Uninstall CryptoWall virus (Uninstall Instructions) - Mar 2016 updated
CryptoWall virus Removal Guide
Description of CryptoWall virus
The fundamental things you should know about CryptoWall virus
CryptoWall virus is one of the many ransomware viruses that are continually being created every day. Just like other programs, such as Locky, Cryptolocker, BitCrypt, Cerber and a number of others, CryptoWall is intended to bring profit to its developers. It is a rather easy money as well. The principle of CryptoWall allows its creators to collect considerable sums of money by using an extremely complex RSA-2048 algorithm to encrypt the user’s files and asking to pay the ransom for the ability to unlock them. CryptoWall virus is also considered dangerous because there are a few versions of this malicious program. CryptoWall 2.0, CryptoWall 3.0 and CryptoWall 0.4 are all equally harmful and can damage your files irreversibly. There is no known way to decrypt the encrypted files without paying for the decryption key. Therefore, for the sake of your system’s health and the safety of your future files, it is highly recommended not to keep this program on your computer. If your notice that you lost access to some of your files, scan your system with a reputable antivirus tool, such as FortectIntego ASAP! Perhaps you will manage to save at least some of the remaining documents and remove CryptoWall from your computer before it causes more damage.
Speaking about the workings of CryptoWall virus in more detail, it should be noted that this ransomware travels through infected emails and can infect virtually any of the Windows operational systems, including XP, Vista, Windows 7 and Windows 8. Once the infected email is opened, and the attached infectious file is downloaded, the virus becomes activated and can begin scanning your system for files and encrypt them with the mentioned algorithm. Usually, this virus targets the audio, video files, pictures, documents and archives, but there is a number of different file extensions it can affect as well. The victims of this virus report that after CryptoWall encrypts the files it displays a message explaining what exactly happened to the computer and what can be done to retrieve the files. Typically, the victim is given a deadline to pay the ransom of $500 (~£350) after which, the sum required for the file decryption key doubles. The ransom must be paid in virtual BitCoin money. Also, the notification features links to the websites where the CryptoWall decryption key can be obtained. However, visiting the indicated websites can also be dangerous since they have to be accessed through the anonymous Tor network. It is no secret that this web browser is favored by cyber criminals because the anonymous platform enables them to easily conceal their identities. Therefore, if you decide to pay up, you not only risk of being issued a bogus decryption key or not receiving one at all, but also contaminating your system even more, with different viruses, Trojans and worms possibly lurking in the unsafe websites. We do not recommend making any transactions to the cyber criminals and better hurry with the CryptoWall removal. If you still feel sorry for your files think about whether you want to encourage the further development of such fraudulent programs and support their creators by giving them the ability to earn illegal money.
How can this virus infect my computer?
Apart from the already mentioned CryptoWall distribution via spam emails, this virus can enter the system through deceptive software updates which most commonly are encountered on unreliable websites. Java, Flash Player, Adobe Reader and similar software are the usual targets of this virus infection. The victim unsuspectedly downloads the software update, which is, in fact, an .exe file that downloads the virus and runs it on the PC. However, the most widespread method for CryptoWall to travel around the internet is through the infected email attachments. Therefore, the first thing you should do before opening newly received correspondence, especially, if it comes from an unknown source, is to make sure the emails are safe. It is not recommended to interact with any of the emails stored in the “spam” folder since the possibly hazardous emails are usually recognized by your mail provider’s system and automatically placed in this category. You can open “spam” emails unless you are really sure of their safety. If you do not take these initial precautions, the CryptoWall virus can easily slip into your computer and carry out its malicious activities, so, the next message you will see on your computer will be the ransom note, named as DECRYPT_INSTRUCTION.txt, DECRYPT_INSTRUCTION.html or DECRYPT_INSTRUCTION.url. The contents of this note go as follows:
Decrypt service
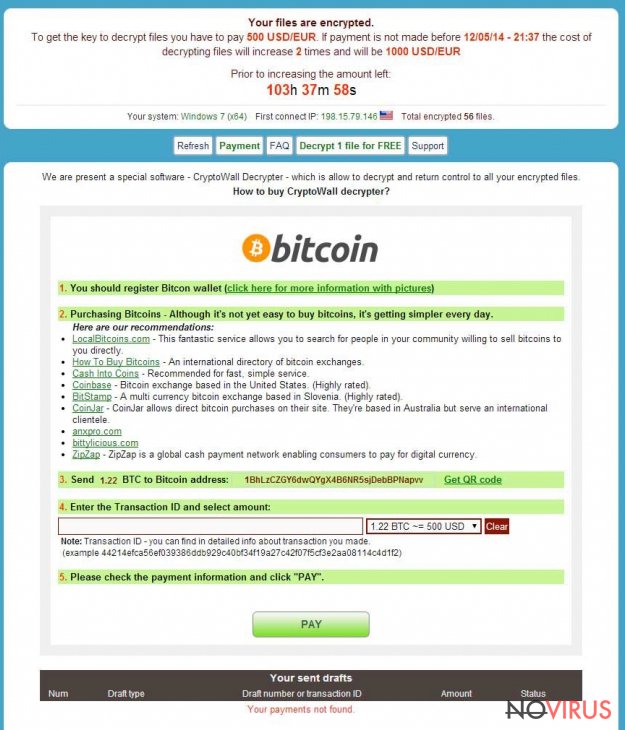
Your files are encrypted.
