Uninstall Locky virus (Uninstall Guide) - Aug 2017 updated
Locky virus Removal Guide
Description of Locky virus
Locky virus, a ransomware you need to look out for
Recently, the cyber community was shaken by a new wave of ransomware, dubbed Locky virus. Since then, this ransomware has already taken control over hundreds of thousands of computers all across the world. Locky spreads throughout all the continents. Europe, America, and Australia have been infected.
Interestingly enough, this virus does not work on the Russian operating systems, which suggests the cyber security experts that there is a great chance that it hails from this particular Eastern European country. In fact, identification of the computer’s operating system is one of the first processes that Locky ransomware carries out in the infiltrated computer.
Therefore, it may be presumed that the origin of the operational system is of high priority to the virus developers. Once the system is identified and it appears that it is Russian, the virus terminates its activity and eliminates itself from the computer, so you don't need to think about Locky removal. Otherwise, the ransomware begins its encryption of the hijacked computer’s contents.
The ransomware does not distinguish between private or public computers and attacks any system it can access. A more broad-scale event worth mentioning, to give you an idea of the perils of this virus, took place in one of the Hollywood’s hospitals, the Hollywood Presbyterian Medical Center.
For over a week, the doctors and other medical workers were not capable of accessing the hospital’s inner system and networks since they were taken ‘hostage’ by the Locky virus.
It has been reported that the hospital administration decided to buy out their files and access to inner networks by paying the 40 Bitcoin (or around $17.000) ransom. The medical files and other data that was locked by the virus is without a doubt a vital information that the hospital authorities could not allow being lost.
However, if a virus attacks your computer, we do not recommend following this example because there is a high risk that you will not only lose your files but your money as well. It is advisable that you remove Locky from your computer as soon as possible, to protect yourself from being exposed to further threats this virus may impose on your system.
You will need a substantial antivirus tool to take care of the Locky removal. It is preferable you use FortectIntego for this purpose.
Workings of the virus: how it infiltrates your system and locks your files
As you are already familiar with the impact the appearance of Locky virus has made and is still making in the world, we can now discuss the more technical details of this virus’s workings. Essentially, there are 5 main goals of this malicious program are:
- To infiltrate the system and activate the virus;
- To determine your operating system type;
- To scan computer for files;
- To encrypt the victim’s files;
- To receive a ransom.
As you can see, there are a few steps between the actual infiltration of the system and paying the ransom to retrieve your files. We will talk about the ways this virus can infiltrate your system We can now elaborate on each of these steps individually.
1. System infiltration
Locky virus, similarly to other types of ransomware such as CTB Locker, Cryptowall, Cryptolocker or Teslacrypt, travels through infected spam email attachments. The cyber security experts estimate that Locky virus releases over 4 million infected emails a week, which is really a considerable number.
However, unlike less dangerous potentially unwanted programs, which can stealthily install into the computer through software packages, this virus requires more interaction on the behalf of the user. First, the infected email must be opened.
The developers of this ransomware make sure the user feels tempted to do that, by giving the email a gripping title. The letter itself also provides some deceptive information about the attached file, encouraging the user to download and open it.
Once the victim downloads attached archive, the containing Word or JavaScript files, need to be extracted and opened to activate the virus. The infected Word document runs on macros script which needs to be enabled in your Word settings to activate the virus.
So, if you accidentally open a suspicious email, featuring some unintelligible symbols you may be asked to enable Word macros to decrypt them. DO NOT enable it because the decrypted script will only activate the virus and lock all of your files. JavaScript file, however, overtakes the computer’s system much faster.
After it is extracted, it will begin the malicious processes on the infected computer immediately, so you should be even more cautious about these files.
2. System identification
As it was already mentioned in the introductory paragraph, it is important for the Locky virus to determine the operational system’s type. It does that by running a specifically designed script. It is important to note that the script is run in the newer versions of Locky virus, by the JavaScript file only, while the Word macros begins the encryption process as soon as it is activated.
3. Scanning for files
Now that the virus is activated, it initiates the scanning of the computer for files, including photo, video files, documents, archives, etc. A number of different file extensions can be encrypted.
4. File encryption
When Locky detects the required files, it encrypts them with a military-type AES algorithm, which is extremely complicated and impossible to decrypt without a personalized decryption key. The whole encryption process may range from several hours and to a few days to encrypt the data.
It is impossible to notice the virus at the encryption stage, yet, you may witness some slowing of the system’s performance, but it does not tend to be as significant to cause any concerns. After the virus is done encrypting the files, instead of the regular file extensions, the victim will see the unusual .locky extension.
5. Asking for ransom
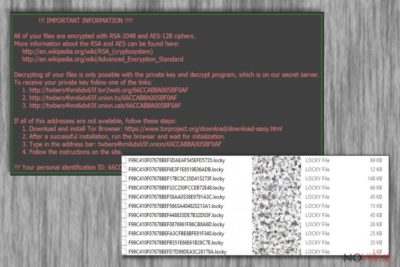
When the ransomware finishes its dirty work, it creates a _Locky_recover_instructions.txt file in every folder containing the encrypted documents. The note usually explains what happened to the victim’s computer and offers a solution. The proposed solution is rather simple.
All you have to do is purchase a decryption key which will help you to unlock the files. At the given moment, the Locky decryptor’s reaches from 0,5 up to 4 Bitcoin, while the decryptor itself can be obtained through the anonymous Tor network. However, it is not advisable to make any transactions to these cyber criminals because you may not receive the key or it may not be functional at all.
Besides, think about whether you want to encourage these crooks to continue their felonious activities and to infect more computers with new malicious programs?
The only way to protect yourself from this virus is to take precautions yourself. Make a backup copy of your system and keep it in some external storage drive, and you won't need to think about Locky removal. Also, make sure not to open suspicious emails and, most importantly, do not download the attachments.
Nevertheless, it is also important to note that Locky virus does not limit itself to the computer files only. It may also target your external storage drives once you connected them to your device. Also, the network sharing websites are vulnerable to this virus, which can infiltrate and lock the files there as well.
What is more, the online storage, or the so-called clouds, are not a safe place to store your files either. Locky is an extremely ferocious virus, so we recommend you to remove Locky as soon as you suspect it may have hijacked your computer.
How to remove Locky virus?
Locky ransomware is a surprisingly well-structured malware. Sadly, but the experts around the world have not yet discovered a way to decrypt the files without having to pay the ransom. Of course, if you are already a victim of this virus, you can try to wait it out, until the decryption key is invented.
However, in the meanwhile, you should take care of the Locky removal from your computer. Since this program is rather complicated itself, it poses some difficulties regarding its removal as well. You may find that the virus is blocking your antivirus suite and cannot run a scan.
In such case, you can try disconnecting your computer from the network, because according to the cyber security experts, it may decrease some functionalities of this ransomware. If you are encountering any other problems, you can also use our virus removal manual, provided by our team of experts below.
Getting rid of Locky virus. Follow these steps
In-depth guide for the Locky elimination
Important! →
The elimination guide can appear too difficult if you are not tech-savvy. It requires some knowledge of computer processes since it includes system changes that need to be performed correctly. You need to take steps carefully and follow the guide avoiding any issues created due to improper setting changes. Automatic methods might suit you better if you find the guide too difficult.
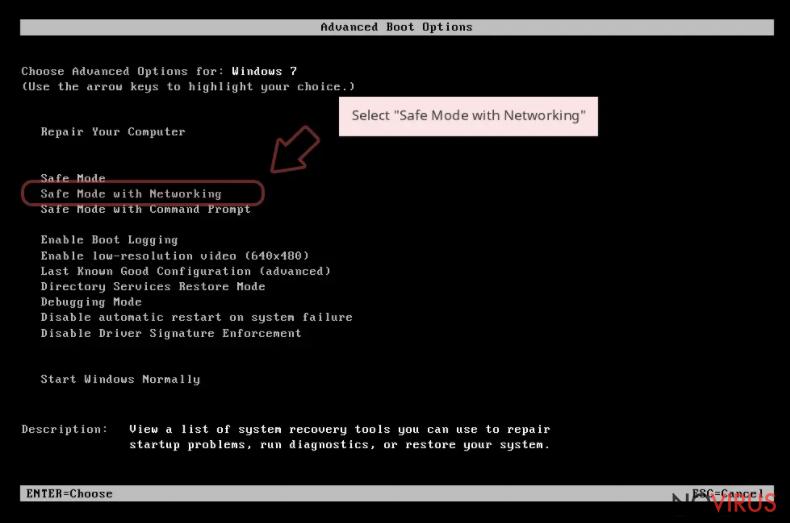
Step 1. Launch Safe Mode with Networking
Safe Mode environment offers better results of manual virus removal
Windows 7 / Vista / XP
- Go to Start.
- Choose Shutdown, then Restart, and OK.
- When your computer boots, start pressing the F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) a few times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click the Start button and choose Settings.

