Uninstall Sage 2.2 virus (Uninstall Guide) - Aug 2017 updated
Sage 2.2 virus Removal Guide
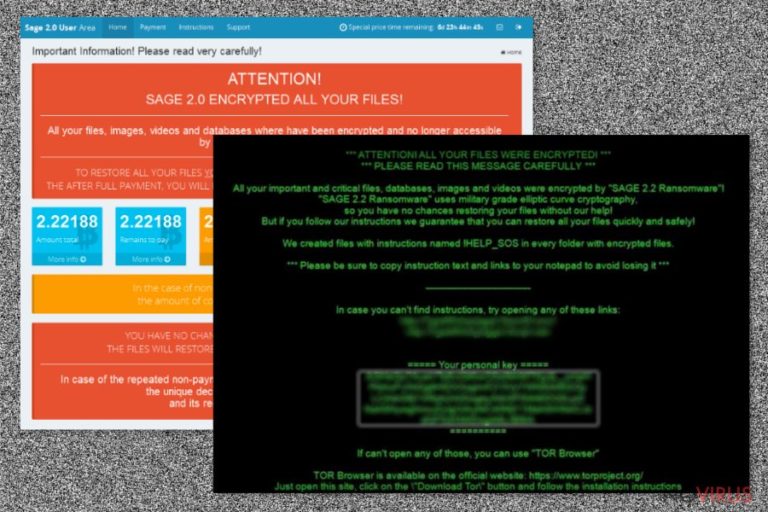
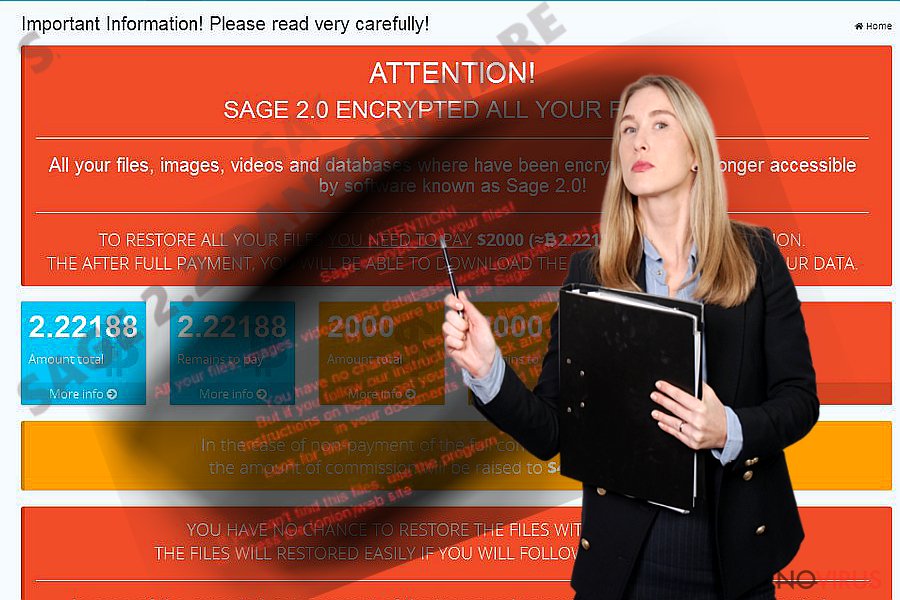
Description of Sage 2.2 ransomware
Sage ransomware presents its third installment – Sage 2.2 virus
Soon after the emergence of its predecessors Sage and Sage 2.0, Sage 2.2 virus joins the family. Despite few modifications, it operates in a similar way as its former editions. After finding transmission similarities with such threats as Locky and Cerber, IT professionals suspect that the same cyber villains might behind these threats. It targets users via email attachments.
The binaries of the crypto-malware are delivered in the form of .doc or .js file. Read this review to arm up with proper knowledge and protect yourself from this virtual misfortune. If you have already fallen into the trap of this ransomware, do not give into distress and proceed to Sage 2.2 removal.
Surely, when it comes to discussions about Locky or Cerber, various allusions raise up in netizens‘ minds. Those, who have been affected by either of them, might have shivers after hearing the mention of these threats. Those, who escaped this misfortunate, might have diverse impressions.