To get the key to decrypt files, you have to pay 500 USD/EUR. If payments is not made before [date] the cost of decrypting files will increase 2 times and will be 1000 USD/EUR Prior to increasing the amount left: [count down timer]
We are present a special software – CryptoWall Decrypter – which is allow to decrypt and return control to all your encrypted files. How to buy CryptoWall decrypter?
1. You should register Bitcoin waller
2. Purchasing Bitcoins – Although it’s not yet easy to buy bit coins, it’s getting simpler every day.
3. Send 1.22 BTC to Bitcoin address: 1BhLzCZGY6dwQYgX4B6NR5sjDebBPNapvv
4. Enter the Transaction ID and select amount.
5. Please check the payment information and click “PAY”.
Once again we have to warn you not to feel frightened or tempted by this note. The cyber criminals are only waiting for the easy profit and will do anything to make the victims pay. Therefore, it is better to avoid this malicious virus than losing your files or having to deal with the lengthy virus removal. We want to emphasize the fundamental precautions to be taken if you want to avoid this virus from entering your system. First and foremost, you should always keep a backup copy of your files in some external storage. Use USB, external hard drives, CD’s, DVD’s or any other storage which you can trust. You can store your files on file clouds like Google Drive or Dropbox, however, be aware that it is also a risky solution since this ransomware-type viruses tend to hijacks these platforms as well. Another security measure you can employ in your computer protection is the obtaining of a reliable antivirus suite, which should safeguard your computer and your browsing not only from CryptoWall but other threats as well. Finally, be very attentive while browsing the internet yourself and do not fall for the tricks, different hackers and scammers may be have prepared for you.
CryptoWall removal tips:
As you are already acquainted with this virus, its workings and dangers, you most probably are thinking about its removal. However, CryptoWall removal may pose some problems. First, it may be well hidden deep in your computer’s system, so detecting it can take time. Also, viruses like these tend to spread their malicious files throughout the infected system therefore, deleting the executive file may not be enough to completely eliminate the virus from the computer. If you do not delete all the viruses components from your system and try to recover the files from a backup, the virus may infiltrate your external storages as well and encrypt the containing files.
After you safely and entirely remove CryptoWall then, and only then, can you attempt to recover your files from external storages or online clouds. Therefore, it is essential to remove the virus and its components from your computer to the last infectious file. It can be a rather complicated task for the less experienced computer users. Even the most experienced users can overlook some cleverly concealed files. To avoid such errors it is better to rely on sophisticated antivirus programs for the purpose of the virus removal. Keep the virus database updated and your antivirus will do the rest for you. However, if CryptoWall is blocking your antivirus suite from working, disconnect your computer from the network and follow the instructions provided below.
Getting rid of CryptoWall virus. Follow these steps
In-depth guide for the CryptoWall elimination
Important! →
The elimination guide can appear too difficult if you are not tech-savvy. It requires some knowledge of computer processes since it includes system changes that need to be performed correctly. You need to take steps carefully and follow the guide avoiding any issues created due to improper setting changes. Automatic methods might suit you better if you find the guide too difficult.