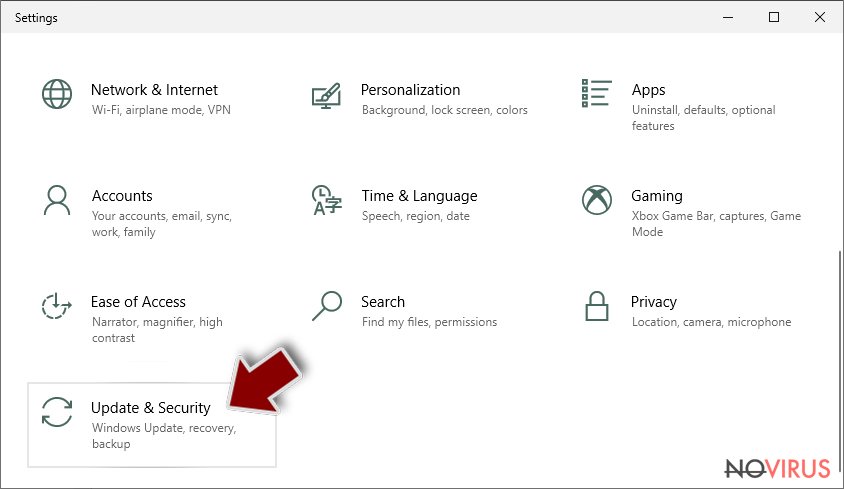
- Scroll down to find Update & Security.

