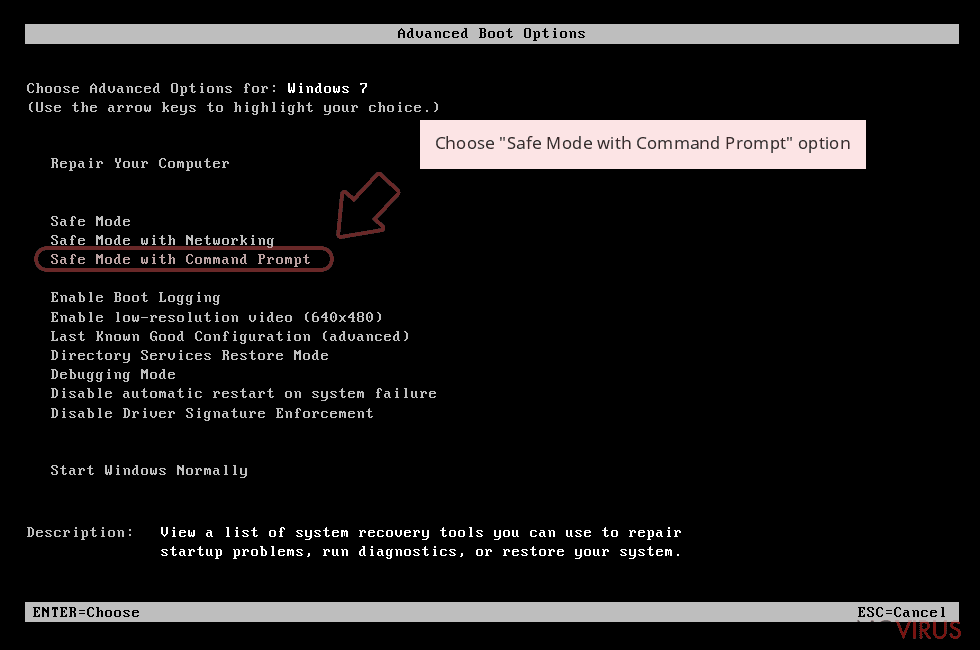
Step 1: Restart your computer in Safe Mode with Command Prompt
Windows 7 / Vista / XP- Go to Start → Shutdown → Restart → OK.
- As soon as your computer starts, start pressing F8 key repeatedly before the Windows logo shows up.
-
Choose Command Prompt from the list

Windows 10 / Windows 8- Click on the Power button at the Windows login screen, and then press and hold Shift key on your keyboard. Then click Restart.
- Then select Troubleshoot → Advanced options → Startup Settings and click Restart.
-
Once your computer starts, select Enable Safe Mode with Command Prompt from the list of options in Startup Settings.

-
Step 2: Perform a system restore to recover files and settings
-
When the Command Prompt window appears, type in cd restore and press Enter.

-
Then type rstrui.exe and hit Enter..

-
In a new window that shows up, click the Next button and choose a restore point that was created before the infiltration of Petya and then click on the Next button again.


-
To start system restore, click Yes.

-
When the Command Prompt window appears, type in cd restore and press Enter.
It is strongly recommended to take precautions and secure your computer from malware attacks. To protect your PC from Petya and other dangerous viruses, you should install and keep a powerful malware removal tool, for instance, FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes.
How to prevent from getting ransomware
Prevent the government from spying on you
As there is a growing debate in government about collecting users' data and spying on citizens, you should take a closer look at this issue and find out what shady ways of gathering information can be used to collect information about you. You need to browse anonymously if you want to avoid any government-initiated spying and tracking of information.
You can enjoy secure internet browsing and minimize the risk of intrusion into your system if you use Private Internet Access VPN program. This VPN application creates a virtual private network and provides access to the required data without any content restrictions.
Control government and other third party access to your data and ensure safe web browsing. Even if you do not engage in illegal activities and trust your ISP, we recommend being careful about your security. You should take extra precautions and start using a VPN program.
Recover files damaged by a dangerous malware attack
Despite the fact that there are various circumstances that can cause data to be lost on a system, including accidental deletion, the most common reason people lose photos, documents, videos, and other important data is the infection of malware.
Some malicious programs can delete files and prevent the software from running smoothly. However, there is a greater threat from the dangerous viruses that can encrypt documents, system files, and images. Ransomware-type viruses focus on encrypting data and restricting users’ access to files, so you can permanently lose personal data when you download such a virus to your computer.
The ability to unlock encrypted files is very limited, but some programs have a data recovery feature. In some cases, the Data Recovery Pro program can help recover at least some of the data that has been locked by a virus or other cyber infection.