Continuing their terror, the developers intend to keep the virtual community in their grip with Sage 2.2 malware as well. Following the pattern of the previous version, it is detectable in spam messages. Like the infamous Cerber which deceived users with fake invoice attachments, Sage 2.2 ransomware continues this trend as well. The infected emails may contain [random numbers]_ACH20022017.zip or min1_201720103191.58778.zip attachments or similar ones.
In these folders, a .doc file is placed with the macro settings. Previously felons generated a Word file which asked victims to enable macro settings. The recent heir of Sage – Sage 2.2 – forges a fake message that the file is presented in the outdated MS Word version, so users have to ‘Enable content’ to see the contents.
Recent discoveries reveal that Sage 2.2 borrows the old Cerber’s feature to alarm users with VBScript voice messages. In these notifications, the victim’ are enticed to extract the contents of the attached file by opening the provoking folder with the supposed sexual intercourse content. Certainly, what they download is not the expected video but a destructive file-encrypting threat. After launching the virus, it may take some time to show any signs of vitality.
It replicates itself to C:\Users\[loginname]\AppData\Roaming which results in the appearance of User Account Control message and asks for victim‘s permission to execute further. Users see the window asking to enable Windows Command Processor launched by Microsoft Windows.
The only hint that suggests the origin of this virus is the program location. It refers to a sub folder located in an AppData Roaming folder. Do not enable this command. If you do, the virus will successfully encrypt your files. Later on, Sage 2.2 crypto-malware presents the demands in !HELP_SOS.html and !HELP_SOS.bmp files.
In the case of the previous version, the threat asked for 2000 USD in exchange for the files. The mentioned files do not indicate a specific amount of ransom. It varies depending on each victim. Brush aside any thoughts to remit the payment and instead remove Sage 2.2.
When did the infection occupy my device?
The gearheads of this file-encrypting infection have been exploiting botnets for distributing several thousand infected spam messages simultaneously. As mentioned before, do not fall for the bait even if the received spam email is supposedly sent from an official institution. Even if the subject contains ‘urgent’ do not extract any attached contents without verifying the sender.
Additionally, boost up your cyber security by combing your anti-virus and anti-spyware tools. FortectIntego and Malwarebytes are effective tools battling with ransomware and lowering the risk of Sage 2.2 hijack. The combination of these tools is the only viable method to block trojans which distribute this virus.
The malware has been disguised under the names of these threats: Win32.Trojan.WisdomEyes.16070401.9500.9973, Trojan/Win32.SageCrypt.C1798570, trojan.Encoder.10307, and Win32/Trojan.Ransom.aac.
Can I delete Sage 2.2 permanently?
Speaking of Sage 2.2 removal, automatic methods are effective. Unless you are a proficient virus researcher, it is not recommended meddling with the virus manually. Let security tools remove Sage 2.2 virus. Only when it is completely removed, you might think of data recovery instructions.
Currently, there is no official decryption software released, but the below-suggested methods might be efficient in your case. If you encounter any problems launching the problem, use the access recovery instructions.
Getting rid of Sage 2.2 virus. Follow these steps
In-depth guide for the Sage 2.2 elimination
Enter Safe Mode to open your anti-virus and malware removal utilities and remove Sage 2.2 virus properly.
Important! →
The elimination guide can appear too difficult if you are not tech-savvy. It requires some knowledge of computer processes since it includes system changes that need to be performed correctly. You need to take steps carefully and follow the guide avoiding any issues created due to improper setting changes. Automatic methods might suit you better if you find the guide too difficult.
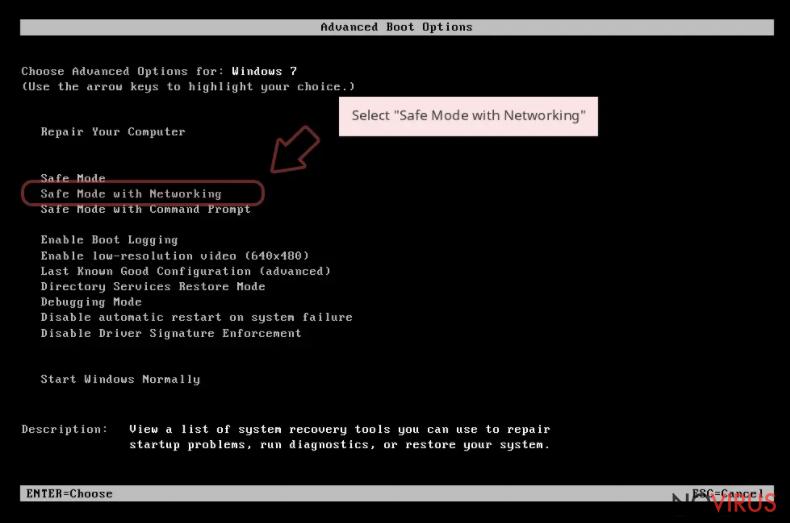
Step 1. Launch Safe Mode with Networking
Safe Mode environment offers better results of manual virus removal
Windows 7 / Vista / XP
- Go to Start.