- On the left, pick Recovery.
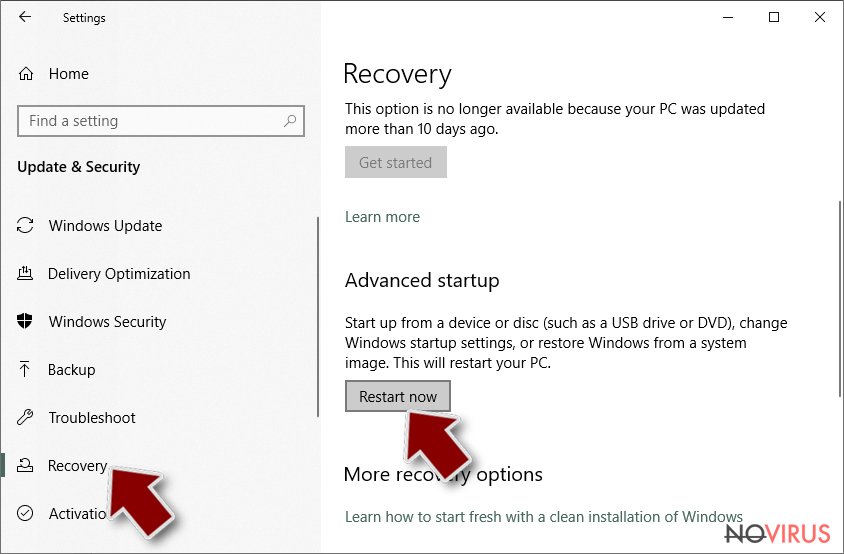
- Scroll to find Advanced Startup section.
- Click Restart now.