Step 1. Launch Safe Mode with Networking
Safe Mode environment offers better results of manual virus removal
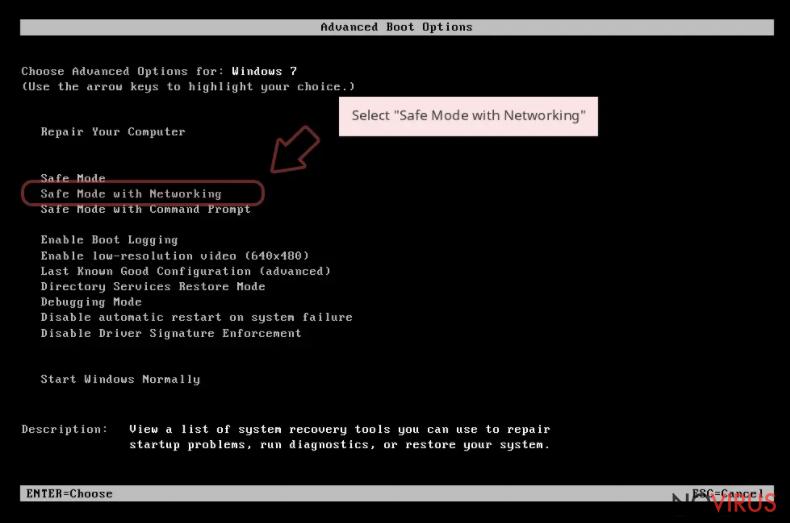
Windows 7 / Vista / XP
- Go to Start.
- Choose Shutdown, then Restart, and OK.
- When your computer boots, start pressing the F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) a few times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.
Windows 10 / Windows 8
- Right-click the Start button and choose Settings.
- Scroll down to find Update & Security.
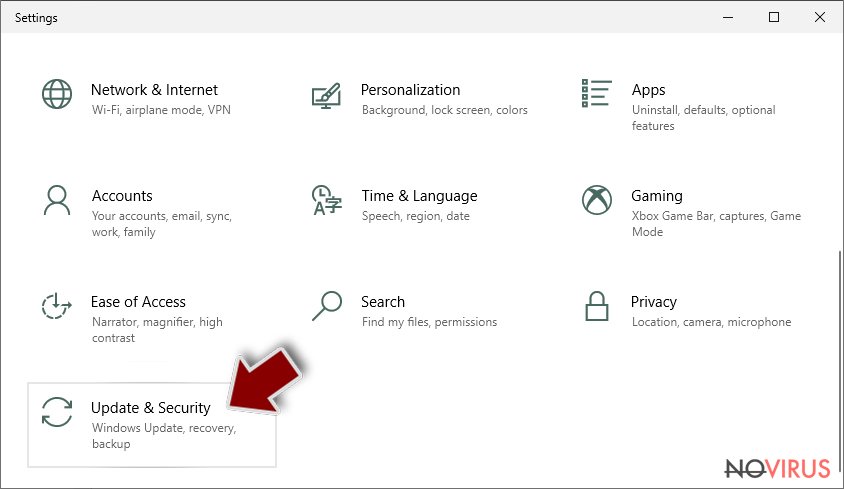
- On the left, pick Recovery.
- Scroll to find Advanced Startup section.
- Click Restart now.
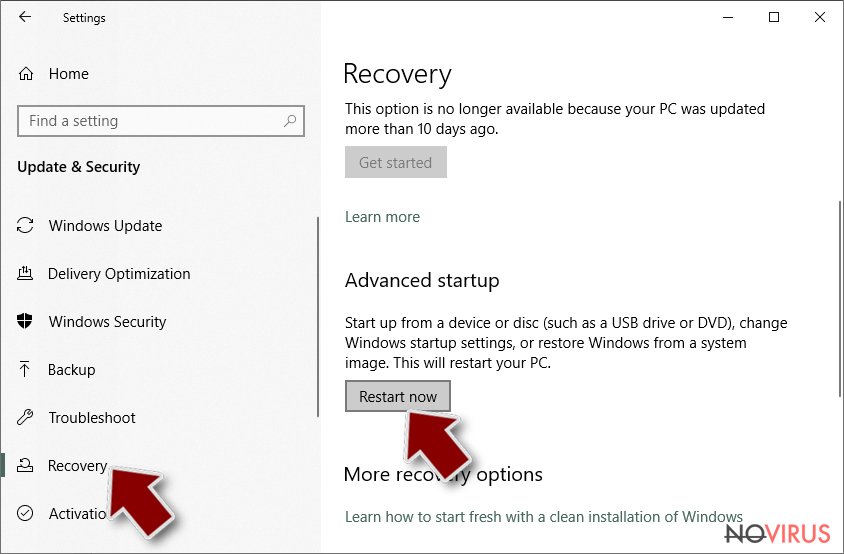
- Choose Troubleshoot.