- Choose Shutdown, then Restart, and OK.
- When your computer boots, start pressing the F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) a few times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.
Windows 10 / Windows 8
- Right-click the Start button and choose Settings.
- Scroll down to find Update & Security.
- On the left, pick Recovery.
- Scroll to find Advanced Startup section.
- Click Restart now.
- Choose Troubleshoot.
- Go to Advanced options.
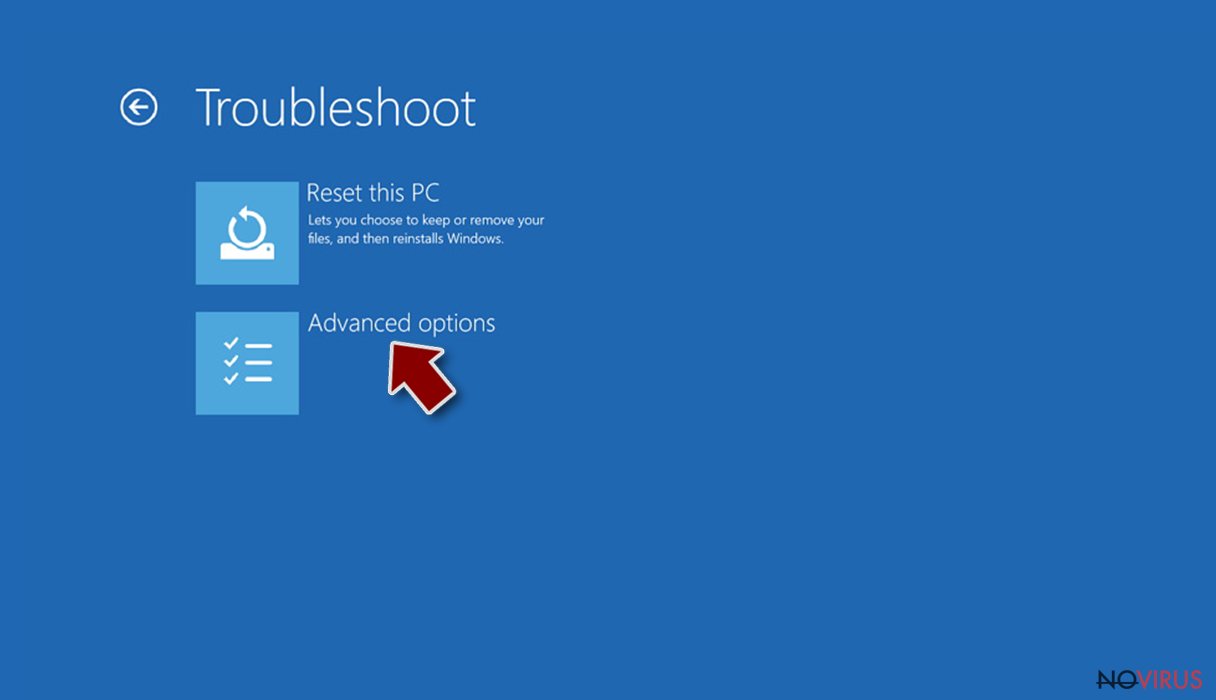
- Select Startup Settings.