- Choose Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

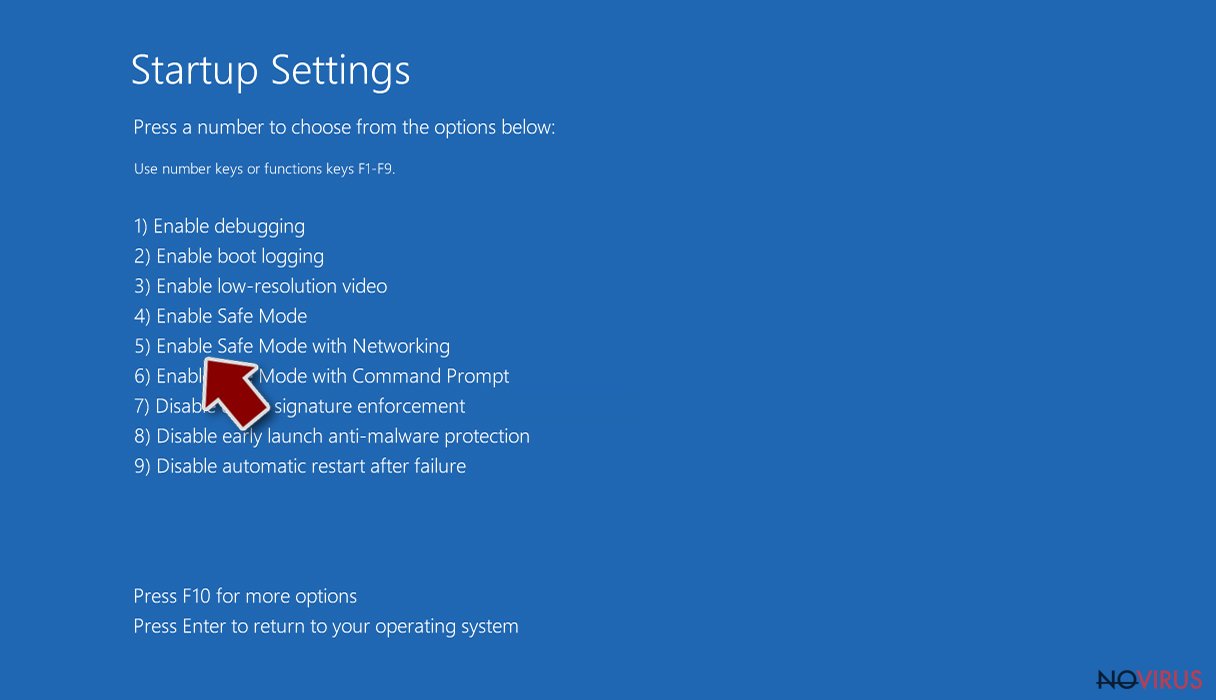
- Press Restart.

- Choose 5) Enable Safe Mode with Networking.
Step 2. End questionable processes
You can rely on Windows Task Manager that finds all the random processes in the background. When the intruder is triggering any processes, you can shut them down:
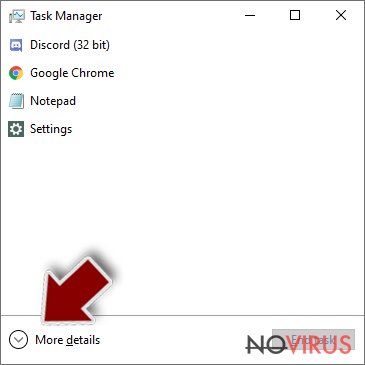
- Press Ctrl + Shift + Esc keys to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes.
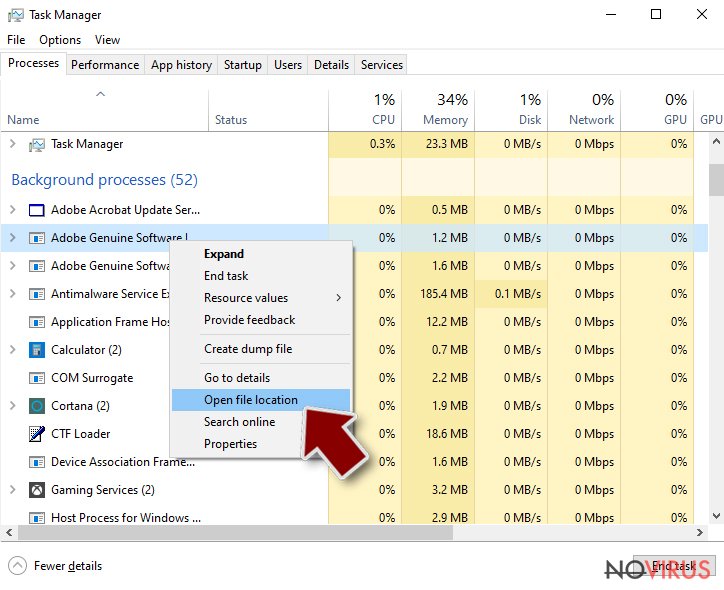
- Look for anything suspicious.
- Right-click and select Open file location.