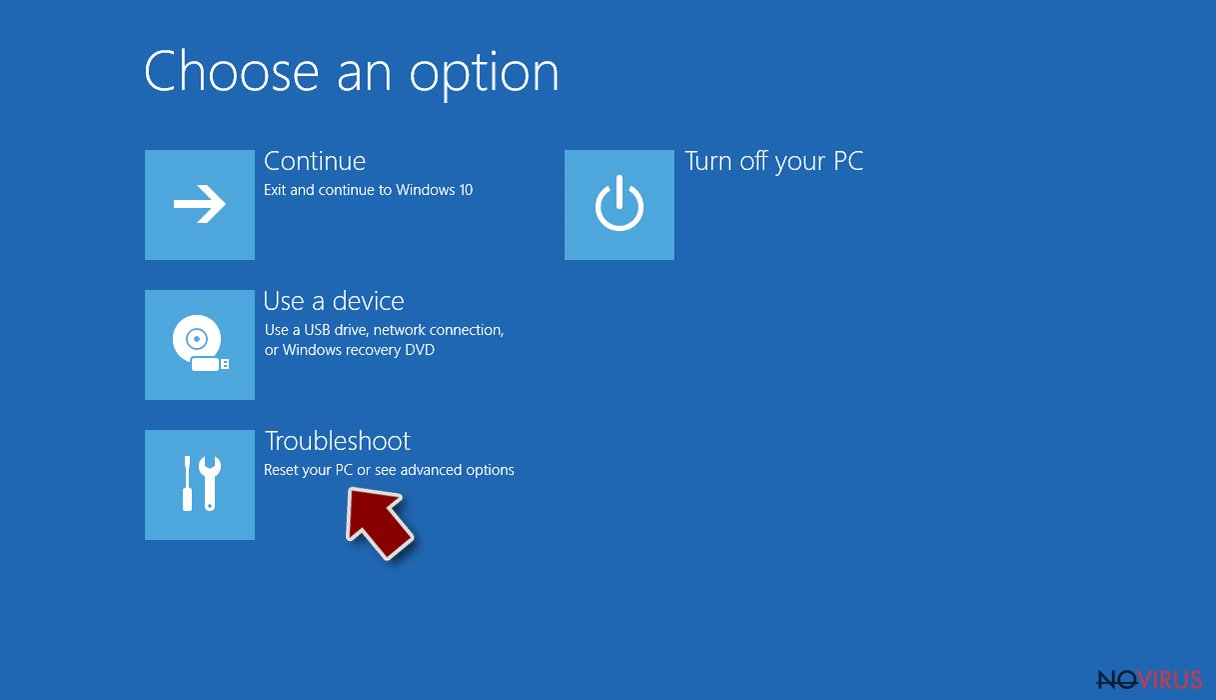
- Go to Advanced options.
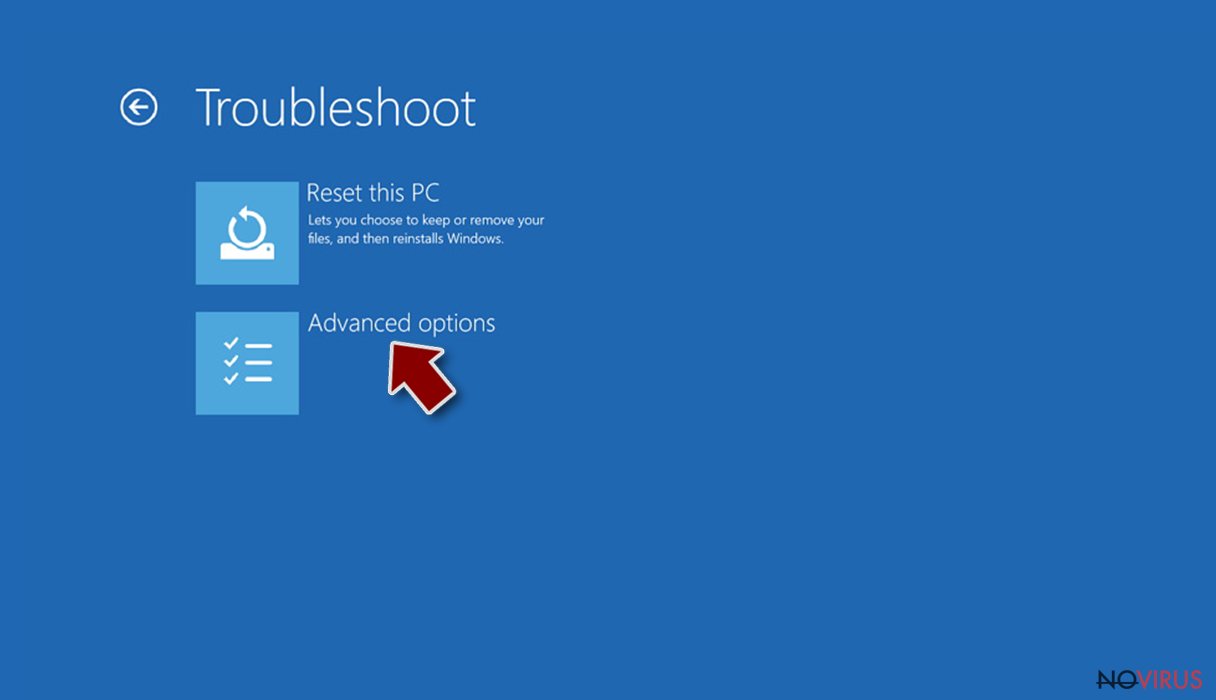
- Select Startup Settings.