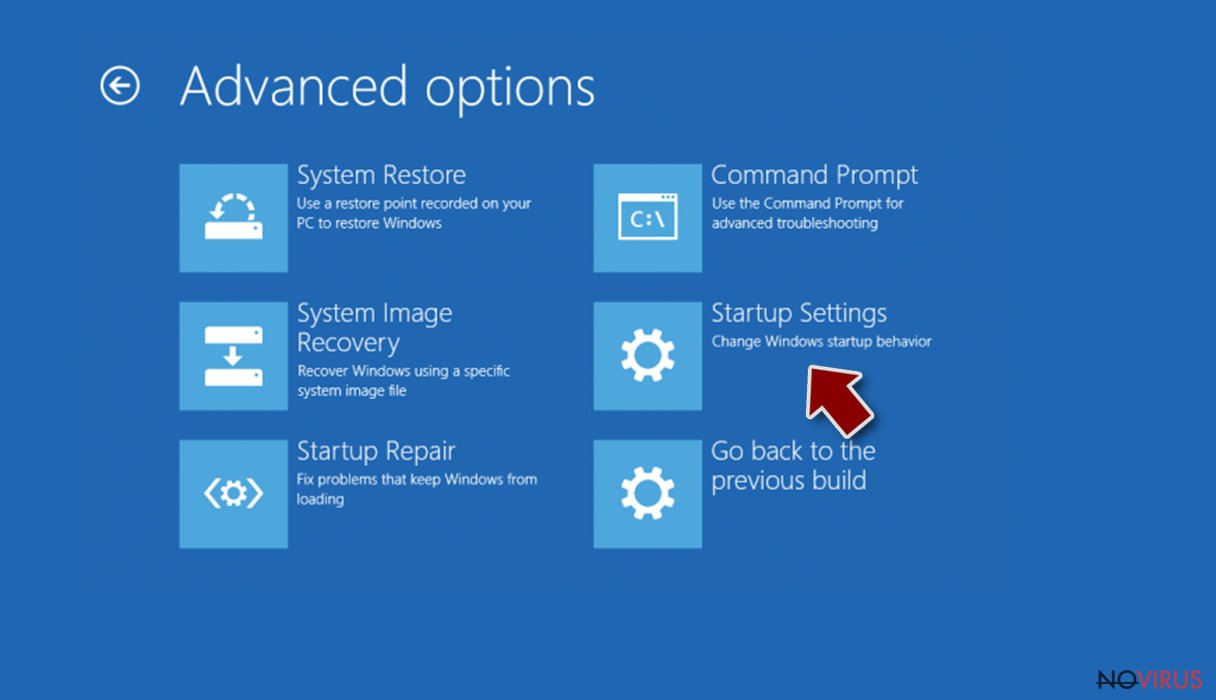
- Press Restart.
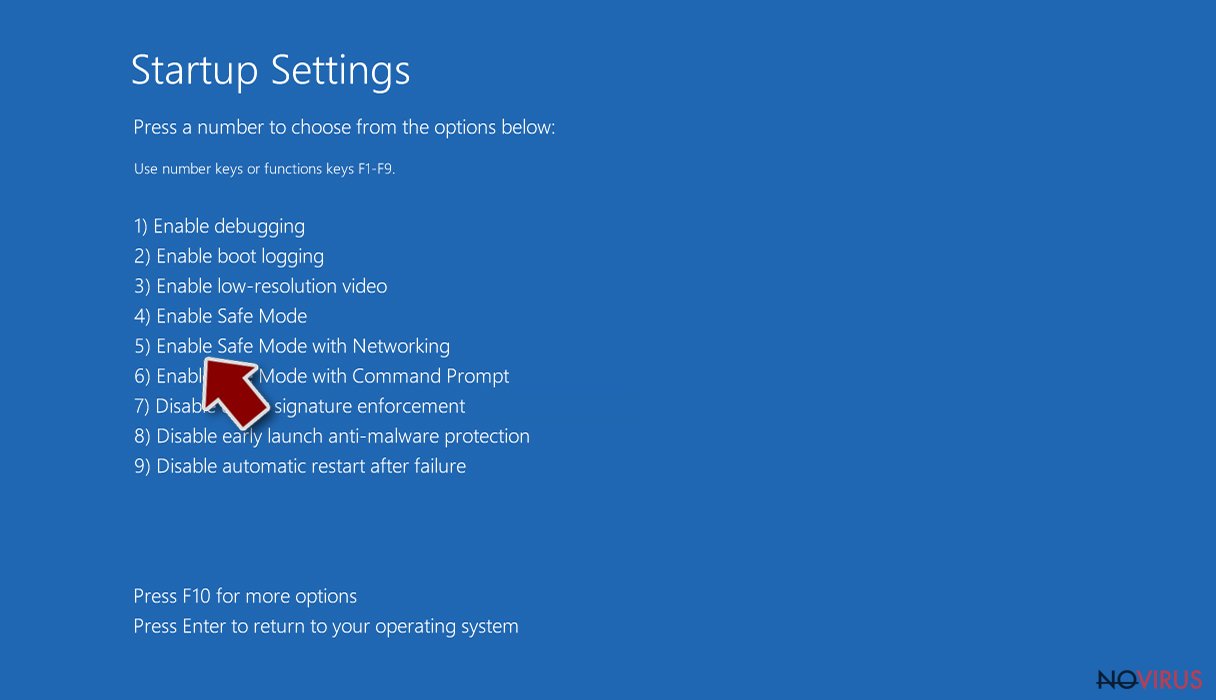
- Choose 5) Enable Safe Mode with Networking.