- Go back to the Process tab, right-click and pick End Task.
- Delete the contents of the malicious folder.
Step 3. Check the program in Startup
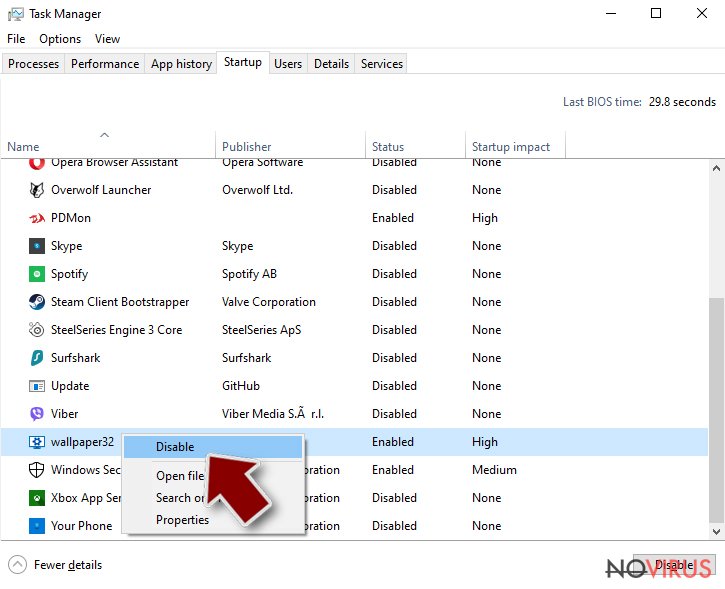
- Press Ctrl + Shift + Esc on your keyboard again.
- Go to the Startup tab.
- Right-click on the suspicious app and pick Disable.

Step 4. Find and eliminate virus files
Data related to the infection can be hidden in various places. Follow the steps and you can find them:
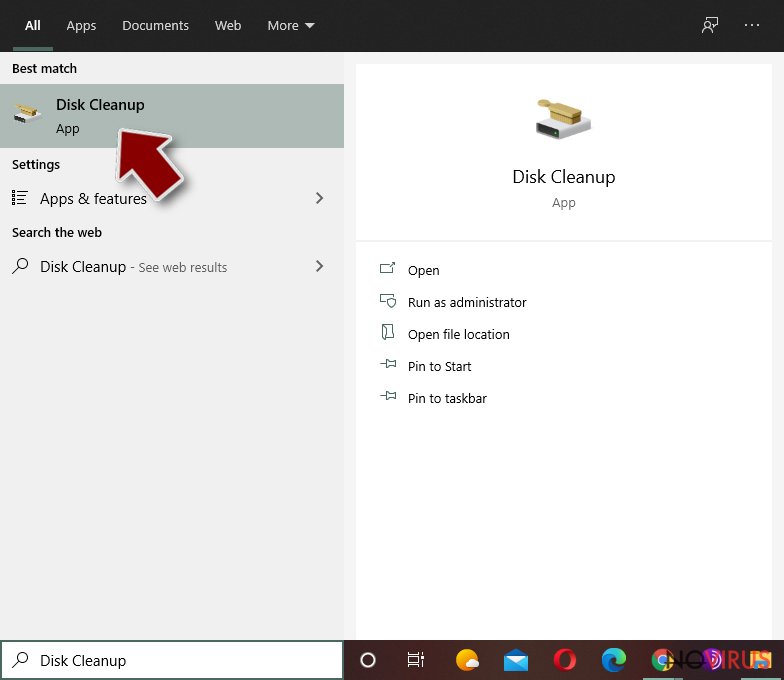
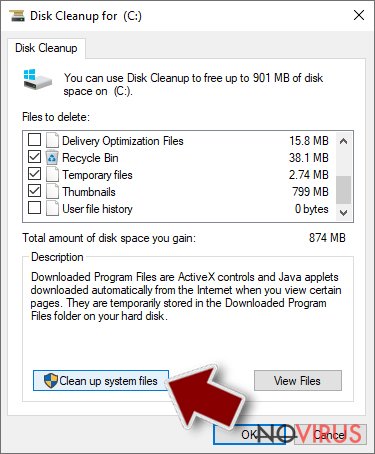
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive (C: is your main drive by default and is likely to be the one that has malicious files in) you want to clean.
- Scroll through the Files to delete and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Eliminate Locky using System Restore
-
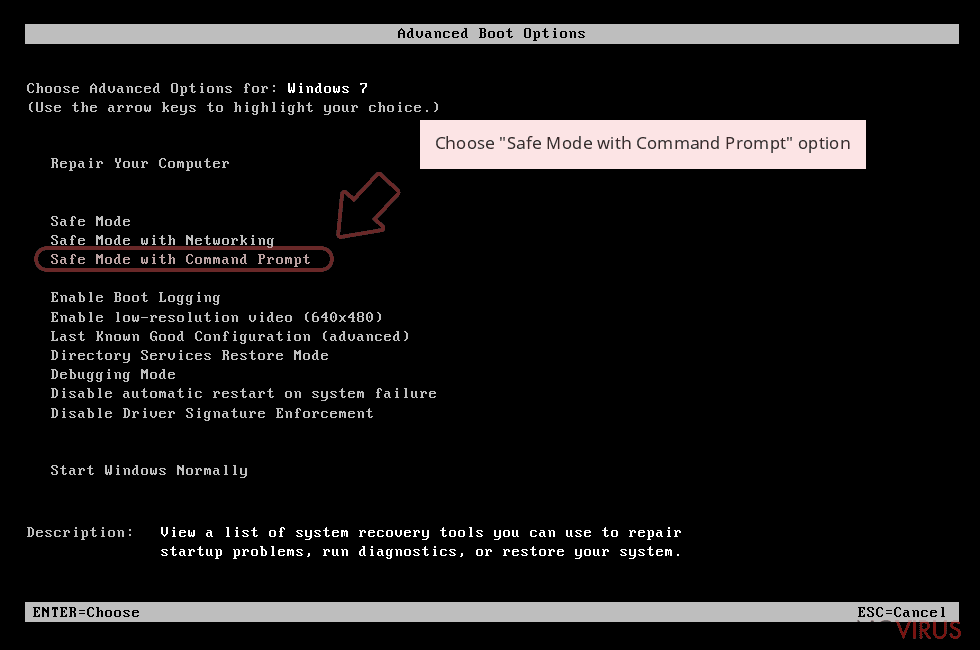
Step 1: Restart your computer in Safe Mode with Command Prompt
Windows 7 / Vista / XP- Go to Start → Shutdown → Restart → OK.
- As soon as your computer starts, start pressing F8 key repeatedly before the Windows logo shows up.
-
Choose Command Prompt from the list