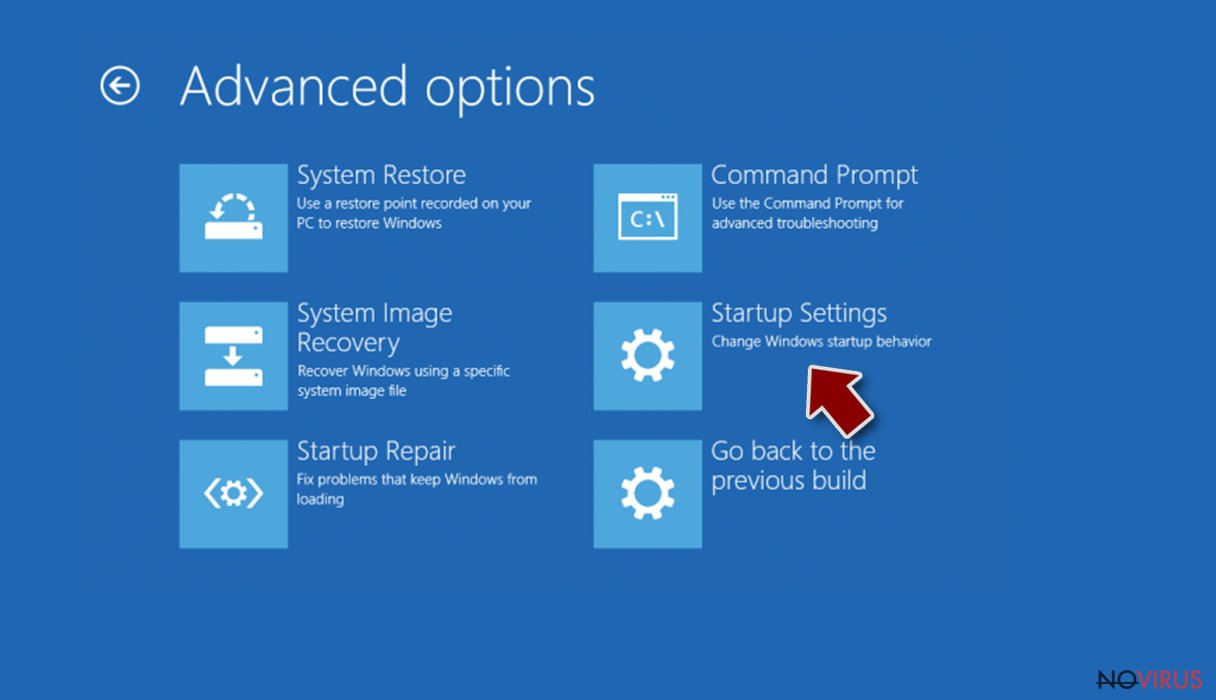
- Press Restart.