Step 2. End questionable processes
You can rely on Windows Task Manager that finds all the random processes in the background. When the intruder is triggering any processes, you can shut them down:
- Press Ctrl + Shift + Esc keys to open Windows Task Manager.
- Click on More details.
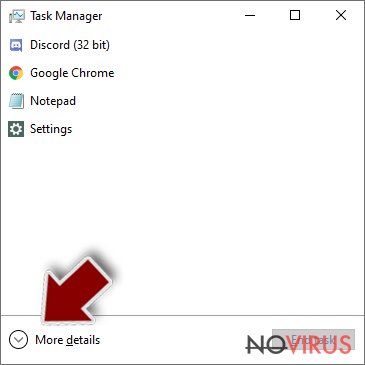
- Scroll down to Background processes.
- Look for anything suspicious.
- Right-click and select Open file location.
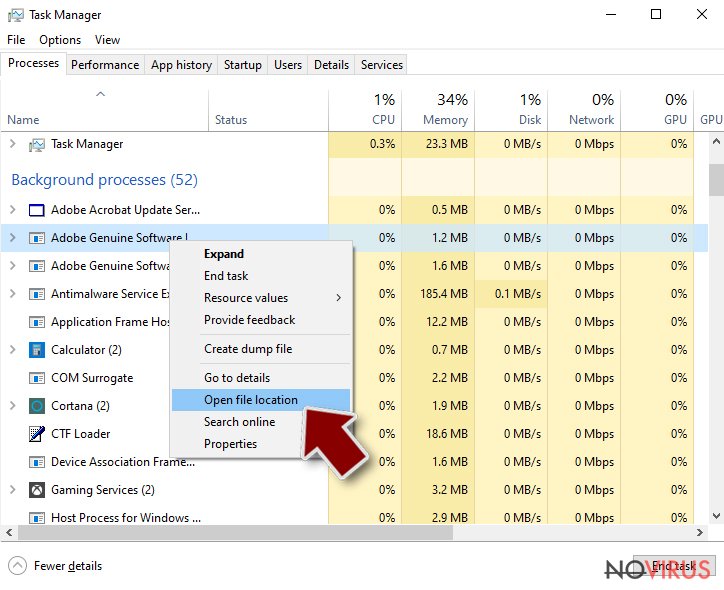
- Go back to the Process tab, right-click and pick End Task.
- Delete the contents of the malicious folder.
Step 3. Check the program in Startup
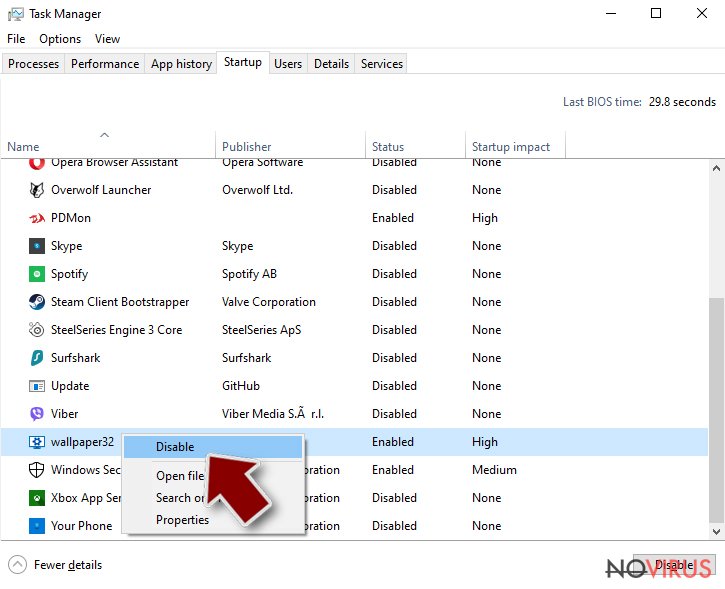
- Press Ctrl + Shift + Esc on your keyboard again.