Windows 10 / Windows 8- Click on the Power button at the Windows login screen, and then press and hold Shift key on your keyboard. Then click Restart.
- Then select Troubleshoot → Advanced options → Startup Settings and click Restart.
-
Once your computer starts, select Enable Safe Mode with Command Prompt from the list of options in Startup Settings.

-
Step 2: Perform a system restore to recover files and settings
-
When the Command Prompt window appears, type in cd restore and press Enter.

-
Then type rstrui.exe and hit Enter..

-
In a new window that shows up, click the Next button and choose a restore point that was created before the infiltration of Locky and then click on the Next button again.


-
To start system restore, click Yes.

-
When the Command Prompt window appears, type in cd restore and press Enter.
It is strongly recommended to take precautions and secure your computer from malware attacks. To protect your PC from Locky and other dangerous viruses, you should install and keep a powerful malware removal tool, for instance, FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes.
How to prevent from getting ransomware
A proper web browser and VPN tool can guarantee better safety
As online spying becomes an increasing problem, people are becoming more interested in how to protect their privacy. One way to increase your online security is to choose the most secure and private web browser. But if you want complete anonymity and security when surfing the web, you need Private Internet Access VPN service. This tool successfully reroutes traffic across different servers, so your IP address and location remain protected. It is also important that this tool is based on a strict no-log policy, so no data is collected and cannot be leaked or made available to first or third parties. If you want to feel safe on the internet, a combination of a secure web browser and a Private Internet Access VPN will help you.
Recover files damaged by a dangerous malware attack
Despite the fact that there are various circumstances that can cause data to be lost on a system, including accidental deletion, the most common reason people lose photos, documents, videos, and other important data is the infection of malware.
Some malicious programs can delete files and prevent the software from running smoothly. However, there is a greater threat from the dangerous viruses that can encrypt documents, system files, and images. Ransomware-type viruses focus on encrypting data and restricting users’ access to files, so you can permanently lose personal data when you download such a virus to your computer.
The ability to unlock encrypted files is very limited, but some programs have a data recovery feature. In some cases, the Data Recovery Pro program can help recover at least some of the data that has been locked by a virus or other cyber infection.