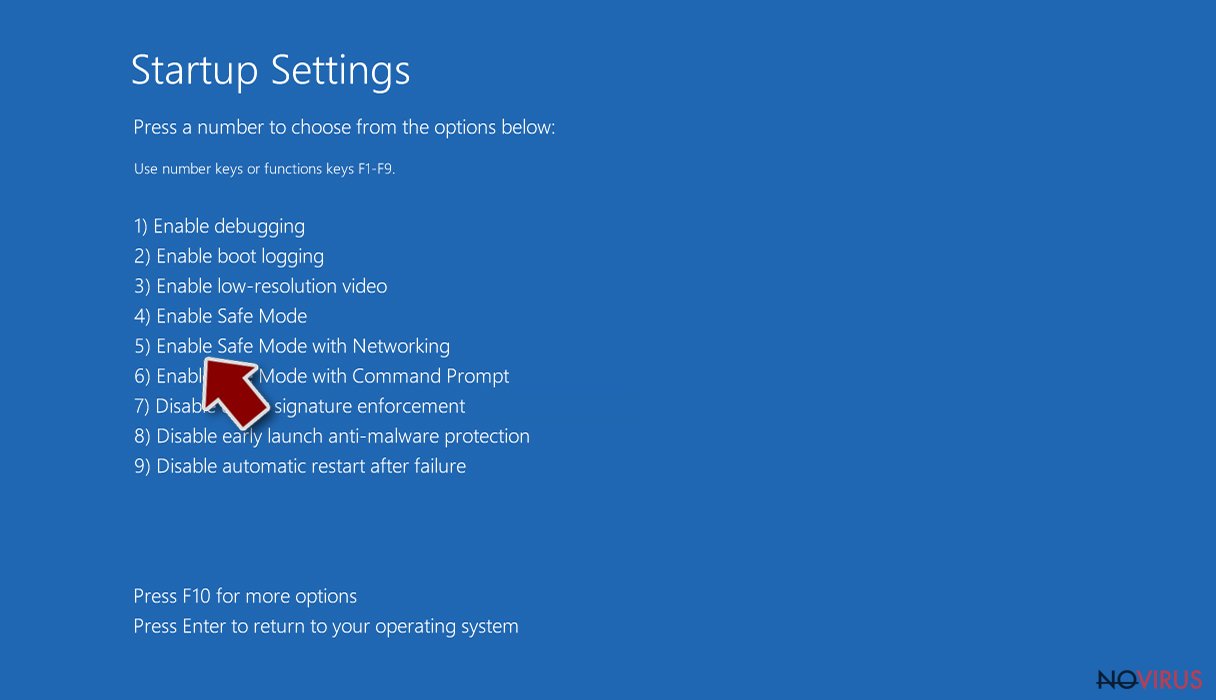
- Choose 5) Enable Safe Mode with Networking.
Step 2. End questionable processes
You can rely on Windows Task Manager that finds all the random processes in the background. When the intruder is triggering any processes, you can shut them down:
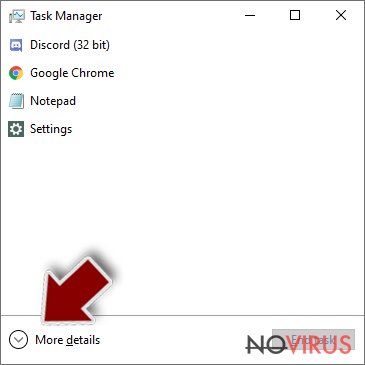
- Press Ctrl + Shift + Esc keys to open Windows Task Manager.
- Click on More details.
- Scroll down to Background processes.
- Look for anything suspicious.
- Right-click and select Open file location.
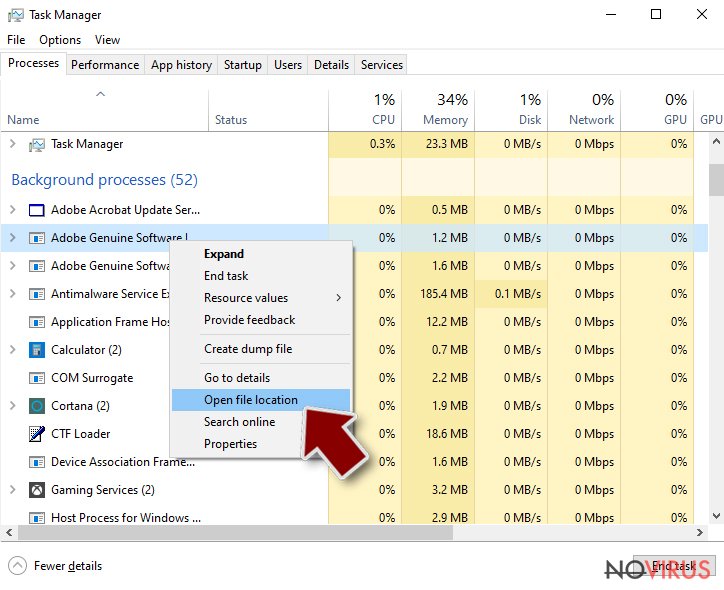
- Go back to the Process tab, right-click and pick End Task.
- Delete the contents of the malicious folder.