- Go to the Startup tab.
- Right-click on the suspicious app and pick Disable.
Step 4. Find and eliminate virus files
Data related to the infection can be hidden in various places. Follow the steps and you can find them:
- Type in Disk Cleanup in Windows search and press Enter.
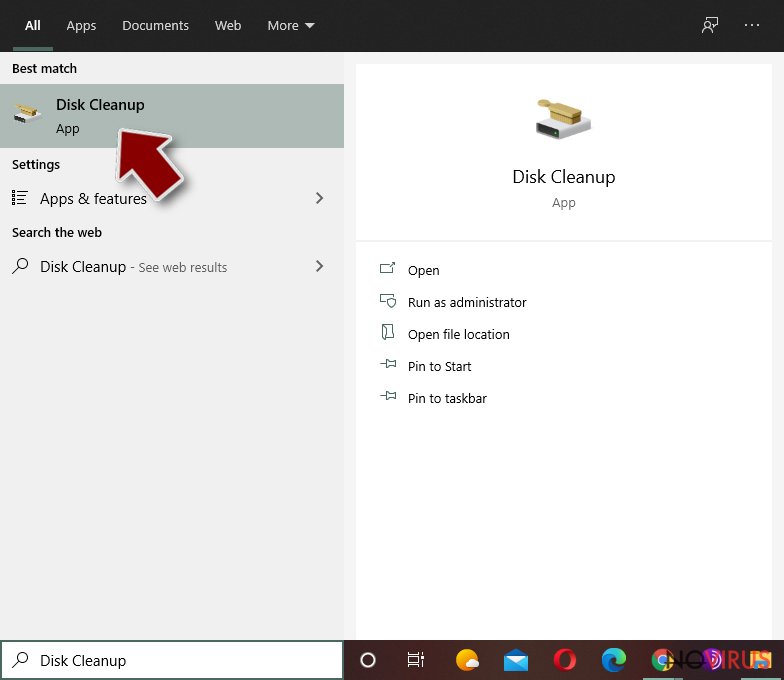
- Select the drive (C: is your main drive by default and is likely to be the one that has malicious files in) you want to clean.
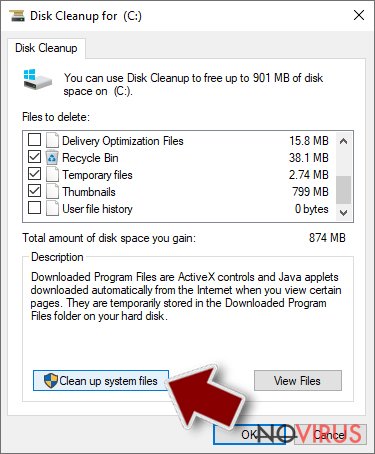
- Scroll through the Files to delete and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.
- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Eliminate Sage 2.2 using System Restore
-
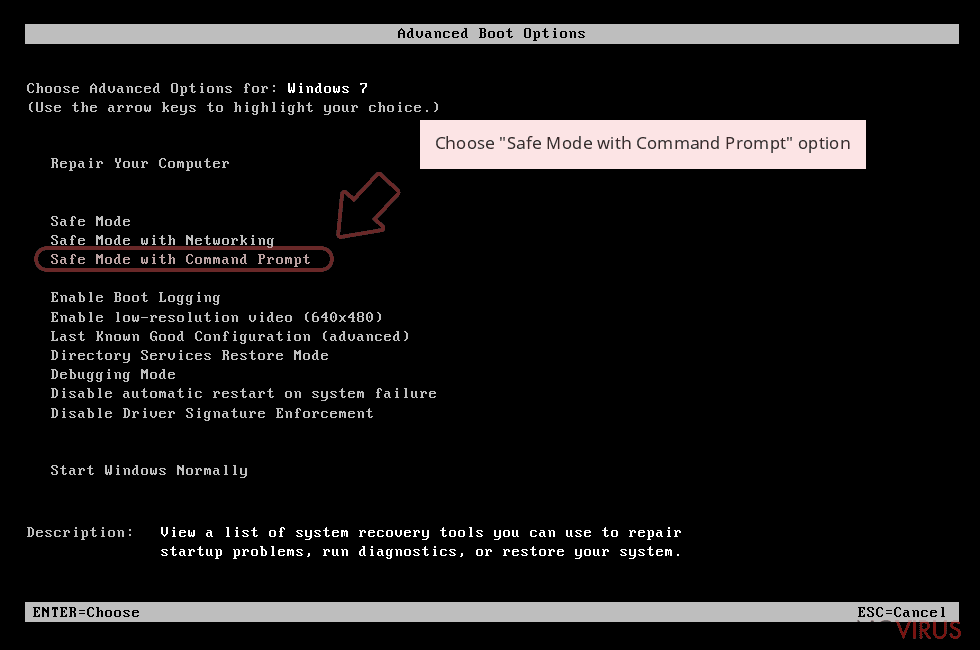
Step 1: Restart your computer in Safe Mode with Command Prompt
Windows 7 / Vista / XP- Go to Start → Shutdown → Restart → OK.