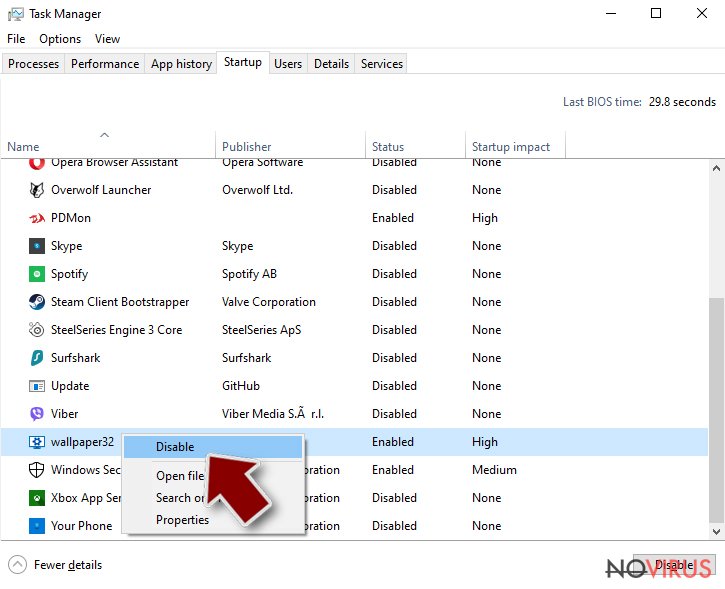
Step 3. Check the program in Startup
- Press Ctrl + Shift + Esc on your keyboard again.
- Go to the Startup tab.
- Right-click on the suspicious app and pick Disable.
Step 4. Find and eliminate virus files
Data related to the infection can be hidden in various places. Follow the steps and you can find them:
- Type in Disk Cleanup in Windows search and press Enter.
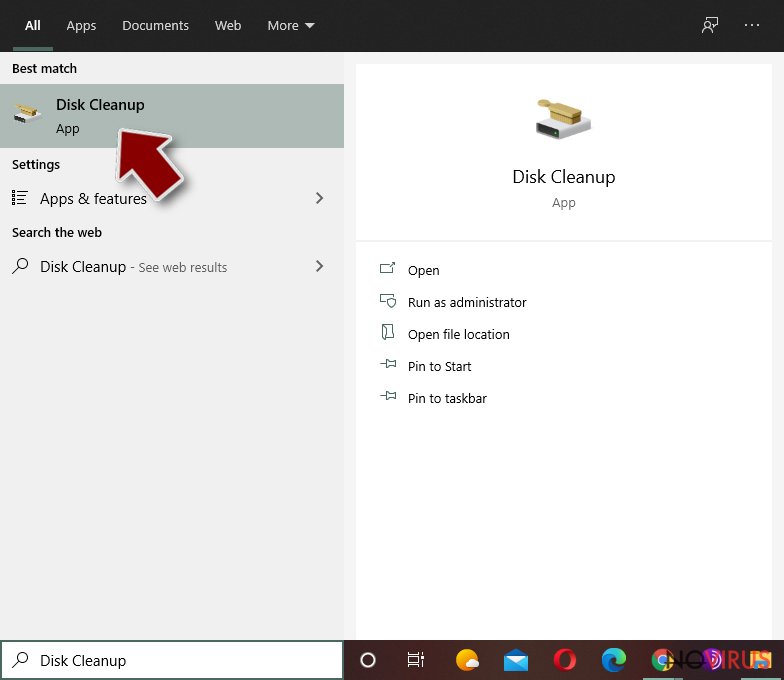
- Select the drive (C: is your main drive by default and is likely to be the one that has malicious files in) you want to clean.
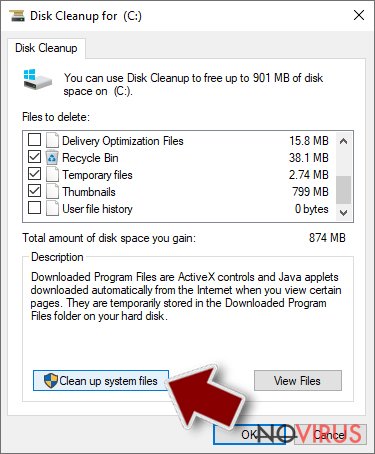
- Scroll through the Files to delete and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.
- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Eliminate CryptoWall using System Restore
-
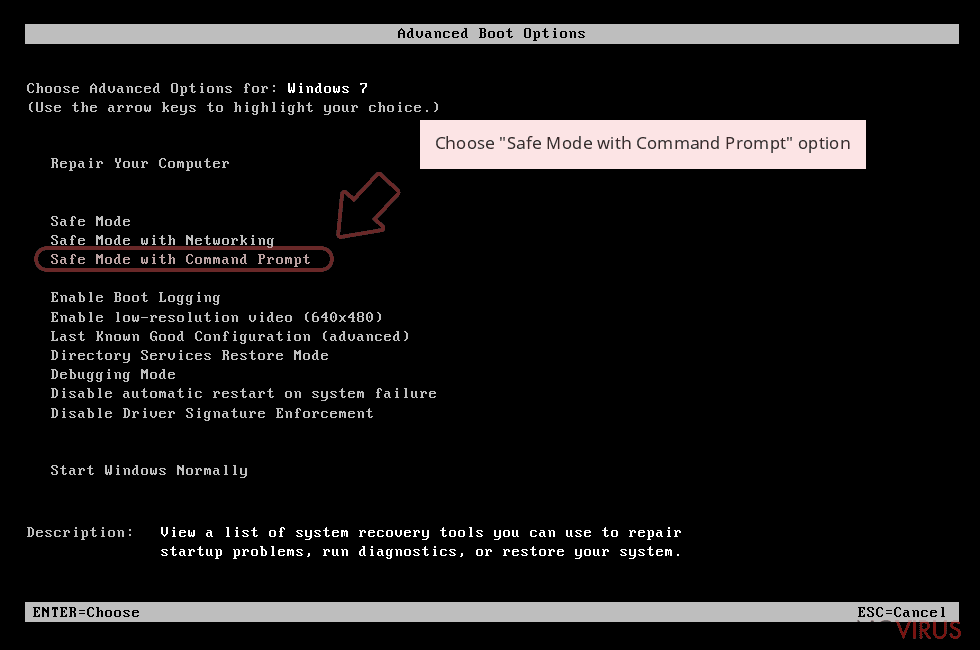
Step 1: Restart your computer in Safe Mode with Command Prompt
Windows 7 / Vista / XP- Go to Start → Shutdown → Restart → OK.
- As soon as your computer starts, start pressing F8 key repeatedly before the Windows logo shows up.
-
Choose Command Prompt from the list

Windows 10 / Windows 8- Click on the Power button at the Windows login screen, and then press and hold Shift key on your keyboard. Then click Restart.
- Then select Troubleshoot → Advanced options → Startup Settings and click Restart.
-
Once your computer starts, select Enable Safe Mode with Command Prompt from the list of options in Startup Settings.

-
Step 2: Perform a system restore to recover files and settings
-
When the Command Prompt window appears, type in cd restore and press Enter.

-
Then type rstrui.exe and hit Enter..

-
In a new window that shows up, click the Next button and choose a restore point that was created before the infiltration of CryptoWall and then click on the Next button again.


-
To start system restore, click Yes.

-
When the Command Prompt window appears, type in cd restore and press Enter.
It is strongly recommended to take precautions and secure your computer from malware attacks. To protect your PC from CryptoWall and other dangerous viruses, you should install and keep a powerful malware removal tool, for instance, FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes.
How to prevent from getting ransomware
Prevent the government from spying on you
As there is a growing debate in government about collecting users' data and spying on citizens, you should take a closer look at this issue and find out what shady ways of gathering information can be used to collect information about you. You need to browse anonymously if you want to avoid any government-initiated spying and tracking of information.
You can enjoy secure internet browsing and minimize the risk of intrusion into your system if you use Private Internet Access VPN program. This VPN application creates a virtual private network and provides access to the required data without any content restrictions.
Control government and other third party access to your data and ensure safe web browsing. Even if you do not engage in illegal activities and trust your ISP, we recommend being careful about your security. You should take extra precautions and start using a VPN program.
Reduce the threat of viruses by backing up your data
Due to their own careless behavior, computer users can suffer various losses caused by cyber infections. Viruses can affect the functionality of the software or directly corrupt data on your system by encrypting it. These problems can disrupt the system and cause you to lose personal data permanently. There is no such threat if you have the latest backups, as you can easily recover lost data and get back to work.
It is recommended to update the backups in parallel each time the system is modified. This way, you will be able to access the latest saved data after an unexpected virus attack or system failure. By having the latest copies of important documents and projects, you will avoid serious inconveniences. File backups are especially useful if malware attacks your system unexpectedly. We recommend using the Data Recovery Pro program to restore the system.