- As soon as your computer starts, start pressing F8 key repeatedly before the Windows logo shows up.
-
Choose Command Prompt from the list

Windows 10 / Windows 8- Click on the Power button at the Windows login screen, and then press and hold Shift key on your keyboard. Then click Restart.
- Then select Troubleshoot → Advanced options → Startup Settings and click Restart.
-
Once your computer starts, select Enable Safe Mode with Command Prompt from the list of options in Startup Settings.

-
Step 2: Perform a system restore to recover files and settings
-
When the Command Prompt window appears, type in cd restore and press Enter.

-
Then type rstrui.exe and hit Enter..

-
In a new window that shows up, click the Next button and choose a restore point that was created before the infiltration of Sage 2.2 and then click on the Next button again.


-
To start system restore, click Yes.

-
When the Command Prompt window appears, type in cd restore and press Enter.
Bonus: Restore your files
Using the tutorial provided above you should be able to eliminate Sage 2.2 from the infected device. novirus.uk team has also prepared an in-depth data recovery guide which you will also find above.There are a couple of methods you can apply to recover data encrypted by Sage 2.2:
Opt for Data Recovery Pro
The program is practical when locating damaged and deleted files. The tool is also useful when recovering lost emails and data from removal data storage devices.
- Download Data Recovery Pro;
- Install Data Recovery on your computer following the steps indicated in the software’s Setup;
- Run the program to scan your device for the data encrypted by Sage 2.2 ransomware;
- Recover the data.
Opt for Windows Previous Versions function
Follow the steps to recover the previous automatically saved copy of your data. Though this option is more time-consuming, you might likewise restore some of the files.
- Right-click on the encrypted document you want to recover;
- Click “Properties” and navigate to “Previous versions” tab;
- In the “Folder versions” section look for the available file copies. Choose the desired version and press “Restore”.
Sage 2.2 Decrypter
There is still no decryptor released for this malware.
It is strongly recommended to take precautions and secure your computer from malware attacks. To protect your PC from Sage 2.2 and other dangerous viruses, you should install and keep a powerful malware removal tool, for instance, FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes.
How to prevent from getting ransomware
Securely connect to your website wherever you are
Sometimes you may need to log in to a content management system or server more often, especially if you are actively working on a blog, website, or different project that needs constant maintenance or that requires frequent content updates or other changes. Avoiding this problem can be easy if you choose a dedicated/fixed IP address. It's a static IP address that only belongs to a specific device and does not change when you are in different locations.
VPN service providers such as Private Internet Access can help you with these settings. This tool can help you control your online reputation and successfully manage your projects wherever you are. It is important to prevent different IP addresses from connecting to your website. With a dedicated/fixed IP address, VPN service, and secure access to a content management system, your project will remain secure.
Reduce the threat of viruses by backing up your data
Due to their own careless behavior, computer users can suffer various losses caused by cyber infections. Viruses can affect the functionality of the software or directly corrupt data on your system by encrypting it. These problems can disrupt the system and cause you to lose personal data permanently. There is no such threat if you have the latest backups, as you can easily recover lost data and get back to work.
It is recommended to update the backups in parallel each time the system is modified. This way, you will be able to access the latest saved data after an unexpected virus attack or system failure. By having the latest copies of important documents and projects, you will avoid serious inconveniences. File backups are especially useful if malware attacks your system unexpectedly. We recommend using the Data Recovery Pro program to restore the system.